tb03m
asked on
Routing between vlans
Hello,
I have a 3com 5500 switch with the following vlans setup:
Vlan1 10.0.0.0/16 (ip address 10.0.0.1)
Vlan10 192.168.0.0/16 (ip address 192.168.0.1, router 192.168.0.250)
Vlan20 172.16.1.0/24 (ip address 172.16.1.1, router 172.16.1.250)
I’d like vlan10 and vlan20 to talk to each other because I need to create a trust between 2 domains. Am I right in saying I can create static routes on the 3com 5500 on doing the following on the switch?
interface vlan-interface10
ip route-static 172.16.1.0 255.255.255.0 172.16.1.1
ip route-static 0.0.0.0 0.0.0.0 192.168.0.250
interface vlan-interface20
ip route-static 192.168.0.0 255.255.0.0 192.168.0.1
ip route-static 0.0.0.0 0.0.0.0 172.16.1.250
Then set all client/servers with the default gateway of vlan10 192.168.0.1 and vlan20 172.16.1.1
thanks
I have a 3com 5500 switch with the following vlans setup:
Vlan1 10.0.0.0/16 (ip address 10.0.0.1)
Vlan10 192.168.0.0/16 (ip address 192.168.0.1, router 192.168.0.250)
Vlan20 172.16.1.0/24 (ip address 172.16.1.1, router 172.16.1.250)
I’d like vlan10 and vlan20 to talk to each other because I need to create a trust between 2 domains. Am I right in saying I can create static routes on the 3com 5500 on doing the following on the switch?
interface vlan-interface10
ip route-static 172.16.1.0 255.255.255.0 172.16.1.1
ip route-static 0.0.0.0 0.0.0.0 192.168.0.250
interface vlan-interface20
ip route-static 192.168.0.0 255.255.0.0 192.168.0.1
ip route-static 0.0.0.0 0.0.0.0 172.16.1.250
Then set all client/servers with the default gateway of vlan10 192.168.0.1 and vlan20 172.16.1.1
thanks
ASKER
Thanks for the reply. The 5500 is a layer 3 device so can do the routing. It's got a few layer 2 devices plugged into it.
The 5500 may be a Layer3 capable device,....but until you actually "enabled routing" on it,....it is just a Layer2 Switch that has been chopped into 3 pieces by the VLAN config.
Also even if you had a separate Router,...that doesn't automatically mean trunking. You can still run 3 separate physical cables to the router so that each segment gets the full dedicated bandwidth of the physical cable. If you trunk a single cable with three VLANs then each Segment only gets 33% of the bandwidth capacity of the physical cable if all three Segments are getting hit with traffic at the same moment. Trunking = Bad,...it is only a convenience tool when you can only afford to run a single cable, but you sacrifice performance.
Remember that when you get the 5500 working corerectly,..that it must become the Default Gateway for all the Hosts on the LAN,...the 5500 will then use your Firewall Device as its Default Gateway. Then you must configure the Firewall to know that it must use the 5500 as the "gateway" to reach the other LAN Segments,...usually that is done with a Static Route and editing the LAT to cover all LAN Ranges,...but some Firewalls are a bit strange in how that is done,...your mileage may vary,..as they say.
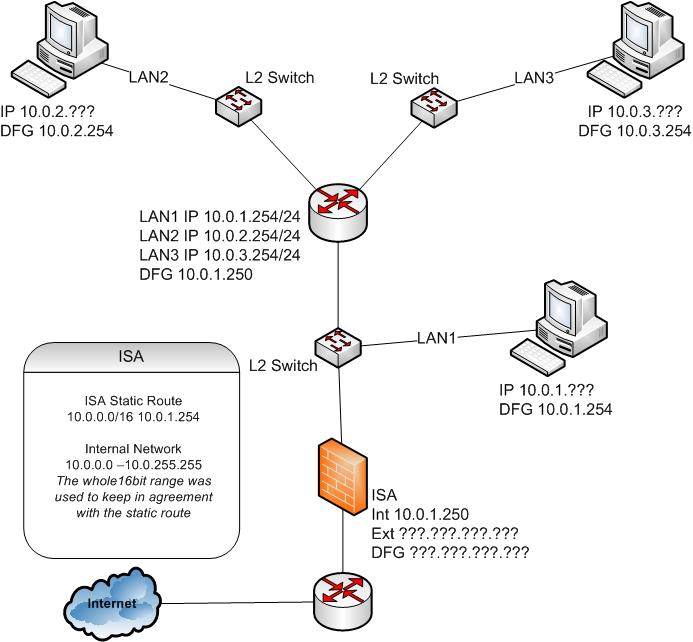
Here's a diagram of how it works out. Note that each L2 Switch icons represents the entire segment they are in,..they don't represent an individual switches. The Firewall in the Diagram is MS ISA Server, but the principle is the same.
Also even if you had a separate Router,...that doesn't automatically mean trunking. You can still run 3 separate physical cables to the router so that each segment gets the full dedicated bandwidth of the physical cable. If you trunk a single cable with three VLANs then each Segment only gets 33% of the bandwidth capacity of the physical cable if all three Segments are getting hit with traffic at the same moment. Trunking = Bad,...it is only a convenience tool when you can only afford to run a single cable, but you sacrifice performance.
Remember that when you get the 5500 working corerectly,..that it must become the Default Gateway for all the Hosts on the LAN,...the 5500 will then use your Firewall Device as its Default Gateway. Then you must configure the Firewall to know that it must use the 5500 as the "gateway" to reach the other LAN Segments,...usually that is done with a Static Route and editing the LAT to cover all LAN Ranges,...but some Firewalls are a bit strange in how that is done,...your mileage may vary,..as they say.
Here's a diagram of how it works out. Note that each L2 Switch icons represents the entire segment they are in,..they don't represent an individual switches. The Firewall in the Diagram is MS ISA Server, but the principle is the same.

I would also recommend not skipping numbers in the VLAN Names. It is pointless,...just do VLAN1, VLAN2, VLAN3. They are not IP Numbers,...you don't need to reserve anything for anything.
Lastley,...before you make a HUGE mess...
Get rid of the /16 bit masks!!! There is no way that you can put 65,534 Hosts on a single Segment,...so don't waste the addresses. Stop that now before it grows into a Frankenstein Monster that is very difficult to correct later. Your current scheme is set to have 131,322 Hosts on 3 segments,...which is absolutely impossible to do,...but it will give you over 130,000 chances to get bitten in the rearend when you try to expand to other sites or join VPNs to other established companies
Yes,..you can wast RFC Private addresses,...you'll find that out when the inevitable happens and you are asked to setup a VPN with another company or another site and,...whala!,...address conflicts due to overlapping IP Ranges,...so the routing refuses to route to the other company or other site. It doesn't matter if a specific IP# has no PC using it,...it still is accounted for in the Routing Table and will effect the routing procedures.
On top of all that,...Ethernet efficiency starts to drop off around 250-300 Hosts on a segment due to the increase in Broadcasts,..and the industry is inventing more and more devices, applications, and protocols that use and create broadcasting. So it is only going to get worse. So never go beyond a /24 bit mask that limits a segment to 254 Hosts,...that is the perfect maximum size.
Yes you might "get away" with a /23 bit mask with 510 Hosts,..but are you just wanting to "get away" with something,...or do you actually want things to perform at their best?
Get rid of the /16 bit masks!!! There is no way that you can put 65,534 Hosts on a single Segment,...so don't waste the addresses. Stop that now before it grows into a Frankenstein Monster that is very difficult to correct later. Your current scheme is set to have 131,322 Hosts on 3 segments,...which is absolutely impossible to do,...but it will give you over 130,000 chances to get bitten in the rearend when you try to expand to other sites or join VPNs to other established companies
Yes,..you can wast RFC Private addresses,...you'll find that out when the inevitable happens and you are asked to setup a VPN with another company or another site and,...whala!,...address conflicts due to overlapping IP Ranges,...so the routing refuses to route to the other company or other site. It doesn't matter if a specific IP# has no PC using it,...it still is accounted for in the Routing Table and will effect the routing procedures.
On top of all that,...Ethernet efficiency starts to drop off around 250-300 Hosts on a segment due to the increase in Broadcasts,..and the industry is inventing more and more devices, applications, and protocols that use and create broadcasting. So it is only going to get worse. So never go beyond a /24 bit mask that limits a segment to 254 Hosts,...that is the perfect maximum size.
Yes you might "get away" with a /23 bit mask with 510 Hosts,..but are you just wanting to "get away" with something,...or do you actually want things to perform at their best?
ASKER
Thanks for your posts.
The 3com 5500 has already got routing enabled as the ip route-static 0.0.0.0 0.0.0.0 192.168.0.250 (TMG box) rule is already in there and its working.
I understand about the /16 bit mask, the system is one i've inherited and that will be sorted out but am I along the right lines with getting the 2 vlans to talk to each other?
The 3com 5500 has already got routing enabled as the ip route-static 0.0.0.0 0.0.0.0 192.168.0.250 (TMG box) rule is already in there and its working.
I understand about the /16 bit mask, the system is one i've inherited and that will be sorted out but am I along the right lines with getting the 2 vlans to talk to each other?
that will be sorted out but am I along the right lines with getting the 2 vlans to talk to each other?
Well,...you tell me. With what we have given you,..and comparing that to what you know you have in front of you,...what do you think? I don't really know your stuff where you are as well as you would. All I can do is try to give guide lines and point you in the proper direction. You kinda have to take it from there.
Now I can say that I don't see anything jumping out at me that is wrong (other than the /16 bit masks).
Well,...you tell me. With what we have given you,..and comparing that to what you know you have in front of you,...what do you think? I don't really know your stuff where you are as well as you would. All I can do is try to give guide lines and point you in the proper direction. You kinda have to take it from there.
Now I can say that I don't see anything jumping out at me that is wrong (other than the /16 bit masks).
"Trunking = Bad,...it is only a convenience tool when you can only afford to run a single cable, but you sacrifice performance."
Ha. You must deal with small networks and small numbers of VLANs. Although for this application I don't disagree.
Good luck,
Steve
Ha. You must deal with small networks and small numbers of VLANs. Although for this application I don't disagree.
Good luck,
Steve
Since your 3Com is a layer 3 switch you need to configure your layer 3 virtual interfaces for each VLAN. Which you will define the layer 3 virtual interface with the VLAN ID, Default Gateway IP and subnetmask for the VLAN, as well as IP helper-addresses for any DHCP, DNS services, if applicable. You won't need to configure routes for each network because all connected router 'connected' interfaces will pass traffic. If you don't won't certain networks to communicate you will need to implemtent ACLs (Access Control Lists). I would not recommend the suggestion of using a firewall for your default gateway for each of the VLANs. That would be a major bottleneck for inter-VLAN routing. Plus always want to avoid any router-on-a-stick type configuration. Now on your layer 3 switch you will need a 'Gateway of Last Resort' static route entry, which directs all Internet bound traffic to your firewall (not Inter-VLAN traffic). Your firewall will need to know about the internal networks and what interface or IP to get to them. This could be a single route or multiple depending on your IP design.
Also, as suggested consolidate your /16 IP addressing in to multiple /24 networks. In my network I use a 10.SITE.VLAN.HOST/24 structure that's very scalable. But do whatever works for your environment.
So all devices on a VLAN should be pointing to the virtual interface as it's default gateway.
Also, as suggested consolidate your /16 IP addressing in to multiple /24 networks. In my network I use a 10.SITE.VLAN.HOST/24 structure that's very scalable. But do whatever works for your environment.
So all devices on a VLAN should be pointing to the virtual interface as it's default gateway.
I would not recommend the suggestion of using a firewall for your default gateway for each of the VLANs. That would be a major bottleneck for inter-VLAN routing. Plus always want to avoid any router-on-a-stick type configuration.
I was not suggesting anything like that
Now on your layer 3 switch you will need a 'Gateway of Last Resort' static route entry, which directs all Internet bound traffic to your firewall (not Inter-VLAN traffic).
That is what I was suggesting. To clarify where I am coming from, in my environment it is all HP/Procurve routing and switching. There is no such thing as a Default Gateway for each VLAN with HP. With them "Default Gateway" is the only term they use (Gateway of Last Resort is a Cisco specific term) and there is only one per the entire physical device,...so it is the same thing functionally that Cisco calls the "Gateway of Last Resort".
So,...we are saying the same thing,...so we must be right :-).
I was not suggesting anything like that
Now on your layer 3 switch you will need a 'Gateway of Last Resort' static route entry, which directs all Internet bound traffic to your firewall (not Inter-VLAN traffic).
That is what I was suggesting. To clarify where I am coming from, in my environment it is all HP/Procurve routing and switching. There is no such thing as a Default Gateway for each VLAN with HP. With them "Default Gateway" is the only term they use (Gateway of Last Resort is a Cisco specific term) and there is only one per the entire physical device,...so it is the same thing functionally that Cisco calls the "Gateway of Last Resort".
So,...we are saying the same thing,...so we must be right :-).
Pwindell - Sorry, for the misunderstanding. After reviewing your comments I see what you were trying to depict. We somewhat different ways of diagraming and describing the same architecture; no big deal.
In my network, I use enterprise class Brocade/Foundry Network L2/L3 switches (once OEM'd by HP) for LAN along with Cisco routers for all WAN connectivity (Private MPLS and Internet). So the reason for using certain terminology is due to my many years as Cisco background as a past Cisco Network Consultant and Engineer. Therefore the term Default Gateway is relative and applicable to any brand of hardware you use (personal preference); Fyi... DFG was referrenced in your diagram in the same manner for each VLAN. Also, I prefer to use the Cisco term of Gateway of Last Resort to clearly differiniate from the Default Gateway term used on a VLAN by hosts, servers, and other network devices. This is a personal preference irrespective of brand of hardware plus most if not all network devices use the term Default Gateway which in L3 VLAN network points to the IP address of the virtual VLAN interface.
Now, if we talk about other Cisco terminologies like Access, Trunk, EtherChannel, etc... vs Tagged, Untagged, LAG (LACP), Trunk, etc... then I use the terminology that's specific to the vendors hardware to avoid confusion.
Anyway, we both are on point with our recommendations. So in that respect I don't take credit for your previously proposed recommendations, but I will validate your proposal.
In my network, I use enterprise class Brocade/Foundry Network L2/L3 switches (once OEM'd by HP) for LAN along with Cisco routers for all WAN connectivity (Private MPLS and Internet). So the reason for using certain terminology is due to my many years as Cisco background as a past Cisco Network Consultant and Engineer. Therefore the term Default Gateway is relative and applicable to any brand of hardware you use (personal preference); Fyi... DFG was referrenced in your diagram in the same manner for each VLAN. Also, I prefer to use the Cisco term of Gateway of Last Resort to clearly differiniate from the Default Gateway term used on a VLAN by hosts, servers, and other network devices. This is a personal preference irrespective of brand of hardware plus most if not all network devices use the term Default Gateway which in L3 VLAN network points to the IP address of the virtual VLAN interface.
Now, if we talk about other Cisco terminologies like Access, Trunk, EtherChannel, etc... vs Tagged, Untagged, LAG (LACP), Trunk, etc... then I use the terminology that's specific to the vendors hardware to avoid confusion.
Anyway, we both are on point with our recommendations. So in that respect I don't take credit for your previously proposed recommendations, but I will validate your proposal.
ASKER
Thanks for all the comments. When I tried to add the following ip route:
interface vlan-interface10
ip route-static 172.16.1.0 255.255.255.0 172.16.1.1
I got invalid next hop address. From this I found that the 3com 5500 automatically routes between vlans when you setup more than one vlan. I hadn't correctly configured the devices with the gateway address. I do however get some strange behaviour, if I do a tracert from vlan20 (172.16.1.0/24) to for example www.google.com the first hop is ok (this hits 172.16.1.1) but sometimes the second hit is the router on the vlan10 side (192.168.0.250).......
thanks
interface vlan-interface10
ip route-static 172.16.1.0 255.255.255.0 172.16.1.1
I got invalid next hop address. From this I found that the 3com 5500 automatically routes between vlans when you setup more than one vlan. I hadn't correctly configured the devices with the gateway address. I do however get some strange behaviour, if I do a tracert from vlan20 (172.16.1.0/24) to for example www.google.com the first hop is ok (this hits 172.16.1.1) but sometimes the second hit is the router on the vlan10 side (192.168.0.250).......
thanks
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
One thing I thought was unusual, and this maybe something completely related to 3Com, typically you configure an IP address and subnet mask on the interface. Your static routes are then globally defined to direct traffic vs having static routes defined on each interface.
Most layer 3 switches and routers - layer 3 interfaces (physically connected or virtual will route between each other with no static routes. Connected routes are placed in the routing table by default. Connected routes have an administrative distance of 0, where a static route is 1, unless configured otherwise, and then dynamic routing protocols have their respective administrative distances.
The point is that static route should only need to be configured for your gateway of last resort/default gateway for Internet bound traffic. I am not sure what the configuration may look like if static routes are defined on the interface vs. Globally. If their defined at the interface level then can you still configure an IP address for the interface. If so, how does the routing table look without a static route on the interface? Does the virtual interface IP network show in the routing table? If so, then you certainly shouldn't require a static route on the interface.
Most layer 3 switches and routers - layer 3 interfaces (physically connected or virtual will route between each other with no static routes. Connected routes are placed in the routing table by default. Connected routes have an administrative distance of 0, where a static route is 1, unless configured otherwise, and then dynamic routing protocols have their respective administrative distances.
The point is that static route should only need to be configured for your gateway of last resort/default gateway for Internet bound traffic. I am not sure what the configuration may look like if static routes are defined on the interface vs. Globally. If their defined at the interface level then can you still configure an IP address for the interface. If so, how does the routing table look without a static route on the interface? Does the virtual interface IP network show in the routing table? If so, then you certainly shouldn't require a static route on the interface.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for all the comments. It is a single site but with 2 networks which have 2 separate internet connections. I think when i've added the second route:
interface vlan-interface10
ip route-static 172.16.1.0 255.255.255.0 172.16.1.1
The 3com has just taken this as another route to get out where I thought it would be a route for a certain VLAN. So in effect I created 2 routes of last resort.
Thanks for all your help and your comments will help in the future.
interface vlan-interface10
ip route-static 172.16.1.0 255.255.255.0 172.16.1.1
The 3com has just taken this as another route to get out where I thought it would be a route for a certain VLAN. So in effect I created 2 routes of last resort.
Thanks for all your help and your comments will help in the future.
If you have two segments with each trying to use its own distinct internet connection (to me that means two firewalls) then it is a recipe for problems and it will require two LAN routers with a point-to-point link between them. Each site will use it's own LAN Router as their DFG and then each LAN Router will use,...as its DFG,..whatever respective Firewall it should use according to which ever Internet connection it is supposed to use. Routing between the segments themselves (assuming you want there to be) can either be handled by static Routes on the Routers or via Dynamic Routing Protocols.
Ignore the fact that I used the term WAN in the diagram,...it doesn't change the concept,...these are pre-drawn generic diagrams.
It looks like this....
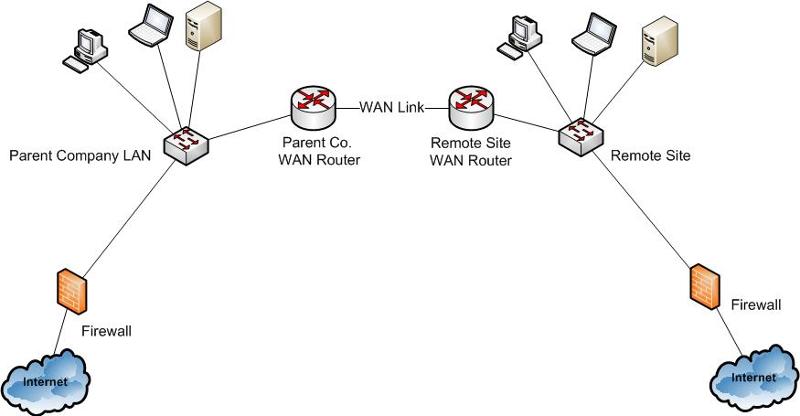
Ignore the fact that I used the term WAN in the diagram,...it doesn't change the concept,...these are pre-drawn generic diagrams.
It looks like this....

That said, you need a layer 3 device to do the routing, which typically would mean that you set up a trunk from the switch to a router, and define sub-interfaces on the router to correspond to the vlans. Your inter-vlan traffic would be routed by the router.
Good luck,
Steve