Cisco ASA 5505 and Cisco Small Business WRVS4400N VPN tunnel
I didn't receive any responses the first time I asked this question over two weeks ago, so I'll ask again.
I'm trying to establish a VPN tunnel between our main office running a Cisco ASA 5505 [8.3(2)] and a remote user using a Cisco Small Business WRVS4400N firmware version V2.0.1.3.
The Cisco ASA 5505 is already configured to allow incoming IPSec VPN connections via the Cisco VPN Client.
Is this possible, and if so, how would I go about doing so? The remote user has a static IP address as well as the main office.
Any information provided would be appreciated. Thanks
I'm trying to establish a VPN tunnel between our main office running a Cisco ASA 5505 [8.3(2)] and a remote user using a Cisco Small Business WRVS4400N firmware version V2.0.1.3.
The Cisco ASA 5505 is already configured to allow incoming IPSec VPN connections via the Cisco VPN Client.
Is this possible, and if so, how would I go about doing so? The remote user has a static IP address as well as the main office.
Any information provided would be appreciated. Thanks
Is the VPN pass-thru option selected/enabled on the WRV device? Also, please clarify a little...Are you looking to enable a site to site vpn or just allow the remote user to access local resources that sit behind the ASA? Let us know.
ASKER
I'm looking to build a Site to Site tunnel between the remote user's house and the office.
Assuming you are not sure on how to configure site to site vpn on ASA, please go through the below link
https://learningnetwork.cisco.com/docs/DOC-8696
If you have ASDM then,
http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080a9a7a3.shtml
Once you configure on ASA, its pretty easy to connect from other device.
https://learningnetwork.cisco.com/docs/DOC-8696
If you have ASDM then,
http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080a9a7a3.shtml
Once you configure on ASA, its pretty easy to connect from other device.
ASKER
The ASA is already configured to allow incoming IPSec VPN Client connections via the Cisco VPN Client. The issue I'm having is how to configure the Cisco WRVS4400N.
I've setup site to site VPN tunnels before using two or more ASA5505's. I'm just wanting to know how, if it can be done, to do so using the WRVS4400N's.
Thanks for the responses and looking forward to working towards a solution.
I've setup site to site VPN tunnels before using two or more ASA5505's. I'm just wanting to know how, if it can be done, to do so using the WRVS4400N's.
Thanks for the responses and looking forward to working towards a solution.
connection using Cisco VPN Client and Cisco Site to Site is totally different.
You have to set up Site to Site VPN on ASA and WRV.
here are the steps for WRV
http://www.cisco.com/en/US/docs/routers/csbr/wrvs4400n/administration/guide/WRVS4400N_AG_OL-20048.pdf - page 203.
Once you setup WRV router, follow the instructions on
https://learningnetwork.cisco.com/docs/DOC-8696
If you have ASDM then,
http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080a9a7a3.shtml
You have to set up Site to Site VPN on ASA and WRV.
here are the steps for WRV
http://www.cisco.com/en/US/docs/routers/csbr/wrvs4400n/administration/guide/WRVS4400N_AG_OL-20048.pdf - page 203.
Once you setup WRV router, follow the instructions on
https://learningnetwork.cisco.com/docs/DOC-8696
If you have ASDM then,
http://www.cisco.com/en/US/products/ps5855/products_configuration_example09186a0080a9a7a3.shtml
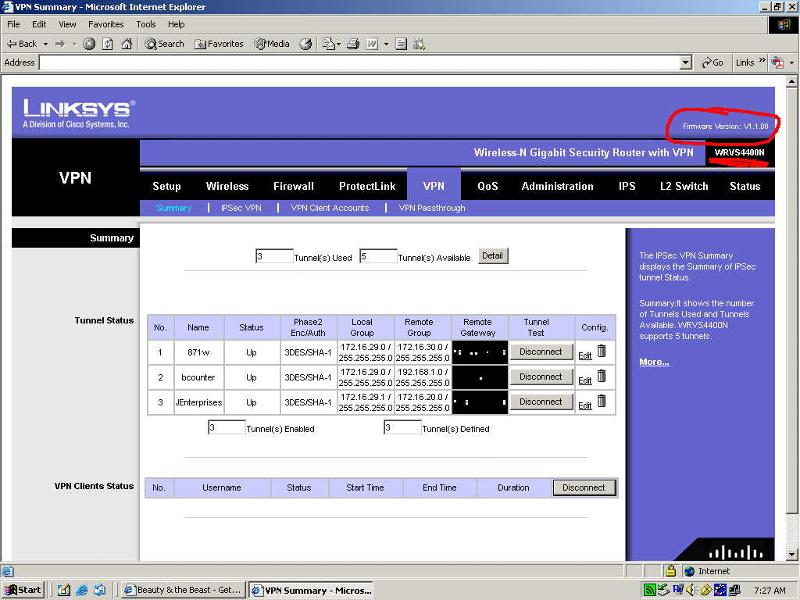
You have to configure it accordingly (Ip Addr., Encr/Auth type, etc) in the WRVS web interface section of VPN>Ip Sec. Configure your tunnel here and you should b able to see the tunnel under the "Summary" page of this same section. It supports up to 5 tunnels. I've attached a screen shot I found of a similar setup showing 3 tunnels and have attached it below. If you are already configured on your ASA(Since you stated you are and the WRVS has a Static Ip), then configuring the WRVS should be quite fast and simple. If you need anything else let us know.

ASKER
Ok, it's 0200 in the morning here and I have the tunnels established between the two units.
The only issue I'm having now, is that I'm not able to access the networks on the opposite ends of the tunnels from computers behind those routers, i.e. any of the computers behind the WRVS4400N can not access the servers behind the ASA.
In the morning, I'll post some screen captures of each configuration.
The tunnel connects almost instantly so I'm not sure what I've missed.
The only issue I'm having now, is that I'm not able to access the networks on the opposite ends of the tunnels from computers behind those routers, i.e. any of the computers behind the WRVS4400N can not access the servers behind the ASA.
In the morning, I'll post some screen captures of each configuration.
The tunnel connects almost instantly so I'm not sure what I've missed.
Split tunnel on the ASA side?? Maybe show us that portion of your config in the ASA and or your associated ACL's. Let us know, but Im glad to see that you at least have it up and running.
ASKER
Here is my current ASA configuration with the following definitions.
$.$.$.146 is the external IP of the ASA
$.$.$.150 is the external IP of the WRVS4400N
192.168.0.0 is the internal IP addresses behind the ASA
192.168.175.0 is the internal IP addresses behind the WRVS4400N
!
ASA Version 8.3(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address $.$.$.146 255.255.255.240
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network inside_lan
subnet 192.168.0.0 255.255.255.0
object network mailserver
host 192.168.0.15
object network webserver
host 192.168.0.15
object network webserver_ssl
host 192.168.0.15
object network webserver2
host 192.168.0.110
object network obj-vpnpool
subnet 192.168.2.0 255.255.255.0
object network NETWORK_OBJ_192.168.0.0
host 192.168.0.0
object network 192.168.175.0
subnet 192.168.175.0 255.255.255.0
access-list outside-in extended permit tcp any host 192.168.0.15 eq smtp
access-list outside-in extended permit tcp any host 192.168.0.15 eq www
access-list outside-in extended permit tcp any host 192.168.0.15 eq https
access-list outside-in extended permit tcp any host 192.168.0.110 eq www
access-list internal standard permit 192.168.0.0 255.255.255.0
access-list outside_1_cryptomap extended permit ip object inside_lan object 192.168.175.0
access-list Split_Tunnel_List remark The network behind the ASA
access-list Split_Tunnel_List standard permit 192.168.0.0 255.255.255.0
pager lines 24
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool vpnpool 192.168.2.1-192.168.2.254
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,outside) source static any any destination static obj-vpnpool obj-vpnpool
nat (inside,outside) source dynamic any interface
nat (inside,outside) source static NETWORK_OBJ_192.168.0.0 NETWORK_OBJ_192.168.0.0 destination static 192.168.175.0 192.168.175.0
nat (inside,outside) source static inside_lan inside_lan destination static 192.168.175.0 192.168.175.0
!
object network obj_any
nat (inside,outside) dynamic interface
object network inside_lan
nat (inside,outside) dynamic $.$.$.147
object network mailserver
nat (inside,outside) static $.$.$.$.147 service tcp smtp smtp
object network webserver
nat (inside,outside) static $.$.$.147 service tcp www www
object network webserver_ssl
nat (inside,outside) static $.$.$.147 service tcp https https
object network webserver2
nat (inside,outside) static $.$.$.148 service tcp www www
access-group outside-in in interface outside
route outside 0.0.0.0 0.0.0.0 $.$.$.145 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-reco
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
http server enable
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set RA-TS esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map DYN_MAP 10 set transform-set RA-TS
crypto map VPN_MAP 1 match address outside_1_cryptomap
crypto map VPN_MAP 1 set pfs group1
crypto map VPN_MAP 1 set peer $.$.$.150
crypto map VPN_MAP 1 set transform-set RA-TS
crypto map VPN_MAP 30 ipsec-isakmp dynamic DYN_MAP
crypto map VPN_MAP interface outside
crypto ca server
shutdown
smtp from-address admin@ciscoasa.null
crypto isakmp enable outside
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 3600
crypto isakmp policy 40
authentication pre-share
encryption 3des
hash sha
group 1
lifetime 86400
telnet timeout 5
ssh 192.168.0.0 255.255.255.0 inside
ssh timeout 30
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl encryption des-sha1
webvpn
group-policy company-vpn-policy internal
group-policy company-vpn-policy attributes
dns-server value 192.168.0.10
vpn-idle-timeout 30
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_Tunnel_List
username arhame password jbwAVYYVbQnpK8qZ encrypted
tunnel-group vpnclient type remote-access
tunnel-group vpnclient general-attributes
address-pool vpnpool
default-group-policy company-vpn-policy
tunnel-group vpnclient ipsec-attributes
pre-shared-key *****
tunnel-group $.$.$.150 type ipsec-l2l
tunnel-group $.$.$.150 ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:d6306b34a7a
ciscoasa(config)#
$.$.$.146 is the external IP of the ASA
$.$.$.150 is the external IP of the WRVS4400N
192.168.0.0 is the internal IP addresses behind the ASA
192.168.175.0 is the internal IP addresses behind the WRVS4400N
!
ASA Version 8.3(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address $.$.$.146 255.255.255.240
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network inside_lan
subnet 192.168.0.0 255.255.255.0
object network mailserver
host 192.168.0.15
object network webserver
host 192.168.0.15
object network webserver_ssl
host 192.168.0.15
object network webserver2
host 192.168.0.110
object network obj-vpnpool
subnet 192.168.2.0 255.255.255.0
object network NETWORK_OBJ_192.168.0.0
host 192.168.0.0
object network 192.168.175.0
subnet 192.168.175.0 255.255.255.0
access-list outside-in extended permit tcp any host 192.168.0.15 eq smtp
access-list outside-in extended permit tcp any host 192.168.0.15 eq www
access-list outside-in extended permit tcp any host 192.168.0.15 eq https
access-list outside-in extended permit tcp any host 192.168.0.110 eq www
access-list internal standard permit 192.168.0.0 255.255.255.0
access-list outside_1_cryptomap extended permit ip object inside_lan object 192.168.175.0
access-list Split_Tunnel_List remark The network behind the ASA
access-list Split_Tunnel_List standard permit 192.168.0.0 255.255.255.0
pager lines 24
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool vpnpool 192.168.2.1-192.168.2.254
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,outside) source static any any destination static obj-vpnpool obj-vpnpool
nat (inside,outside) source dynamic any interface
nat (inside,outside) source static NETWORK_OBJ_192.168.0.0 NETWORK_OBJ_192.168.0.0 destination static 192.168.175.0 192.168.175.0
nat (inside,outside) source static inside_lan inside_lan destination static 192.168.175.0 192.168.175.0
!
object network obj_any
nat (inside,outside) dynamic interface
object network inside_lan
nat (inside,outside) dynamic $.$.$.147
object network mailserver
nat (inside,outside) static $.$.$.$.147 service tcp smtp smtp
object network webserver
nat (inside,outside) static $.$.$.147 service tcp www www
object network webserver_ssl
nat (inside,outside) static $.$.$.147 service tcp https https
object network webserver2
nat (inside,outside) static $.$.$.148 service tcp www www
access-group outside-in in interface outside
route outside 0.0.0.0 0.0.0.0 $.$.$.145 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-reco
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
http server enable
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set RA-TS esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map DYN_MAP 10 set transform-set RA-TS
crypto map VPN_MAP 1 match address outside_1_cryptomap
crypto map VPN_MAP 1 set pfs group1
crypto map VPN_MAP 1 set peer $.$.$.150
crypto map VPN_MAP 1 set transform-set RA-TS
crypto map VPN_MAP 30 ipsec-isakmp dynamic DYN_MAP
crypto map VPN_MAP interface outside
crypto ca server
shutdown
smtp from-address admin@ciscoasa.null
crypto isakmp enable outside
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 3600
crypto isakmp policy 40
authentication pre-share
encryption 3des
hash sha
group 1
lifetime 86400
telnet timeout 5
ssh 192.168.0.0 255.255.255.0 inside
ssh timeout 30
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl encryption des-sha1
webvpn
group-policy company-vpn-policy internal
group-policy company-vpn-policy attributes
dns-server value 192.168.0.10
vpn-idle-timeout 30
split-tunnel-policy tunnelspecified
split-tunnel-network-list value Split_Tunnel_List
username arhame password jbwAVYYVbQnpK8qZ encrypted
tunnel-group vpnclient type remote-access
tunnel-group vpnclient general-attributes
address-pool vpnpool
default-group-policy company-vpn-policy
tunnel-group vpnclient ipsec-attributes
pre-shared-key *****
tunnel-group $.$.$.150 type ipsec-l2l
tunnel-group $.$.$.150 ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:d6306b34a7a
ciscoasa(config)#
I'm a little confused after looking at your config.
Questions:
1) Do you have remote users accessing local resources via a software VPN client or are you just establishing a site to site tunnel?
2) If client access, are remote users able to establish a vpn session?
3) Have you reviewed your logs?
Let us know.
Questions:
1) Do you have remote users accessing local resources via a software VPN client or are you just establishing a site to site tunnel?
2) If client access, are remote users able to establish a vpn session?
3) Have you reviewed your logs?
Let us know.
ASKER
Yes, we also have the ability for workers who are traveling to connect remotely via the Cisco VPN Client (version 5.0.07.0290).
They are able to connect successfully.
Which logs should I review?
They are able to connect successfully.
Which logs should I review?
ASKER
I did find one issue, and corrected it, but still no luck.
object network NETWORK_OBJ_192.168.0.0
host 192.168.0.0
should be
object network NETWORK_OBJ_192.168.0.0
subnet 192.168.0.0 255.255.255.0
I made the change, re-established the tunnel, and still no routing between the two.
object network NETWORK_OBJ_192.168.0.0
host 192.168.0.0
should be
object network NETWORK_OBJ_192.168.0.0
subnet 192.168.0.0 255.255.255.0
I made the change, re-established the tunnel, and still no routing between the two.
ASKER
Any ideas on what to adjust?
Does everything look correct?
Does everything look correct?
I will review this and advise you on creating site to site tunnel in few hours.
ASKER
many thanks. still working on it now.
I have tried to re-write the ipsec tunnel for you here. Go through this and see if this helps.
Do not mix your l2l tunnel config with web-vpn config.
Do not mix your l2l tunnel config with web-vpn config.
crypto isakmp policy 50
authentication pre-share
encryption 3des
hash sha
group 3
lifetime 86400
object network inside_lan
subnet 192.168.0.0 255.255.255.0
object network 192.168.175.0 (may be instead of using the subnet u can call it remote_network? if so change the same with the below access-list)
subnet 192.168.175.0 255.255.255.0
access-list outside_1_cryptomap extended permit ip object-group inside_lan object-group 192.168.175.0
crypto ipsec transform-set RA-TS1 esp-3des esp-sha-hmac
crypto map VPN_MAP 2 match address outside_1_cryptomap
crypto map VPN_MAP 2 set peer $.$.$.150
crypto map VPN_MAP 2 set transform-set RA-TS1 (Create a new transfrom-set)
crypto map VPN_MAP 2 set security-association lifetime seconds 86400
crypto map VPN_MAP 2 set nat-t-disable
crypto map VPN_MAP interface outside
crypto isakmp enable outside ( ISAKMP policy has not been applied?)
crypto isakmp policy 50 ( 50 or what ever number)
tunnel-group $.$.$.150 type ipsec-l2l
tunnel-group $.$.$.150 ipsec-attributes
pre-shared-key *****
nat (inside,outside) source static NETWORK_OBJ_192.168.0.0 NETWORK_OBJ_192.168.0.0 destination static 192.168.175.0 192.168.175.0 > Dont think this is required
nat (inside,outside) source static inside_lan inside_lan destination static 192.168.175.0 192.168.175.0 > Dont think this is requiredASKER
I've been looking over this and am confused as to what I should remove from my existing configuration to clean it up.
Also, there shouldn't be a web-vpn setup.
I had used the ASDM interface to configure the site to site tunnel via the IPsec VPN Wizard.
Also, there shouldn't be a web-vpn setup.
I had used the ASDM interface to configure the site to site tunnel via the IPsec VPN Wizard.
ASKER
Ok.
I think I'm heading in the right direction.
Today, I reset the device to the factory default configuration. From there, I setup the ASA as I had it before, with the exception of the Remote Access IPsec VPN configuration.
It worked perfectly.
The issue is, I still need the ability to create a vpn connection to the ASA unit via the Cisco VPN client, while having the site to site vpn established.
I am going to do more experimenting, but does anyone have any experience on running both on the same unit? Any tips or advice would be appreciated.
I think I'm heading in the right direction.
Today, I reset the device to the factory default configuration. From there, I setup the ASA as I had it before, with the exception of the Remote Access IPsec VPN configuration.
It worked perfectly.
The issue is, I still need the ability to create a vpn connection to the ASA unit via the Cisco VPN client, while having the site to site vpn established.
I am going to do more experimenting, but does anyone have any experience on running both on the same unit? Any tips or advice would be appreciated.
ASKER
Hrm.
Well, as soon as I went through to setup the Remote Access IPsec VPN configuration on the ASA, my site-to-site tunnel was trashed, and will no longer come up.
Earlier, after resetting the unit back to the factory default configuration, I simply used the IPsec VPN wizard in the ASDM to establish the site-to-site tunnel. Worked easy and perfect.
So, that must be the issue I'm having, making the two configurations play together.
Here are the commands I entered into the unit to setup the Remote Access IPsec VPN configuration:
ip local pool vpnpool 192.168.2.1-192.168.2.254
object network obj-vpnpool
subnet 192.168.2.0 255.255.255.0
nat (inside,outside) 1 source static any any destination static obj-vpnpool obj-vpnpool
group-policy company-vpn-policy internal
group-policy company-vpn-policy attributes
vpn-idle-timeout 30
dns-server value 192.168.0.10
isakmp policy 20
encryption 3des
hash sha
authentication pre-share
group 2
lifetime 3600
isakmp enable outside
crypto ipsec transform-set RA-TS esp-3des esp-sha-hmac
crypto dynamic-map DYN_MAP 10 set transform-set RA-TS
crypto map VPN_MAP 30 ipsec-isakmp dynamic DYN_MAP
crypto map VPN_MAP interface outside
tunnel-group *vpnclient* type remote-access
tunnel-group *vpnclient* general-attributes
address-pool vpnpool
default-group-policy company-vpn-policy
tunnel-group *vpnclient* ipsec-attributes
pre-shared-key *passphrase*
Well, as soon as I went through to setup the Remote Access IPsec VPN configuration on the ASA, my site-to-site tunnel was trashed, and will no longer come up.
Earlier, after resetting the unit back to the factory default configuration, I simply used the IPsec VPN wizard in the ASDM to establish the site-to-site tunnel. Worked easy and perfect.
So, that must be the issue I'm having, making the two configurations play together.
Here are the commands I entered into the unit to setup the Remote Access IPsec VPN configuration:
ip local pool vpnpool 192.168.2.1-192.168.2.254
object network obj-vpnpool
subnet 192.168.2.0 255.255.255.0
nat (inside,outside) 1 source static any any destination static obj-vpnpool obj-vpnpool
group-policy company-vpn-policy internal
group-policy company-vpn-policy attributes
vpn-idle-timeout 30
dns-server value 192.168.0.10
isakmp policy 20
encryption 3des
hash sha
authentication pre-share
group 2
lifetime 3600
isakmp enable outside
crypto ipsec transform-set RA-TS esp-3des esp-sha-hmac
crypto dynamic-map DYN_MAP 10 set transform-set RA-TS
crypto map VPN_MAP 30 ipsec-isakmp dynamic DYN_MAP
crypto map VPN_MAP interface outside
tunnel-group *vpnclient* type remote-access
tunnel-group *vpnclient* general-attributes
address-pool vpnpool
default-group-policy company-vpn-policy
tunnel-group *vpnclient* ipsec-attributes
pre-shared-key *passphrase*
ASKER
I decided to go ahead and post the entire config. Using this one, only the remote access ipsec vpn works. the site-to-site has stopped working.
Here is the current complete config:
: Saved
:
ASA Version 8.3(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address *.*.*.146 255.255.255.240
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network mailserver
host 192.168.0.15
object network webserver
host 192.168.0.15
object network webserver_ssl
host 192.168.0.15
object network webserver2
host 192.168.0.110
object network NETWORK_OBJ_192.168.0.0_24
subnet 192.168.0.0 255.255.255.0
object network remote_network
subnet 192.168.175.0 255.255.255.0
object network obj-vpnpool
subnet 192.168.2.0 255.255.255.0
access-list outside-in extended permit tcp any host 192.168.0.15 eq smtp
access-list outside-in extended permit tcp any host 192.168.0.15 eq www
access-list outside-in extended permit tcp any host 192.168.0.15 eq https
access-list outside-in extended permit tcp any host 192.168.0.110 eq www
access-list outside_1_cryptomap extended permit ip 192.168.0.0 255.255.255.0 object remote_network
pager lines 24
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool vpnpool 192.168.2.1-192.168.2.254
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,outside) source static any any destination static obj-vpnpool obj-vpnpool
nat (inside,outside) source static NETWORK_OBJ_192.168.0.0_24
!
object network obj_any
nat (inside,outside) dynamic interface
object network mailserver
nat (inside,outside) static *.*.*.147 service tcp smtp smtp
object network webserver
nat (inside,outside) static *.*.*.147 service tcp www www
object network webserver_ssl
nat (inside,outside) static *.*.*.147 service tcp https https
object network dbsoftinc
nat (inside,outside) static *.*.*.148 service tcp www www
access-group outside-in in interface outside
route outside 0.0.0.0 0.0.0.0 *.*.*.145 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-reco
aaa authentication ssh console LOCAL
http server enable
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set RA-TS esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map DYN_MAP 10 set transform-set RA-TS
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs group1
crypto map outside_map 1 set peer *.*.*.150
crypto map outside_map 1 set transform-set ESP-3DES-SHA
crypto map VPN_MAP 30 ipsec-isakmp dynamic DYN_MAP
crypto map VPN_MAP interface outside
crypto ca server
shutdown
smtp from-address admin@ciscoasa.null
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 1
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 3600
telnet timeout 5
ssh 192.168.0.0 255.255.255.0 inside
ssh timeout 30
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
no threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy company-vpn-policy internal
group-policy company-vpn-policy attributes
dns-server value 192.168.0.10
vpn-idle-timeout 30
username ******** password XLRO2tJ8dfXviPOG encrypted
tunnel-group *.*.*.150 type ipsec-l2l
tunnel-group *.*.*.150 ipsec-attributes
pre-shared-key *****
tunnel-group *vpnclient* type remote-access
tunnel-group *vpnclient* general-attributes
address-pool vpnpool
default-group-policy company-vpn-policy
tunnel-group *vpnclient* ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:e1b5251ca2f
: end
no asdm history enable
Here is the current complete config:
: Saved
:
ASA Version 8.3(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address *.*.*.146 255.255.255.240
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network mailserver
host 192.168.0.15
object network webserver
host 192.168.0.15
object network webserver_ssl
host 192.168.0.15
object network webserver2
host 192.168.0.110
object network NETWORK_OBJ_192.168.0.0_24
subnet 192.168.0.0 255.255.255.0
object network remote_network
subnet 192.168.175.0 255.255.255.0
object network obj-vpnpool
subnet 192.168.2.0 255.255.255.0
access-list outside-in extended permit tcp any host 192.168.0.15 eq smtp
access-list outside-in extended permit tcp any host 192.168.0.15 eq www
access-list outside-in extended permit tcp any host 192.168.0.15 eq https
access-list outside-in extended permit tcp any host 192.168.0.110 eq www
access-list outside_1_cryptomap extended permit ip 192.168.0.0 255.255.255.0 object remote_network
pager lines 24
logging asdm informational
mtu inside 1500
mtu outside 1500
ip local pool vpnpool 192.168.2.1-192.168.2.254
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (inside,outside) source static any any destination static obj-vpnpool obj-vpnpool
nat (inside,outside) source static NETWORK_OBJ_192.168.0.0_24
!
object network obj_any
nat (inside,outside) dynamic interface
object network mailserver
nat (inside,outside) static *.*.*.147 service tcp smtp smtp
object network webserver
nat (inside,outside) static *.*.*.147 service tcp www www
object network webserver_ssl
nat (inside,outside) static *.*.*.147 service tcp https https
object network dbsoftinc
nat (inside,outside) static *.*.*.148 service tcp www www
access-group outside-in in interface outside
route outside 0.0.0.0 0.0.0.0 *.*.*.145 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-reco
aaa authentication ssh console LOCAL
http server enable
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec transform-set RA-TS esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map DYN_MAP 10 set transform-set RA-TS
crypto map outside_map 1 match address outside_1_cryptomap
crypto map outside_map 1 set pfs group1
crypto map outside_map 1 set peer *.*.*.150
crypto map outside_map 1 set transform-set ESP-3DES-SHA
crypto map VPN_MAP 30 ipsec-isakmp dynamic DYN_MAP
crypto map VPN_MAP interface outside
crypto ca server
shutdown
smtp from-address admin@ciscoasa.null
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 1
lifetime 86400
crypto isakmp policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 3600
telnet timeout 5
ssh 192.168.0.0 255.255.255.0 inside
ssh timeout 30
console timeout 0
dhcpd auto_config outside
!
threat-detection basic-threat
no threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
group-policy company-vpn-policy internal
group-policy company-vpn-policy attributes
dns-server value 192.168.0.10
vpn-idle-timeout 30
username ******** password XLRO2tJ8dfXviPOG encrypted
tunnel-group *.*.*.150 type ipsec-l2l
tunnel-group *.*.*.150 ipsec-attributes
pre-shared-key *****
tunnel-group *vpnclient* type remote-access
tunnel-group *vpnclient* general-attributes
address-pool vpnpool
default-group-policy company-vpn-policy
tunnel-group *vpnclient* ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:e1b5251ca2f
: end
no asdm history enable
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I've successfully created the WebVPN configuration via ASDM as you reccomended.
When I enter the config at the console for the site-to-site as you suggested,
access-list outside_1_cryptomap extended permit ip object-group inside_lan object-group outside_network
I immediately get the following error:
ERROR: specified object group <inside_lan> not found
I have verified that there wasn't any typos in the creation of the network object inside_lan and I can see the network object inside_lan within ASDM and it is properly defined
Any ideas?
Thanks for all of the help.
When I enter the config at the console for the site-to-site as you suggested,
access-list outside_1_cryptomap extended permit ip object-group inside_lan object-group outside_network
I immediately get the following error:
ERROR: specified object group <inside_lan> not found
I have verified that there wasn't any typos in the creation of the network object inside_lan and I can see the network object inside_lan within ASDM and it is properly defined
Any ideas?
Thanks for all of the help.
Sorry it should be
access-list outside_1_cryptomap extended permit object-group inside_lan object-group outside_network
access-list outside_1_cryptomap extended permit object-group inside_lan object-group outside_network
ASKER
I get a different error when trying to enter that config line.
ERROR: % Invalid input detected at '^' marker.
and just to verify that it wasn't a typo, I entered the command as:
access-list outside_1_cryptomap extended permit object-group inside_lan object-group outside_network
ERROR: % Invalid input detected at '^' marker.
and just to verify that it wasn't a typo, I entered the command as:
access-list outside_1_cryptomap extended permit object-group inside_lan object-group outside_network
ASKER
ok, the line command format was:
access-list outside_1_cryptomap extended permit ip object inside_lan object outside_network
still didn't work though. Running more tests-experiments.
access-list outside_1_cryptomap extended permit ip object inside_lan object outside_network
still didn't work though. Running more tests-experiments.
ASKER
Status Update.
Ok, here is what I have tested and learned so far.
After the clean reset to default, I can easilty configure the site-to-site tunnel if I use the ASDM Wizard.
After a clean reset to default, and then using the code you gave me above (chesperito), the site-to-site tunnel will not function. I did have to make one change to the code you gave me in addition to the access-list command.
Under the crypto isakmp policy 50, I changed the group to 1, for compatibility purposes with the WRVS. I also had to do this using the ASDM Wizard and it worked. For some reason, group 3 doesn't work on my ASA unit. Not sure why.
I'll create another post that has the content of both configurations. I'm going through them now to see if I see anything obvious on why one works and the other doesn't.
Then, back to why it will not work while the Remote Access IPsec VPN tunnel is enabled.
Ok, here is what I have tested and learned so far.
After the clean reset to default, I can easilty configure the site-to-site tunnel if I use the ASDM Wizard.
After a clean reset to default, and then using the code you gave me above (chesperito), the site-to-site tunnel will not function. I did have to make one change to the code you gave me in addition to the access-list command.
Under the crypto isakmp policy 50, I changed the group to 1, for compatibility purposes with the WRVS. I also had to do this using the ASDM Wizard and it worked. For some reason, group 3 doesn't work on my ASA unit. Not sure why.
I'll create another post that has the content of both configurations. I'm going through them now to see if I see anything obvious on why one works and the other doesn't.
Then, back to why it will not work while the Remote Access IPsec VPN tunnel is enabled.
ASKER
ok, one thing I found that was preventing the site-to-site tunnel from connecting with the code you suggested, was the need to add in the following command:
crypto map VPN_MAP 2 set pfs group1
Once I added this in, the tunnel connected, but I'm still not able to route traffic through either way.
crypto map VPN_MAP 2 set pfs group1
Once I added this in, the tunnel connected, but I'm still not able to route traffic through either way.
ASKER
Ok, I found another issue with the code. There was no nat statment.
I've added the following and now I am routing between the networks
nat (inside,outside) source static inside_lan inside_lan destination static outside_network outside_network
Now, I need to setup the remote-access vpn and see if that will work.
Will let you know.
I've added the following and now I am routing between the networks
nat (inside,outside) source static inside_lan inside_lan destination static outside_network outside_network
Now, I need to setup the remote-access vpn and see if that will work.
Will let you know.
ASKER
Sorry for the delayed response.
Once made a few adjustments to the suggested code, and then used the IPsec Remote Access VPN wizard, almost everything is working perfectly.
The only thing left to troubleshoot is split tunneling.
As soon as I get all the kinks worked out, I'll post the updated code for anyone else who might be wanting to try this same scenario.
Overall, so far, I'm very happy with the stability and ability to use the less expensive WRVS with the ASA.
Thanks
Once made a few adjustments to the suggested code, and then used the IPsec Remote Access VPN wizard, almost everything is working perfectly.
The only thing left to troubleshoot is split tunneling.
As soon as I get all the kinks worked out, I'll post the updated code for anyone else who might be wanting to try this same scenario.
Overall, so far, I'm very happy with the stability and ability to use the less expensive WRVS with the ASA.
Thanks
ASKER
Thanks for the help in working through this configuration. I did a considerable amount of searching on the internet for someone else attempting this same setup, and couldn't find anything. Hopefully someone else can now benefit from the work.