pfsense router and comcast setup
Greetings,
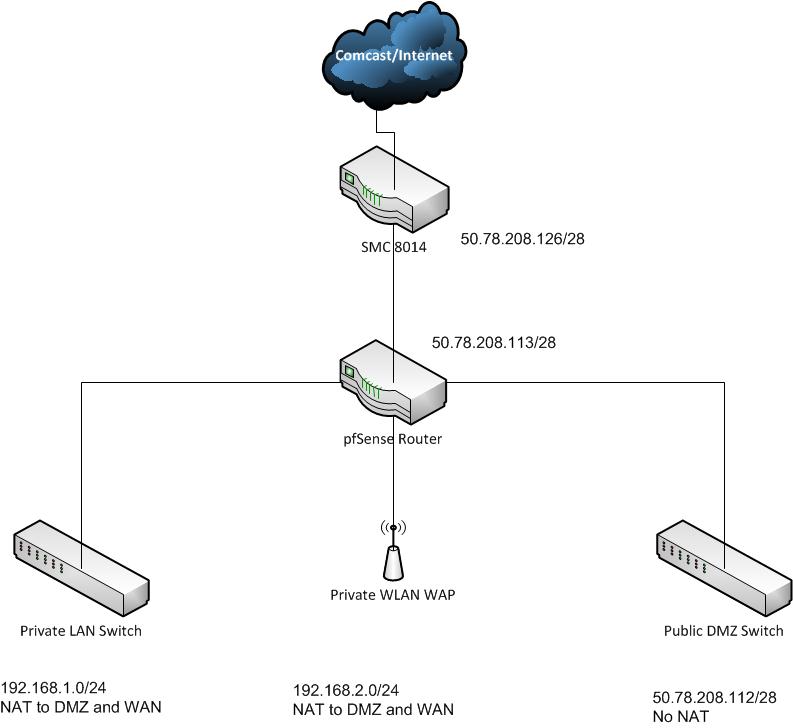
I have a comcast business WAN connection. I've also requested a block of CIDR/28 addresses. The internal side of the cable router utilizes this address space. I'm unable to physically bridge the cable router, and I can't figure out how to use the CIDR/28 addresses in a DMZ subnet on the inside of my pfsense router...the pfsense router is connected to the cable router using one of the CIDR/28 addresses. What's the best way to set this up so that the DMZ on the inside of the pfsense router can utilize the CIDR addresses, while still providing packet filtering/NATing? How would I go about setting up the gateways?
Thanks in advance for your advice.
-Herald
I have a comcast business WAN connection. I've also requested a block of CIDR/28 addresses. The internal side of the cable router utilizes this address space. I'm unable to physically bridge the cable router, and I can't figure out how to use the CIDR/28 addresses in a DMZ subnet on the inside of my pfsense router...the pfsense router is connected to the cable router using one of the CIDR/28 addresses. What's the best way to set this up so that the DMZ on the inside of the pfsense router can utilize the CIDR addresses, while still providing packet filtering/NATing? How would I go about setting up the gateways?
Thanks in advance for your advice.
-Herald
What is the brand and model of the comcast modem?
ASKER
Sorry, it's an SMC 8014
A /28 should give you 14 IPs... and typically, the ISP will give you 13 of them and keep one to use as your Gateway IP, which would really be a port on their layer 3 managed switch.
1 of those 13 IPs will be assigned to the WAN port of the SMC (that's the Gateway to your /28 from Comcast's end); that leaves you 12 IPs. All 12 of those should be covered by a static route that sends traffic back and forth to the Gateway address at Comcast, and the route on their end sends all traffic bound for your /28 range to the IP address assigned to your SMC's WAN port.
If their instructions aren't clear how to do that, you should be able to call their Biz support, and they should be able to configure the SMC remotely for you. That should be included in the Biz service (i.e. it should not cost anything extra for them to do that).
If you want to use another router to do NAT to a private range on your LAN, give its WAN port one of those 12 IPs and connect it to the SMC (you'll need a couple/few simple dumb switches to break out enough ports for all 12 IPs from the 4 ports on the SMC). I don't see why you would need to use any DMZ at all, though.
Check out this message - http://www.dslreports.com/forum/r20013082-
To see that whole thread, click the " [Connectivity] Attn: Former Insight sticky IP customers" part of the 'bread crumb trail' at the top.
1 of those 13 IPs will be assigned to the WAN port of the SMC (that's the Gateway to your /28 from Comcast's end); that leaves you 12 IPs. All 12 of those should be covered by a static route that sends traffic back and forth to the Gateway address at Comcast, and the route on their end sends all traffic bound for your /28 range to the IP address assigned to your SMC's WAN port.
If their instructions aren't clear how to do that, you should be able to call their Biz support, and they should be able to configure the SMC remotely for you. That should be included in the Biz service (i.e. it should not cost anything extra for them to do that).
If you want to use another router to do NAT to a private range on your LAN, give its WAN port one of those 12 IPs and connect it to the SMC (you'll need a couple/few simple dumb switches to break out enough ports for all 12 IPs from the 4 ports on the SMC). I don't see why you would need to use any DMZ at all, though.
Check out this message - http://www.dslreports.com/forum/r20013082-
To see that whole thread, click the " [Connectivity] Attn: Former Insight sticky IP customers" part of the 'bread crumb trail' at the top.
Oh... and if they didn't give you ANY instructions on how to set it up, you need to disable the SMC's DHCP server and firewall.
I find conflicting info to disable the firewall... online someone said to
check the box next to Disable Firewall for True Static IP Subnet Only in its Firewall settings.
But in its manual it says to just UNcheck the Enable Firewall Module box.

I find conflicting info to disable the firewall... online someone said to
check the box next to Disable Firewall for True Static IP Subnet Only in its Firewall settings.
But in its manual it says to just UNcheck the Enable Firewall Module box.

ASKER
Thanks, I appreciate the time you took explaining all that. I'm pretty good up to that point. My problem is that I have internet facing servers and I have private servers and workstations. The whole reason I'm running my own router is to gain added security benefits. I can't run spam filtering and antivirus detection on the SMC router, so I'm installing my own that will. My problem is that I want to be able to protect and limit the traffic to my internet facing systems. Typically, this is done in a DMZ. Due to the limitations of the SMC and the necessities of its configuration, I can't have the DMZ in between the two different routers and still get the kind of protection I want. Thus, I want to bring the DMZ behind my internal router (running pfsense), but I'd really rather not have to set up 1:1 NAT. I can set up a bridge, but I'm not sure if it's a good idea bridging an internal interface with a WAN interface. I might be able to set up some static routes, but I'd need some hand holding to do that.
That's primarily what I'm looking for help on at this point.
That's primarily what I'm looking for help on at this point.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I found the vendor recommended way to do exactly what I'm trying to do.