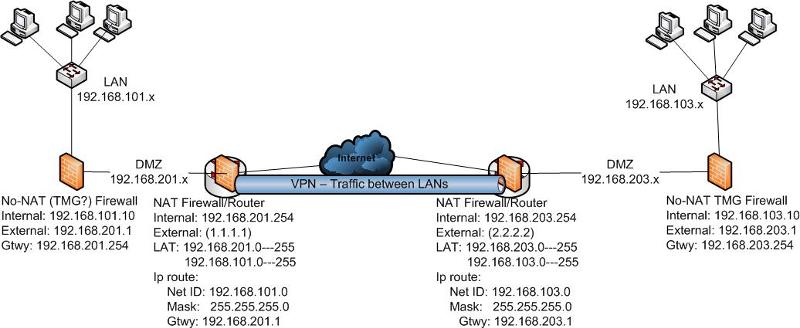
TMG is hosting SQL server, i have a rule to allow, connections are initiated then denied
So my firewall is also hosting an SQL server ( I know not best practice but i dont have much choice (money expense))
its only for internal use so not much of a threat
but anyway, ive created my rule to match denies i saw in the firewall logging
now the rule allows initates then its deneid due to a non sync packet
ive read this might be to do with default gateways
im connecting of a VPN managed by our cisco routers (trying setting up SQL Replication)
ive created a routgin topolgy in TMG from one network to the other
the network connectivity is fine, im rdping to the machine now from over the VPN so i didnt think it could be a network issue
anyway if anyone has any ideas?
Thanks
log.png
rule.png
its only for internal use so not much of a threat
but anyway, ive created my rule to match denies i saw in the firewall logging
now the rule allows initates then its deneid due to a non sync packet
ive read this might be to do with default gateways
im connecting of a VPN managed by our cisco routers (trying setting up SQL Replication)
ive created a routgin topolgy in TMG from one network to the other
the network connectivity is fine, im rdping to the machine now from over the VPN so i didnt think it could be a network issue
anyway if anyone has any ideas?
Thanks
log.png
rule.png
Sorry, I know you and I have worked together on a good number of questions together but this isn't a question I would be able to respond to.
ASKER
Hey keith, what do you mean you would not be able to respond?
i have created a topology and some screens of the scenario if it helps
Firewall-Topology.jpg
DC1-Firewall-Networks.png
DC1-Firewall-Routing.png
DC3-Firewall-Routing.png
DC3-Firewall-Networks.png
i have created a topology and some screens of the scenario if it helps
Firewall-Topology.jpg
DC1-Firewall-Networks.png
DC1-Firewall-Routing.png
DC3-Firewall-Routing.png
DC3-Firewall-Networks.png
No, for me this is simply just so far from best-practice and the supported position that I'll leave it for others to respond to. The issues you are opening up for yourself are horrible - for example, housekeeping routines and the like (or anything that requires amending services) will stop TMG's ability to write its logs - meaning that Internet service is impacted because the ability to log must be available at all times. Additional required ports and rules to the localhost take it into areas that I do not deal in.
I'm sure there will be others to are less fussu who will pick this one up for you.
I'm sure there will be others to are less fussu who will pick this one up for you.
From what I can see:
1. the topology is all screwed up,...it is going in circles Either you need to remove the link between the Switch and the Router (implying that this router is really a NAT Firewall),...or remove the link between the DC and the Router (which means TMG is removed and the second nic is removed or disabled). So pick one and do it
2. the DC is multi-homed. Running an SQL Server on the TMG is bad enough,...but running the same machine as a DC (which creates a multi-homed DC) is just unacceptable. No sensible IT person is going to want to get anywhere near that.
1. the topology is all screwed up,...it is going in circles Either you need to remove the link between the Switch and the Router (implying that this router is really a NAT Firewall),...or remove the link between the DC and the Router (which means TMG is removed and the second nic is removed or disabled). So pick one and do it
2. the DC is multi-homed. Running an SQL Server on the TMG is bad enough,...but running the same machine as a DC (which creates a multi-homed DC) is just unacceptable. No sensible IT person is going to want to get anywhere near that.
ASKER
the router is there for NAT yes
The server is not a DC you cannot isntall TMG on a DC, the name DC1-Firewall is just my way of naming (basically saying this is the firewall for DC1, my other servers are named as such DC1-FileServer, DC2-SQL Server, its just reference)
so the server is not connected to the DC, the firewall is connected to the router and the clients
the only way i could get this to work without that topology is to get the firewall to do the natting and all the routing, which is what my router is for, i onyl have 1 public IP address so its setup this way
my routers manage the VPNS so any traffic destined for another lan goes to the internal side of the router and any external goes to the firewall then out
is this explained any better now?
should i get an old crappy server and put the sql on that instead of this way?
Cheers
The server is not a DC you cannot isntall TMG on a DC, the name DC1-Firewall is just my way of naming (basically saying this is the firewall for DC1, my other servers are named as such DC1-FileServer, DC2-SQL Server, its just reference)
so the server is not connected to the DC, the firewall is connected to the router and the clients
the only way i could get this to work without that topology is to get the firewall to do the natting and all the routing, which is what my router is for, i onyl have 1 public IP address so its setup this way
my routers manage the VPNS so any traffic destined for another lan goes to the internal side of the router and any external goes to the firewall then out
is this explained any better now?
should i get an old crappy server and put the sql on that instead of this way?
Cheers
Your "router" IS the Firewall. If it is running NAT and is hosting the VPN,...then it IS the Firewall.
You TMGs have no reason to even exist,..., they aren't doing anything useful,...plus your topology is bypassing them anyway.
SQL on the TMG is a problem. TMG already uses the SQL Express for its logging. Installing another means you now have two SQL Servers on the TMG and removing one may very well screw up the other and screwing up the SQL used for TMG's logging will require a removal of TMG and a reinstall to fix.
You TMGs have no reason to even exist,..., they aren't doing anything useful,...plus your topology is bypassing them anyway.
SQL on the TMG is a problem. TMG already uses the SQL Express for its logging. Installing another means you now have two SQL Servers on the TMG and removing one may very well screw up the other and screwing up the SQL used for TMG's logging will require a removal of TMG and a reinstall to fix.
ASKER
well firewalls have more uses than NAT and VPN.
its used to filter incoming traffic that the router allows through and prohibit outgoing traffic or certain types
I only have 1 public IP address and my routers run a DMVPN what else am i supposed to do
the internal side of the firewall only connects to the router for lan to lan traffic, if it doesnt then the traffic has no way of traversing the VPN
All clients point to the firewall then internal traffic is sent to the internal IP (192.168.101.254) of the router, external traffic is sent to the external IP of the router (192.168.201.254) its the best i could do with the situation, unless I want TMG to manage the VPNs in which i want my cisco routers to do, so it has to be this way, the firewalls are still working to their main purpose of packet inspection, the only thing thats getting bypassed is lan to lan traffic
its used to filter incoming traffic that the router allows through and prohibit outgoing traffic or certain types
I only have 1 public IP address and my routers run a DMVPN what else am i supposed to do
the internal side of the firewall only connects to the router for lan to lan traffic, if it doesnt then the traffic has no way of traversing the VPN
All clients point to the firewall then internal traffic is sent to the internal IP (192.168.101.254) of the router, external traffic is sent to the external IP of the router (192.168.201.254) its the best i could do with the situation, unless I want TMG to manage the VPNs in which i want my cisco routers to do, so it has to be this way, the firewalls are still working to their main purpose of packet inspection, the only thing thats getting bypassed is lan to lan traffic
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
true about internal to internal traffic, that will be the cause of a routing issue i was thinking about
if the clients DG is the firewall the return traffic wont go back to the firewall it will go directly to the client
i never work on ive made up my mind i know best cos i know i dont, as much as i think i know somone always knows more thats why im here.
I have two firewalls at the moment so to speak, my router blocks and allows NATs and VPNs and anything the router allows through is then checked again by TMG, two is better than one no? :)
im perfectly willing to get a better/cleaner topology setup aslong as my router can keep doing NAT and the VPNs
am i correct in what your suggesting would be to let TMG do Routing/NAT/VPN?
there wouldnt be any use in my routers then though would there :S
how can i therfore route LAN to LAN if i set the TMG as the DG and removed the link between the router and the swtich for internal LAN?
if the clients DG is the firewall the return traffic wont go back to the firewall it will go directly to the client
i never work on ive made up my mind i know best cos i know i dont, as much as i think i know somone always knows more thats why im here.
I have two firewalls at the moment so to speak, my router blocks and allows NATs and VPNs and anything the router allows through is then checked again by TMG, two is better than one no? :)
im perfectly willing to get a better/cleaner topology setup aslong as my router can keep doing NAT and the VPNs
am i correct in what your suggesting would be to let TMG do Routing/NAT/VPN?
there wouldnt be any use in my routers then though would there :S
how can i therfore route LAN to LAN if i set the TMG as the DG and removed the link between the router and the swtich for internal LAN?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Oh,...and the SQL that was in the original question,...you need to get that off the TMG. An old crappy server would be "ok" as long as it is not too crappy. Also the more crappy the server,..the more important the Full System State Backups become. You also don't want it to be so crappy that you can not replace failed hardware parts with exact identical replacement parts. The Full System State Backups only work if the hardware is near identical when restoring.
With your existing arrangement the only possible way (as ugly as it is) to even get close to working normal with the VPN is to create a Static Route on every machine on the LAN that tells them in order to reach the Subnet of the Remote LAN they must use the Cisco's 192.168.103.254 as the "Gateway" to get there. This is a management nightmare, but it will allow the traffic to/from the Remote LAN in a Synchronous Path. This also means you have to add the Remote LAN's IP Range to the Internal Network Definition on the TMG
ASKER
with regards to your last post, the clients DG is set to the router
i trialled the clients pointing to the firewall as DG and as discussed earlier that failed and i can now remember why
the clients currently point to 192.168.103.254 and the firewalls internal range has 192.168.101.0/24 192.168.102.0/24 in it
so the firewall thinks that traffic is local, the only thing clients use the TMG server for is proxy and the TMG is only used as proxy and as an additional firewall layer to the ciscos firewall when ports are forwarded
as far as im aware i cant get a more than 1 ip on our current dsl packages so the Inter-to-External Relationship relationship, the below image is this where it is?
also i dont know what is meant by bidirectional Access Rules?
and would i keep my tmg static routes and internal address ranges on the internal network?
Thanks
route.png
i trialled the clients pointing to the firewall as DG and as discussed earlier that failed and i can now remember why
the clients currently point to 192.168.103.254 and the firewalls internal range has 192.168.101.0/24 192.168.102.0/24 in it
so the firewall thinks that traffic is local, the only thing clients use the TMG server for is proxy and the TMG is only used as proxy and as an additional firewall layer to the ciscos firewall when ports are forwarded
as far as im aware i cant get a more than 1 ip on our current dsl packages so the Inter-to-External Relationship relationship, the below image is this where it is?
also i dont know what is meant by bidirectional Access Rules?
and would i keep my tmg static routes and internal address ranges on the internal network?
Thanks
route.png
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
My "real" job is requiring me to go to the State Capitol Building in a bit, so I may not be able to reply back till later.
ASKER
ok creating the address set, is it under networks or network sets as both ask which type and id presume its internal but i thought id double check
then i add this to each tmg server we have at each site then i leave the extra routing and internal ranges i added in response #36356542?
then from applying the tmg will do the natting and the ciscos still the VPNs?
do i then point all the clients to the TMG as gateway or leave them as the router?
Thanks
int-ranges.png
then i add this to each tmg server we have at each site then i leave the extra routing and internal ranges i added in response #36356542?
then from applying the tmg will do the natting and the ciscos still the VPNs?
do i then point all the clients to the TMG as gateway or leave them as the router?
Thanks
int-ranges.png
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ok heres what i got
Rule Name: Inter-Site Access
Action: Allow
Protocols: All Outbound Taffic
From: Internal/ Remote LANs
To: Internal/Remote LANs
Users: All Users
i took the routes to the other networks out of the routing topology and ping fails, im guessing i need to get these back in?
Thanks
remote-lans.png
Networks.png
Routing.png
Internet-Access.png
Rule Name: Inter-Site Access
Action: Allow
Protocols: All Outbound Taffic
From: Internal/ Remote LANs
To: Internal/Remote LANs
Users: All Users
i took the routes to the other networks out of the routing topology and ping fails, im guessing i need to get these back in?
Thanks
remote-lans.png
Networks.png
Routing.png
Internet-Access.png
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I didn't see anything wrong with your other details.
At this point I really think I have said all I can say. Anything else I say will be me just repeating something I have already said. So if you have more problems then look back over my posts above,...the answer will be in there somewhere. Although this method is not what I would ever do,...it is still a normal well established method, it is simple, straight forward, with no "secrets" anywhere. You just have to think it through and understand the logic of how it works,...it is just "normal stuff".
At this point I really think I have said all I can say. Anything else I say will be me just repeating something I have already said. So if you have more problems then look back over my posts above,...the answer will be in there somewhere. Although this method is not what I would ever do,...it is still a normal well established method, it is simple, straight forward, with no "secrets" anywhere. You just have to think it through and understand the logic of how it works,...it is just "normal stuff".
Also keep in mind that if you screw up TMG's ability to write its log because you installed an SQL Server on the TMG,...then the TMG is going to get really "stupid" on you and I can't say for sure how it is going to behave.
On the way into work this morning I started thinking about the Cisco NAT Router. I had not focused on it since I figured you would know what to do with it. But in the back-to-back topology shown in the diagram above you have to remove any and all configuration related to 192.168.103.254 Interface and eliminate the Interface. You then have to add the 192.168.103.x network range to the Local Address Table (because it is running NAT) and you have to create a Static Route on the device that tells it in order to reach the 192.168.103.x network it must use 192.168.203.1 as the Gateway (the External TMG nic).
ASKER
thats what had me confused whilst trying to do this :)
then the external TMG knows how to send it back because of that inter site access rule? thats not right is it?
i then need a static route in tmg that says to send all .103.0/24 traffic to 192.168.203.254?
if im right the each cisco will need a static route from one to another as will tmg?
so cisco 103
ip route 192.168.101.0 255.255.255.0 192.168.201.1
TMG 103
Network Topology Route
192.168.101.0 /24 192.168.201.1
cisco 101
ip route 192.168.103.0 255.255.255.0 192.168.203.1
192.168.103.0 /24 192.168.201.1
the vpns will then need to connect via the 192.168.20x.0 routes and forget about the 192.168.10x.0 routes
it will be like the vpns connect on the external ints of the TMG?
i cant test this during working hours unfortunately but i can in about 2 hours and ill give it a whirl then
Thanks
then the external TMG knows how to send it back because of that inter site access rule? thats not right is it?
i then need a static route in tmg that says to send all .103.0/24 traffic to 192.168.203.254?
if im right the each cisco will need a static route from one to another as will tmg?
so cisco 103
ip route 192.168.101.0 255.255.255.0 192.168.201.1
TMG 103
Network Topology Route
192.168.101.0 /24 192.168.201.1
cisco 101
ip route 192.168.103.0 255.255.255.0 192.168.203.1
192.168.103.0 /24 192.168.201.1
the vpns will then need to connect via the 192.168.20x.0 routes and forget about the 192.168.10x.0 routes
it will be like the vpns connect on the external ints of the TMG?
i cant test this during working hours unfortunately but i can in about 2 hours and ill give it a whirl then
Thanks
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
the vpns will then need to connect via the 192.168.20x.0 routes and forget about the 192.168.10x.0 routes. it will be like the vpns connect on the external ints of the TMG?
No. The VPN terminates on the Cisco NAT Router/Firewall the same as it has been.
Nothing involving the VPNs will have a clue that TMG even exist to begin with. TMG will behave as nothing more than a generic LAN Router sitting between the 203.x and the 103.x LAN segments.
No. The VPN terminates on the Cisco NAT Router/Firewall the same as it has been.
Nothing involving the VPNs will have a clue that TMG even exist to begin with. TMG will behave as nothing more than a generic LAN Router sitting between the 203.x and the 103.x LAN segments.
That does nto mean that the TMG will only be a generic LAN Router. I only meant that language in the specific context of the traffic moving between the Sites over the VPN.
ASKER
sorry i should of mentioned, im usuing gre over IPsec for the VPNs and using EIGRP to propogate the routes
currently each router has
router eigrp xxx
network (tunnel addresses)
network 192.168.10x.0 (LAN for each site)
i should then
no network 192.168.10x.0
network 192.168.20x.0
yes?
currently each router has
router eigrp xxx
network (tunnel addresses)
network 192.168.10x.0 (LAN for each site)
i should then
no network 192.168.10x.0
network 192.168.20x.0
yes?
It is irrelevant to the discussion. VPN almost always uses GRE, so it is a given. Plus the Tunnel terminates on the Cisco box and never touches the TMG,...so irrelevant.
EIGRP is irrelevant to the discussion as well. Dynamic Routing Protocols do not mean you can't use a Static Route if you need one,....and you need one.
EIGRP is irrelevant to the discussion as well. Dynamic Routing Protocols do not mean you can't use a Static Route if you need one,....and you need one.
ASKER
sorry i meant in the sense that if i am to eradicate the 192.168.103.254 interface from the router than the router should no longer advertise its dynamic routes and should only use the static?
Sounds right,..yes.
This discussion let me to create a blog page with a generic version of this diagram.
Site-to-Site VPN with B2B DMZ, Terminating Tunnel at Outer Firewall
http://phillipwindell.wordpress.com/site-to-site-vpn-with-b2b-dmz-terminating-tunnel-at-outer-firewall/
Site-to-Site VPN with B2B DMZ, Terminating Tunnel at Outer Firewall
http://phillipwindell.wordpress.com/site-to-site-vpn-with-b2b-dmz-terminating-tunnel-at-outer-firewall/
ASKER
good idea for anyone in my situation there, if i could of had two public IPs i would of done it a better way but my ISP will only give me it on their highest package, (double what we pay now)
i failed to inform you that we have 5 all set up similarly and ive just realised this is gonna be a big job to get everything up and routed then all the right traffic allowed through, im going to have to arrange to come in weekend to do this
i will report back prob saturday afternoon when i have accoplished it :)
thanks for your help so far though
Alex
i failed to inform you that we have 5 all set up similarly and ive just realised this is gonna be a big job to get everything up and routed then all the right traffic allowed through, im going to have to arrange to come in weekend to do this
i will report back prob saturday afternoon when i have accoplished it :)
thanks for your help so far though
Alex
ASKER
oh quick question, i have some traditional site to site VPNS set up, im sure you know being a ccna...
you have to create a NAT exemption ACL
in my instance
10 permit ip 192.168.101.0 0.0.0.255 172.30.2.0 0.0.0.255 (171260 matches)
now with the router not knowing about the 101 network any more other than it as static route and everything sending out as 201 do i need to change that nat exemption to 201 from 101?
you have to create a NAT exemption ACL
in my instance
10 permit ip 192.168.101.0 0.0.0.255 172.30.2.0 0.0.0.255 (171260 matches)
now with the router not knowing about the 101 network any more other than it as static route and everything sending out as 201 do i need to change that nat exemption to 201 from 101?
In spite of the CCNA,...I don't "do" Cisco devices. That CCNA is back from 2006 and I have never touched one since then. The CCNA, at least back then, never covered those types of configs involving NAT anyway,...you had to go up to the CCNP to get that.
Everything I work with is HP Procurve and none of them run NAT,..they are just routers. The only firewall I am intimately familiar with is ISA/TMG. None of anything I work with even has any such thing as a "NAT Exemption",...so I have no idea,...I don't even know what Cisco means by that terminology.
Everything I work with is HP Procurve and none of them run NAT,..they are just routers. The only firewall I am intimately familiar with is ISA/TMG. None of anything I work with even has any such thing as a "NAT Exemption",...so I have no idea,...I don't even know what Cisco means by that terminology.
If you take that last diagram (or the one from my blog) to someone familiar enough with the Cisco products, they will know how to translate from the generic diagram into what a valid Cisco specific config would look like.
ASKER
did it on saturday, all up and working TMG now handles ALL traffic :)
still creating rules now though to make sure everything comes through! :)
Thanks Phil
Alex
still creating rules now though to make sure everything comes through! :)
Thanks Phil
Alex
Very good sir! Glad it all worked out.
Good work Phil :)
Thanks! I'm just a glutton for punishment I guess :-)