ddotson
asked on
Active Directory DNS test shows failure
Hello:
I was working on some DNS stuff and found references to a bunch of old domain controllers that are no longer. I started cleaning them up and wondered if we are having performance issues due to all of these old entries. I Google'd the issue and found the DCDIAG /TEST:DNS test. I ran that and got this as a summary:
I'm concerned about the "del" column, which has to do with Delegation. I'm not sure what the implications of this failure are. Can someone enlighten me?
Thanks,
Dan
I was working on some DNS stuff and found references to a bunch of old domain controllers that are no longer. I started cleaning them up and wondered if we are having performance issues due to all of these old entries. I Google'd the issue and found the DCDIAG /TEST:DNS test. I ran that and got this as a summary:
Summary of DNS test results:
Auth Basc Forw Del Dyn RReg Ext
_________________________________________________________________
Domain: domain.com
DC01 PASS PASS PASS FAIL PASS PASS n/a
DC02 PASS PASS PASS FAIL PASS PASS n/a
DC03 PASS PASS PASS FAIL PASS PASS n/a
DC04 PASS PASS PASS FAIL PASS PASS n/a
DC05 PASS PASS PASS FAIL PASS WARN n/a
DC06 PASS PASS PASS FAIL PASS WARN n/a
......................... domain.com failed test DNSI'm concerned about the "del" column, which has to do with Delegation. I'm not sure what the implications of this failure are. Can someone enlighten me?
Thanks,
Dan
ASKER
So all of our DNS servers are domain controllers. From your article I read:
Does this mean that we have broken delegations? What does this mean? What are the implications?
The delegation test confirms that the delegated name server is a functioning DNS Server.
The delegation test checks for broken delegations by ensuring that all NS records in the Active Directory domain zone in which the target domain controller resides have corresponding glue A records.
Does this mean that we have broken delegations? What does this mean? What are the implications?
Hi ddotson,
This means some of the zones you have configured in your DNS servers are not delegated. That in a more practical way means that those DNS servers are not giving any name answers regarding those zones.
If this is your internal domain you should create the appropriate delegations on your DNS servers, to create check out this document:
http://technet.microsoft.com/en-us/library/cc785881(v=ws.10).aspx
Regards,
GFilipe
This means some of the zones you have configured in your DNS servers are not delegated. That in a more practical way means that those DNS servers are not giving any name answers regarding those zones.
If this is your internal domain you should create the appropriate delegations on your DNS servers, to create check out this document:
http://technet.microsoft.com/en-us/library/cc785881(v=ws.10).aspx
Regards,
GFilipe
ASKER
I saw this entry in the section for each domain controller (dns server):
The entry "lgedc.domain.com" is an old domain controller. There is nothing else in that subdomain.
I looked at the instructions for adding delegations, but it didn't make sense. Here is a screen shot:

This is for our internal active directory domain name. I'm not sure what I would enter here.
Also, we use these DNS servers for our websites (split-brain). So there are many many zones.
I hope that I'm making sense.
TEST: Delegations (Del)
Delegation information for the zone: domain.com.
Delegated domain name: _msdcs.domain.com.
Error: DNS server: lgedc.domain.com. IP:<Unavailable>
[Missing glue A record]
[Error details: 9714 (Type: Win32 - Description: DNS name does not exist.)]The entry "lgedc.domain.com" is an old domain controller. There is nothing else in that subdomain.
I looked at the instructions for adding delegations, but it didn't make sense. Here is a screen shot:

This is for our internal active directory domain name. I'm not sure what I would enter here.
Also, we use these DNS servers for our websites (split-brain). So there are many many zones.
I hope that I'm making sense.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
OK - so to be clear, we don't *think* we are seeing any problems. However, that could be manifested as something else, and DNS be the real culprit. I don't know at this time.
I have made three changes based on what you've all posted:
1) I checked the domain controller's DNS settings. Most were mis-configured to point to another domain controller. I pointed the primary DNS to itself and then the secondary to a domain controller outside of the AD site.
2) I configured all forwarders to go to the Internet (8.8.8.8, etc) instead of another domain controller. To be clear, these were forwarding to a single domain controller, which was then forwarding to the internet. Now they all forward to the internet.
3) Checked for stale DC per the previous instructions. Did not find any.
For clarification, here is an image of that strange entry:
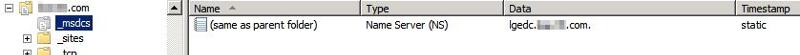
The Zone listed is our AD domain. The entry is for the old lgedc.domain.com domain controller. I can delete this? Should there be entries for the other domain controllers there?
Thanks,
Dan
I have made three changes based on what you've all posted:
1) I checked the domain controller's DNS settings. Most were mis-configured to point to another domain controller. I pointed the primary DNS to itself and then the secondary to a domain controller outside of the AD site.
2) I configured all forwarders to go to the Internet (8.8.8.8, etc) instead of another domain controller. To be clear, these were forwarding to a single domain controller, which was then forwarding to the internet. Now they all forward to the internet.
3) Checked for stale DC per the previous instructions. Did not find any.
For clarification, here is an image of that strange entry:

The Zone listed is our AD domain. The entry is for the old lgedc.domain.com domain controller. I can delete this? Should there be entries for the other domain controllers there?
Thanks,
Dan
You may delete this and restart DNS server service
ASKER
I've rerun the test and everything passes!
I'm still a little foggy about the delegation. If no zones are delegated, are we at some sort of risk? Say one server goes down, etc?
I'm still a little foggy about the delegation. If no zones are delegated, are we at some sort of risk? Say one server goes down, etc?
For such cases only we select secondary DNS servers in TCP/IP search orders in DC as well as member clients
ASKER
Thank you everyone for your help. I think things will be much cleaner going forward.
Thanks,
Dan
Thanks,
Dan
Hi,
To understand zone delegation I believe this is a good doc:
http://technet.microsoft.com/en-us/library/cc771640.aspx
further to this:
"Active Directory (AD) uses DNS as its locator service to support the various types of services that AD offers, such as Global Catalog (GC), Kerberos, and (LDAP). Sometimes clients might need to contact a Microsoft-hosted service. For that reason, each domain in DNS has an _msdcs subdomain that hosts only DNS SRV records that are registered by Microsoft-based services. The Netlogon process dynamically creates these records on each domain controller (DC). The _msdcs subdomain also includes the globally unique identifier (GUID) for all domains in the forest and a list of GC servers.
If you install a new forest on a system that runs Windows Server 2003 and let the Dcpromo wizard configure DNS, Dcpromo will actually create a separate zone called _msdcs.<forest name> on the DNS server. This zone is configured to store its records in a forestwide application directory partition, ForestDNSZones, which is replicated to every DC in the forest that runs the DNS service. This replication makes the zone highly available anywhere in the forest."
Hope this answers your question,
Regards,
GFilipe
To understand zone delegation I believe this is a good doc:
http://technet.microsoft.com/en-us/library/cc771640.aspx
further to this:
"Active Directory (AD) uses DNS as its locator service to support the various types of services that AD offers, such as Global Catalog (GC), Kerberos, and (LDAP). Sometimes clients might need to contact a Microsoft-hosted service. For that reason, each domain in DNS has an _msdcs subdomain that hosts only DNS SRV records that are registered by Microsoft-based services. The Netlogon process dynamically creates these records on each domain controller (DC). The _msdcs subdomain also includes the globally unique identifier (GUID) for all domains in the forest and a list of GC servers.
If you install a new forest on a system that runs Windows Server 2003 and let the Dcpromo wizard configure DNS, Dcpromo will actually create a separate zone called _msdcs.<forest name> on the DNS server. This zone is configured to store its records in a forestwide application directory partition, ForestDNSZones, which is replicated to every DC in the forest that runs the DNS service. This replication makes the zone highly available anywhere in the forest."
Hope this answers your question,
Regards,
GFilipe
http://technet.microsoft.com/en-us/library/cc776854%28v=WS.10%29.aspx
Make sure all NS record has A record.