AymanOZ
asked on
Server Access Security
ASKER
I am so sorry for delay .
Dear Ujitnos its working... But if the user access first time he can access next time without password
so how I can make the password question every time try to access
Dear Ujitnos its working... But if the user access first time he can access next time without password
so how I can make the password question every time try to access
Go to
Configuration > Auth > Auth Servers > Local
and try the timeout options.
Configuration > Auth > Auth Servers > Local
and try the timeout options.
ASKER
Not working probably ......thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
i am late again!
ASKER
@ujitnos
no automatic command
no automatic command
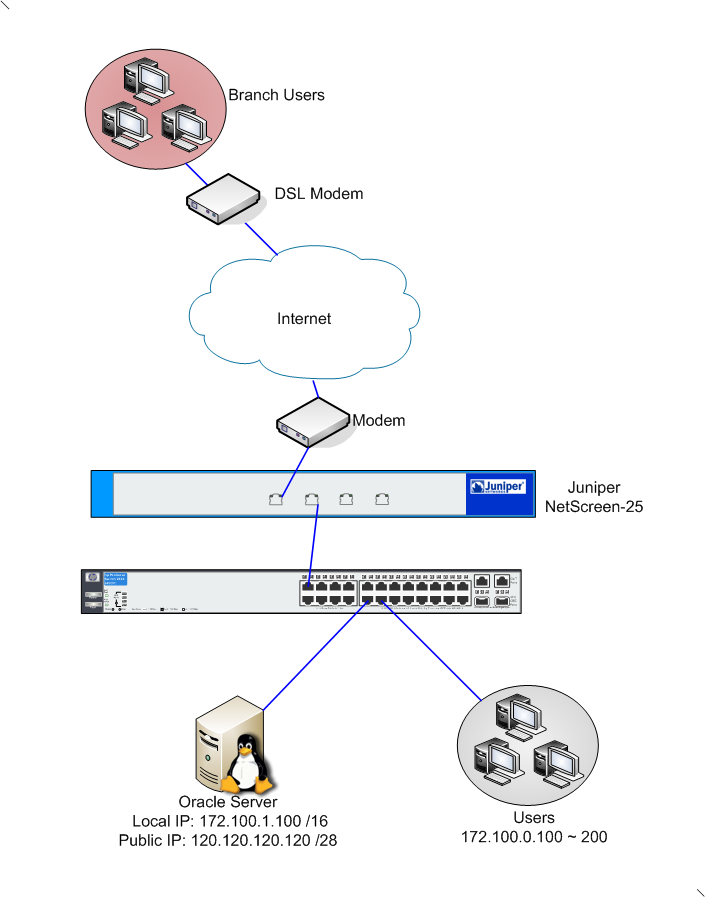
Suppose brach users want to access the oracle server, then create a rule in juniper;
Branch Zone to Oracle Zone --> Allow req port and in the advanced option select local authentication.
Now for this you will need to create local users in juniper. so when this rule is hit, user will be prompted for a username and password (from Juniper). once authenticated, traffic will continue to the oracle server, else it will be denied.