jmichaelpalermo4
asked on
DNS Fails When Connected to SSTP VPN
Experts,
I am running into an issue that has cost some significant time - your help is appreciated. We're currently running an SSTP VPN connection hosted on a 2008 R2 RRAS server. A few weeks ago, at random, DNS lookups stopped working for those connected to the VPN (giving the user the impression that connecting to the VPN completely disables their network connection).
Here's the facts:
1. Users can connect to the VPN fine; once they do, they're able to ping any device on the protected network.
2. ANY DNS lookup fails when they are connected to the VPN.
3. Using NSLookup to test DNS while connected to the VPN shows their existing (public) DNS server works. Manually changing the DNS setting to a local DNS server on the protected network also works.
4. Broadcast name resolution is enabled on the RRAS server:
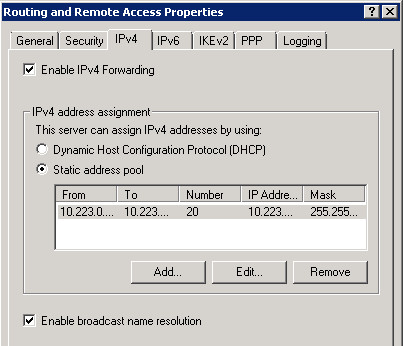
5. Wireshark captures from the client while connected show the client attempting to broadcast for name resolution. Note: the subnet I am assigning for the SSTP VPN is 10.223.0.50-69. This client has the IP address 10.223.0.53 on the SSTP VPN, 10.223.99.100 on the LAN:

I'm not too sure where to go from here. Thanks so much for your help!
I am running into an issue that has cost some significant time - your help is appreciated. We're currently running an SSTP VPN connection hosted on a 2008 R2 RRAS server. A few weeks ago, at random, DNS lookups stopped working for those connected to the VPN (giving the user the impression that connecting to the VPN completely disables their network connection).
Here's the facts:
1. Users can connect to the VPN fine; once they do, they're able to ping any device on the protected network.
2. ANY DNS lookup fails when they are connected to the VPN.
3. Using NSLookup to test DNS while connected to the VPN shows their existing (public) DNS server works. Manually changing the DNS setting to a local DNS server on the protected network also works.
4. Broadcast name resolution is enabled on the RRAS server:

5. Wireshark captures from the client while connected show the client attempting to broadcast for name resolution. Note: the subnet I am assigning for the SSTP VPN is 10.223.0.50-69. This client has the IP address 10.223.0.53 on the SSTP VPN, 10.223.99.100 on the LAN:

I'm not too sure where to go from here. Thanks so much for your help!
"Broadcast name resolution" will use NetBiosNameService.
This only works for the netbios-names of local clients/servers and i think this is not gogle.com :-).
Are wins active within your LAN ? then you should push the server-address with the connection.
If your VPN-connected clients use their own (the public) DNS server they can't found your internal servers.
Then you have to push your internal DNS-Server with the connection.
Can the client ping the DNS (and WINS) servers? (know they the route to the VPN-Client Subnet?)
This only works for the netbios-names of local clients/servers and i think this is not gogle.com :-).
Are wins active within your LAN ? then you should push the server-address with the connection.
If your VPN-connected clients use their own (the public) DNS server they can't found your internal servers.
Then you have to push your internal DNS-Server with the connection.
Can the client ping the DNS (and WINS) servers? (know they the route to the VPN-Client Subnet?)
Under the TCP/IP4 properties of the VPN connection, you can specify DNS servers.
You can use CMAK to create a fully customized VPN client and specify the DNS servers there.
ASKER
Thanks for the advice all -
In testing, if I statically set the DNS server on the VPN Client, the client works okay. However, my main concern is that this was working fine before...I'm not sure why it stopped working.
KeremE - The server terminating the VPN connection is able to resolve DNS entries correctly
Dkotte - I'm not able to resolve names on the local LAN or the Internet. The client is able to ping all devices by IP address (including DNS servers) while connected to the VPN.
Robdl / Sulimanw - Hard coding the DNS server on the SSTP VPN client properties would be an alternative if I'm able to figure out a way to do it via GPO (there are many laptops in our organization). Can you advise on this?
Thanks all!
In testing, if I statically set the DNS server on the VPN Client, the client works okay. However, my main concern is that this was working fine before...I'm not sure why it stopped working.
KeremE - The server terminating the VPN connection is able to resolve DNS entries correctly
Dkotte - I'm not able to resolve names on the local LAN or the Internet. The client is able to ping all devices by IP address (including DNS servers) while connected to the VPN.
Robdl / Sulimanw - Hard coding the DNS server on the SSTP VPN client properties would be an alternative if I'm able to figure out a way to do it via GPO (there are many laptops in our organization). Can you advise on this?
Thanks all!
It seems that your firewall does not push DNS addresses with VPN connection. Since they are available via IP but not FQDN it seenms that eithr the DNS name pushed by the VPN is incorrect or it does not push at all ..
Can you launch CMD after you've logged in to VPN and run ipconfig /all to make sure that your DNS settings are properly pushed from the VPN Server.
Can you launch CMD after you've logged in to VPN and run ipconfig /all to make sure that your DNS settings are properly pushed from the VPN Server.
You might lso try adding a persistent 'route add' command on the RRAS server for each subnet.
ASKER
There's definitely no DNS assigned - why is that not coming over? RRAS only allows me to set up a local pool of addresses - I used a pool from within my central site subnet.
Yeah but also there are options in which you can add some resources such as DNS... Since NetBIOS is enabled it is trying to query the DNS request iver NetBIOS.. So if you add an option for DNS it would push them too.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I resolved this myself.

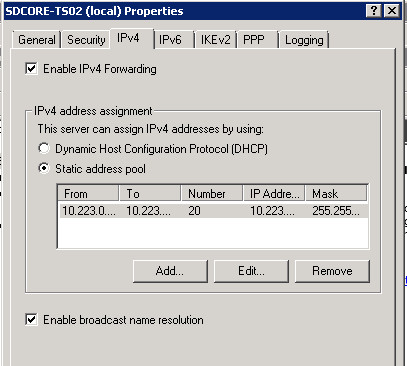
DNS settings in Microsoft DNS inherited from the VPN Server. As a rule of thumb if VPN Server con not resolve names then clients also cannot resolve. So you'd better check your VPN server first. Make sure that your VPN server could resolve names. Also you might like to check the routing and make sure that you're routing the traffic for the DNS segment traffic to the VPN interface and not the internet (through Default Gateway)
Cheers,
K.