okamon
asked on
why put web server in DMZ?
I don't understand why would someone put the webserver in DMZ. the port forwarding can be done, why put it in dmz without firewall protection? I understand for gamers, sometimes they need to use dmz because they are too many ports need to be open and they are not sure the exactly the ports are. So for servers, what is the purpose? any companies put their production server in dmz?
Also, in some situations it might be beneficial to even split it up more, thereby segregating multiple systems in their own specific area, increasing security between the DMZ systems ...
Depends on your setup. Many do this to isolate the web server from the internal network, which provides an extra layer of security. Some may locate a front end web server, email server, etc. in the DMZ and then put your database server(s) and clients in the internal network. If your web server, etc. is compromised, the hackers still need to get to your internal network to get any real data. In addition to the internal network, the DMZ is almost always protected from the Internet to some degree.
If you have multiple public IPs there is little reason for using a DMZ. However if you are short of public IPs using a DMZ allows you to run multiple servers AND have NAT access for a LAN on one IP. VERY handy!
Like Garry-G says locating a server in a DMZ (or another public IP) makes your LAN safer buy moving servers that are by their nature more open to compromise off your LAN.
Like Garry-G says locating a server in a DMZ (or another public IP) makes your LAN safer buy moving servers that are by their nature more open to compromise off your LAN.
ASKER
so if I put my webserver in DMZ will that get hacked easily? as I know it's no firewall protected means all opens are open, sounds scary.
The idea is that IF your webserver gets hacked it does not provide a path to your internal network. Mitigate the possible harm.
A properly configured webserver will expose no more ports to the wild world of the Internet than required so port forwards do little to protect the webserver. Once hacked a compromised webserver on your LAN would, in most cases, be a platform to mount other attacks on your (no longer) protected network.
Most webservers operate all day every day on public IPs not behind routers with port forwards. Firewalling is done through server configuration to turn off unused ports, temporarily deny IP addresses that are engaging in suspicious activity and fixing known vulnerabilities as soon as patched. Add in a good backup and recovery plan and you have done your job.
Like I stated previously if you have enough public IPs for your servers and private network router there is no compelling reason to use a DMZ.
If you want to run a webserver and are uncomfortable with the security implications the best choice is to take advantage of any one of the myriad of web hosting options available. In many cases this you will save money in the long run.
A properly configured webserver will expose no more ports to the wild world of the Internet than required so port forwards do little to protect the webserver. Once hacked a compromised webserver on your LAN would, in most cases, be a platform to mount other attacks on your (no longer) protected network.
Most webservers operate all day every day on public IPs not behind routers with port forwards. Firewalling is done through server configuration to turn off unused ports, temporarily deny IP addresses that are engaging in suspicious activity and fixing known vulnerabilities as soon as patched. Add in a good backup and recovery plan and you have done your job.
Like I stated previously if you have enough public IPs for your servers and private network router there is no compelling reason to use a DMZ.
If you want to run a webserver and are uncomfortable with the security implications the best choice is to take advantage of any one of the myriad of web hosting options available. In many cases this you will save money in the long run.
Firewalls (nowadays) do more than just block ports or stateful inspection ... features like protocol inspection, IDS/IPS or content scanning allow you to more effectively secure your system ... of course, using a hosting/housing provider is the sensible alternative if you don't want to go through all the hassle and keep your internet connection simple to set up and operate securely ...
ASKER
Instead of using DMZ, can I setup my network with 2 routers, like below
Modem ----- router1 (web server) -------------router2 (internal)
So each router has firewall enabled, then I put my webserver, DNS, etc behind router1
Isn't this method more secure than the DMZ???
Modem ----- router1 (web server) -------------router2 (internal)
So each router has firewall enabled, then I put my webserver, DNS, etc behind router1
Isn't this method more secure than the DMZ???
ASKER
I still think with firewall protection for the webserver is more secure than the one without firewall (DMZ)
Let me know if I am wrong
Let me know if I am wrong
Why run two devices when you can do the same with one? Plus, if you actually set it up like that, you'd have to route everything through your web server ...
What do you mean with your last question? The Firewall is what provides the DMZ ...
What do you mean with your last question? The Firewall is what provides the DMZ ...
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
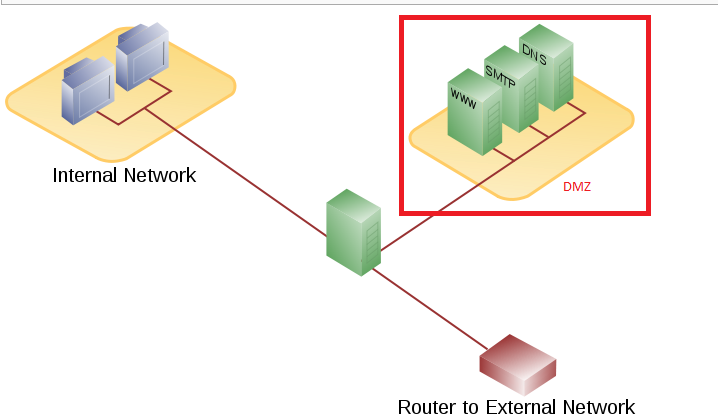
E.g., if someone were to find an exploit that allowed you shell access using the (allowed) access to port 80 of your webserver, if the system were located in the internal network, you could then access any internal system without further access control by the firewall. By putting systems that require access from the internet in a DMZ, you can set up the firewall to deny all access to the internal network, or set it up very tightly, as usually not many reasons exist to access the inside net from either the internet or the DMZ ...