MySql Data Restore
I recently had to restore a backup and to say the least it went bad. I have missing records. I now have two tables one is a good backup of the originally lost data (loanFindingReplace) and a live table that has some, but not all of the original findings. I can not just replace the current live table (loanFinding) since I have had number entries since the restore. How is the easiest/quickest query to determine which records don't exist in the loanFinding table that do exist in the loanFindingReplace table and insert those into loanFinding? Both tables have the same fields with the same names. 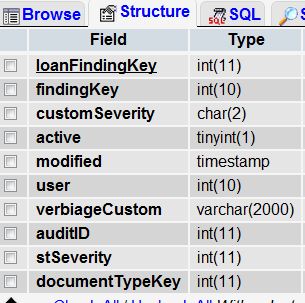
Thank you.
Thank you.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER