Active Directory Best Practices Analyzer shows same 2 security errors on 3 out of our 4 domain controllers
As far as I can tell, we are having no problems, however when I run the Best Practices Analyzer for Active Directory Domain Services, 3 out of our 4 Domain Controllers all produce the following 2 errors:
Issue:
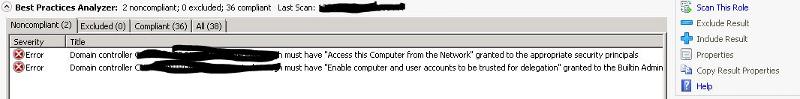
Domain Controller <name> does not have user right "Access this computer from the network" granted to 'Builtin Administrators', 'Enterprise Domain Controllers' or 'Authenticated Users', or has the user right "Deny access to this computer from the network" assigned to either of those groups or 'Everyone'.
Issue:
Domain controller <name> must have the "Enable computer and user accounts to be trusted for delegation" user right granted to the Builtin Administrators security group if domain controller <name> is used as a replication partner during a domain controller promotion.
I have reviewed the documentation on each issue, and confirmed that both the domain controller group policy and the local policy on each of our 4 DC's have the correct settings, and have confirmed that no where in any policy (that I can find) are there any deny policies for these settings.
Can anyone suggest any other reasons I might be getting these errors? Or someplace I might be forgetting to look for a deny policy?
Issue:
Domain Controller <name> does not have user right "Access this computer from the network" granted to 'Builtin Administrators', 'Enterprise Domain Controllers' or 'Authenticated Users', or has the user right "Deny access to this computer from the network" assigned to either of those groups or 'Everyone'.
Issue:
Domain controller <name> must have the "Enable computer and user accounts to be trusted for delegation" user right granted to the Builtin Administrators security group if domain controller <name> is used as a replication partner during a domain controller promotion.
I have reviewed the documentation on each issue, and confirmed that both the domain controller group policy and the local policy on each of our 4 DC's have the correct settings, and have confirmed that no where in any policy (that I can find) are there any deny policies for these settings.
Can anyone suggest any other reasons I might be getting these errors? Or someplace I might be forgetting to look for a deny policy?
ASKER
I get an indication that the update is not applicable to my system on all my DC's, which I'm assuming means it's already installed.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hmm...I had found an unkown SID in both of those settings on the local policy for these servers. Possibly in the group policy, but I can't recall. I removed it as it would probably have been migrated from our old domain. Using the steps in the link you provided, I removed all unkown SID's from all group and local policies for User Rights Assessment, but I still get the same 2 errors....I think we're on the right track though...
Not sure how many DCs you have but did you wait for replication to complete? and after you made the change to the GPO did you update the computer policy? you can run "gpupdate /force /target:computer"
ASKER
Ya, after I modified the GPO, I did a gpupdate /force, and I checked the local policy as well to make sure no more unknown SID's where listed. I also just checked again now, it's had pleanty of time to replicate....
Something I just noticed though...on the one DC that doesn't show the BPA errors (which happns to hold the FSMO roles, including PDC, if that makes a difference..), the local computer User Rights Assessment polices that are set by the Default Domain Controller GPO are locked and can't be changed, but on the other 3 that do have the BPA errors, they are not, all local User Rights Assessment polices are editable through gpedit. Could this indicate maybe a problem with GPO's being applied to the DC's?
Something I just noticed though...on the one DC that doesn't show the BPA errors (which happns to hold the FSMO roles, including PDC, if that makes a difference..), the local computer User Rights Assessment polices that are set by the Default Domain Controller GPO are locked and can't be changed, but on the other 3 that do have the BPA errors, they are not, all local User Rights Assessment polices are editable through gpedit. Could this indicate maybe a problem with GPO's being applied to the DC's?
Are all your DCs in the default "Domain Controllers" OU?
Do you have any secuirty filtering set in the GPOs?
if you run DCDIAG do you have any errors?
Run "repadmin /showrepl", are there any errors?
Do you have any secuirty filtering set in the GPOs?
if you run DCDIAG do you have any errors?
Run "repadmin /showrepl", are there any errors?
ASKER
Yes, all in the default OU, with the Default Domain Controllers GPO applied.
The Delegation looks weird though on Default Domain Controllers Policy, now that I look at it. I've included a screenshot. The first group looks custom, something one of the other guys must have added, I'll have to ask them about it on Monday, not sure what it's for, but let me know if it looks like something is missing.
DCDIAG shows that one of the DC's at our main site with the BPA error is not advertising as a time server, but that's it. The other two DC's at remote sites have more errors, I've attached txt file outputs. The one DC without the BPA errors has no DCDIAG errors.
repadmin /showrepl shows no errors from any DC's.
I also now have 3 new additional BPA errors on one of our remote DC's:
Issue:
The Active Directory Domain Services Best Practices Analyzer (AD DS BPA) is not able to collect data about applied Group Policy objects from the domain controller <Serverwithbpaerrors2>.
Issue:
The Active Directory Domain Services Best Practices Analyzer (AD DS BPA) is not able to collect data about the number of days since the last backup of the directory partition from the domain controller <Serverwithbpaerrors2>.
Issue:
The Active Directory Domain Services Best Practices Analyzer (AD DS BPA) is not able to collect data about the number of days since the last backup of the directory partition from the domain controller <Serverwithbpaerrors2>.
Capture.JPG
Serverwithbpaerrors2dcdiag.txt
Serverwithbpaerrors3dcdiag.txt
The Delegation looks weird though on Default Domain Controllers Policy, now that I look at it. I've included a screenshot. The first group looks custom, something one of the other guys must have added, I'll have to ask them about it on Monday, not sure what it's for, but let me know if it looks like something is missing.
DCDIAG shows that one of the DC's at our main site with the BPA error is not advertising as a time server, but that's it. The other two DC's at remote sites have more errors, I've attached txt file outputs. The one DC without the BPA errors has no DCDIAG errors.
repadmin /showrepl shows no errors from any DC's.
I also now have 3 new additional BPA errors on one of our remote DC's:
Issue:
The Active Directory Domain Services Best Practices Analyzer (AD DS BPA) is not able to collect data about applied Group Policy objects from the domain controller <Serverwithbpaerrors2>.
Issue:
The Active Directory Domain Services Best Practices Analyzer (AD DS BPA) is not able to collect data about the number of days since the last backup of the directory partition from the domain controller <Serverwithbpaerrors2>.
Issue:
The Active Directory Domain Services Best Practices Analyzer (AD DS BPA) is not able to collect data about the number of days since the last backup of the directory partition from the domain controller <Serverwithbpaerrors2>.
Capture.JPG
Serverwithbpaerrors2dcdiag.txt
Serverwithbpaerrors3dcdiag.txt
Are you running DCDIAG with a domain admin account?
How many DCs do you have?
Are all DCs pointing to internal DNS servers?
It looks like the DC may have lost the trust relationship with the other DCs. To fix this you can use netdom or just demoted and repromote.
How many DCs do you have?
Are all DCs pointing to internal DNS servers?
It looks like the DC may have lost the trust relationship with the other DCs. To fix this you can use netdom or just demoted and repromote.
ASKER
Yes, alsways with a domain admin account.
4 total. 2 at our main site, 1 at each of 2 other remote sites. 1 at the main site has no BPA errors, the others do.
Yes, all point at themselves for DNS. The two at the main site are also DNS servers, and each points at itself. The other two point at the main DC (that doesn't have the BPA errors) for primary dns, and the other as the secondary DNS.
Are you refering to the one with the addition BPA errors, and the more DCDIAG errors? I will try fixing it's trust, do you think that might be causing the BPA errors on the other servers?
4 total. 2 at our main site, 1 at each of 2 other remote sites. 1 at the main site has no BPA errors, the others do.
Yes, all point at themselves for DNS. The two at the main site are also DNS servers, and each points at itself. The other two point at the main DC (that doesn't have the BPA errors) for primary dns, and the other as the secondary DNS.
Are you refering to the one with the addition BPA errors, and the more DCDIAG errors? I will try fixing it's trust, do you think that might be causing the BPA errors on the other servers?
ASKER
I always forget the simple things. I just rebooted all three of the servers that were haveing the BPA errors, and now none of them have any BPA errors. I think we had it from the beginning, probably just removing the unkown SID's from the 2 specified policies did it, but Microsoft failed to mention 'and then reboot' in the resolution.
I still have some (most likely unrelated) DCDIAG issues to work out on the one DC, but the problem I set out to resolve is fixed. Thansk for your help!
I still have some (most likely unrelated) DCDIAG issues to work out on the one DC, but the problem I set out to resolve is fixed. Thansk for your help!
http://support.microsoft.com/kb/980360