SupermanTB
asked on
Multiple SSIDs with VLANs
I have been tasked with coming up with a cost effective solution to create approximately 50 SSIDs, each on their own VLAN. Each SSID/VLAN represents a separate tenant in building comprised mainly of of a bunch of single offices. Each of the tenants in the building is a separate business, hence the need for the VLANs.
I've poked around on the internet for a few hours and didn't see anything terribly obvious. I also was quoted a very expensive option from a Cicso reseller.
Does anyone have a suggestion or could possibly point me in the right direction?
I've poked around on the internet for a few hours and didn't see anything terribly obvious. I also was quoted a very expensive option from a Cicso reseller.
Does anyone have a suggestion or could possibly point me in the right direction?
ASKER
I would say approximatley 12 access points. Normally 1 user per VLAN, but possibly 2 in some cases. I am only concerned with providing access to the internet for standard stuff like email, web browsing, etc. I have some flexibility on how the users authenticate, but my initial thoughts were PSK.
These users are doing very simple stuff. In most cases, it will be just a single user and their laptop. They'll be primarily browsing the internet, checking email and nothing more than that.
I will be providing ample bandwidth to accomodate the needs of these users.
Thanks again for your help.
These users are doing very simple stuff. In most cases, it will be just a single user and their laptop. They'll be primarily browsing the internet, checking email and nothing more than that.
I will be providing ample bandwidth to accomodate the needs of these users.
Thanks again for your help.
It seems DD-WRT may support separate WLANs with individual SSID but I am wondering if you have powerful enough hardware to support 50 SSIDs.
http://www.dd-wrt.com/wiki/index.php/Multiple_WLANs
However, using several DD-WRT capable wireless routers may allow you to built totally 50 wireless VLANs.
http://www.dd-wrt.com/wiki/index.php/Multiple_WLANs
However, using several DD-WRT capable wireless routers may allow you to built totally 50 wireless VLANs.
Not sure if doing it that way is very efficient as for throughput ... have never had the need of adding so many SSIDs before though ...
Not sure if this would be a technically (or from other requirements) usable solution, but if not, maybe you can go into details a bit more if not:
How about putting in decent APs that allows for user isolation, with controller in the back. That way, you won't really need separate VLANs, as even on the same SSIDs, users will not be able to reach each other directly. As long as all you need is routing towards the Internet, why go through all the trouble with the VLANs? Alternatively, you could even put in a Hotspot solution (like e.g. CoovaChilli) as a backend, allowing the tenants to connect, with documentation in case you need documentation which tenant did anything illegal ...
Not sure if this would be a technically (or from other requirements) usable solution, but if not, maybe you can go into details a bit more if not:
How about putting in decent APs that allows for user isolation, with controller in the back. That way, you won't really need separate VLANs, as even on the same SSIDs, users will not be able to reach each other directly. As long as all you need is routing towards the Internet, why go through all the trouble with the VLANs? Alternatively, you could even put in a Hotspot solution (like e.g. CoovaChilli) as a backend, allowing the tenants to connect, with documentation in case you need documentation which tenant did anything illegal ...
ASKER
The VLAN was just my intuitive solution. I definitely don't have to do that. I only need to separate the users and give them access to the internet. Do you have any particular equipment in mind that would handle the solution you mention regarding the APs/user isolation with a controller in the back?
One possible solution would be based on Cisco Aironet APs and a controller ... with 12 APs, you could go with the smallest WLAN-Controller, I'd have to look up how many APs their license supports out of the box ...
Also, depending on the switch used you could also use a controller-less solution if your Switch supports isolation ... that way, you could get bye with just handing out IPs from some central DHCP server (could be a firewall, too) and route everything towards the internet ...
Do your users need/want fixed routeable IPs? If so, what do you plan to do as far as security goes? Will they take care of themselves, or would they want some Firewall/IDS in front?
Also, depending on the switch used you could also use a controller-less solution if your Switch supports isolation ... that way, you could get bye with just handing out IPs from some central DHCP server (could be a firewall, too) and route everything towards the internet ...
Do your users need/want fixed routeable IPs? If so, what do you plan to do as far as security goes? Will they take care of themselves, or would they want some Firewall/IDS in front?
ASKER
OK, so for the AP/Controller solution, I can't say that I'm extremely familiar with the concept of a WLAN-Controller. It appears it is a box that controls all the settings, etc for the APs? I wouldn't think that WLAN-Controller would handle the DHCP, firewall, internet settings, etc, so I would need a separate device for that? I typically use SonicWall appliances, so would I plug the internet into that and the SonicWall would feed into the WLAN-Controller which would then manage all the APs? Just trying to make sure I understand the infrastructure behind this option.
Regarding the network switch with isolation, this solution sounds simpler, which I like, but I'm not sure I understand the isolation part. I get that I could use a switch to separate each AP into a separate VLAN, but I don't see how I could do more than that. If you could enlighten me, I would appreciate it.
My users do not need fixed routeable IPs.
Regarding the network switch with isolation, this solution sounds simpler, which I like, but I'm not sure I understand the isolation part. I get that I could use a switch to separate each AP into a separate VLAN, but I don't see how I could do more than that. If you could enlighten me, I would appreciate it.
My users do not need fixed routeable IPs.
Controller-based solutions (at least for Cisco) means that you have a central point which controls all the WLAN APs, takes care of all associations/authenticatio
The isolation is like the "UNI"-ports on metro switches from Cisco - anything coming in on one of those ports will only be allowed to be transported to non-isolated ports, but never to any other isolated port (not sure I'm using the exact terminology though ;) ). The access points (at least Cisco) can be configured to do the same thing, with multiple physical or vlan ports that can be configured to this "isolated" state ... then, the uplink would not be isolated, but would on the switch side ...
The isolation is like the "UNI"-ports on metro switches from Cisco - anything coming in on one of those ports will only be allowed to be transported to non-isolated ports, but never to any other isolated port (not sure I'm using the exact terminology though ;) ). The access points (at least Cisco) can be configured to do the same thing, with multiple physical or vlan ports that can be configured to this "isolated" state ... then, the uplink would not be isolated, but would on the switch side ...
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for all the comments everyone.
Jakob, your solution sounds the smoothest. I'm guessing you meant Aruba MBC 650 instead of Aruan?
The users definitely need to be separated as they are completely different businesses. This separation was at the top of the list in terms of requirements of this solution. Can the Aruba equipment you describe handle the 50 VLAN? Also, you mention that I can separate according to username/pwd as opposed to SSID. I like that solution much better. Can you tell me how that would work?
Jakob, your solution sounds the smoothest. I'm guessing you meant Aruba MBC 650 instead of Aruan?
The users definitely need to be separated as they are completely different businesses. This separation was at the top of the list in terms of requirements of this solution. Can the Aruba equipment you describe handle the 50 VLAN? Also, you mention that I can separate according to username/pwd as opposed to SSID. I like that solution much better. Can you tell me how that would work?
You can do this using Cisco IOS APs (so no controller) and RADIUS using one SSID if you really want to. This makes configuration exactly the same on the APs, and you can use something like Microsoft's Active Directory and NPS/IAS to control network access and assign the VLAN ID per customer.
Or run something like CoovaChilli Hotspot-Software, which would allow you (or the tenants) to dynamically add guest accounts that are e.g. valid for the day or an hour or something ...
sorry --- I've been away for some days.
The Aruba equipment could support this yes. As CraigBeck says you can use AD with NPS/IAS to handle VLANs dependent on group membership, or use Aruba Controller and create different user accounts for different users. With Aruba you can create a Captive Portal (Web Page) for login and create different users and which VLAN they should belong to (See attached image ...
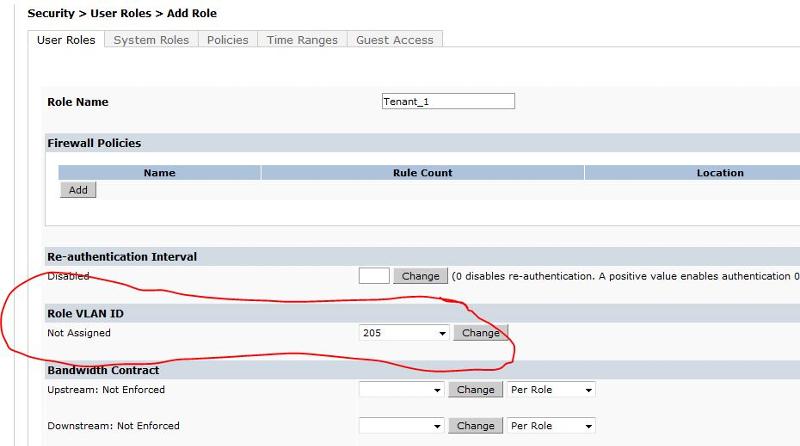
The Aruba equipment could support this yes. As CraigBeck says you can use AD with NPS/IAS to handle VLANs dependent on group membership, or use Aruba Controller and create different user accounts for different users. With Aruba you can create a Captive Portal (Web Page) for login and create different users and which VLAN they should belong to (See attached image ...
ASKER
Hey everyone. Sorry for the delay. I've never used NPS to control network access and assign VLANs like you're suggesting. Is that simple to setup? It also brings an additional expense, as I would have to integrate a server into the network.
I'm leaning towards the controller model. I see Jakob speaking about a Captive Portal (Web Page) for user login. Would the users have to login say each morning? While this type of thing might work great for guest access, it will likely get annoying for the tenants.
Garry-G....with the architecture look like with the CoovaChilli solution. Will I still need a wireless controller? Do I need a separate device to run the CoovaChilli software?
Thanks everyone!
I'm leaning towards the controller model. I see Jakob speaking about a Captive Portal (Web Page) for user login. Would the users have to login say each morning? While this type of thing might work great for guest access, it will likely get annoying for the tenants.
Garry-G....with the architecture look like with the CoovaChilli solution. Will I still need a wireless controller? Do I need a separate device to run the CoovaChilli software?
Thanks everyone!
If you go with Cisco, you can avoid lot of configuration:
12 APs , managed centrally by two controllers (for redundancy) + ISE controller
You will have only one SSID. When client associate will get get permission and vlan according to domain permissions
Also, you will have guest functionality.
Cisco ISE appliance (runs also in VM) here:
http://www.cisco.com/en/US/products/ps11640/index.html
If you dont want ISE, you can get the 12 AP plus the controller. You will avoid configuring AP one by one, and when you make changes you will apply automatically to all (avoiding mistakes and forgotten AP).
12 APs , managed centrally by two controllers (for redundancy) + ISE controller
You will have only one SSID. When client associate will get get permission and vlan according to domain permissions
Also, you will have guest functionality.
Cisco ISE appliance (runs also in VM) here:
http://www.cisco.com/en/US/products/ps11640/index.html
If you dont want ISE, you can get the 12 AP plus the controller. You will avoid configuring AP one by one, and when you make changes you will apply automatically to all (avoiding mistakes and forgotten AP).
Aruba is equally easy to configure --
If you use Captive Portal they would need to log in every day.
But you can also create users in the integrated user database, assign different roles and VLANs to each user, and set Wireless Settings on clients to connect using EAP-MsChap V2 and user authentication
(EAP-MsChap V2 uses usernames and passwords)
Then you'd avoid the entire NPS as well - and it is integrated into the Aruba Controller - requiring only the PEFNG firewall license
If you use Captive Portal they would need to log in every day.
But you can also create users in the integrated user database, assign different roles and VLANs to each user, and set Wireless Settings on clients to connect using EAP-MsChap V2 and user authentication
(EAP-MsChap V2 uses usernames and passwords)
Then you'd avoid the entire NPS as well - and it is integrated into the Aruba Controller - requiring only the PEFNG firewall license
ASKER
I would like to keep things as simple as possible for both me and the users. Jackob, your solutions appears the most simple. With the EAP-MsChap suggestion you mention w/ having the user info stored in a database, would that prevent the requirement to sign on everyday?
I dont think that is a very secure solution.... Prefer WPA2-Enterprise with a certificate.
If you want guest access, you can use mikrotik hostspot functionality
www.mikrotik.com
If you want guest access, you can use mikrotik hostspot functionality
www.mikrotik.com
ASKER
So the users will have to have a certificate installed on their computer in order to access the network?
When new users want to access wireless network, will visit IT to get a ceritificate.
This way you manage which devices will connect to network (for example you may allow only laptops and not any device that support eap-mschap authenticaiton!)
You can also auto distribute it through your Active Directory.
You can have a different ssid/vlan with limited access for users with mobile device. Maybe you dont want users to carry data sensitive (and expensive) data with their portable device.
This way you manage which devices will connect to network (for example you may allow only laptops and not any device that support eap-mschap authenticaiton!)
You can also auto distribute it through your Active Directory.
You can have a different ssid/vlan with limited access for users with mobile device. Maybe you dont want users to carry data sensitive (and expensive) data with their portable device.
Of course EAP-MsChap V2 is secure --- 10times more secure than PSKs are.
But of course not as secure as deploying machine AND user authentication based on certificates. But providing you wanted to keep this simple, then EAP-MsChap using usernames and password is the easiest way to deploy this.
With EAP-MsChap V2 (still deploying WPA2-Enterprise) all users have different, unique, randomly generated and time limited encryption keys - So there is no way any equipment these days that can crack the encryption.
Yes - users will log in to the wireless automatically, once client authentication is set up.
If you - however - need to deploy certiicate based authentication, you need to deploy the following server roles, preferably on at least 2 servers:
- AD CS
- Network Policy Server (co-located with AD CS role)
- Certificate server
Then you need to deploy a RAS/IAS certificate to NPS server and create, and enroll for user certificates (or machine certificates if you want to give access to only users that have machine AND user certificates) for all users you want to give access to. And then export and install all client (user or machine certificates) to all computers you want to give access to - and also install your AD root certificate to users computers - so they can trust your NPS .. sounds like work you do npt want for computers not joined to your AD....
All of this is easy peasy lemon squeezy if all users and computers are domain joined. A lot of hassle if they're not ... It's not just enrolling certs - it's maintaining them as well ...
But of course not as secure as deploying machine AND user authentication based on certificates. But providing you wanted to keep this simple, then EAP-MsChap using usernames and password is the easiest way to deploy this.
With EAP-MsChap V2 (still deploying WPA2-Enterprise) all users have different, unique, randomly generated and time limited encryption keys - So there is no way any equipment these days that can crack the encryption.
Yes - users will log in to the wireless automatically, once client authentication is set up.
If you - however - need to deploy certiicate based authentication, you need to deploy the following server roles, preferably on at least 2 servers:
- AD CS
- Network Policy Server (co-located with AD CS role)
- Certificate server
Then you need to deploy a RAS/IAS certificate to NPS server and create, and enroll for user certificates (or machine certificates if you want to give access to only users that have machine AND user certificates) for all users you want to give access to. And then export and install all client (user or machine certificates) to all computers you want to give access to - and also install your AD root certificate to users computers - so they can trust your NPS .. sounds like work you do npt want for computers not joined to your AD....
All of this is easy peasy lemon squeezy if all users and computers are domain joined. A lot of hassle if they're not ... It's not just enrolling certs - it's maintaining them as well ...
ASKER
It looks like I've got two options here
1. Ampranti: using digital certificates. This presents the problems Jakob mentioned in his last post. These computers will definitely not be joined to the same domain, which presents problems.
2. Jakob: simple, but this solution will require the users to login each morning to the internet connection.
I'm OK with the security level of the PSK vs. the digital certificate. I understand the difference between the two and for this situation, the PSK will be just fine.
Jakob, is there a way to utilize your solution without having to have the users login each day?
1. Ampranti: using digital certificates. This presents the problems Jakob mentioned in his last post. These computers will definitely not be joined to the same domain, which presents problems.
2. Jakob: simple, but this solution will require the users to login each morning to the internet connection.
I'm OK with the security level of the PSK vs. the digital certificate. I understand the difference between the two and for this situation, the PSK will be just fine.
Jakob, is there a way to utilize your solution without having to have the users login each day?
PCs may join the same domain if you want... Depends on what you want to do & how you want to separate access
ASKER
I definitely do not want these PCs joining the domain. They are completely separate businesses and tenants.
EAP-MsChap V2 is not based on PSK - it's based on usernames and passwords from some kind of database, in my suggestion - the database in Aruba Controller.
With EAP-MsChap V2 users do not need to login in everyday - but you need to configure wireless setings on clients to use Eap-MsChap as authentication - but remove the check mark on "Use Windows Login Credentials" - that way users will enter username and password the first time they connect to the network. The next times it will remenber uid/pwd
Some tips on configuring clients here: http://www.jmu.edu/computing/desktop/wireless/wm_library/OfficialWireless-Windows7.pdf
With EAP-MsChap V2 users do not need to login in everyday - but you need to configure wireless setings on clients to use Eap-MsChap as authentication - but remove the check mark on "Use Windows Login Credentials" - that way users will enter username and password the first time they connect to the network. The next times it will remenber uid/pwd
Some tips on configuring clients here: http://www.jmu.edu/computing/desktop/wireless/wm_library/OfficialWireless-Windows7.pdf
ASKER
Very nice. I will be calling the folks at Aruba today to investigate pricing.
There should be a timeout associated with EAP-MSChapV2, so the login will be required each time the client tries to authenticate to the AP. This means the client will need to enter their username/password every time the laptop is turned on. If you use MS Active Directory usernames you can and generally should use the Windows Login Credentials so that the login box doesn't pop-up unnecessarily.
ASKER
MS Active Directory is just not an option b/c the computers will not be joining a domain.
Jakob, is this true regarding the timeout/login for EAP-MSChapV2?
Jakob, is this true regarding the timeout/login for EAP-MSChapV2?
I'm using MsChap for some customers without needing to login more than once - the first time
ASKER
Interesting. I should be getting a call back from the engineers at Aruba next week. I'll be sure to bring this up with them.
I was going to say....
...but at this point...
...I think I'll leave you in Jakob's capable hands!
The computers don't have to be on a domain to use AD... at the end of the day it is just a directory of users.
It all depends on how you ultimately decide you want the business users to authenticate. There are lots of ways, but you need to decide how each business will connect to the WLAN.
In all honesty the way I would do it would be totally dependant on cost. If you plan to give each business their own wireless bridge the solution could be pretty simple. The problem comes when you want to secure each connection by username/password on an ad-hoc basis (per client device).
If you use a Cisco solution you can do this a couple of ways:
One way is to use Mesh APs and assign a VLAN ID per bridge. This is slightly complicated to implement but would work for as many clients devices per business as you want.
The other way would be to use standard access points and configure each business AP as a workgroup-bridge. This limits your client devices per business to 255, but I doubt that'd be a problem.
Alternatively, if cost is an issue and you can't afford to provide a bridge per business you could use PEAP.
A 3rd Party certificate can be installed on a RADIUS server and linked to MS AD. On the AD you create a username/password for each business and configure the AP to authenticate against the RADIUS. The RADIUS will tell the AP which VLAN to put the client on based on its login.
Most of the WLAN kit aimed at the Enterprise will be able to do this stuff, so vendor isn't really important. I know 1000% Cisco kit will do this as I've done it before for a major sporting event in the UK, amongst other projects.
It all depends on how you ultimately decide you want the business users to authenticate. There are lots of ways, but you need to decide how each business will connect to the WLAN.
In all honesty the way I would do it would be totally dependant on cost. If you plan to give each business their own wireless bridge the solution could be pretty simple. The problem comes when you want to secure each connection by username/password on an ad-hoc basis (per client device).
If you use a Cisco solution you can do this a couple of ways:
One way is to use Mesh APs and assign a VLAN ID per bridge. This is slightly complicated to implement but would work for as many clients devices per business as you want.
The other way would be to use standard access points and configure each business AP as a workgroup-bridge. This limits your client devices per business to 255, but I doubt that'd be a problem.
Alternatively, if cost is an issue and you can't afford to provide a bridge per business you could use PEAP.
A 3rd Party certificate can be installed on a RADIUS server and linked to MS AD. On the AD you create a username/password for each business and configure the AP to authenticate against the RADIUS. The RADIUS will tell the AP which VLAN to put the client on based on its login.
Most of the WLAN kit aimed at the Enterprise will be able to do this stuff, so vendor isn't really important. I know 1000% Cisco kit will do this as I've done it before for a major sporting event in the UK, amongst other projects.
...but at this point...
Jakob, is this true regarding the timeout/login for EAP-MSChapV2?
...I think I'll leave you in Jakob's capable hands!
ASKER
I must have mistakenly closed this question with no points being awarded. Not sure how I did that. I don't see how I can prevent it from being closed. I apologize. The help was great.
looks like it all worked out :-)
But more importantly is to know this:
- How many APs ?
- How many wireless users? (in total, and perhaps per SSID or AP). remember to include PCs, tablets and smart phones in the user count
- What services will run on the wireless?
- How should users authenticate? PSK? 802.1X?
Most APs/Controllers have support for at least 64 SSID, and VLANs ...
but the most important factor in wireless is having enough bandwidth and performance for all services for all users ...