mhentrich
asked on
Segmenting Cardholder Data to Assist in PCI Compliance
Experts,
Looking for experts on the PCI DSS today. I ran a question by our ASV Scanner folks and got some interesting information not too long ago, but I'm not entirely sure he/she understood the question and now I want to verify what I've learned.
Let's say I have an internal corporate network that contains, amongst other things, a SQL server. Let's also say that this SQL Server contains cardholder data. According to the PCI DSS, I now have to implement the wide array of requirements listed in the DSS on all of the systems in the internal network.
Now let's say I create a second SQL server, and set it on it's own, seperate network. I move the DB that contains the cardholder data onto that SQL server, and place a firewall between my new network and my old internal network (thereby creating two networks: the internal network and the network with cardholder data present). I open a few ports between the networks, such as 25 for SMTP and any others that are needed.
After all of this, do I still need to apply all of the PCI DSS standards to the original, internal network? Or do I have to apply the standards to just the new, cardholder data network?
For instance, DSS requirement 8.3 states: "Incorporate two-factor authentication for remote access (network-level access originating from outside the network) to the network by employees, administrators, and third parties." Does this requirement apply to my old, internal network if no cardholder data is stored there, with the proviso that there is a firewall between the internal network and the network that stores cardholder data?
I've attached an image to illustrate my Q. Thanks in advance for your help!
Regards,
Matt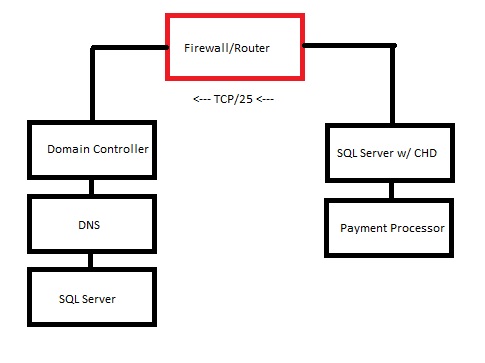
Looking for experts on the PCI DSS today. I ran a question by our ASV Scanner folks and got some interesting information not too long ago, but I'm not entirely sure he/she understood the question and now I want to verify what I've learned.
Let's say I have an internal corporate network that contains, amongst other things, a SQL server. Let's also say that this SQL Server contains cardholder data. According to the PCI DSS, I now have to implement the wide array of requirements listed in the DSS on all of the systems in the internal network.
Now let's say I create a second SQL server, and set it on it's own, seperate network. I move the DB that contains the cardholder data onto that SQL server, and place a firewall between my new network and my old internal network (thereby creating two networks: the internal network and the network with cardholder data present). I open a few ports between the networks, such as 25 for SMTP and any others that are needed.
After all of this, do I still need to apply all of the PCI DSS standards to the original, internal network? Or do I have to apply the standards to just the new, cardholder data network?
For instance, DSS requirement 8.3 states: "Incorporate two-factor authentication for remote access (network-level access originating from outside the network) to the network by employees, administrators, and third parties." Does this requirement apply to my old, internal network if no cardholder data is stored there, with the proviso that there is a firewall between the internal network and the network that stores cardholder data?
I've attached an image to illustrate my Q. Thanks in advance for your help!
Regards,
Matt

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
The short answer is you open what you need but nothing else. Anything you have open should be monitored, and if there's a risk, you need to mitigate the risk as much as possible, whether that's the web-app firewall, IDS, etc.
ASKER
Perfect, thanks so much!!
ASKER
Excellent, thanks! That's what I was told, and I'm very glad to hear it. We do have a Barracuda web-app firewall in our DMZ already, so we've got a head start there. Most of our credit card orders come in over the phone and are run through a payment processing application, so that is where most of my headache will be.
Let me ask you this: the DSS aren't very specific regarding which ports I can open before I'm creating a security gap. My thoughts are that I would open SMTP ports, DNS ports, SMB ports, and SQL ports. Is that too much, or I can I still consider the cardholder environment seperate and secure with those ports open?
Thanks!!
Matt