And a third Virus!
Hi Art,
In the future, just go to the last comment of your old question and click on the "Ask a related question" link below that comment. When you use that feature, a special email alert will be sent to any Expert who posted in the old question.
Did you install the Premium version of Malwarebytes?
I haven't yet had a re-infected system when the customer is running MSE + MBAM (Pro).
Post the results of your scanner logs and give us any symptoms (especially names/banners) that are displaying.
I probably gave you this link before - it has all the details.
Rogue-Killer-What-a-great-
MALWARE - "An Ounce of Prevention..."
Ask an Expert
Search Solutions
ID:36471185Author:artismob
Was this comment helpful?
Yes No
Ok,
I see where I can re-post now. I don't think I'm running the pro. Funny, but now I'm running a full scan (not done yet) it's found 3 since I killed the fake trojan alert. AND MSE just found and item not yet been classified for risks. MSE was silent before that. I have not sent it yet.
ID:36471218Author:artismob
Was this comment helpful?
Yes No
Malwarebytes' Anti-Malware 1.51.1.1800
www.malwarebytes.org
Database version: 7633
Windows 6.1.7600
Internet Explorer 8.0.7600.16385
9/1/2011 9:45:52 PM
mbam-log-2011-09-01 (21-45-32).txt
Scan type: Full scan (C:\|)
Objects scanned: 311183
Time elapsed: 37 minute(s), 45 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 3
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Michala\AppData\L
c:\Users\Michala\AppData\L
c:\Users\Michala\AppData\L
MSE detected 1 file and removed it. Why is there no action taken by MWB?
ID:36471233Author:artismob
Was this comment helpful?
Yes No
RogueKiller V5.3.1 [08/06/2011] by Tigzy
contact at http://www.sur-la-toile.com
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.sur-la-toile.com/discussion-193725-1-BRogueKillerD-Remontees.html
Operating System: Windows 7 (6.1.7600 ) 64 bits version
Started in : Normal mode
User: Michala [Admin rights]
Mode: Scan -- Date : 09/01/2011 21:01:48
Bad processes: 1
[SUSP PATH] win4036e0.dat -- c:\users\michala\appdata\l
Registry Entries: 2
[SUSP PATH] 2906828992.job : \\.\globalroot\device\hard
[SUSP PATH] win4036e0.job : \\.\globalroot\device\hard
HOSTS File:
Finished : << RKreport[10].txt >>
RKreport[10].txt ; RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt ; RKreport[4].txt ;
RKreport[5].txt ; RKreport[6].txt ; RKreport[7].txt ; RKreport[8].txt ; RKreport[9].txt
This was the 2nd time I ran it in Windows SAFE mode
ID:36471409Author:artismob
Was this comment helpful?
Yes No
Just purchased MWB pro. We'll see what happens!
ID:36472065Author:phototro
Was this solution helpful?
Yes No
125 PointsA EXCELLENT
"...Why is there no action taken by MWB?..." Mbam allows you to decide which items you wish to remove by checking or unchecking the box next to each entry. You then click on "Remove selected" to quarantine the items. From there you can permanently delete them. "No action taken" means Mbam has not been asked to remove any of the selected items which it found. Run the scan again and click on "Remove selected" and see if it can remove the malware.
Getting infected twice in a month suggests that there is a problem with safe surfing.of the internet. Review the sites you routinely visit. Are any in any way disreputable? The most common source for infections is visiting disreputable sites: adult sites; peer-to-peer networks and torrent sites; infected codecs; online games downloads; cracks and keygens; etc.
I apologise in advance for bringing this up, but the viral infection must be coming from somewhere. Did you make a data backup during the last infection? If so, that may be infected. Do you have a flashdrive that may be re-infecting your pc? I think once your machine is once again clean you should review recent internet activity so that you can narrow down exactly where this infection is coming from. Prevention is better than cure.
ID:36473280Author:tskellyD
Was this solution helpful?
Yes No
125 PointsA EXCELLENT
For safer web searching, Web of Trust has benefited me.
Although some Web of Trust users unfortunately don't like Experts Exchange, and have marked it unsafe, Web of Trust otherwise identifies many malicious web sites that show up in Google search results, helping avoid malware. (The discussion of Web of Trust can be seen elsewhere.)
Link to Web of Trust:
http://www.mywot.com/
ID:36476006Author:SSharmaD
Was this solution helpful?
Yes No
125 PointsA EXCELLENT
@artismobile,
You have posted MalwareBytes logs first and then RogueKiller logs. Ideally RogueKiller should be run first and then MalwareBytes.
Once you are done with RogueKiller run MBAM again (do the update first and run Full System Scan)
Systems also get infected if they have older version of software installed as they are vulnerable and often are target of hackers.
Software like Flash, Shockwave, Java JRE should be updated too with the latest available version.
I hope that would help too.
Sudeep
ID:36476507Author:artismob
Was this comment helpful?
Yes No
I ran Rouge first then MEB. I posted the 2nd time I ran MWB after the first one I deleted the note. It is my daughter's computer and we just went over her search features, again. I'll have her update the old software versions as well.
Thanks
ID:36477556Author:younghvD
Was this comment helpful?
Yes No
Art,
I apologize for losing track of this one and not responding.
If I remember right, your daughter was doing her best to help us Experts stay on our toes :)
*************
You might want to consider a permanent solution to this problem as was discussed in my question from several years ago: https://www.experts-exchange.com/questions/23528044/Image-creation-storage-recommendations.html
The Expert (garycase) making the recommendation of "Boot-It NG" is an MS MVP and one of those people whose knowledge levels are way off the charts.
If you decide to go this route, creating a fresh image involves clicking a desktop icon and then go getting a cup of coffee (or other adult beverage) and coming back in about 5 minutes. The image is auto-stored on a separate partition and available to re-image simply by re-booting and following the directions.
As you can tell by reading through his comments, Gary is one of those guys who will walk you through the entire process - step-by-step. He hangs out in the Hardware Zones if you would like to post for some current advice/recommendations.
Use the "Ask a related question" function in my question and Gary will get the notification that you've done so.
Good luck with your lifetime project and say hey to your daughter for us.
In the future, just go to the last comment of your old question and click on the "Ask a related question" link below that comment. When you use that feature, a special email alert will be sent to any Expert who posted in the old question.
Did you install the Premium version of Malwarebytes?
I haven't yet had a re-infected system when the customer is running MSE + MBAM (Pro).
Post the results of your scanner logs and give us any symptoms (especially names/banners) that are displaying.
I probably gave you this link before - it has all the details.
Rogue-Killer-What-a-great-
MALWARE - "An Ounce of Prevention..."
Ask an Expert
Search Solutions
ID:36471185Author:artismob
Was this comment helpful?
Yes No
Ok,
I see where I can re-post now. I don't think I'm running the pro. Funny, but now I'm running a full scan (not done yet) it's found 3 since I killed the fake trojan alert. AND MSE just found and item not yet been classified for risks. MSE was silent before that. I have not sent it yet.
ID:36471218Author:artismob
Was this comment helpful?
Yes No
Malwarebytes' Anti-Malware 1.51.1.1800
www.malwarebytes.org
Database version: 7633
Windows 6.1.7600
Internet Explorer 8.0.7600.16385
9/1/2011 9:45:52 PM
mbam-log-2011-09-01 (21-45-32).txt
Scan type: Full scan (C:\|)
Objects scanned: 311183
Time elapsed: 37 minute(s), 45 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 3
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Michala\AppData\L
c:\Users\Michala\AppData\L
c:\Users\Michala\AppData\L
MSE detected 1 file and removed it. Why is there no action taken by MWB?
ID:36471233Author:artismob
Was this comment helpful?
Yes No
RogueKiller V5.3.1 [08/06/2011] by Tigzy
contact at http://www.sur-la-toile.com
mail: tigzyRK<at>gmail<dot>com
Feedback: http://www.sur-la-toile.com/discussion-193725-1-BRogueKillerD-Remontees.html
Operating System: Windows 7 (6.1.7600 ) 64 bits version
Started in : Normal mode
User: Michala [Admin rights]
Mode: Scan -- Date : 09/01/2011 21:01:48
Bad processes: 1
[SUSP PATH] win4036e0.dat -- c:\users\michala\appdata\l
Registry Entries: 2
[SUSP PATH] 2906828992.job : \\.\globalroot\device\hard
[SUSP PATH] win4036e0.job : \\.\globalroot\device\hard
HOSTS File:
Finished : << RKreport[10].txt >>
RKreport[10].txt ; RKreport[1].txt ; RKreport[2].txt ; RKreport[3].txt ; RKreport[4].txt ;
RKreport[5].txt ; RKreport[6].txt ; RKreport[7].txt ; RKreport[8].txt ; RKreport[9].txt
This was the 2nd time I ran it in Windows SAFE mode
ID:36471409Author:artismob
Was this comment helpful?
Yes No
Just purchased MWB pro. We'll see what happens!
ID:36472065Author:phototro
Was this solution helpful?
Yes No
125 PointsA EXCELLENT
"...Why is there no action taken by MWB?..." Mbam allows you to decide which items you wish to remove by checking or unchecking the box next to each entry. You then click on "Remove selected" to quarantine the items. From there you can permanently delete them. "No action taken" means Mbam has not been asked to remove any of the selected items which it found. Run the scan again and click on "Remove selected" and see if it can remove the malware.
Getting infected twice in a month suggests that there is a problem with safe surfing.of the internet. Review the sites you routinely visit. Are any in any way disreputable? The most common source for infections is visiting disreputable sites: adult sites; peer-to-peer networks and torrent sites; infected codecs; online games downloads; cracks and keygens; etc.
I apologise in advance for bringing this up, but the viral infection must be coming from somewhere. Did you make a data backup during the last infection? If so, that may be infected. Do you have a flashdrive that may be re-infecting your pc? I think once your machine is once again clean you should review recent internet activity so that you can narrow down exactly where this infection is coming from. Prevention is better than cure.
ID:36473280Author:tskellyD
Was this solution helpful?
Yes No
125 PointsA EXCELLENT
For safer web searching, Web of Trust has benefited me.
Although some Web of Trust users unfortunately don't like Experts Exchange, and have marked it unsafe, Web of Trust otherwise identifies many malicious web sites that show up in Google search results, helping avoid malware. (The discussion of Web of Trust can be seen elsewhere.)
Link to Web of Trust:
http://www.mywot.com/
ID:36476006Author:SSharmaD
Was this solution helpful?
Yes No
125 PointsA EXCELLENT
@artismobile,
You have posted MalwareBytes logs first and then RogueKiller logs. Ideally RogueKiller should be run first and then MalwareBytes.
Once you are done with RogueKiller run MBAM again (do the update first and run Full System Scan)
Systems also get infected if they have older version of software installed as they are vulnerable and often are target of hackers.
Software like Flash, Shockwave, Java JRE should be updated too with the latest available version.
I hope that would help too.
Sudeep
ID:36476507Author:artismob
Was this comment helpful?
Yes No
I ran Rouge first then MEB. I posted the 2nd time I ran MWB after the first one I deleted the note. It is my daughter's computer and we just went over her search features, again. I'll have her update the old software versions as well.
Thanks
ID:36477556Author:younghvD
Was this comment helpful?
Yes No
Art,
I apologize for losing track of this one and not responding.
If I remember right, your daughter was doing her best to help us Experts stay on our toes :)
*************
You might want to consider a permanent solution to this problem as was discussed in my question from several years ago: https://www.experts-exchange.com/questions/23528044/Image-creation-storage-recommendations.html
The Expert (garycase) making the recommendation of "Boot-It NG" is an MS MVP and one of those people whose knowledge levels are way off the charts.
If you decide to go this route, creating a fresh image involves clicking a desktop icon and then go getting a cup of coffee (or other adult beverage) and coming back in about 5 minutes. The image is auto-stored on a separate partition and available to re-image simply by re-booting and following the directions.
As you can tell by reading through his comments, Gary is one of those guys who will walk you through the entire process - step-by-step. He hangs out in the Hardware Zones if you would like to post for some current advice/recommendations.
Use the "Ask a related question" function in my question and Gary will get the notification that you've done so.
Good luck with your lifetime project and say hey to your daughter for us.
Many years of experience doing cleanups for the same customers yields some pretty good statistics:
- Households with young people ("young" in attitude, not age) who are inquisitive and adventurous strongly correlate with infections. No software is 100% successful in prevention.
- "Good" internet security software is overcome in those same environments.
- "Good" internet security software is adequate in "normal" environments.
(I have had infections occur with "good" internet security software in a very small number of cases .. and the environment above applied every time. Otherwise, the "good" software seems to do the job .. not that it doesn't catch something now and then but it does its job.
Protection software companies are in a race with the infectors. So, there *will* be some leakage - particularly during the first few days from release - that will vary from company to company and software to software. This results in two observations:
- frequent updating is essential
- frequent risky activity is more likely to cause infections than the same that's infrequent (because it's more likely that the protection has caught up).
- Establishing "parental controls" (an unfortunate descriptor .. it should be more like "added security") which prevents website access without a password to override seems to help a lot! If a website is blocked, it stays blocked. This seems to have made quite a difference in a situation where reinfections were happening every 2-3 months. (Only I have the password and it's not been requested .. ever). That its' not been requested at least suggests:
- blocked websites aren't getting hit (but then how to explain the improvement?)
- revealing the sites "desired" would be embarrassing
- some blocked sites just aren't worth the trouble....
Firewalls are essential.
- Households with young people ("young" in attitude, not age) who are inquisitive and adventurous strongly correlate with infections. No software is 100% successful in prevention.
- "Good" internet security software is overcome in those same environments.
- "Good" internet security software is adequate in "normal" environments.
(I have had infections occur with "good" internet security software in a very small number of cases .. and the environment above applied every time. Otherwise, the "good" software seems to do the job .. not that it doesn't catch something now and then but it does its job.
Protection software companies are in a race with the infectors. So, there *will* be some leakage - particularly during the first few days from release - that will vary from company to company and software to software. This results in two observations:
- frequent updating is essential
- frequent risky activity is more likely to cause infections than the same that's infrequent (because it's more likely that the protection has caught up).
- Establishing "parental controls" (an unfortunate descriptor .. it should be more like "added security") which prevents website access without a password to override seems to help a lot! If a website is blocked, it stays blocked. This seems to have made quite a difference in a situation where reinfections were happening every 2-3 months. (Only I have the password and it's not been requested .. ever). That its' not been requested at least suggests:
- blocked websites aren't getting hit (but then how to explain the improvement?)
- revealing the sites "desired" would be embarrassing
- some blocked sites just aren't worth the trouble....
Firewalls are essential.
ASKER
Children are challenges. Looks like this one piggybacked when we downloaded the VLC player after having problems with Windows Media Player, at least the icon for VLC is gone now. (It's still scanning MS essentials.) The problems occurred shortly after. I have AVG on all the other computers with no problems so far. The daughter in college with Macafee Internet got one last month. She was too far from me at the time and we had to pay $60.00 to clean that one. The more the searching the more problems. I blame it on YouTube and Rap music. :-) Used to be that darn rock and roll. <wink>
I'll post the results. Still scanning.
I'll post the results. Still scanning.
ASKER
Malwarebytes and Microsoft Essentials working properly. I guess its not infected anymore.
Hi Art,
If you look at the very bottom of your original post up above, you will see this link:
"Related Solutions: And ANOTHER virus"
We can use that link to review the old question, so there is no need for you to include all the text in your post.
*******************
Your last comment (in this thread) shows that your scans have finished and you think you are now OK.
What were the symptoms that caused you to post this and do you have any logs from RK or MBAM to attach?
RK and MBAM are really great products, but there is malware that will survive them.
Please re-state the problem you are/were now having and let's see if there is anything else you should run.
Thanks,
Vic
If you look at the very bottom of your original post up above, you will see this link:
"Related Solutions: And ANOTHER virus"
We can use that link to review the old question, so there is no need for you to include all the text in your post.
*******************
Your last comment (in this thread) shows that your scans have finished and you think you are now OK.
What were the symptoms that caused you to post this and do you have any logs from RK or MBAM to attach?
RK and MBAM are really great products, but there is malware that will survive them.
Please re-state the problem you are/were now having and let's see if there is anything else you should run.
Thanks,
Vic
VLC player is your main cause of this type of infection. I did some research while TDL3 rootkit made it's way out into the world. A site called videocop was installing VLC codec's hen the user authorized them. The problem was boy a exploit in this situation it was social engineering in motion. It enticed the user to drop security precautions to allow the codec(Trojan bundled with this codec) and installed the application giving the malware author money for what is called pay-per-click install, and one for user just visiting the site, and yet another one for installing the malware (From a criminal syndicate). You need to express and teach proper surfing habits for this to be avoided. Curiosity can be the undoing of the all the expensive software that was installed to prevent this problem. Fmatshall has the correct idea. Best thing is educate the user. These criminals have been known to steal your data and your life by careless curiousity choices.
Best things to avoid are:
Non-approved DVD sites. This is a very BIG point where these criminals focus there attention on unsuspecting users wanting something like free music or movies. Torrent sites are notorious for this content as well. Malware authors love using torrent as it is hard to control what is shared, it also anonymizes the user who initially uploaded the content making te abuser almost uncatchable by normal means.
Other suggestions I have given people is using a "sandboxed" approach to browsing the web using a browser. This would include using software like sandboxie and allowing this program to create a virtual sandbox for the applications to run in a more secure virtual environment instead of directly running on the computer and finding out the file was malicious. Sandboxing does not allow whatever has been run in he secured sandbox to effect what is outside this virtual box helping prevent infections and allows you to fix the problem in a few clicks by deleting the sandbox session compared to risky formats and reinstalling, buying more software to make up for damages done by the malware, and time & frustration used in this effect. If I may add it is very important to note(If known) What infected the machine if caught by one of the antivirus or removal tools used. This saves not only the user time but also the experts who spend there time to help out. Details are golden and sometimes priceless.
Best things to avoid are:
Non-approved DVD sites. This is a very BIG point where these criminals focus there attention on unsuspecting users wanting something like free music or movies. Torrent sites are notorious for this content as well. Malware authors love using torrent as it is hard to control what is shared, it also anonymizes the user who initially uploaded the content making te abuser almost uncatchable by normal means.
Other suggestions I have given people is using a "sandboxed" approach to browsing the web using a browser. This would include using software like sandboxie and allowing this program to create a virtual sandbox for the applications to run in a more secure virtual environment instead of directly running on the computer and finding out the file was malicious. Sandboxing does not allow whatever has been run in he secured sandbox to effect what is outside this virtual box helping prevent infections and allows you to fix the problem in a few clicks by deleting the sandbox session compared to risky formats and reinstalling, buying more software to make up for damages done by the malware, and time & frustration used in this effect. If I may add it is very important to note(If known) What infected the machine if caught by one of the antivirus or removal tools used. This saves not only the user time but also the experts who spend there time to help out. Details are golden and sometimes priceless.
ASKER
Yonghv, fmarshal, Russell,
I'll post the log after the scan when I can get a hold of that computer. I say it was the VCL player but simultaneously, she loaded Spotify which is a free music application that's still on her computer. I loaded it on mine for a short amount of time and then deleted it. ME ran a scan afterwards that found 3 threats but didn't clean them..allowed them to run. I ran MalwareBytes again and cleared it up. I agree our younger gen. has more of an opportunity to run into these things. We did too when we were younger, but not with computers. I'll grab her notepad and post when I have a chance.
I'll post the log after the scan when I can get a hold of that computer. I say it was the VCL player but simultaneously, she loaded Spotify which is a free music application that's still on her computer. I loaded it on mine for a short amount of time and then deleted it. ME ran a scan afterwards that found 3 threats but didn't clean them..allowed them to run. I ran MalwareBytes again and cleared it up. I agree our younger gen. has more of an opportunity to run into these things. We did too when we were younger, but not with computers. I'll grab her notepad and post when I have a chance.
ASKER
Actually since the last post, it came back. I deleted the VLC player after I ran Rkill and malwarebytes again. Here's the info:
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122308
Windows 6.1.7600 (Safe Mode)
Internet Explorer 8.0.7600.16385
12/29/2011 12:40:01 PM
mbam-log-2011-12-29 (12-40-01).txt
Scan type: Quick scan
Objects scanned: 169835
Time elapsed: 2 minute(s), 33 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 1
Folders Infected: 0
Files Infected: 1
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWAR
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Michala\AppData\L
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122308
Windows 6.1.7600
Internet Explorer 8.0.7600.16385
12/29/2011 12:47:25 PM
mbam-log-2011-12-29 (12-47-25).txt
Scan type: Quick scan
Objects scanned: 170567
Time elapsed: 4 minute(s), 24 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Any advice (other than watch the sites we dowload from) to follow?
Thanks
Art
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122308
Windows 6.1.7600 (Safe Mode)
Internet Explorer 8.0.7600.16385
12/29/2011 12:40:01 PM
mbam-log-2011-12-29 (12-40-01).txt
Scan type: Quick scan
Objects scanned: 169835
Time elapsed: 2 minute(s), 33 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 1
Folders Infected: 0
Files Infected: 1
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWAR
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Michala\AppData\L
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122308
Windows 6.1.7600
Internet Explorer 8.0.7600.16385
12/29/2011 12:47:25 PM
mbam-log-2011-12-29 (12-47-25).txt
Scan type: Quick scan
Objects scanned: 170567
Time elapsed: 4 minute(s), 24 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 0
Folders Infected: 0
Files Infected: 0
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
(No malicious items detected)
Folders Infected:
(No malicious items detected)
Files Infected:
(No malicious items detected)
Any advice (other than watch the sites we dowload from) to follow?
Thanks
Art
ASKER
I don't know where the Rkill log went
ASKER
Asking for more suggestions on this. The same virus is back. re-cap I have Microsoft Essentials and I run malwarebytes. It seems like it started after I loaded the VLC player and Spotify. I deleted the VLC player and ran Rkiller and this same virus keeps coming back. Each time I run R killer in Safe Mode as a boot up from the flash drive. Both Malwarebytes and ME find viruses and cleans them. I reboot. I can go on line no problem. When I shut the computer down the virus is back. I'm going to try this again and delete Spotify.
ASKER
Here's the log. By the way, this time I ran TDSSKiller and it found no threats...
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122308
Windows 6.1.7600 (Safe Mode)
Internet Explorer 8.0.7600.16385
1/2/2012 2:39:48 PM
mbam-log-2012-01-02 (14-39-40).txt
Scan type: Quick scan
Objects scanned: 169956
Time elapsed: 2 minute(s), 19 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 1
Folders Infected: 0
Files Infected: 2
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWAR
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Michala\local settings\application data\dox.exe (Trojan.ExeShell.Gen) -> No action taken.
c:\Users\Michala\AppData\L
Why does this say no action taken?
Malwarebytes' Anti-Malware 1.51.2.1300
www.malwarebytes.org
Database version: 911122308
Windows 6.1.7600 (Safe Mode)
Internet Explorer 8.0.7600.16385
1/2/2012 2:39:48 PM
mbam-log-2012-01-02 (14-39-40).txt
Scan type: Quick scan
Objects scanned: 169956
Time elapsed: 2 minute(s), 19 second(s)
Memory Processes Infected: 0
Memory Modules Infected: 0
Registry Keys Infected: 0
Registry Values Infected: 0
Registry Data Items Infected: 1
Folders Infected: 0
Files Infected: 2
Memory Processes Infected:
(No malicious items detected)
Memory Modules Infected:
(No malicious items detected)
Registry Keys Infected:
(No malicious items detected)
Registry Values Infected:
(No malicious items detected)
Registry Data Items Infected:
HKEY_LOCAL_MACHINE\SOFTWAR
Folders Infected:
(No malicious items detected)
Files Infected:
c:\Users\Michala\local settings\application data\dox.exe (Trojan.ExeShell.Gen) -> No action taken.
c:\Users\Michala\AppData\L
Why does this say no action taken?
ASKER
Also, running Microsoft Essentials full scan for the 4th time and it's saying that potentially unwanted software exist on my computer. Why doesn't Rkill, TDDSKILL, Malwarebytes find this?
ASKER
Microsoft Essentials found but allows Exploit:Java/CVE=2011-3544
It Removed Rogue:Win32 FakeRean
What does this mean?
It Removed Rogue:Win32 FakeRean
What does this mean?
You probably have malwarebytes setup to take no action.
Can you run a scan with GMER's MBR scan tool and see what it comes up with. Your boot sector (MBR) is definitely infected.
Can you run a scan with GMER's MBR scan tool and see what it comes up with. Your boot sector (MBR) is definitely infected.
Additionally. Do you know what site specifically this version of VLC and Spotify was downloaded from? I may need to get a working example to find what version it dropped.
ASKER
I don't remember what site both those came from. Right now I'm doing a full Malwarebytes Anti Malware full scan again 27 minutes in it. I'll download and run MBR when it stops.
ASKER
Here's the result of the Malwarebytes scan this time. I'm running MBR now..
Malwarebytes Anti-Malware 1.60.0.1800
www.malwarebytes.org
Database version: v2012.01.02.04
Windows 7 x64 NTFS
Internet Explorer 8.0.7600.16385
Michala :: MICHALA-PC [administrator]
1/2/2012 4:16:24 PM
mbam-log-2012-01-02 (16-16-24).txt
Scan type: Full scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 322851
Time elapsed: 41 minute(s), 43 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
Malwarebytes Anti-Malware 1.60.0.1800
www.malwarebytes.org
Database version: v2012.01.02.04
Windows 7 x64 NTFS
Internet Explorer 8.0.7600.16385
Michala :: MICHALA-PC [administrator]
1/2/2012 4:16:24 PM
mbam-log-2012-01-02 (16-16-24).txt
Scan type: Full scan
Scan options enabled: Memory | Startup | Registry | File System | Heuristics/Extra | Heuristics/Shuriken | PUP | PUM
Scan options disabled: P2P
Objects scanned: 322851
Time elapsed: 41 minute(s), 43 second(s)
Memory Processes Detected: 0
(No malicious items detected)
Memory Modules Detected: 0
(No malicious items detected)
Registry Keys Detected: 0
(No malicious items detected)
Registry Values Detected: 0
(No malicious items detected)
Registry Data Items Detected: 0
(No malicious items detected)
Folders Detected: 0
(No malicious items detected)
Files Detected: 0
(No malicious items detected)
(end)
ASKER
OK MBR is running, I have never used this. What am I looking for? Will it give a notepad or something when it is done to forward to you?
You will need to run this command in a command prompt:
push the key combination CTRL+R , this will bring up a run box, Then type "cmd" hit enter. Next change directory to where you saved mbr.exe.
Example:
Please send that file.
push the key combination CTRL+R , this will bring up a run box, Then type "cmd" hit enter. Next change directory to where you saved mbr.exe.
Example:
cd %userprofile%\desktop"mbr -d0 -t -s -l logfile.logPlease send that file.
ASKER
I still don't know what to do with the MBR. I'll shut it down and wait for someone to get back with me. Doesn't look like there is still a virus on it now, but it look like this 4 attempts ago.
To answer your question above about
As for your post here. Well whoever that is they are going to need to flush the MBR to make sure this infection is gone. Using W7's bootrec.exe tool and running this code from a recovery console. I also forgot your on W7 X64 and not X86.
Exploit:Java/CVE=2011-3544It means your still infected with a varient of Fake Antivirus. If your getting "Exploit:Java/CVE=2011-354.E and Rogue:Win32 FakeRean
As for your post here. Well whoever that is they are going to need to flush the MBR to make sure this infection is gone. Using W7's bootrec.exe tool and running this code from a recovery console. I also forgot your on W7 X64 and not X86.
BootRec.exe /fixmbrASKER
I'll run the CTRL R in a bit.
Ref:
" As for your post here. Well whoever that is they are going to need to flush the MBR to make sure this infection is gone. Using W7's bootrec.exe tool and running this code from a recovery console. I also forgot your on W7 X64 and not X86."
I don't know what your mean
Ref:
" As for your post here. Well whoever that is they are going to need to flush the MBR to make sure this infection is gone. Using W7's bootrec.exe tool and running this code from a recovery console. I also forgot your on W7 X64 and not X86."
I don't know what your mean
Usage of bootrec.exe is explained here
ASKER
I can't get mbr to run at the command prompt.
I have this saved on my E: drive (flash drive)
mbr -d0 -t -s -l logfile.log
I have this saved on my E: drive (flash drive)
mbr -d0 -t -s -l logfile.log
ASKER
mbr is not recognized as an internal or external command
ASKER
I don't have a windows 7 installation disc. Everything was loaded on the computer from Toshiba when I bought it.
The computer still has the same virus. You are right, it's in the root system.
The computer still has the same virus. You are right, it's in the root system.
ASKER
Ref:
mbr -d0 -t -s -l logfile.log
do the dashes mean something?
mbr -d0 -t -s -l logfile.log
do the dashes mean something?
ASKER
I'll re-post this to learn how to delete this virus from the root.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Gotcha!
A man that knows and understands my skill level! I'll try it in the a.m.
Art
A man that knows and understands my skill level! I'll try it in the a.m.
Art
Any luck?
Has this been resolved?
There are tools also that checks for mbr modifications and tools like combofix will actually try and fix it if mbr has been modfied or the log will show that mbr is infected which we can then use its script function to fix the mbr.
Some variant of TDL rootkit can also render the system unbootable when running the "Bootrec /FixMbr' command if the rootkit is still active(rootkit files are still present), so I hope this isn't the case here.
There are tools also that checks for mbr modifications and tools like combofix will actually try and fix it if mbr has been modfied or the log will show that mbr is infected which we can then use its script function to fix the mbr.
Some variant of TDL rootkit can also render the system unbootable when running the "Bootrec /FixMbr' command if the rootkit is still active(rootkit files are still present), so I hope this isn't the case here.
That is ok, actually. If you remove the repair the mbr using this method an it does exactly that you know it's a TDL Infection and can just redo the boot order. TDL4 redirects the boot order and forewords through the MBR. That is why I gave instructions to make 2 disks. 1.) Repair Disk 2.) System Image Backup. The first disk will allow you to have access so you can reach the command prompt to issue the needed commands and also allow you to reinstall the operating system among other options.
I was curious because Gmer already has a different tool that detects TDL4/ZA/Alureon which only takes a few seconds and can shows the mbr status. Just wondering why that option wasn't given.
"TDL4 redirects the boot order and forewords through the MBR."
Gmer's other tool deals with that exact variant, it scans partitions and shows which partition is active and if the malicious partition has the boot flag you can run a command to activate proper partition.
Like I said if this isn't the TDL/Alureon variant that modifies the partition table and creates hidden partition then my concern is unnecessary, :)
"TDL4 redirects the boot order and forewords through the MBR."
Gmer's other tool deals with that exact variant, it scans partitions and shows which partition is active and if the malicious partition has the boot flag you can run a command to activate proper partition.
Like I said if this isn't the TDL/Alureon variant that modifies the partition table and creates hidden partition then my concern is unnecessary, :)
ASKER
I can't get it to boot from the repair disc
I made 2 repair disc and imaged the HD on 4 DVD's. I pressed f2 during start up to the boot menu for it to boot from the DVD and it still didn't work.
I made 2 repair disc and imaged the HD on 4 DVD's. I pressed f2 during start up to the boot menu for it to boot from the DVD and it still didn't work.
Have you checked to make sure you have the right boot order in your bios? Try following these directions here. Once you have ran through these instructions post back on here on what your current boot order setup as configured as. These instructions should be similar to what you have. I suspect you have hard drive as your default.
@rpggamergirl, I assume your talking about the hiearchy the of boot cycle with TDL4. You might want to take a look at bdcedit(Windows Native Tool). There is some good documentation on this as well. GMER is doing something very similar to this tool. TDL4 does not even touch the mbr(Hense, "Forwarding through"). It infects the VBR, that is why MBR checks fail for TDL4 as its not there. You have the right understanding though (Concern noted). Hope this picture helps for understanding, its from ESET's Article: TDL4 Rebooted. :)
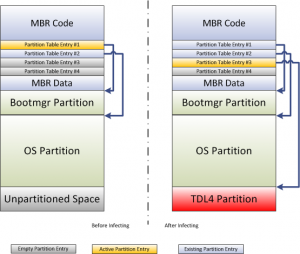

Yeah I know TDL4 doesn't infect mbr, just modifies the partition table to point to its malicious hidden partition which has the boot flag instead of the OS. I have read a few articles about it.
Yes, I have read that article and some .pdf from somewhere, :)
Yes, I have read that article and some .pdf from somewhere, :)
Thought so :)
ASKER
Ok
I booted from the CD and got a command prompt X=\sources\recovery\Tools>
The operation completed successfully.
I that all I have to do? Do I reboot regular and do a Malwarebyte scan?
I booted from the CD and got a command prompt X=\sources\recovery\Tools>
The operation completed successfully.
I that all I have to do? Do I reboot regular and do a Malwarebyte scan?
ASKER
I scanned with MalwareBytes and Microsoft Essentials and didn't find anything
Ok, are you booting into windows ok?
ASKER
Yes I booted without the CD I made, (But I always could boot normally just when I tried to get on the internet the virus came back)
It just seemed too simple to go to the prompt and type that in to cure it. I have not tried to do anything with the computer yet but it is up and running.
It just seemed too simple to go to the prompt and type that in to cure it. I have not tried to do anything with the computer yet but it is up and running.
Well be sure to update if you see the virus again. This should have wiped the startup method. If you are still getting this then we are going to need to look at more in-depth removal procedures.
ASKER
Alright,
I'll run it through the normal activities and see what happens and report back later.
Thanks,
Art
I'll run it through the normal activities and see what happens and report back later.
Thanks,
Art
ASKER
No problems. Looks like that's the best solution. Thanks for the hard work!
Art
Art
Applause!
You betcha! Thanks for allowing us to troubleshoot your issue here on EE.
ASKER
Art