Cisco Switch Design for a Small Datacenter
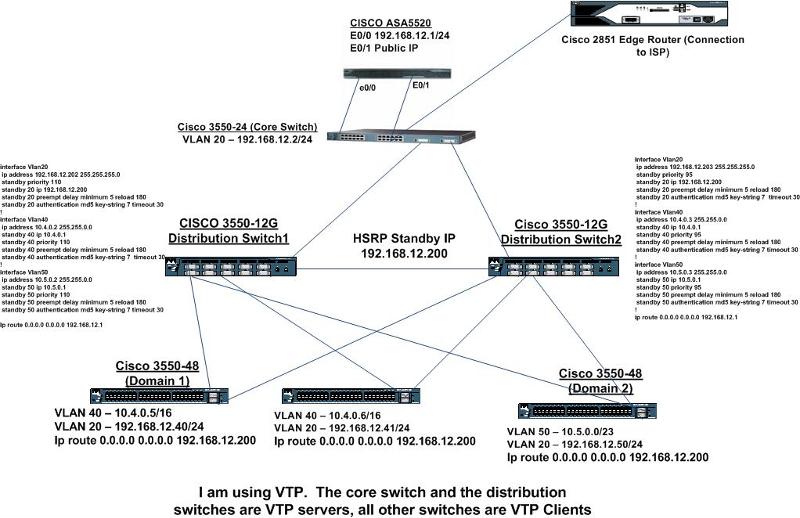
I have to put together a quick design for a small datacenter. Below you will see a diagram of my network so far. As far as switching goes, I have two Cisco 3550-12Gs configured with HSRP, these are my distribution switches. I have two domains, domain1 and domain2, both domains are on their own vlan. I am trunking the uplink ports on all switches to the distribution switches. At the moment I have this setup in a lab and everything is working. I just want to make sure that I have HSRP, VTP, and STP configured correctly before I go changing this in production. I will attach my configurations of the distribution switches so you can see my HSRP config. As far as VTP goes, the Core Switch and the Distribution Switches are VTP Servers, and all other switches are VTP Clients. All Switches are on the same VTP Domain and have the same password. As far as Spanning-Tree goes, I have done nothing, all STP settings are default. Please have look and let me know what you think. Any suggestions for improving this setup would be appreciated. Thanks.
 Distribution-Switch-1.txt
Distribution-Switch-1.txt
Distribution-Switch-2.txt
 Distribution-Switch-1.txt
Distribution-Switch-1.txtDistribution-Switch-2.txt
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Set the spanning tree root for each VLAN (don't forget VLAN 1) to the switch that has the lower HSRP priority. Set the secondary root to the switch that has highest HSRP priority.
>Do I need to make any spanning-tree changes on the 3550 that sits behind the firewall that these 3550-12Gs go to?
No, since you have set the root bridges for all VLAN this switch will adapt to the spanning tree as well.
>Do I need to make any spanning-tree changes on the 3550 that sits behind the firewall that these 3550-12Gs go to?
No, since you have set the root bridges for all VLAN this switch will adapt to the spanning tree as well.
ASKER
Thanks mar1458, I set the spanning tree root for each vlan in my test lab, it brought everything down for a few seconds, then everything came back up again. I appreciate all your help. I have downtime schedules tomorrow night to do all this in production at the datacenter. Is there anything you else you feel I should look at in regards to switching? If not I'll close the case and award points. Thanks.
In my opinion it would be worth having a look at Rapid Spanning Tree. I don't know if the 3550 with your sorftware support it, but with your small network it might bring down recalculation times a whole lot. Try if you can set RSTP on all switches and do some unplugging while running pings across your test network.
ASKER
Thanks. I was reading a little bit about RSTP. To enable RSTP, do I just enter the following on each switch?
spanning-tree mode rapid-pvst
spanning-tree mode rapid-pvst
Sounds good to me, however you have to test if it works with the 3550s and your current software version.
ASKER
Last question. I have not configured RSTP yet, but just for testing I unplugged one of the 3550-12Gs. When I did this I lost about 6 pings before traffic started passing again. Is this normal with HSRP?
It's not HSRP that takes so long, it's spanning tree. STP is very old and takes its time to converge. It can take up to 50 seconds until traffic flows again. That's why it suggested RSTP.
ASKER
Thanks. If I give a server in vlan 40 (10.4.0.0/16) for example the default gateway of vlan 5 (10.5.0.1) I can still pass traffic without issues. Is there something I can do so this doesn't happen?
Yes, there is. But why would you want to do that?
Actually your system recognizes that the default gateway does not belong to its own subnet and it sends out an ARP for the destination address that it wants to reach. The switch sees the ARP and recognizes that somebody is sending out ARPs for systems that do not belong to the VLAN the ARP is being sent out. The switch then replies to the ARP by sending its own MAC address together with the destination IP address and that's why it all works.
You can disable it by using
no ip proxy-arp
on the VLAN interface in which you have the system with the wrong default gateway. For testing purposes don't forget to remove the ARP entry out of the PCs cache (arp -d probably).
Actually your system recognizes that the default gateway does not belong to its own subnet and it sends out an ARP for the destination address that it wants to reach. The switch sees the ARP and recognizes that somebody is sending out ARPs for systems that do not belong to the VLAN the ARP is being sent out. The switch then replies to the ARP by sending its own MAC address together with the destination IP address and that's why it all works.
You can disable it by using
no ip proxy-arp
on the VLAN interface in which you have the system with the wrong default gateway. For testing purposes don't forget to remove the ARP entry out of the PCs cache (arp -d probably).
ASKER
Thanks for all your help mat1458. I had scheduled downtime at the datacenter last night, and it went very smooth due to your help. I appreciate your time.
You're very welcome. Good luck with your change.
ASKER
Primary 3550-12G
spanning-tree vlan 20 root secondary
spanning-tree vlan 40 root secondary
spanning-tree vlan 50 root primary
Secondary 3550-12G
spanning-tree vlan 20 root primary
spanning-tree vlan 40 root primary
spanning-tree vlan 50 root secondary
Do I need to make any spanning-tree changes on the 3550 that sits behind the firewall that these 3550-12Gs go to? Thanks.