Access DFS from different subnet, same domain.
Computers are in the same Domain, same physical site, Site IP subnets 10.1.1.0/24 Second IP subnet 10.1.2.0/24 DHCP scope are on the same server.
Clients on subnet 10.1.2.0/24 Cannont access the DFS share path, but clients on 10.1.1.x/24 CAN access the DFS share with no problems at all.
Clients from 10.1.2.x can ping everything on 10.1.1.0
Any ideas of what may be going on?
Best regards to all the Pros, life will be more difficult for me without your tech support.
Clients on subnet 10.1.2.0/24 Cannont access the DFS share path, but clients on 10.1.1.x/24 CAN access the DFS share with no problems at all.
Clients from 10.1.2.x can ping everything on 10.1.1.0
Any ideas of what may be going on?
Best regards to all the Pros, life will be more difficult for me without your tech support.
ASKER
What are these 445/137/139 exactly for?
ASKER
You have to make sure that you have a routing path between the segments
What is the device to which is segment connected (router/firewall)? Firewall.
What IP does the server with the SHARE has and what is the DC's IP?
Answer: Server Share IP. 10.1.1.94 DC's IP 10.1.1.254 and 10.1.1.253
Ping is one thing does a system on 10.1.2.x telnet to 10.1.1.x 445/137/139?
How should I do this, I'm confused with the syntax to use.
You may have a rule that does not allow this traffic through while the clients on the 10.1.1.x see the DFS as local and send the request directly versus going through the router.
(this I need to find out, I'm a bit familiar with Cisco, but do you know of a Command I can use?
What is the device to which is segment connected (router/firewall)? Firewall.
What IP does the server with the SHARE has and what is the DC's IP?
Answer: Server Share IP. 10.1.1.94 DC's IP 10.1.1.254 and 10.1.1.253
Ping is one thing does a system on 10.1.2.x telnet to 10.1.1.x 445/137/139?
How should I do this, I'm confused with the syntax to use.
You may have a rule that does not allow this traffic through while the clients on the 10.1.1.x see the DFS as local and send the request directly versus going through the router.
(this I need to find out, I'm a bit familiar with Cisco, but do you know of a Command I can use?
445, 137,139 are the MS ports used for file sharing.
Brand of firewall and what configurations on the firewall do you have to allow one segment to access the other segment.
i.e.
10.1.1.0/24
/
firewall
\ 10.1.2.0/24
if the server is on the same segment as the 10.1.1.0 or a completely different third segment?
If on the same 10.1.1.0 the traffic stays within the switch and never hits the firewall (local traffic)
For the 10.1.2.x segment to reach 10.1.1.x it has to go through the firewall where the inter segment rules will apply i.e. do you have a rule that says that any packet from 10.1.2.0/24 can hit 10.1.1.0/24 and the same in reverse so when a packet from 10.1.2.x makes it to the 10.1.1.x the response will have a path back?
Brand of firewall and what configurations on the firewall do you have to allow one segment to access the other segment.
i.e.
10.1.1.0/24
/
firewall
\ 10.1.2.0/24
if the server is on the same segment as the 10.1.1.0 or a completely different third segment?
If on the same 10.1.1.0 the traffic stays within the switch and never hits the firewall (local traffic)
For the 10.1.2.x segment to reach 10.1.1.x it has to go through the firewall where the inter segment rules will apply i.e. do you have a rule that says that any packet from 10.1.2.0/24 can hit 10.1.1.0/24 and the same in reverse so when a packet from 10.1.2.x makes it to the 10.1.1.x the response will have a path back?
ASKER
Arnold, I made a mistake previously when you asked "What is the device to which is segment connected (router/firewall)? I said Firewall, the fact is that is a L3 switch. And here's it configuration.
CoreSwitch-3560>en
CoreSwitch-3560#sh run
Building configuration...
Current configuration : 5747 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
service password-encryption
!
hostname CoreSwitch-3560
!
boot-start-marker
boot-end-marker
!
enable secret 5 $6.$Jn6cP99998OVytU.jVbG//
!
no aaa new-model
system mtu routing 1500
ip subnet-zero
ip routing
!
!
!
!
crypto pki trustpoint TP-self-signed-1452456
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certifi
revocation-check none
rsakeypair TP-self-signed-1652538779
!
!
crypto pki certificate chain TP-self-signed-1432534656
certificate self-signed 01
30820247 308201B0 A0030201 02020101 300D0609 2A864886
31312F30 2D060355 04031326 494F532D 53656C66 2D536967
69666963 6174652D 31343332170D3933 30333031 30303031
33315A17 0D323030 31303130 30303030 305A3031 312F302D
4F532D53 656C662D 5369676E 65642D43 65727469 66696361
33343635 3630819F 300D0609 2A864886 F70D0101 01050003
8100F314 2B09B6AD 16D4E910 F2F93951 24921EF7818D0030
79F1F4B2 8914DF45 1342F5C4 4267CF87 BE60B00B 3943EA30
16B3CB85 D80EE5B6 9D64B498 9597F0CD 2BFC3270 AC4EBB4D
B8C5A79E 305C1940 ADE94F20 EEB0E382 0C6A67C4 90683C06
EE3F0203 010001A3 6F306D30 FF040530 030101FF 301A060
551D1104 13301182 0F4C4159 432D436F 72652D33 3536302E
18301680 14E739BA C43BD286 F4302435 05A9C81E E3E89A2C
04160414 E739BAC4 3BD286F4 30243505 A9C81EE3 E89A2C56
F70D0101 04050003 DC73F4B7 87D1CFA2 01019F6A 2362247C
0E73AEB0 DAE42AFA 0BE17452 4A126A32 A6C0D782 3068752E
358C419C 3E619593 68F0C93A 9947A96A 42920030 1B981D9C
69426A79 A20943A4 FACFC34F 3B231760 B7AA96E9 24ECC01D
quit
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface GigabitEthernet0/1
description Uplink to FW
no switchport
ip address 10.1.0.2 255.255.255.0
!
interface GigabitEthernet0/2
description IT-ServerSw
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/3
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/5
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/16
!
interface GigabitEthernet0/17
!
interface GigabitEthernet0/18
!
interface GigabitEthernet0/19
description Uplink to Class-Lab-3550
switchport access vlan 100
switchport mode access
!
interface GigabitEthernet0/20
description Uplink to HQs-Srvr-3560
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/21
description Uplink to Switch-Dist3-2950
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/22
description Uplink to Switch-Dist2-2950
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/23
description Uplink to Switch-Dist1-2950
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/24
!
interface GigabitEthernet0/25
!
interface GigabitEthernet0/26
!
interface GigabitEthernet0/27
!
interface GigabitEthernet0/28
!
interface Vlan1
ip address 10.1.1.1 255.255.255.0
!
interface Vlan2
description Staff-VLAN2
ip address 10.1.2.1 255.255.255.0
ip helper-address 10.1.1.254
ip helper-address 10.1.1.253
!
interface Vlan100
description labs
ip address 10.1.100.1 255.255.255.0
ip access-group 100 in
!
interface Vlan172
description ITVLAN
ip address 172.16.1.1 255.255.255.0
!
router ospf 1
router-id 10.1.1.1
log-adjacency-changes
network 10.1.0.0 0.0.0.255 area 0
network 10.1.1.1 0.0.0.0 area 0
network 10.1.2.1 0.0.0.0 area 0
network 10.1.100.1 0.0.0.0 area 0
network 10.1.250.2 0.0.0.0 area 0
network 172.16.1.1 0.0.0.0 area 0
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.1.0.1
ip http server
ip http secure-server
!
!
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.234 eq www
access-list 100 permit udp 10.1.100.0 0.0.0.255 host 10.1.1.254 eq domain
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.254 eq domain
access-list 100 permit udp 10.1.100.0 0.0.0.255 any eq domain
access-list 100 permit tcp 10.1.100.0 0.0.0.255 any eq domain
access-list 100 permit udp 10.1.100.0 0.0.0.255 host 10.1.1.254 eq bootpc
access-list 100 permit tcp host 10.1.100.2 10.1.0.0 0.0.255.255 eq telnet
access-list 100 permit icmp host 10.1.100.2 10.1.0.0 0.0.255.255 echo-reply
access-list 100 permit tcp host 10.1.100.2 eq telnet 10.1.0.0 0.0.255.255
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.251 eq smtp
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.251 eq www
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.251 eq 443
access-list 100 permit tcp 10.1.100.0 0.0.0.255 172.16.1.0 0.0.0.255 established
access-list 100 deny ip 10.1.100.0 0.0.0.255 10.1.0.0 0.0.255.255
access-list 100 permit ip any any
!
control-plane
!
!
line con 0
length 20
line vty 0 4
pass 7 8090317050D0A2D
login local
line vty 5
pass 7 044A1E0C0B161C0C0
login
line vty 6 15
login
!
end
CoreSwitch-3560#
CoreSwitch-3560>en
CoreSwitch-3560#sh run
Building configuration...
Current configuration : 5747 bytes
!
version 12.2
no service pad
service timestamps debug uptime
service timestamps log uptime
service password-encryption
!
hostname CoreSwitch-3560
!
boot-start-marker
boot-end-marker
!
enable secret 5 $6.$Jn6cP99998OVytU.jVbG//
!
no aaa new-model
system mtu routing 1500
ip subnet-zero
ip routing
!
!
!
!
crypto pki trustpoint TP-self-signed-1452456
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certifi
revocation-check none
rsakeypair TP-self-signed-1652538779
!
!
crypto pki certificate chain TP-self-signed-1432534656
certificate self-signed 01
30820247 308201B0 A0030201 02020101 300D0609 2A864886
31312F30 2D060355 04031326 494F532D 53656C66 2D536967
69666963 6174652D 31343332170D3933 30333031 30303031
33315A17 0D323030 31303130 30303030 305A3031 312F302D
4F532D53 656C662D 5369676E 65642D43 65727469 66696361
33343635 3630819F 300D0609 2A864886 F70D0101 01050003
8100F314 2B09B6AD 16D4E910 F2F93951 24921EF7818D0030
79F1F4B2 8914DF45 1342F5C4 4267CF87 BE60B00B 3943EA30
16B3CB85 D80EE5B6 9D64B498 9597F0CD 2BFC3270 AC4EBB4D
B8C5A79E 305C1940 ADE94F20 EEB0E382 0C6A67C4 90683C06
EE3F0203 010001A3 6F306D30 FF040530 030101FF 301A060
551D1104 13301182 0F4C4159 432D436F 72652D33 3536302E
18301680 14E739BA C43BD286 F4302435 05A9C81E E3E89A2C
04160414 E739BAC4 3BD286F4 30243505 A9C81EE3 E89A2C56
F70D0101 04050003 DC73F4B7 87D1CFA2 01019F6A 2362247C
0E73AEB0 DAE42AFA 0BE17452 4A126A32 A6C0D782 3068752E
358C419C 3E619593 68F0C93A 9947A96A 42920030 1B981D9C
69426A79 A20943A4 FACFC34F 3B231760 B7AA96E9 24ECC01D
quit
!
!
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
interface GigabitEthernet0/1
description Uplink to FW
no switchport
ip address 10.1.0.2 255.255.255.0
!
interface GigabitEthernet0/2
description IT-ServerSw
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/3
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/5
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/16
!
interface GigabitEthernet0/17
!
interface GigabitEthernet0/18
!
interface GigabitEthernet0/19
description Uplink to Class-Lab-3550
switchport access vlan 100
switchport mode access
!
interface GigabitEthernet0/20
description Uplink to HQs-Srvr-3560
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/21
description Uplink to Switch-Dist3-2950
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/22
description Uplink to Switch-Dist2-2950
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/23
description Uplink to Switch-Dist1-2950
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/24
!
interface GigabitEthernet0/25
!
interface GigabitEthernet0/26
!
interface GigabitEthernet0/27
!
interface GigabitEthernet0/28
!
interface Vlan1
ip address 10.1.1.1 255.255.255.0
!
interface Vlan2
description Staff-VLAN2
ip address 10.1.2.1 255.255.255.0
ip helper-address 10.1.1.254
ip helper-address 10.1.1.253
!
interface Vlan100
description labs
ip address 10.1.100.1 255.255.255.0
ip access-group 100 in
!
interface Vlan172
description ITVLAN
ip address 172.16.1.1 255.255.255.0
!
router ospf 1
router-id 10.1.1.1
log-adjacency-changes
network 10.1.0.0 0.0.0.255 area 0
network 10.1.1.1 0.0.0.0 area 0
network 10.1.2.1 0.0.0.0 area 0
network 10.1.100.1 0.0.0.0 area 0
network 10.1.250.2 0.0.0.0 area 0
network 172.16.1.1 0.0.0.0 area 0
!
ip classless
ip route 0.0.0.0 0.0.0.0 10.1.0.1
ip http server
ip http secure-server
!
!
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.234 eq www
access-list 100 permit udp 10.1.100.0 0.0.0.255 host 10.1.1.254 eq domain
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.254 eq domain
access-list 100 permit udp 10.1.100.0 0.0.0.255 any eq domain
access-list 100 permit tcp 10.1.100.0 0.0.0.255 any eq domain
access-list 100 permit udp 10.1.100.0 0.0.0.255 host 10.1.1.254 eq bootpc
access-list 100 permit tcp host 10.1.100.2 10.1.0.0 0.0.255.255 eq telnet
access-list 100 permit icmp host 10.1.100.2 10.1.0.0 0.0.255.255 echo-reply
access-list 100 permit tcp host 10.1.100.2 eq telnet 10.1.0.0 0.0.255.255
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.251 eq smtp
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.251 eq www
access-list 100 permit tcp 10.1.100.0 0.0.0.255 host 10.1.1.251 eq 443
access-list 100 permit tcp 10.1.100.0 0.0.0.255 172.16.1.0 0.0.0.255 established
access-list 100 deny ip 10.1.100.0 0.0.0.255 10.1.0.0 0.0.255.255
access-list 100 permit ip any any
!
control-plane
!
!
line con 0
length 20
line vty 0 4
pass 7 8090317050D0A2D
login local
line vty 5
pass 7 044A1E0C0B161C0C0
login
line vty 6 15
login
!
end
CoreSwitch-3560#
What is the IP/netmask and default gateway that gets set to a system with IP 10.1.2.x?
upstream from this switch is a router?
upstream from this switch is a router?
ASKER
What is the IP/netmask and default gateway that gets set to a system with IP 10.1.2.x?
Answer: 10.1.2.x/24 default gateway: 10.1.2.1
Upstream device is a Firewall.
Answer: 10.1.2.x/24 default gateway: 10.1.2.1
Upstream device is a Firewall.
ASKER
And strange enough I can access the DFS share when connected remotely via Cisco VPN from home.
What are the rules on the firewall when an system from 10.1.2.x tries to access 10.1.1.x system?
You likely have a rule for the IPSEC/vpn to allow access to the 10.1.1.x segment so comparing the behavior of communications between two VLANs and access from the VPN is not something you can compare given that you've configured the VPN policy so that the VPN user can access the share.
Check the ASA to see what happens to a packet from 10.1.2.x to 10.1.1.x?
Debug the traffic with source 10.1.2.0/24 and destination 10.1.1.0/24 as well as source 10.1.1.0/24 and destination 10.1.2.0/24 and try to access a share when the debug is on.
Your issue is on the ASA firewall. This is where you need to add a rule to allow 10.1.2.0/24 access to 10.1.1.0/24 and the reverse or at least established traffic to go back and forth.
You likely have a rule for the IPSEC/vpn to allow access to the 10.1.1.x segment so comparing the behavior of communications between two VLANs and access from the VPN is not something you can compare given that you've configured the VPN policy so that the VPN user can access the share.
Check the ASA to see what happens to a packet from 10.1.2.x to 10.1.1.x?
Debug the traffic with source 10.1.2.0/24 and destination 10.1.1.0/24 as well as source 10.1.1.0/24 and destination 10.1.2.0/24 and try to access a share when the debug is on.
Your issue is on the ASA firewall. This is where you need to add a rule to allow 10.1.2.0/24 access to 10.1.1.0/24 and the reverse or at least established traffic to go back and forth.
ASKER
Will give a shot to the last comment, will keep you posted.
ASKER
Can you take a look at our Fwall config file? It's not an ASA it's a Pix 515E
Result of the command: "show running-config"
: Saved
:
PIX Version 7.2(2)
!
hostname productionpix
domain-name
enable password wl11000000EaEFr encrypted
no names
name 10.1.1.0 main_office
name 10.13.1.0 lang-Site
name 10.100.1.0 ldm
name 10.14.1.0 gh-Site description House
name 10.16.1.0 River
name 10.17.1.0 ssm
name 10.12.1.0 FC
name 10.1.1.234 web
name 10.1.1.231 barracuda
name 10.1.1.251 exchange
name 10.18.1.0 Woodner
name 10.19.1.0 WIre description WIrE Net
dns-guard
!
interface Ethernet0
nameif outside
security-level 0
ip address xx.510.95.000 255.255.255.248
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.1.0.1 255.255.255.0
!
passwd aFt9xxxxx3mp6IJ encrypted
boot system flash:/image.bin
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns server-group DefaultDNS
domain-name mydom.org
object-group network mydom_gh
description girls house
network-object 10.14.1.0 255.255.255.0
object-group network Postini
network-object 64.18.0.0 255.255.240.0
object-group network sstr
network-object 10.17.1.0 255.255.255.0
object-group network lang-Site
network-object 10.13.1.0 255.255.255.0
object-group network ldm
network-object 10.100.1.0 255.255.255.0
object-group network river
network-object 10.16.1.0 255.255.255.0
object-group network lang-Site
network-object 10.200.1.0 255.255.255.0
object-group network HQ-to-Wire-Grp
network-object 10.1.1.0 255.255.255.0
network-object 10.1.2.0 255.255.255.0
object-group network HQ_VLAN2
network-object 10.1.2.0 255.255.255.0
access-list outside_access_in extended permit tcp any host xx.xxx.xx.xxx eq https
access-list outside_access_in extended permit tcp any host xx.xxx.xx.xxx eq www
access-list outside_access_in extended permit tcp any host xx.xxx.xx.xxx eq smtp
access-list outside_access_in extended permit icmp host xx.xxx.xx.xxx any echo-reply
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.12.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.100.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.1.7.192 255.255.255.192
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.14.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.16.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.17.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.255.0 10.12.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.200.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.20.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.1.0 255.255.255.0 10.13.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.18.1.0 255.255.255.0
access-list inside_outbound_nat0_acl remark To Dan and Matt
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.19.1.0 255.255.255.0
access-list outside_220_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.12.1.0 255.255.255.0
access-list outside_cryptomap_60 extended permit ip 10.1.0.0 255.255.0.0 10.100.1.0 255.255.255.0
access-list outside_320_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.13.1.0 255.255.255.0
access-list tunnel_splitTunnelAcl extended permit ip 10.1.0.0 255.255.255.0 any
access-list outside_100_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.14.1.0 255.255.255.0
access-list outside_120_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list outside_nat0_outbound extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list outside_260_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.10.0 255.255.255.0
access-list outside_140_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.16.1.0 255.255.255.0
access-list outside_160_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.17.1.0 255.255.255.0
access-list outside_cryptomap_65535.20
access-list split_tunnel_list standard permit 10.1.0.0 255.255.0.0
access-list outside_240_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.10.0 255.255.255.0
access-list outside_280_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.200.1.0 255.255.255.0
access-list outside_300_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.13.1.0 255.255.255.0
access-list outside_300_cryptomap_1 extended permit ip 10.1.0.0 255.255.0.0 10.20.1.0 255.255.255.0
access-list outside_320_cryptomap_1 extended permit ip 10.1.1.0 255.255.255.0 10.13.1.0 255.255.255.0
access-list outside_340_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.18.1.0 255.255.255.0
access-list inside_access_in extended permit ip any any
access-list outside_360_cryptomap remark To DanMatt 2555 14th
access-list outside_360_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list outside_380_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.10.0 255.255.255.0
access-list outside_380_cryptomap_1 extended permit ip 10.1.0.0 255.255.0.0 10.19.1.0 255.255.255.0
pager lines 24
logging enable
logging timestamp
logging monitor alerts
logging trap debugging
logging asdm critical
logging host inside 10.1.1.21
logging debug-trace
mtu outside 1500
mtu inside 1500
ip local pool VPN_remote 10.1.7.200-10.1.7.250
ip verify reverse-path interface outside
ip verify reverse-path interface inside
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
asdm image flash:/asdm
asdm history enable
arp timeout 14400
nat-control
global (outside) 10 interface
nat (outside) 0 access-list outside_nat0_outbound
nat (inside) 0 access-list inside_outbound_nat0_acl
nat (inside) 10 0.0.0.0 0.0.0.0
static (inside,outside) xx.xxx.xx.xxx 10.1.1.234 netmask 255.255.255.255
static (inside,outside) xx.xxx.xx.xxx 10.1.1.251 netmask 255.255.255.255
static (inside,outside) xx.xxx.xx.xxx 10.1.1.231 netmask 255.255.255.255
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
route outside 0.0.0.0 0.0.0.0 xx.xxx.xx.xxx 1
route inside 10.1.0.0 255.255.0.0 10.1.0.2 1
route inside 172.16.1.0 255.255.255.0 10.1.0.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
group-policy DfltGrpPolicy attributes
banner none
wins-server none
dns-server none
dhcp-network-scope none
vpn-access-hours none
vpn-simultaneous-
vpn-idle-timeout 30
vpn-session-timeout none
vpn-filter none
vpn-tunnel-protocol IPSec l2tp-ipsec
password-storage
ip-comp disable
re-xauth disable
group-lock none
pfs disable
ipsec-udp disable
ipsec-udp-port 10000
split-tunnel-policy tunnelall
split-tunnel-network-list none
default-domain none
split-dns none
intercept-dhcp 255.255.255.255 disable
secure-unit-authentication
user-authentication disable
user-authentication-idle-t
ip-phone-bypass disable
leap-bypass disable
nem disable
backup-servers keep-client-config
msie-proxy server none
msie-proxy method no-modify
msie-proxy except-list none
msie-proxy local-bypass disable
nac disable
nac-sq-period 300
nac-reval-period 36000
nac-default-acl none
address-pools none
client-firewall
client-access-
group-policy Groups internal
group-policy Groups attributes
wins-server value 10.1.1.253
dns-server value 10.1.1.253
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split_tunnel_list
username xxxxx password 8jBjTxxxx1223pM encrypted privilege 15
username cxxxxx password enn5xxxseefT8HL encrypted privilege 15
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
aaa authentication enable console LOCAL
aaa authentication telnet console LOCAL
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server community public
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto dynamic-map outside_dyn_map 20 match address outside_cryptomap_65535.20
crypto dynamic-map outside_dyn_map 20 set pfs
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 60 match address outside_cryptomap_60
crypto map outside_map 60 set peer xx.xxx.xxx.xx
crypto map outside_map 60 set transform-set ESP-DES-MD5
crypto map outside_map 100 match address outside_100_cryptomap
crypto map outside_map 100 set pfs
crypto map outside_map 100 set peer xx.xx.xxx.xxx
crypto map outside_map 100 set transform-set ESP-3DES-MD5
crypto map outside_map 140 match address outside_140_cryptomap
crypto map outside_map 140 set pfs
crypto map outside_map 140 set peer xx.xx.xxx.x
crypto map outside_map 140 set transform-set ESP-3DES-MD5
crypto map outside_map 160 match address outside_160_cryptomap
crypto map outside_map 160 set pfs
crypto map outside_map 160 set peer xx.xxx.xxx.x
crypto map outside_map 160 set transform-set ESP-3DES-MD5
crypto map outside_map 220 match address outside_220_cryptomap
crypto map outside_map 220 set pfs
crypto map outside_map 220 set peer xxx.xx.xxx.xxx
crypto map outside_map 220 set transform-set ESP-3DES-MD5
crypto map outside_map 260 match address outside_260_cryptomap
crypto map outside_map 260 set pfs
crypto map outside_map 260 set peer xxx.xx.xxx.xx
crypto map outside_map 260 set transform-set ESP-3DES-MD5
crypto map outside_map 280 match address outside_280_cryptomap
crypto map outside_map 280 set pfs
crypto map outside_map 280 set peer xx.xxx.xx.xx
crypto map outside_map 280 set transform-set ESP-3DES-SHA
crypto map outside_map 300 match address outside_300_cryptomap_1
crypto map outside_map 300 set pfs
crypto map outside_map 300 set peer xxx.xx.xxx.xxx
crypto map outside_map 300 set transform-set ESP-3DES-SHA
crypto map outside_map 320 match address outside_320_cryptomap_1
crypto map outside_map 320 set pfs
crypto map outside_map 320 set peer xx.xx.xxx.xx
crypto map outside_map 320 set transform-set ESP-3DES-SHA
crypto map outside_map 340 match address outside_340_cryptomap
crypto map outside_map 340 set pfs
crypto map outside_map 340 set peer xxx.xx.xxx.xxx
crypto map outside_map 340 set transform-set ESP-3DES-MD5
crypto map outside_map 360 match address outside_360_cryptomap
crypto map outside_map 360 set pfs
crypto map outside_map 360 set peer xx.xx.xxx.xxx
crypto map outside_map 360 set transform-set ESP-3DES-MD5
crypto map outside_map 380 match address outside_380_cryptomap_1
crypto map outside_map 380 set pfs
crypto map outside_map 380 set peer xxx.xxx.xxx.xxx
crypto map outside_map 380 set transform-set ESP-3DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto ca trustpoint prod-pix
enrollment self
crl configure
crypto isakmp identity hostname
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
crypto isakmp policy 30
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 20
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key **
tunnel-group DM type ipsec-l2l
tunnel-group DM ipsec-attributes
pre-shared-key **
tunnel-group xxxx type ipsec-ra
tunnel-group xxxx general-attributes
address-pool VPN_remote
default-group-policy vPN
tunnel-group Groups ipsec-attributes
pre-shared-key **
isakmp ikev1-user-authentication none
tunnel-group xx.xx.xx.x type ipsec-l2l
tunnel-group xx.xxx.xxx.x ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xx.xx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group Wards type ipsec-l2l
tunnel-group Wards ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key ******
telnet 10.1.0.1 255.255.255.255 inside
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 outside
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 20
console timeout 0
management-access inside
dhcpd ping_timeout 750
!
dhcpd address 10.1.0.200-10.1.0.250 inside
dhcpd dns 10.1.1.1 interface inside
!
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
ssl encryption des-sha1 rc4-md5
prompt hostname context
Cryptochecksum:c38f6xxxx3f
: end
Result of the command: "show running-config"
: Saved
:
PIX Version 7.2(2)
!
hostname productionpix
domain-name
enable password wl11000000EaEFr encrypted
no names
name 10.1.1.0 main_office
name 10.13.1.0 lang-Site
name 10.100.1.0 ldm
name 10.14.1.0 gh-Site description House
name 10.16.1.0 River
name 10.17.1.0 ssm
name 10.12.1.0 FC
name 10.1.1.234 web
name 10.1.1.231 barracuda
name 10.1.1.251 exchange
name 10.18.1.0 Woodner
name 10.19.1.0 WIre description WIrE Net
dns-guard
!
interface Ethernet0
nameif outside
security-level 0
ip address xx.510.95.000 255.255.255.248
!
interface Ethernet1
nameif inside
security-level 100
ip address 10.1.0.1 255.255.255.0
!
passwd aFt9xxxxx3mp6IJ encrypted
boot system flash:/image.bin
ftp mode passive
clock timezone EST -5
clock summer-time EDT recurring
dns server-group DefaultDNS
domain-name mydom.org
object-group network mydom_gh
description girls house
network-object 10.14.1.0 255.255.255.0
object-group network Postini
network-object 64.18.0.0 255.255.240.0
object-group network sstr
network-object 10.17.1.0 255.255.255.0
object-group network lang-Site
network-object 10.13.1.0 255.255.255.0
object-group network ldm
network-object 10.100.1.0 255.255.255.0
object-group network river
network-object 10.16.1.0 255.255.255.0
object-group network lang-Site
network-object 10.200.1.0 255.255.255.0
object-group network HQ-to-Wire-Grp
network-object 10.1.1.0 255.255.255.0
network-object 10.1.2.0 255.255.255.0
object-group network HQ_VLAN2
network-object 10.1.2.0 255.255.255.0
access-list outside_access_in extended permit tcp any host xx.xxx.xx.xxx eq https
access-list outside_access_in extended permit tcp any host xx.xxx.xx.xxx eq www
access-list outside_access_in extended permit tcp any host xx.xxx.xx.xxx eq smtp
access-list outside_access_in extended permit icmp host xx.xxx.xx.xxx any echo-reply
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.12.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.100.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.1.7.192 255.255.255.192
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.14.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.16.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.17.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.255.0 10.12.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.200.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.20.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.1.0 255.255.255.0 10.13.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.18.1.0 255.255.255.0
access-list inside_outbound_nat0_acl remark To Dan and Matt
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list inside_outbound_nat0_acl extended permit ip 10.1.0.0 255.255.0.0 10.19.1.0 255.255.255.0
access-list outside_220_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.12.1.0 255.255.255.0
access-list outside_cryptomap_60 extended permit ip 10.1.0.0 255.255.0.0 10.100.1.0 255.255.255.0
access-list outside_320_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.13.1.0 255.255.255.0
access-list tunnel_splitTunnelAcl extended permit ip 10.1.0.0 255.255.255.0 any
access-list outside_100_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.14.1.0 255.255.255.0
access-list outside_120_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list outside_nat0_outbound extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list outside_260_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.10.0 255.255.255.0
access-list outside_140_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.16.1.0 255.255.255.0
access-list outside_160_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.17.1.0 255.255.255.0
access-list outside_cryptomap_65535.20
access-list split_tunnel_list standard permit 10.1.0.0 255.255.0.0
access-list outside_240_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.10.0 255.255.255.0
access-list outside_280_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.200.1.0 255.255.255.0
access-list outside_300_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.13.1.0 255.255.255.0
access-list outside_300_cryptomap_1 extended permit ip 10.1.0.0 255.255.0.0 10.20.1.0 255.255.255.0
access-list outside_320_cryptomap_1 extended permit ip 10.1.1.0 255.255.255.0 10.13.1.0 255.255.255.0
access-list outside_340_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.18.1.0 255.255.255.0
access-list inside_access_in extended permit ip any any
access-list outside_360_cryptomap remark To DanMatt 2555 14th
access-list outside_360_cryptomap extended permit ip 10.1.0.0 255.255.0.0 10.15.1.0 255.255.255.0
access-list outside_380_cryptomap extended permit ip 10.1.1.0 255.255.255.0 10.1.10.0 255.255.255.0
access-list outside_380_cryptomap_1 extended permit ip 10.1.0.0 255.255.0.0 10.19.1.0 255.255.255.0
pager lines 24
logging enable
logging timestamp
logging monitor alerts
logging trap debugging
logging asdm critical
logging host inside 10.1.1.21
logging debug-trace
mtu outside 1500
mtu inside 1500
ip local pool VPN_remote 10.1.7.200-10.1.7.250
ip verify reverse-path interface outside
ip verify reverse-path interface inside
icmp unreachable rate-limit 1 burst-size 1
icmp permit any outside
icmp permit any inside
asdm image flash:/asdm
asdm history enable
arp timeout 14400
nat-control
global (outside) 10 interface
nat (outside) 0 access-list outside_nat0_outbound
nat (inside) 0 access-list inside_outbound_nat0_acl
nat (inside) 10 0.0.0.0 0.0.0.0
static (inside,outside) xx.xxx.xx.xxx 10.1.1.234 netmask 255.255.255.255
static (inside,outside) xx.xxx.xx.xxx 10.1.1.251 netmask 255.255.255.255
static (inside,outside) xx.xxx.xx.xxx 10.1.1.231 netmask 255.255.255.255
access-group outside_access_in in interface outside
access-group inside_access_in in interface inside
route outside 0.0.0.0 0.0.0.0 xx.xxx.xx.xxx 1
route inside 10.1.0.0 255.255.0.0 10.1.0.2 1
route inside 172.16.1.0 255.255.255.0 10.1.0.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
aaa-server TACACS+ protocol tacacs+
aaa-server RADIUS protocol radius
group-policy DfltGrpPolicy attributes
banner none
wins-server none
dns-server none
dhcp-network-scope none
vpn-access-hours none
vpn-simultaneous-
vpn-idle-timeout 30
vpn-session-timeout none
vpn-filter none
vpn-tunnel-protocol IPSec l2tp-ipsec
password-storage
ip-comp disable
re-xauth disable
group-lock none
pfs disable
ipsec-udp disable
ipsec-udp-port 10000
split-tunnel-policy tunnelall
split-tunnel-network-list none
default-domain none
split-dns none
intercept-dhcp 255.255.255.255 disable
secure-unit-authentication
user-authentication disable
user-authentication-idle-t
ip-phone-bypass disable
leap-bypass disable
nem disable
backup-servers keep-client-config
msie-proxy server none
msie-proxy method no-modify
msie-proxy except-list none
msie-proxy local-bypass disable
nac disable
nac-sq-period 300
nac-reval-period 36000
nac-default-acl none
address-pools none
client-firewall
client-access-
group-policy Groups internal
group-policy Groups attributes
wins-server value 10.1.1.253
dns-server value 10.1.1.253
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split_tunnel_list
username xxxxx password 8jBjTxxxx1223pM encrypted privilege 15
username cxxxxx password enn5xxxseefT8HL encrypted privilege 15
aaa authentication ssh console LOCAL
aaa authentication http console LOCAL
aaa authentication enable console LOCAL
aaa authentication telnet console LOCAL
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server community public
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto dynamic-map outside_dyn_map 20 match address outside_cryptomap_65535.20
crypto dynamic-map outside_dyn_map 20 set pfs
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 60 match address outside_cryptomap_60
crypto map outside_map 60 set peer xx.xxx.xxx.xx
crypto map outside_map 60 set transform-set ESP-DES-MD5
crypto map outside_map 100 match address outside_100_cryptomap
crypto map outside_map 100 set pfs
crypto map outside_map 100 set peer xx.xx.xxx.xxx
crypto map outside_map 100 set transform-set ESP-3DES-MD5
crypto map outside_map 140 match address outside_140_cryptomap
crypto map outside_map 140 set pfs
crypto map outside_map 140 set peer xx.xx.xxx.x
crypto map outside_map 140 set transform-set ESP-3DES-MD5
crypto map outside_map 160 match address outside_160_cryptomap
crypto map outside_map 160 set pfs
crypto map outside_map 160 set peer xx.xxx.xxx.x
crypto map outside_map 160 set transform-set ESP-3DES-MD5
crypto map outside_map 220 match address outside_220_cryptomap
crypto map outside_map 220 set pfs
crypto map outside_map 220 set peer xxx.xx.xxx.xxx
crypto map outside_map 220 set transform-set ESP-3DES-MD5
crypto map outside_map 260 match address outside_260_cryptomap
crypto map outside_map 260 set pfs
crypto map outside_map 260 set peer xxx.xx.xxx.xx
crypto map outside_map 260 set transform-set ESP-3DES-MD5
crypto map outside_map 280 match address outside_280_cryptomap
crypto map outside_map 280 set pfs
crypto map outside_map 280 set peer xx.xxx.xx.xx
crypto map outside_map 280 set transform-set ESP-3DES-SHA
crypto map outside_map 300 match address outside_300_cryptomap_1
crypto map outside_map 300 set pfs
crypto map outside_map 300 set peer xxx.xx.xxx.xxx
crypto map outside_map 300 set transform-set ESP-3DES-SHA
crypto map outside_map 320 match address outside_320_cryptomap_1
crypto map outside_map 320 set pfs
crypto map outside_map 320 set peer xx.xx.xxx.xx
crypto map outside_map 320 set transform-set ESP-3DES-SHA
crypto map outside_map 340 match address outside_340_cryptomap
crypto map outside_map 340 set pfs
crypto map outside_map 340 set peer xxx.xx.xxx.xxx
crypto map outside_map 340 set transform-set ESP-3DES-MD5
crypto map outside_map 360 match address outside_360_cryptomap
crypto map outside_map 360 set pfs
crypto map outside_map 360 set peer xx.xx.xxx.xxx
crypto map outside_map 360 set transform-set ESP-3DES-MD5
crypto map outside_map 380 match address outside_380_cryptomap_1
crypto map outside_map 380 set pfs
crypto map outside_map 380 set peer xxx.xxx.xxx.xxx
crypto map outside_map 380 set transform-set ESP-3DES-MD5
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto ca trustpoint prod-pix
enrollment self
crl configure
crypto isakmp identity hostname
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
crypto isakmp policy 30
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto isakmp nat-traversal 20
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key **
tunnel-group DM type ipsec-l2l
tunnel-group DM ipsec-attributes
pre-shared-key **
tunnel-group xxxx type ipsec-ra
tunnel-group xxxx general-attributes
address-pool VPN_remote
default-group-policy vPN
tunnel-group Groups ipsec-attributes
pre-shared-key **
isakmp ikev1-user-authentication none
tunnel-group xx.xx.xx.x type ipsec-l2l
tunnel-group xx.xxx.xxx.x ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xx.xx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group Wards type ipsec-l2l
tunnel-group Wards ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key *
tunnel-group xx.xx.xxx.xxxx type ipsec-l2l
tunnel-group xx.xx.xxx.xxxx ipsec-attributes
pre-shared-key ******
telnet 10.1.0.1 255.255.255.255 inside
telnet timeout 5
ssh 0.0.0.0 0.0.0.0 outside
ssh 0.0.0.0 0.0.0.0 inside
ssh timeout 20
console timeout 0
management-access inside
dhcpd ping_timeout 750
!
dhcpd address 10.1.0.200-10.1.0.250 inside
dhcpd dns 10.1.1.1 interface inside
!
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns migrated_dns_map_1
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns migrated_dns_map_1
inspect ftp
inspect h323 h225
inspect h323 ras
inspect http
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
ssl encryption des-sha1 rc4-md5
prompt hostname context
Cryptochecksum:c38f6xxxx3f
: end
I'm not sure what happens to a packet sent from 10.1.2.x to 10.1.1.x.
you have 10.1.2.1 defined as an IP on the Switch port.Do you have an internal web server where you have logs. can any system on the 10.1.2.x access that site?
look at the log entry to see what the source IP for the request is.
i.e. http://www.myinternalsite.com/apagethatshouldnotandevercouldnotexist.html
then look for this request if present in the log and see if it matches the IP of the system from which you made the request.
you have 10.1.2.1 defined as an IP on the Switch port.Do you have an internal web server where you have logs. can any system on the 10.1.2.x access that site?
look at the log entry to see what the source IP for the request is.
i.e. http://www.myinternalsite.com/apagethatshouldnotandevercouldnotexist.html
then look for this request if present in the log and see if it matches the IP of the system from which you made the request.
ASKER
Yes, we do host our own website, and I'm on the 10.1.2.x and I can access it either via IP or name.
Everything is accessible from 10.1.2.x, it's just the DFS.
Everything is accessible from 10.1.2.x, it's just the DFS.
is this a DFS namespace with a single server, or are multiple servers involved ?
are there any firewall rules set on the DFS server(s) ?
are there any firewall rules set on the DFS server(s) ?
ASKER
is this a DFS namespace with a single server, or are multiple servers involved ?
answer: 2 servers involved.
are there any firewall rules set on the DFS server(s) ?
Answer: no fwall rules enabled.
answer: 2 servers involved.
are there any firewall rules set on the DFS server(s) ?
Answer: no fwall rules enabled.
can the 10.1.2.x ping each server where the share is?
can those servers ping 10.1.2.x?
can those servers ping 10.1.2.x?
ASKER
Arnold, Yes I can ping from 10.1.2.x to 10.1.1.x and vice versa. I can even access the server via \\10.1.1.20 \\10.1.1.21 from 10.1.2.x.
The only problem on this Vlan is just that I can't access the DFS.
The only problem on this Vlan is just that I can't access the DFS.
can you resolve domain? What does the 10.1.2.x system use for DNS?
can 10.1.2.x system access any other resource?
does it make a difference if you use \\domain\root\share versus \\domain.local\root\share?
can 10.1.2.x system access any other resource?
does it make a difference if you use \\domain\root\share versus \\domain.local\root\share?
ASKER
I can access both server dfs host servers if I use the following syntax:
\\DataCenterServer.mydomai
\\hyperv.mydomain.org\Staf
but if I tried this \\mydomain.org\Staff Files I can't get to it.
\\DataCenterServer.mydomai
\\hyperv.mydomain.org\Staf
but if I tried this \\mydomain.org\Staff Files I can't get to it.
ASKER
I can access both dfs host servers if I use the following syntax:
\\DataCenterServer.mydomai
\\hyperv.mydomain.org\Staf
but if I try this \\mydomain.org\Staff Files I can't get to it.
\\DataCenterServer.mydomai
\\hyperv.mydomain.org\Staf
but if I try this \\mydomain.org\Staff Files I can't get to it.
What DNS servers are listed for systems on 10.1.2.x?
does mydomain.org resolve
nslookup -q=srv _ldap._tcp.mydomain.org
what is returned? does it return the list of your DC's?
does mydomain.org resolve
nslookup -q=srv _ldap._tcp.mydomain.org
what is returned? does it return the list of your DC's?
ASKER
Can a system on the 10.1.2.x access the system on 10.16.1.152?
This could be the only explanation.
try \\10.1.1.253\Staff Files
\\10.1.1.254\Staff Files
\\10.16.1.152\Staff Files
The DC's are the DFS servers.
Alternatively edit c:\windows\system32\driver
10.1.1.253 mydomain.org
10.1.1.254 mydomain.org
and see if you regain access to the dfs from this system
The others prefer local and will use the 10.1.1.x by default and presumably the VPN clients can access either without an issue.
This could be the only explanation.
try \\10.1.1.253\Staff Files
\\10.1.1.254\Staff Files
\\10.16.1.152\Staff Files
The DC's are the DFS servers.
Alternatively edit c:\windows\system32\driver
10.1.1.253 mydomain.org
10.1.1.254 mydomain.org
and see if you regain access to the dfs from this system
The others prefer local and will use the 10.1.1.x by default and presumably the VPN clients can access either without an issue.
ASKER
Arnold, I'm not sure what you're talking about.
The 10.1.1.253, .254 or the 10.16.1.252 are not the DFS servers.
The DFS servers IP's are 10.1.1.94 and the other one is .10.1.1.147
The 10.1.1.253, .254 or the 10.16.1.252 are not the DFS servers.
The DFS servers IP's are 10.1.1.94 and the other one is .10.1.1.147
They are. Those are presumably your DC's.The way DFS works.
DFS is a reference service akin to an operator. You call the main number and ask for assistance with X and the operator connects to those who provide services for it.
\\mydomain.org resolves to the DC's which then consult the AD for the DFS targets for "Staff Share" which in your case is:
\\DataCenterServer.mydomai
\\hyperv.mydomain.org\Staf
Presumably 10.1.1.94 and 10.1.1.147 are the physical servers where the shares "Staff Share" are.
Try it , what do you have to lose?
DFS is a reference service akin to an operator. You call the main number and ask for assistance with X and the operator connects to those who provide services for it.
\\mydomain.org resolves to the DC's which then consult the AD for the DFS targets for "Staff Share" which in your case is:
\\DataCenterServer.mydomai
\\hyperv.mydomain.org\Staf
Presumably 10.1.1.94 and 10.1.1.147 are the physical servers where the shares "Staff Share" are.
Try it , what do you have to lose?
ASKER
Arnold. Can u tell me what u want me to try again?
The dfs \\mydomain.org\Staff Share is equivalent to \\dc\Staff Share
So I am going on the presumption that the 10.1.1.253, 10.1.1.254 and 10.16.1.252 are the DC's for mydomain.org in which case I am trying to see whether the inability of a system on 10.1.2.x to access the DFS share is because it can not access the 10.16.1.252 DC versus not being able to access the 10.1.1.94 and 10.1.1.147 which are the fileservers hosting the underlying shares (Target Servers for the DFS share.)
I''d like you to access the DFS share using the DC servers IPs in place of mydomain.org!
\\10.1.1.253\Staff Share
\\10.1.1.254\Staff Share
\\10.16.1.252\Staff Share
So I am going on the presumption that the 10.1.1.253, 10.1.1.254 and 10.16.1.252 are the DC's for mydomain.org in which case I am trying to see whether the inability of a system on 10.1.2.x to access the DFS share is because it can not access the 10.16.1.252 DC versus not being able to access the 10.1.1.94 and 10.1.1.147 which are the fileservers hosting the underlying shares (Target Servers for the DFS share.)
I''d like you to access the DFS share using the DC servers IPs in place of mydomain.org!
\\10.1.1.253\Staff Share
\\10.1.1.254\Staff Share
\\10.16.1.252\Staff Share
ASKER
Got it will try that. Will keep u posted. Will do it as soon as I get my hands on my computer.
ASKER
Not working...
What is not working? none of the options work?
Can you try the same from a system on the 10.1.1.x segment?
Did you try the pix debug using an access list to define the type of data you want to capture??
Alternatively, you can use wireshark from wireshark.net as a networking tool running on the server and on the client and then you can see whether traffic from the client reaches the server and then whether the response is making it back to the client.
In DFS there are three steps
/ DC
Client
\ Target File server
So you have to determine whether the client can not hit the DC to get the target System references or the client can not get to the target servers.
Can you try the same from a system on the 10.1.1.x segment?
Did you try the pix debug using an access list to define the type of data you want to capture??
Alternatively, you can use wireshark from wireshark.net as a networking tool running on the server and on the client and then you can see whether traffic from the client reaches the server and then whether the response is making it back to the client.
In DFS there are three steps
/ DC
Client
\ Target File server
So you have to determine whether the client can not hit the DC to get the target System references or the client can not get to the target servers.
ASKER
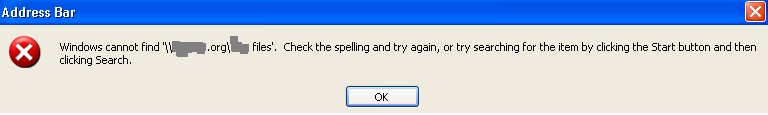
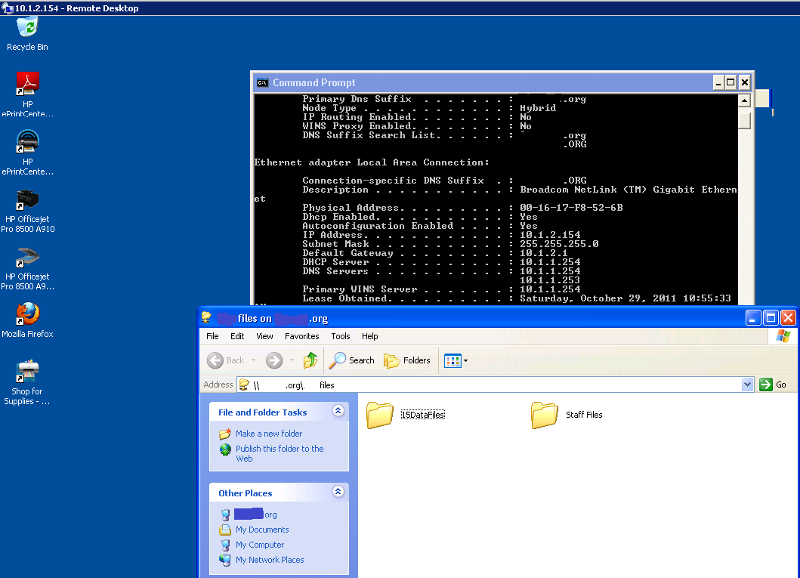
Ran this command, and it's open to interpretation.
output.jpg
output.jpg
ASKER
Arnold: You asked;
"Can you try the same from a system on the 10.1.1.x segment?
Answer, no problems on 10.1.1.x. Should I still do that?
"Can you try the same from a system on the 10.1.1.x segment?
Answer, no problems on 10.1.1.x. Should I still do that?
yes. see whether the 10.1.1.x system can access the dfs share as outlined using IPs of the DCs.
You have 5 listed as responsible for mydomain.org in dfsutil
Yet the nslookup only reflected three DCs.
You have 5 listed as responsible for mydomain.org in dfsutil
Yet the nslookup only reflected three DCs.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I think we are running in circles, the first query for \\mydomain.org\Staff Files goes to the DCs. Which then provide the target information.
Can you from 10.1.2.27 access \\10.16.1.252\Staff Files?
Can you from 10.1.2.27 access \\10.16.1.252\Staff Files?
ASKER
Can you telnet to ports 445 139 137 of the IPs?
Do you have a RODC on the 10.1.2.x segment?
Do you have a RODC on the 10.1.2.x segment?
ASKER
ASKER
On my comments I said that I have been dealing with this issue for the last 3 weeks, now it's working.
ASKER
On my comments I said that I have been dealing with this issue for the last 3 weeks, now it's working.
What is the device to which is segment connected (router/firewall)?
What IP does the server with the SHARE has and what is the DC's IP?
Ping is one thing does a system on 10.1.2.x telnet to 10.1.1.x 445/137/139?
You may have a rule that does not allow this traffic through while the clients on the 10.1.1.x see the DFS as local and send the request directly versus going through the router.