policy based routing problem
I need to come up with a way to route traffic around a content filter that is destined from my dmz to inside network and vice versa. Ive attached a network diagram. I have no experience with policy based routing. My first dive into PBR has not been successfull. Id appreciate it if you could provide me details / commands to make this happen. See diagram 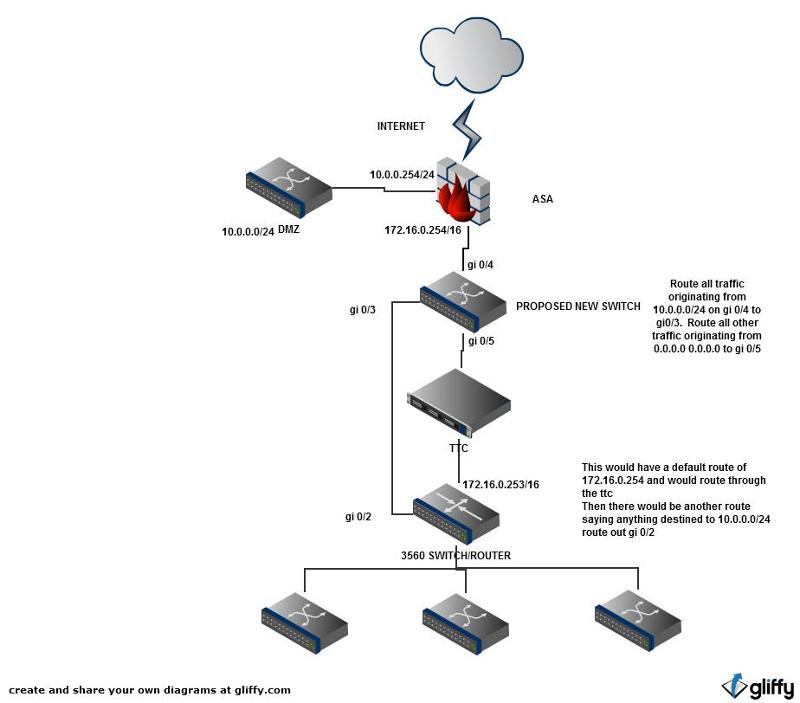

ASKER
Thanks donjohnston! Can you detail the commands for the top device? Would it also be possible to carve out two ports in the bottom switch that already exists to act as the second switch? Thanks!
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
The bottom switch is a 3560g switch. The top switch doesn't exist yet. That where I need to place another switch. Rather than purchasing another switch to go on the top, I was wondering if I could carve two ports in the bottom switch into a separate vlan that would act as the switch on the top. Make sense? Or do I need another physical switch? Sorry for the confusion. I just dont want to have to buy another switch if it's not necessary. Thanks again!
I noticed a slight problem.
The ASA interface and the bottom switch are on the same network. There is no routing. Which means that you can't solve this with PBR or any routing based solution as it is.
Think there are a couple of solutions.
1) Create an additional inside network on the ASA which bypasses the TC. Create an additional VLAN on the bottom switch to accommodate this network. Then you can use rules on the ASA and PBR on the 3560 to direct specific traffic around the TC.
2) Create three networks between the ASA and the networks on the bottom (those three switches at the very bottom). You could do this with the existing 3560 using VRFs. Then use PBR to direct the traffic accordingly.
The ASA interface and the bottom switch are on the same network. There is no routing. Which means that you can't solve this with PBR or any routing based solution as it is.
Think there are a couple of solutions.
1) Create an additional inside network on the ASA which bypasses the TC. Create an additional VLAN on the bottom switch to accommodate this network. Then you can use rules on the ASA and PBR on the 3560 to direct specific traffic around the TC.
2) Create three networks between the ASA and the networks on the bottom (those three switches at the very bottom). You could do this with the existing 3560 using VRFs. Then use PBR to direct the traffic accordingly.
You could create a static route on the bottom device that would route any traffic destined for 10.0.0.0/24 out the g0/2 interface.
Then on the top device, you would create a policy that routes any traffic from 10.0.0.0/24 out the g0/3 interface.
Do you need the commands?