rollnpc
asked on
Ctrl+Alt+Del missing from Windows 8 Domain member
Background:
I am running Windows 8 Enterprise 64 bit. (RTM not a preview)
It is joined to a 2008 R2 Domain.
The Functional level of the domain is 2008 R2.
There have been no domain changes or GPO changes.
This is a new install of Windows 8.
Yes I can replicate the problem on other Windows 8 machines and VM.
The problem does not occur on any other Windows OS, just on 8.
Issue:
When the computer boots to Windows 8, or the user returns from a Lock or Log Off, they are not prompted with the Ctrl+alt+del requirement. They simply click any key or the mouse button and they are prompted for password. This is only common to Windows 8 computers. All XP, 2003, 7, Vista, 2008, etc. systems on the domain require the Crt+alt+del key press.
In my research there is the ability to disable the ctrl+alt+del but no option to require it. (possibly setting the GPO to disabled rather than not defined, but why would that matter?) This is not the case in my domain, this GPO is set to not defined and all other flavors of Windows require the key press as expected. In my reading, any domain member, including Windows 8 systems, should require the key press out of the box. I should not have to change anything, just the fact it is a domain member should require this.
Anyone else see this behavior?
Any ideas on how to force the ctrl+alt+del on a Windows 8 Enterprise Domain member system?
This needs to be a domain wide solution, not a local edit.
I am running Windows 8 Enterprise 64 bit. (RTM not a preview)
It is joined to a 2008 R2 Domain.
The Functional level of the domain is 2008 R2.
There have been no domain changes or GPO changes.
This is a new install of Windows 8.
Yes I can replicate the problem on other Windows 8 machines and VM.
The problem does not occur on any other Windows OS, just on 8.
Issue:
When the computer boots to Windows 8, or the user returns from a Lock or Log Off, they are not prompted with the Ctrl+alt+del requirement. They simply click any key or the mouse button and they are prompted for password. This is only common to Windows 8 computers. All XP, 2003, 7, Vista, 2008, etc. systems on the domain require the Crt+alt+del key press.
In my research there is the ability to disable the ctrl+alt+del but no option to require it. (possibly setting the GPO to disabled rather than not defined, but why would that matter?) This is not the case in my domain, this GPO is set to not defined and all other flavors of Windows require the key press as expected. In my reading, any domain member, including Windows 8 systems, should require the key press out of the box. I should not have to change anything, just the fact it is a domain member should require this.
Anyone else see this behavior?
Any ideas on how to force the ctrl+alt+del on a Windows 8 Enterprise Domain member system?
This needs to be a domain wide solution, not a local edit.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Yes I agree it definitely should require Ctrl Alt Del, but things don't always work as they should.
Something to have prepared would be the results of
gpresult /R
this will tell you what policies are being applied as well as other information. Very useful in this situation, will help determine if policies are actually being applied at all like they should be.
Something to have prepared would be the results of
gpresult /R
this will tell you what policies are being applied as well as other information. Very useful in this situation, will help determine if policies are actually being applied at all like they should be.
This is strange but new feature. Remember that Windows 8 is developed not only for PCs :) Microsoft plans to take some tablet market and that's why you don't have to use CTRL+ALT+DEL to be prompt for password as tablets...
have no this key combination :D They are touch screen devices and probably that was the plan to not use CTRL+ALT+DEL combination to re-logon
that's all
Regards,
Krzysztof
have no this key combination :D They are touch screen devices and probably that was the plan to not use CTRL+ALT+DEL combination to re-logon
that's all
Regards,
Krzysztof
You know, I missed the very last sentence of the question.
Trying to determine what, if any group policy will make this adjustment for you. If not, I strongly suspect it can be done with a registry edit that can be pushed out through script or group policy and the setting may be preserved on systems deployed via imaging (which, if you're using Enterprise, would most likely be the best way for you to deploy this!)
Unfortunately, I may not have an answer until late tonight/tomorrow unless others I'm talking to chime in after they can test/check. Philip? :-)
I will say I reviewed the list of group policies in 2012 and there does NOT appear to be one that specifically addresses this.
Trying to determine what, if any group policy will make this adjustment for you. If not, I strongly suspect it can be done with a registry edit that can be pushed out through script or group policy and the setting may be preserved on systems deployed via imaging (which, if you're using Enterprise, would most likely be the best way for you to deploy this!)
Unfortunately, I may not have an answer until late tonight/tomorrow unless others I'm talking to chime in after they can test/check. Philip? :-)
I will say I reviewed the list of group policies in 2012 and there does NOT appear to be one that specifically addresses this.
Shown is the GPO setup we use for all of our deploys.
Note that we use an OU structure that is either SBS based (MyBusiness --> Computers --> SBSComputers) or we structure our OUs similarly for our Stack deploys (SITES (if used) --> SiteComputers --> UserComputers or SITES --> SiteComputers --> ServerSystems).
We do not create and link GPOs at the domain level if we can help it. The default Computers container is not where we leave any PC or member Server. The same is true for user accounts.
With the shown settings Windows 8, 7, Vista, XP Professional/Business and up will require the CTRL+ALT+DEL to log on.
We also set the user names to not show while the system is locked or when they do go to log on. It is an extra step for them but saves a someone/stranger scoping a logon by hitting the key strokes (BTDT).
[EDIT] Sorry for the multiple edits. Still getting used to this new interface. :P
Philip
ASKER
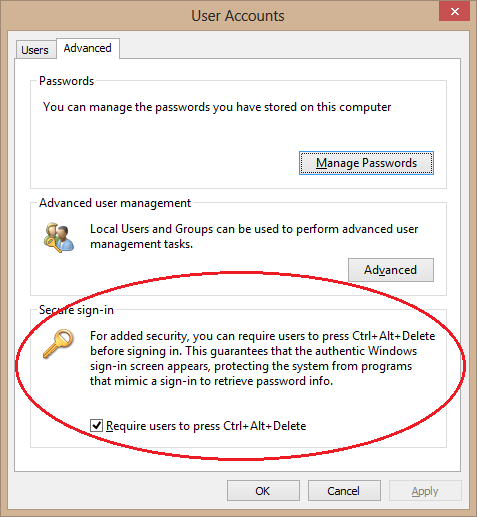
I appears that the best/easiest way to accomplish this is to apply the GPO in the below manner:
GPO Location = Computer > Policies > Windows Settings > Security Settings > Local Policies > Security Options
Set the policy = "Interactive logon: Do not require CTRL+ALT+DEL" to to "Disabled"
After a" gpupdate /force" or a reboot CTRL+ALT+DEL will be required.
GPO Location = Computer > Policies > Windows Settings > Security Settings > Local Policies > Security Options
Set the policy = "Interactive logon: Do not require CTRL+ALT+DEL" to to "Disabled"
After a" gpupdate /force" or a reboot CTRL+ALT+DEL will be required.
2 cts: It has officially changed, yes. See the policy description.
Default on domain-computers: Enabled: At least Windows 8/
Disabled: Windows 7 or earlier.
Default on stand-alone computers: Enabled.
ASKER
Thanks for the answer and I will test it after the weekend and check back.