Remote VPN Connection Terminated
I have configured remote access VPN on my ASA-5510 Firewall 8.4(2) using DynDNS as I do not have static IP addresses. Everything was working fine but now my users cannot access the VPN tunnel from outside. (No changes have been made on the Firewall since the last VPN setup, after which everything was working optimally).
Users are receiving the following error message:
Secure VPN connection terminated locally by the Client. Reason 412: the remote peer is no longer responding.
Also the Host name and IP address is changing properly and seems like there is no problem from Dyn DNS side. All the NAT routes are also in places and seems to be working fine but my users cannot connect.
I will highly appreciate if someone could help me on this.
Thank you,
Usman
Users are receiving the following error message:
Secure VPN connection terminated locally by the Client. Reason 412: the remote peer is no longer responding.
Also the Host name and IP address is changing properly and seems like there is no problem from Dyn DNS side. All the NAT routes are also in places and seems to be working fine but my users cannot connect.
I will highly appreciate if someone could help me on this.
Thank you,
Usman
Hi,
Dyndns not wotkink properly on ASA, so that caused the issue. You need to configre it on a host behind the ASA.
Best regards,
Istvan
Dyndns not wotkink properly on ASA, so that caused the issue. You need to configre it on a host behind the ASA.
Best regards,
Istvan
ikalmar - the ASA's do support DDNS
Here is the info from Cisco on how to configure if needed:
http://www.cisco.com/en/US/docs/security/asa/asa72/configuration/guide/dhcp.html#wp1091527
8.4 code level is out - so it's been working since 7.2...
Thanks
Here is the info from Cisco on how to configure if needed:
http://www.cisco.com/en/US/docs/security/asa/asa72/configuration/guide/dhcp.html#wp1091527
8.4 code level is out - so it's been working since 7.2...
Thanks
ASKER
Dear Travis,
I am using Cisco VPN client 5.0. Please find below the sh run:
ASA Version 8.4(2)
!
hostname
domain-name
enable password encrypted
passwd encrypted
names
name 192.168.25.0
ddns update method vpn.dyndns.org
ddns both
!
!
interface Ethernet0/0
description ADSL
nameif Outside
security-level 0
ddns update hostname vpn.dyndns.org
ddns update vpn.dyndns.org
pppoe client vpdn group
ip address pppoe setroute
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.5.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
boot system disk0:/asa842-k8i.bin
ftp mode passive
clock timezone GST 4
dns server-group DefaultDNS
domain-name
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network NETWORK_OBJ_192.168.25.0_2
subnet 192.168.25.0 255.255.255.0
object network
subnet 192.168.25.0 255.255.255.0
object-group network Infrastructure
network-object 192.168.10.0 255.255.255.0
access-list VPN_splitTunnelAcl standard permit 192.168.10.0 255.255.255.0
access-list VPN_splitTunnelAcl standard permit 192.168.20.0 255.255.255.0
access-list inside_access_in extended permit ip any any
access-list Outside_access_in extended deny ip any any
pager lines 24
logging enable
logging asdm-buffer-size 512
logging asdm informational
mtu Outside 1500
mtu inside 1500
mtu management 1500
ip local pool Pool 192.168.25.1-192.168.25.25
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,Outside) source static any any destination static VPN remote-VPN
!
object network obj_any
nat (inside,Outside) dynamic interface
access-group Outside_access_in in interface Outside
access-group inside_access_in in interface inside
route inside 192.168.0.0 255.255.0.0 192.168.5.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
ldap attribute-map LDAP_memberOf
map-name memberOf Group-Policy
map-value memberOf "CN=VPN User,CN=Users,DC=,DC=com" RemoteAccess_VPN
dynamic-access-policy-reco
aaa-server protocol nt
aaa-server (inside) host 192.168.10.32
server-port 389
nt-auth-domain-controller 192.168.10.32
aaa-server (inside) host 192.168.10.33
server-port 339
nt-auth-domain-controller 192.168.10.33
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.10.0 255.255.255.0 inside
http 192.168.20.0 255.255.255.0 inside
http 192.168.30.0 255.255.255.0 inside
http 192.168.40.0 255.255.255.0 inside
http 192.168.50.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-A
ES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-A
ES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES2
56 AES192 AES 3DES DES
crypto map Outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map Outside_map interface Outside
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable Outside client-services port 443
crypto ikev1 enable Outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 192.168.10.0 255.255.255.0 inside
telnet 192.168.50.0 255.255.255.0 inside
telnet 192.168.40.0 255.255.255.0 inside
telnet 192.168.30.0 255.255.255.0 inside
telnet 192.168.20.0 255.255.255.0 inside
telnet timeout 5
ssh timeout 5
console timeout 0
management-access inside
vpdn group request dialout pppoe
vpdn group localname
vpdn group ppp authentication pap
vpdn username password store-local
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
dhcp-client update dns server both
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable Outside
tunnel-group-list enable
group-policy internal
group-policy attributes
dns-server value 192.168.10.33 192.168.10.32
vpn-tunnel-protocol ikev1 ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value _splitTunnelAcl
default-domain value
tunnel-group type remote-access
tunnel-group general-attributes
address-pool
authentication-server-grou
default-group-policy
tunnel-group webvpn-attributes
group-alias enable
tunnel-group ipsec-attributes
ikev1 pre-shared-key
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class class-default
user-statistics accounting
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DD
CEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:5c4c2bf8e9e
: end
I am using Cisco VPN client 5.0. Please find below the sh run:
ASA Version 8.4(2)
!
hostname
domain-name
enable password encrypted
passwd encrypted
names
name 192.168.25.0
ddns update method vpn.dyndns.org
ddns both
!
!
interface Ethernet0/0
description ADSL
nameif Outside
security-level 0
ddns update hostname vpn.dyndns.org
ddns update vpn.dyndns.org
pppoe client vpdn group
ip address pppoe setroute
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.5.1 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
nameif management
security-level 100
ip address 192.168.1.1 255.255.255.0
management-only
!
boot system disk0:/asa842-k8i.bin
ftp mode passive
clock timezone GST 4
dns server-group DefaultDNS
domain-name
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network NETWORK_OBJ_192.168.25.0_2
subnet 192.168.25.0 255.255.255.0
object network
subnet 192.168.25.0 255.255.255.0
object-group network Infrastructure
network-object 192.168.10.0 255.255.255.0
access-list VPN_splitTunnelAcl standard permit 192.168.10.0 255.255.255.0
access-list VPN_splitTunnelAcl standard permit 192.168.20.0 255.255.255.0
access-list inside_access_in extended permit ip any any
access-list Outside_access_in extended deny ip any any
pager lines 24
logging enable
logging asdm-buffer-size 512
logging asdm informational
mtu Outside 1500
mtu inside 1500
mtu management 1500
ip local pool Pool 192.168.25.1-192.168.25.25
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,Outside) source static any any destination static VPN remote-VPN
!
object network obj_any
nat (inside,Outside) dynamic interface
access-group Outside_access_in in interface Outside
access-group inside_access_in in interface inside
route inside 192.168.0.0 255.255.0.0 192.168.5.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
ldap attribute-map LDAP_memberOf
map-name memberOf Group-Policy
map-value memberOf "CN=VPN User,CN=Users,DC=,DC=com" RemoteAccess_VPN
dynamic-access-policy-reco
aaa-server protocol nt
aaa-server (inside) host 192.168.10.32
server-port 389
nt-auth-domain-controller 192.168.10.32
aaa-server (inside) host 192.168.10.33
server-port 339
nt-auth-domain-controller 192.168.10.33
user-identity default-domain LOCAL
http server enable
http 192.168.1.0 255.255.255.0 management
http 192.168.10.0 255.255.255.0 inside
http 192.168.20.0 255.255.255.0 inside
http 192.168.30.0 255.255.255.0 inside
http 192.168.40.0 255.255.255.0 inside
http 192.168.50.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group1
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-A
ES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-A
ES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES2
56 AES192 AES 3DES DES
crypto map Outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map Outside_map interface Outside
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable Outside client-services port 443
crypto ikev1 enable Outside
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 192.168.10.0 255.255.255.0 inside
telnet 192.168.50.0 255.255.255.0 inside
telnet 192.168.40.0 255.255.255.0 inside
telnet 192.168.30.0 255.255.255.0 inside
telnet 192.168.20.0 255.255.255.0 inside
telnet timeout 5
ssh timeout 5
console timeout 0
management-access inside
vpdn group request dialout pppoe
vpdn group localname
vpdn group ppp authentication pap
vpdn username password store-local
no vpn-addr-assign aaa
no vpn-addr-assign dhcp
dhcp-client update dns server both
dhcpd address 192.168.1.2-192.168.1.254 management
dhcpd enable management
!
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
enable Outside
tunnel-group-list enable
group-policy internal
group-policy attributes
dns-server value 192.168.10.33 192.168.10.32
vpn-tunnel-protocol ikev1 ikev2 ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value _splitTunnelAcl
default-domain value
tunnel-group type remote-access
tunnel-group general-attributes
address-pool
authentication-server-grou
default-group-policy
tunnel-group webvpn-attributes
group-alias enable
tunnel-group ipsec-attributes
ikev1 pre-shared-key
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
class class-default
user-statistics accounting
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DD
CEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:5c4c2bf8e9e
: end
ASKER
Dear Istvan,
How to do that? Before a week everything was working just fine. Can you please put more light on this?
Tks.
How to do that? Before a week everything was working just fine. Can you please put more light on this?
Tks.
Thanks for posting the config - can you also try to establish the vpn connection from a client and while you are attempting to connect capture the logs on either the ASDM via the console log or via a debug capture via the CLI? If you need assistance on either just let me know.
Travis.
Travis.
ASKER
Dear Travis,
Find below the logs that I captured from ASDM:
translation from inside:192.168.20.101/6431
6|Jan 03 2012|13:11:20|302013|192.1
6|Jan 03 2012|13:11:20|305011|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
4|Jan 03 2012|13:11:20|106023|178.9
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|305012|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
4|Jan 03 2012|13:11:19|106023|219.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302013|192.1
6|Jan 03 2012|13:11:19|305011|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302014|74.20
6|Jan 03 2012|13:11:19|302014|74.20
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
4|Jan 03 2012|13:11:19|106023|210.2
6|Jan 03 2012|13:11:19|305012|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|305012|192.1
6|Jan 03 2012|13:11:18|305012|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302013|192.1
6|Jan 03 2012|13:11:18|305011|192.1
6|Jan 03 2012|13:11:17|302014|192.1
6|Jan 03 2012|13:11:17|302015|192.1
6|Jan 03 2012|13:11:17|302015|192.1
Find below the logs that I captured from ASDM:
translation from inside:192.168.20.101/6431
6|Jan 03 2012|13:11:20|302013|192.1
6|Jan 03 2012|13:11:20|305011|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
4|Jan 03 2012|13:11:20|106023|178.9
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|305012|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:20|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
4|Jan 03 2012|13:11:19|106023|219.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302013|192.1
6|Jan 03 2012|13:11:19|305011|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302014|74.20
6|Jan 03 2012|13:11:19|302014|74.20
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
6|Jan 03 2012|13:11:19|302015|192.1
4|Jan 03 2012|13:11:19|106023|210.2
6|Jan 03 2012|13:11:19|305012|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|305012|192.1
6|Jan 03 2012|13:11:18|305012|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302015|192.1
6|Jan 03 2012|13:11:18|302013|192.1
6|Jan 03 2012|13:11:18|305011|192.1
6|Jan 03 2012|13:11:17|302014|192.1
6|Jan 03 2012|13:11:17|302015|192.1
6|Jan 03 2012|13:11:17|302015|192.1
ASKER
I need urgent help to resolve this problem.
Hi,
on the remote client you need to stop/disable ICS (Internet Connection Sharing) service. Then start the vpn client, i believe it will work
max
on the remote client you need to stop/disable ICS (Internet Connection Sharing) service. Then start the vpn client, i believe it will work
max
ASKER
Max,
It is already disabled in the connection setting of VPN network connection.
It is already disabled in the connection setting of VPN network connection.
what do you mean ?
max
max
ASKER
Max,
in the network connection settings of VPN network adapter there is no check mark enabled for ICS.
in the network connection settings of VPN network adapter there is no check mark enabled for ICS.
ASKER
2012|16:50:12|106015|168.1
I found the above logs in ASDM.
I found the above logs in ASDM.
ASKER
above logs are generated in ASDM when I tried connectiong to remote VPN using the client.
it is a matter of operating system, you need to cahnge the setting i inidicated in previous post on the PC:
go to services.msc and stop/disable ICS
max
go to services.msc and stop/disable ICS
max
ASKER
Max,
When I am trying the remote VPN the ICS is not started. Anyway I disabled it but still cannot connect.
When I am trying the remote VPN the ICS is not started. Anyway I disabled it but still cannot connect.
Port 10000 is blocked.....
Is the client trying to use IPSec over TCP?
Is the client trying to use IPSec over TCP?
ASKER
I tried that and enable IPsec over TCP 1000. but it is also not working.
Right now it is configured with UDP/NAT. Do you think that a restart will do anything?
Right now it is configured with UDP/NAT. Do you think that a restart will do anything?
Well it's a kind of MS solution ;)
But it sometimes works for me. It wouldn't hurt to give it a try.
But it sometimes works for me. It wouldn't hurt to give it a try.
Been thinking, can the clients ping the ASA? And does it resolve to the correct IP?
ASKER
Yes ping to the Host which i generated with DynDNS and which is pointing to the firewall IP address is working. I receive the replyies.
Mmm, ok.
Then let's try the pragmatic approach and give a reload to see what happens.
Then let's try the pragmatic approach and give a reload to see what happens.
ASKER
I reloaded the firewall but still the same. Same error.
When connecting with UDP/NAT, do you see any denies in the log?
For example port 500?
Also when you issue a 'deb cryp ips sa' and 'deb cryp is sa' on the ASA, do you see anything happening?
For example port 500?
Also when you issue a 'deb cryp ips sa' and 'deb cryp is sa' on the ASA, do you see anything happening?
'deb cry isa', and 'deb cry ips' tell what is the problem.... plese show the output....
midwestgurus: ASA not supporting properly Dyndns, the is no oppurtunity to set username and password....
midwestgurus: ASA not supporting properly Dyndns, the is no oppurtunity to set username and password....
@ikalmar: crosspost :) And btw, happy new year!
@usmanshaikh: ikalmar has got a point, Dyndns and ASA are not always working quite as it should I'm afraid.
@usmanshaikh: ikalmar has got a point, Dyndns and ASA are not always working quite as it should I'm afraid.
ASKER
So what should be my final steps. Shall i enable IPsec over TCP and allow 1000 port on outside network?
See if that works so we get the vpns up again.
Anything on the debugging?
Anything on the debugging?
Perhaps a long shot, but did the provider change anything (like blocking ports/protocols)?
ASKER
I have no idea about that but found more logs for you guys from ASDM:
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
6|Jan 03 2012|18:23:59|302016|168.1
2012|18:23:59|302016|168.1
@erniebeek: Happy new year
@usmanshaikh:: there is no log for IPSEC:(
@usmanshaikh:: there is no log for IPSEC:(
ASKER
Man can you provide me remote access?
ASKER
I am really stuck and not understanding the issue because seems like the TCP traffic is reaching up to the FW.
Hey usmanshaikh,
Sorry for the delay getting back with you.. needed to catch some shut-eye..
Can you send me some more info on the setup?
What is the external IP address one of the VPN clients is coming from?
What is the current external IP address of the ASA as well as the dyn-dns name used?
You mentioned that you see the traffic reaching the ASA - so I want to get the above info from you so I can look into the problem a little more.
Thanks,
Travis.
Sorry for the delay getting back with you.. needed to catch some shut-eye..
Can you send me some more info on the setup?
What is the external IP address one of the VPN clients is coming from?
What is the current external IP address of the ASA as well as the dyn-dns name used?
You mentioned that you see the traffic reaching the ASA - so I want to get the above info from you so I can look into the problem a little more.
Thanks,
Travis.
In my DNS cpn.dyndns-org shows 93.21.208.121
ASKER
External IP: 168.187.137.179, 168.187.24.114
Cisco ASA current IP: 2.50.15.172
DNS Name: qib-vpn.dyndns.org
Cisco ASA current IP: 2.50.15.172
DNS Name: qib-vpn.dyndns.org
Do me a favor - on one of the clients say 168.187.137.179 change the Cisco VPN client profile to point to the actually IP currently assigned to the outside interface of the ASA (2.50.15.172) and see if it connects for me.
Thanks.
Thanks.
ASKER
Dear Guru,
I tried that earlier with the IP but no benefit. I can ping the hostname as well the IP BTW.
I tried that earlier with the IP but no benefit. I can ping the hostname as well the IP BTW.
Try to set up the debugging (from a console connection). With a bit of luck this might tell us more.
ASKER
can you tell me wht it is and how to configure it?
Hi again,
So we know at this point then that dynamic DNS is not to blame on the problem since using the actual IP doesn't work either..
Since you have the ASDM let's make sure the logging filter is set correctly to capture the info needed - I attached a screenshot. Once this setting is made go to your home screen and what the latest ADSM syslog messages and look for the client at 168.187.137.179 trying to connect - you can stop the logs from scrolling once you see something.. please post the results.
Thanks Usman -
This link is just for your info:
http://www.cisco.com/en/US/tech/tk583/tk372/technologies_tech_note09186a00800949c5.shtml
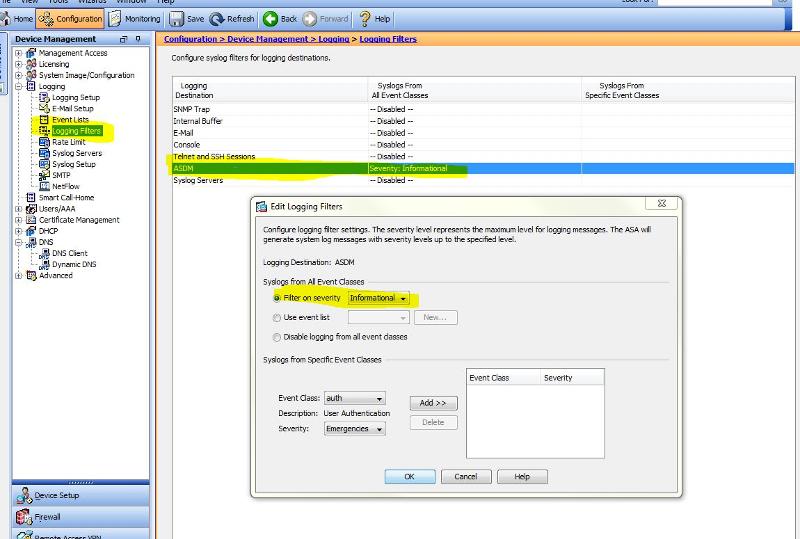
So we know at this point then that dynamic DNS is not to blame on the problem since using the actual IP doesn't work either..
Since you have the ASDM let's make sure the logging filter is set correctly to capture the info needed - I attached a screenshot. Once this setting is made go to your home screen and what the latest ADSM syslog messages and look for the client at 168.187.137.179 trying to connect - you can stop the logs from scrolling once you see something.. please post the results.
Thanks Usman -
This link is just for your info:
http://www.cisco.com/en/US/tech/tk583/tk372/technologies_tech_note09186a00800949c5.shtml
ASKER
Now a new thing, I enabled the logging as recommended and now I cannot see any Traffic coming to my firewall from that IP address. I started the Ping from the client machine and I can successfully see the ICMP traffic:
Jan 03 2012 21:54:04 168.187.24.114 53276 2.50.15.172.0 Teardown ICMP connection for faddr 168.187.24.114/53276 gaddr 2.50.15.172/0 laddr 2.50.15.172/0
6 Jan 03 2012 21:54:04 168.187.24.114 53276 2.50.15.172 0 Built inbound ICMP connection for faddr 168.187.24.114/53276 gaddr 2.50.15.172/0 laddr 2.50.15.172/0
Jan 03 2012 21:54:04 168.187.24.114 53276 2.50.15.172.0 Teardown ICMP connection for faddr 168.187.24.114/53276 gaddr 2.50.15.172/0 laddr 2.50.15.172/0
6 Jan 03 2012 21:54:04 168.187.24.114 53276 2.50.15.172 0 Built inbound ICMP connection for faddr 168.187.24.114/53276 gaddr 2.50.15.172/0 laddr 2.50.15.172/0
I see - so you don't see the 168.187.24.114 trying to setup a VPN session?
Are you still getting 412 on the client side? Also is the 2.50.15.172 IP address that is on the ASA in the USA? Just want to make sure that is really your outside address.
Can you do me another favor? - go to a client machine that is behind the ASA and go out to http://www.ipchicken.com - I want to see what the IP that site says your coming from, we need to be 100% it's 2.50.15.172..
Thanks - below is a lookup on that address as the first octect "2" threw me off a little.
WHOIS - 2.50.15.172
Location: United Arab Emirates [City: Dubai, Dubai]
[Note: Using 2.0.0.0 instead of 2.50.15.172, to save time and bandwidth]
ARIN says that this IP belongs to RIPE; I'm looking it up there.
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Information related to '2.50.12.0 - 2.50.19.255'
inetnum: 2.50.12.0 - 2.50.19.255
netname: ETISALATADSL-EMIRNET
descr: Emirates Telecommunications Corporation
descr: P O Box 1150, Dubai, UAE
country: AE
admin-c: AK915-RIPE
tech-c: AK915-RIPE
status: ASSIGNED PA
mnt-by: ETISALAT-MNT
mnt-lower: ETISALAT-MNT
mnt-routes: ETISALAT-MNT
changed: ***@nic.ae 20100928
source: RIPE
person: Arif Khalid
address: Emirates Telecommunications Corporation
address: P O Box 1150, Dubai, UAE
phone: +971 800 6100
fax-no: +971 4 2959876
e-mail: ***@nic.ae
remarks: For any kind of abuse orignating from our network please
remarks: email *****@emirates.net.ae
nic-hdl: AK915-RIPE
mnt-by: ETISALAT-MNT
changed: ***@nic.ae 20080619
source: RIPE
[The following lines added by www.dnsstuff.com per requirement by RIPE]
This service is subject to the terms and conditions stated in the RIPE NCC Database Copyright Notice.
Contact dnsstuff.com's 'info2@' address to report problems regarding the functionality of the service
Are you still getting 412 on the client side? Also is the 2.50.15.172 IP address that is on the ASA in the USA? Just want to make sure that is really your outside address.
Can you do me another favor? - go to a client machine that is behind the ASA and go out to http://www.ipchicken.com - I want to see what the IP that site says your coming from, we need to be 100% it's 2.50.15.172..
Thanks - below is a lookup on that address as the first octect "2" threw me off a little.
WHOIS - 2.50.15.172
Location: United Arab Emirates [City: Dubai, Dubai]
[Note: Using 2.0.0.0 instead of 2.50.15.172, to save time and bandwidth]
ARIN says that this IP belongs to RIPE; I'm looking it up there.
% This is the RIPE Database query service.
% The objects are in RPSL format.
%
% The RIPE Database is subject to Terms and Conditions.
% See http://www.ripe.net/db/support/db-terms-conditions.pdf
% Information related to '2.50.12.0 - 2.50.19.255'
inetnum: 2.50.12.0 - 2.50.19.255
netname: ETISALATADSL-EMIRNET
descr: Emirates Telecommunications Corporation
descr: P O Box 1150, Dubai, UAE
country: AE
admin-c: AK915-RIPE
tech-c: AK915-RIPE
status: ASSIGNED PA
mnt-by: ETISALAT-MNT
mnt-lower: ETISALAT-MNT
mnt-routes: ETISALAT-MNT
changed: ***@nic.ae 20100928
source: RIPE
person: Arif Khalid
address: Emirates Telecommunications Corporation
address: P O Box 1150, Dubai, UAE
phone: +971 800 6100
fax-no: +971 4 2959876
e-mail: ***@nic.ae
remarks: For any kind of abuse orignating from our network please
remarks: email *****@emirates.net.ae
nic-hdl: AK915-RIPE
mnt-by: ETISALAT-MNT
changed: ***@nic.ae 20080619
source: RIPE
[The following lines added by www.dnsstuff.com per requirement by RIPE]
This service is subject to the terms and conditions stated in the RIPE NCC Database Copyright Notice.
Contact dnsstuff.com's 'info2@' address to report problems regarding the functionality of the service
ASKER
I am sure that this the correct IP my firewall is connected to. Here is the result from http://www.ipchicken.com/
2.50.15.172
I dont see the 168.187.24.114 trying to establish VPN connection and still I am facing 412 error message.
I am located in dubai.
2.50.15.172
I dont see the 168.187.24.114 trying to establish VPN connection and still I am facing 412 error message.
I am located in dubai.
ASKER
I am thinking now to recreate the VPN tunnel. Delete the old one and create everything from scratch.
If you want to us tcp/10000 for remote vpn you need:
crypto isakmp ipsec-over-tcp port 10000
I think there is a problem with the von endpoint settings.....
crypto isakmp ipsec-over-tcp port 10000
I think there is a problem with the von endpoint settings.....
Thanks for the verification - I'm thinking it could be something from client end, but a good test would be try it from a different location/remote site. if you don't have another site to test from, I can try to initiate a test from my end and see if you can find my address in the logs -- I would need the PCF file if you wanted to go that option..
The fact that you don't see any VPN connection trying to be made from the ASA means the client isn't getting their.. on your last test were you using the IP vs. the DYNDNS name?
----
One of the problems with using the older VPN Client is that some firewalls will block IPSEC and you have to enable an IPSEC pass-through option... Just for future reference check out AnyConnect, all you need is an AnyConnect Essentials license and you can support SSL VPN and not have to worry about firewalls from the remote side..
The fact that you don't see any VPN connection trying to be made from the ASA means the client isn't getting their.. on your last test were you using the IP vs. the DYNDNS name?
----
One of the problems with using the older VPN Client is that some firewalls will block IPSEC and you have to enable an IPSEC pass-through option... Just for future reference check out AnyConnect, all you need is an AnyConnect Essentials license and you can support SSL VPN and not have to worry about firewalls from the remote side..
ASKER
Dear Gurus,
I tried it from 2 different locations and it is giving me the same error message. My users are also banging at my door. Yes my last try was with IP vs DynDNS. I have no issue sending you the PCF file but unfortunately i deleted the VPN tunnel and working to create it again as fresh.
Thanks for the recommendations, will try that as well.
I tried it from 2 different locations and it is giving me the same error message. My users are also banging at my door. Yes my last try was with IP vs DynDNS. I have no issue sending you the PCF file but unfortunately i deleted the VPN tunnel and working to create it again as fresh.
Thanks for the recommendations, will try that as well.
Okay good to know - I would agree with you then on trying to re-create the VPN setup. After you finished configuring again and if it still doesn't work - just post the "sh run" again. I'll take a fine tooth comb to it :)
Thanks,
Thanks,
ASKER
Thanks all. Will update you if succeeded.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Glad it's working!
Hope it stays working for you!! :)
Nice working with you - take care.
Travis.
Hope it stays working for you!! :)
Nice working with you - take care.
Travis.
Good!!
As said above: glad it's working. If any troubles arise again, we'll be here :)
As said above: glad it's working. If any troubles arise again, we'll be here :)
ASKER
I fixed the problem myself but anyway I would like to thank the experts for their help.
Is it possible to upload a "show run"?
Also if you go into the ASDM, and turn on console logging with warning events or debug events do you see the clients hitting the ASA when trying to terminate the VPN connection?
Also are you using the VPN Client or the SSL Anyconnect client?
Travis.