ozzietek
asked on
Autodiscover and SSL Warnings during Exchange 2010 Migration.
Hi,
We are in the process of migration of Exchange 2007 to Exchange 2010. Suddenly we are start getting SSL security alert on every client machine.

Since our new servers are still not in production, users should only contact to our old mail server.
But I suspect all three new exchange server are registered in AutoDiscover site scope along with old server.
So I am just looking for way to un-register the new server from auto-discover site scope or the time being and when we ready to move mailboxes we will re-register them.
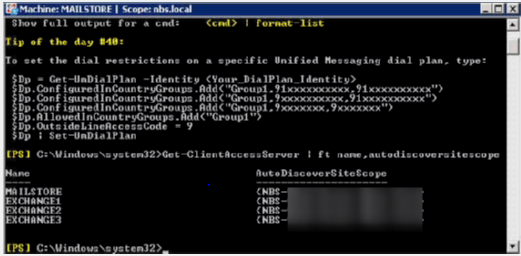
All are register under same site scope, or is there any other temp way so that Outlook client does not search for these server right now.
We are in the process of migration of Exchange 2007 to Exchange 2010. Suddenly we are start getting SSL security alert on every client machine.
Since our new servers are still not in production, users should only contact to our old mail server.
But I suspect all three new exchange server are registered in AutoDiscover site scope along with old server.
So I am just looking for way to un-register the new server from auto-discover site scope or the time being and when we ready to move mailboxes we will re-register them.
All are register under same site scope, or is there any other temp way so that Outlook client does not search for these server right now.
Check if you are using self signed certificates on your new 2010 Exchange servers. Import on your Exchange 2010 servers your current certificate or buy one new.
which box is your RPCClientAccessServer pointing to?
Get-MailboxDatabase | FT Name,RPC*
Regards,
Exchange_Geek
Get-MailboxDatabase | FT Name,RPC*
Regards,
Exchange_Geek
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi Guys, thanks for your comments, sorry for late reply, actually I had solved the problem on that day, by changing the firewall settings.
I had set autodiscover URI on all four servers to External URL and point that external URL to my old server.
I had set autodiscover URI on all four servers to External URL and point that external URL to my old server.
ASKER
I've requested that this question be closed as follows:
Accepted answer: 0 points for ozzietek's comment #a38353839
for the following reason:
I resolved the issue on the same day... As i post the quesiton.
Accepted answer: 0 points for ozzietek's comment #a38353839
for the following reason:
I resolved the issue on the same day... As i post the quesiton.
>> I had set autodiscover URI on all four servers to External URL and point that external URL to my old server.
I hate hitting "Object" to these close requests, but with respect, I feel that was what was alluded to in my comment at http:#a38304403:
"...update the SCP created for the Autodiscover service on the Exchange 2010 CAS to hand out the URL of one of the Exchange 2007 Autodiscover connection points..."
"... autodiscover connection point would typically be autodiscover.company.com, which should be mapped via DNS (using split DNS where necessary) to the Exchange 2007 servers at this time..."
As that is ultimately what you did (using your firewall, rather than split DNS - both are just as good methods), I feel I must contest the closure on this occasion.
-Matt
I hate hitting "Object" to these close requests, but with respect, I feel that was what was alluded to in my comment at http:#a38304403:
"...update the SCP created for the Autodiscover service on the Exchange 2010 CAS to hand out the URL of one of the Exchange 2007 Autodiscover connection points..."
"... autodiscover connection point would typically be autodiscover.company.com, which should be mapped via DNS (using split DNS where necessary) to the Exchange 2007 servers at this time..."
As that is ultimately what you did (using your firewall, rather than split DNS - both are just as good methods), I feel I must contest the closure on this occasion.
-Matt