garconer
asked on
NTFRS Replication Problems
Hi Experts,
Our AD Domain has 6 sites and 12 DC's. For a long time nobody took a really good care over AD replication. Right now every DC has a different sysvol content from each other. And there are many "something_ntfrs_someid" folder, like this:
{CCA243A2-99E7-4FA1-9969-6
Yesterday I set burflags D4 in one of these DC and set the other with D2. NTFRS service restarted on all of them. Sysvol content were moved to NTFRS_PreExisting folder as expected. Before doing this procedure, I created a backup of entire sysvol folder on every Domain Controller.
After starting NTFRS service, replication begins. But some files are not being replicated and there are many folders being renamed as the example I put above as there were replication errors.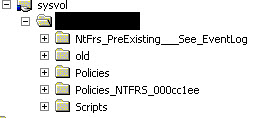
You can see the folders OLD and POLICIES_NTFRS_000cc1ee under c:\windows\sysvol\sysvol\m
I did manually deleted it all before setting D4 and D4 keys. How they came back again?
We are also have many folders under Scripts folder getting renamed because of replication collision as image below. How do I correct it?
How do I know from which DC a specific DC is getting its data to populate Sysvol content?
Can I just clear all sysvol content, then set D4 and D2 burflgs registry keys and then move back to sysvol folder only the files and folders needed?
Our AD Domain has 6 sites and 12 DC's. For a long time nobody took a really good care over AD replication. Right now every DC has a different sysvol content from each other. And there are many "something_ntfrs_someid" folder, like this:
{CCA243A2-99E7-4FA1-9969-6
Yesterday I set burflags D4 in one of these DC and set the other with D2. NTFRS service restarted on all of them. Sysvol content were moved to NTFRS_PreExisting folder as expected. Before doing this procedure, I created a backup of entire sysvol folder on every Domain Controller.
After starting NTFRS service, replication begins. But some files are not being replicated and there are many folders being renamed as the example I put above as there were replication errors.

You can see the folders OLD and POLICIES_NTFRS_000cc1ee under c:\windows\sysvol\sysvol\m
I did manually deleted it all before setting D4 and D4 keys. How they came back again?
We are also have many folders under Scripts folder getting renamed because of replication collision as image below. How do I correct it?
How do I know from which DC a specific DC is getting its data to populate Sysvol content?

Can I just clear all sysvol content, then set D4 and D2 burflgs registry keys and then move back to sysvol folder only the files and folders needed?
ASKER
Hi Mike,
Tks for the reply. Actually I've already done the instructions in the link you've sent. Folders keep being renamed and many folders and files are not being replicated among dcs. Each dc has dfrs links in place and eventvwr shows event 13568 followed by 13569 which is expected but unfortunately things are not working well. Do you know a tool that shows me from which dc some replicated folder came from?
Tks for the reply. Actually I've already done the instructions in the link you've sent. Folders keep being renamed and many folders and files are not being replicated among dcs. Each dc has dfrs links in place and eventvwr shows event 13568 followed by 13569 which is expected but unfortunately things are not working well. Do you know a tool that shows me from which dc some replicated folder came from?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
http://technet.microsoft.com/en-us/library/bb727056.aspx#ECAA
some places also refer to this as name collisions in sysvol.
Thanks
Mike