SharePoint - "file corruption" for only a certain user, permissions issue
Here's the issue I'm having:
I have a Shartpoint site, containing a document library. The document library DOES NOT inherit permissions from the main site, on purpose, because there's one person who isn't a member of the main site who needs access to only this document library.
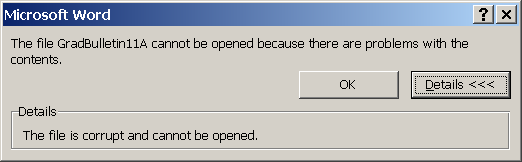
I have setup permissions accordingly. The uesr can get to the doc library when given a direct link. However, when she goes to open any Word file in the doc library, she gets the error message seen in the image. This happens on any computer she uses. The file is NOT corrupt, and opens fine otherwise.
I have found that the only way to make it so she can open the files is by giving her read-access to the root site...but, that's not an acceptable solution. In the root site, it shows she has "limited" access (access only to specific lists/libraries), and in the doc library itself, she has "Contribute" access. Even if I give her "Full Control" access to the doc library, it still won't let her look at the documents unless I give her access to the root site. Why?!?
I have a Shartpoint site, containing a document library. The document library DOES NOT inherit permissions from the main site, on purpose, because there's one person who isn't a member of the main site who needs access to only this document library.
I have setup permissions accordingly. The uesr can get to the doc library when given a direct link. However, when she goes to open any Word file in the doc library, she gets the error message seen in the image. This happens on any computer she uses. The file is NOT corrupt, and opens fine otherwise.

I have found that the only way to make it so she can open the files is by giving her read-access to the root site...but, that's not an acceptable solution. In the root site, it shows she has "limited" access (access only to specific lists/libraries), and in the doc library itself, she has "Contribute" access. Even if I give her "Full Control" access to the doc library, it still won't let her look at the documents unless I give her access to the root site. Why?!?
ASKER
This is Sharepoint 2007. Yes, we are using custom master pages.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
figured it out on my own
Are you by chance using a custom master page on your site?