LDAP Manager Distinguished Name & LDAP User Search Base not working it seems
Dear experts,
I am not getting anywhere trying to integrate Cisco Unity Connection version: 8.6.2.20000-7 with our MS server 2008 Active Directory.
I am getting this error: Error while Connecting to ldap://IP address:389, null
I have tried several ports mention in the internet Cisco sites, created an instance in Active Directory Lightweight Directory services, generated a schema report confirming what the actual distinguished names should be and what I think the search base should be as well.
When I run a connection test using the LDAP.exe tool everything is working well. Here is what I am getting:
ld = ldap_open("172.16.100.10",
Established connection to 172.16.100.10.
Retrieving base DSA information...
Getting 1 entries:
Dn: (RootDSE)
configurationNamingContext
currentTime: 12/19/2012 2:17:40 PM Central Standard Time;
defaultNamingContext: DC=is,DC=ad;
dnsHostName: DSS-TX-DC01.is.ad;
domainControllerFunctional
domainFunctionality: 2 = ( WIN2003 );
dsServiceName: CN=NTDS Settings,CN=DSS-TX-DC01,CN
forestFunctionality: 2 = ( WIN2003 );
highestCommittedUSN: 553569;
isGlobalCatalogReady: TRUE;
isSynchronized: TRUE;
ldapServiceName: is.ad:dss-tx-dc01$@IS.AD;
namingContexts (5): DC=is,DC=ad; CN=Configuration,DC=is,DC=
rootDomainNamingContext: DC=is,DC=ad;
schemaNamingContext: CN=Schema,CN=Configuration
serverName: CN=DSS-TX-DC01,CN=Servers,
subschemaSubentry: CN=Aggregate,CN=Schema,CN=
supportedCapabilities (5): 1.2.840.113556.1.4.800 = ( ACTIVE_DIRECTORY ); 1.2.840.113556.1.4.1670 = ( ACTIVE_DIRECTORY_V51 ); 1.2.840.113556.1.4.1791 = ( ACTIVE_DIRECTORY_LDAP_INTE
supportedControl (29): 1.2.840.113556.1.4.319 = ( PAGED_RESULT ); 1.2.840.113556.1.4.801 = ( SD_FLAGS ); 1.2.840.113556.1.4.473 = ( SORT ); 1.2.840.113556.1.4.528 = ( NOTIFICATION ); 1.2.840.113556.1.4.417 = ( SHOW_DELETED ); 1.2.840.113556.1.4.619 = ( LAZY_COMMIT ); 1.2.840.113556.1.4.841 = ( DIRSYNC ); 1.2.840.113556.1.4.529 = ( EXTENDED_DN ); 1.2.840.113556.1.4.805 = ( TREE_DELETE ); 1.2.840.113556.1.4.521 = ( CROSSDOM_MOVE_TARGET ); 1.2.840.113556.1.4.970 = ( GET_STATS ); 1.2.840.113556.1.4.1338 = ( VERIFY_NAME ); 1.2.840.113556.1.4.474 = ( RESP_SORT ); 1.2.840.113556.1.4.1339 = ( DOMAIN_SCOPE ); 1.2.840.113556.1.4.1340 = ( SEARCH_OPTIONS ); 1.2.840.113556.1.4.1413 = ( PERMISSIVE_MODIFY ); 2.16.840.1.113730.3.4.9 = ( VLVREQUEST ); 2.16.840.1.113730.3.4.10 = ( VLVRESPONSE ); 1.2.840.113556.1.4.1504 = ( ASQ ); 1.2.840.113556.1.4.1852 = ( QUOTA_CONTROL ); 1.2.840.113556.1.4.802 = ( RANGE_OPTION ); 1.2.840.113556.1.4.1907 = ( SHUTDOWN_NOTIFY ); 1.2.840.113556.1.4.1948 = ( RANGE_RETRIEVAL_NOERR ); 1.2.840.113556.1.4.1974 = ( FORCE_UPDATE ); 1.2.840.113556.1.4.1341 = ( RODC_DCPROMO ); 1.2.840.113556.1.4.2026 = ( DN_INPUT ); 1.2.840.113556.1.4.2064 = ( SHOW_RECYCLED ); 1.2.840.113556.1.4.2065 = ( SHOW_DEACTIVATED_LINK ); 1.2.840.113556.1.4.2066 = ( POLICY_HINTS );
supportedLDAPPolicies (14): MaxPoolThreads; MaxDatagramRecv; MaxReceiveBuffer; InitRecvTimeout; MaxConnections; MaxConnIdleTime; MaxPageSize; MaxQueryDuration; MaxTempTableSize; MaxResultSetSize; MinResultSets; MaxResultSetsPerConn; MaxNotificationPerConn; MaxValRange;
supportedLDAPVersion (2): 3; 2;
supportedSASLMechanisms (4): GSSAPI; GSS-SPNEGO; EXTERNAL; DIGEST-MD5;
-----------
-----------
0 = ldap_set_option(ld, LDAP_OPT_ENCRYPT, 0)
res = ldap_bind_s(ld, NULL, &NtAuthIdentity, NEGOTIATE (1158)); // v.3
{NtAuthIdentity: User='Unity$LDAP'; Pwd=<unavailable>; domain = 'is.ad'}
Authenticated as: 'IS\Unity$LDAP'.
-----------
I am out of ideas on how to enter the Distinguished names and search base anymore.
Here is an idea:
LDAP Manager Distinguished Name: Unity$LDAP@is.ad (as per active directory) or CN=Unity$LDAP,OU=Service Accounts,OU=company,DC=is,
LDAP User Search Base:dc=is,dc=ad
Pulling my hair out, I thank you for your time and assistance. M
I am not getting anywhere trying to integrate Cisco Unity Connection version: 8.6.2.20000-7 with our MS server 2008 Active Directory.
I am getting this error: Error while Connecting to ldap://IP address:389, null
I have tried several ports mention in the internet Cisco sites, created an instance in Active Directory Lightweight Directory services, generated a schema report confirming what the actual distinguished names should be and what I think the search base should be as well.
When I run a connection test using the LDAP.exe tool everything is working well. Here is what I am getting:
ld = ldap_open("172.16.100.10",
Established connection to 172.16.100.10.
Retrieving base DSA information...
Getting 1 entries:
Dn: (RootDSE)
configurationNamingContext
currentTime: 12/19/2012 2:17:40 PM Central Standard Time;
defaultNamingContext: DC=is,DC=ad;
dnsHostName: DSS-TX-DC01.is.ad;
domainControllerFunctional
domainFunctionality: 2 = ( WIN2003 );
dsServiceName: CN=NTDS Settings,CN=DSS-TX-DC01,CN
forestFunctionality: 2 = ( WIN2003 );
highestCommittedUSN: 553569;
isGlobalCatalogReady: TRUE;
isSynchronized: TRUE;
ldapServiceName: is.ad:dss-tx-dc01$@IS.AD;
namingContexts (5): DC=is,DC=ad; CN=Configuration,DC=is,DC=
rootDomainNamingContext: DC=is,DC=ad;
schemaNamingContext: CN=Schema,CN=Configuration
serverName: CN=DSS-TX-DC01,CN=Servers,
subschemaSubentry: CN=Aggregate,CN=Schema,CN=
supportedCapabilities (5): 1.2.840.113556.1.4.800 = ( ACTIVE_DIRECTORY ); 1.2.840.113556.1.4.1670 = ( ACTIVE_DIRECTORY_V51 ); 1.2.840.113556.1.4.1791 = ( ACTIVE_DIRECTORY_LDAP_INTE
supportedControl (29): 1.2.840.113556.1.4.319 = ( PAGED_RESULT ); 1.2.840.113556.1.4.801 = ( SD_FLAGS ); 1.2.840.113556.1.4.473 = ( SORT ); 1.2.840.113556.1.4.528 = ( NOTIFICATION ); 1.2.840.113556.1.4.417 = ( SHOW_DELETED ); 1.2.840.113556.1.4.619 = ( LAZY_COMMIT ); 1.2.840.113556.1.4.841 = ( DIRSYNC ); 1.2.840.113556.1.4.529 = ( EXTENDED_DN ); 1.2.840.113556.1.4.805 = ( TREE_DELETE ); 1.2.840.113556.1.4.521 = ( CROSSDOM_MOVE_TARGET ); 1.2.840.113556.1.4.970 = ( GET_STATS ); 1.2.840.113556.1.4.1338 = ( VERIFY_NAME ); 1.2.840.113556.1.4.474 = ( RESP_SORT ); 1.2.840.113556.1.4.1339 = ( DOMAIN_SCOPE ); 1.2.840.113556.1.4.1340 = ( SEARCH_OPTIONS ); 1.2.840.113556.1.4.1413 = ( PERMISSIVE_MODIFY ); 2.16.840.1.113730.3.4.9 = ( VLVREQUEST ); 2.16.840.1.113730.3.4.10 = ( VLVRESPONSE ); 1.2.840.113556.1.4.1504 = ( ASQ ); 1.2.840.113556.1.4.1852 = ( QUOTA_CONTROL ); 1.2.840.113556.1.4.802 = ( RANGE_OPTION ); 1.2.840.113556.1.4.1907 = ( SHUTDOWN_NOTIFY ); 1.2.840.113556.1.4.1948 = ( RANGE_RETRIEVAL_NOERR ); 1.2.840.113556.1.4.1974 = ( FORCE_UPDATE ); 1.2.840.113556.1.4.1341 = ( RODC_DCPROMO ); 1.2.840.113556.1.4.2026 = ( DN_INPUT ); 1.2.840.113556.1.4.2064 = ( SHOW_RECYCLED ); 1.2.840.113556.1.4.2065 = ( SHOW_DEACTIVATED_LINK ); 1.2.840.113556.1.4.2066 = ( POLICY_HINTS );
supportedLDAPPolicies (14): MaxPoolThreads; MaxDatagramRecv; MaxReceiveBuffer; InitRecvTimeout; MaxConnections; MaxConnIdleTime; MaxPageSize; MaxQueryDuration; MaxTempTableSize; MaxResultSetSize; MinResultSets; MaxResultSetsPerConn; MaxNotificationPerConn; MaxValRange;
supportedLDAPVersion (2): 3; 2;
supportedSASLMechanisms (4): GSSAPI; GSS-SPNEGO; EXTERNAL; DIGEST-MD5;
-----------
-----------
0 = ldap_set_option(ld, LDAP_OPT_ENCRYPT, 0)
res = ldap_bind_s(ld, NULL, &NtAuthIdentity, NEGOTIATE (1158)); // v.3
{NtAuthIdentity: User='Unity$LDAP'; Pwd=<unavailable>; domain = 'is.ad'}
Authenticated as: 'IS\Unity$LDAP'.
-----------
I am out of ideas on how to enter the Distinguished names and search base anymore.
Here is an idea:
LDAP Manager Distinguished Name: Unity$LDAP@is.ad (as per active directory) or CN=Unity$LDAP,OU=Service Accounts,OU=company,DC=is,
LDAP User Search Base:dc=is,dc=ad
Pulling my hair out, I thank you for your time and assistance. M
Use this document to collect a packet capture from the Unity server and try to connect to LDAP. attach it along a screen shot of your LDAP config.
ASKER
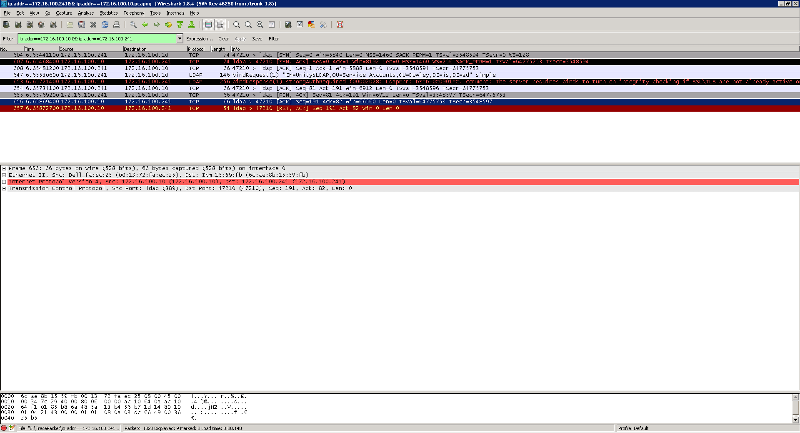
What Document? I did get this however with wireshark:
216 8.850656000 172.16.100.241 172.16.100.10 LDAP 147 bindRequest(1) "CN=Me,OU=OKC,OU=Users,OU=
217 8.852793000 172.16.100.10 172.16.100.241 LDAP 256 bindResponse(1) strongAuthRequired (00002028: LdapErr: DSID-0C0901FC, comment: The server requires binds to turn on integrity checking if SSL\TLS are not already active on the connection, data 0, v1db1)
I think I need to lighten up the authentication settings. I am looking where to do it.
216 8.850656000 172.16.100.241 172.16.100.10 LDAP 147 bindRequest(1) "CN=Me,OU=OKC,OU=Users,OU=
217 8.852793000 172.16.100.10 172.16.100.241 LDAP 256 bindResponse(1) strongAuthRequired (00002028: LdapErr: DSID-0C0901FC, comment: The server requires binds to turn on integrity checking if SSL\TLS are not already active on the connection, data 0, v1db1)
I think I need to lighten up the authentication settings. I am looking where to do it.
My apologies, this is the document:
https://supportforums.cisco.com/docs/DOC-11599
You should be able to connect without ticking the Use SSL box in Unity.
https://supportforums.cisco.com/docs/DOC-11599
You should be able to connect without ticking the Use SSL box in Unity.
ASKER
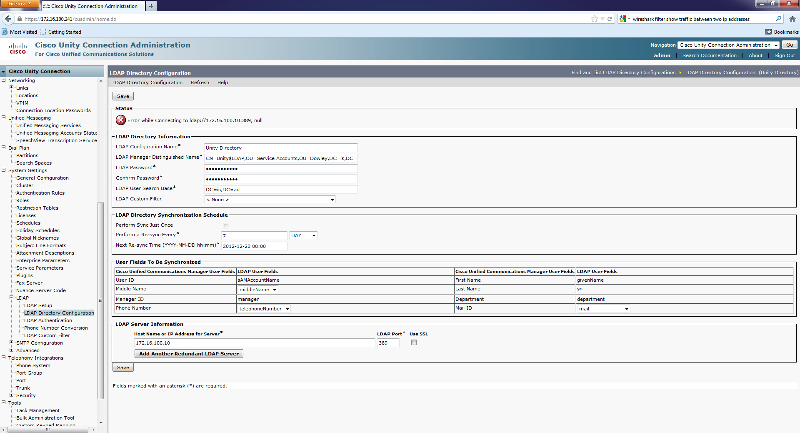
Well I am here now with this steps:
https://supportforums.cisco.com/docs/DOC-22014
However, I cannot get the certificate for Connection-trust to work it did for tomcat-trust as you can see here.
Here are the screenshots:
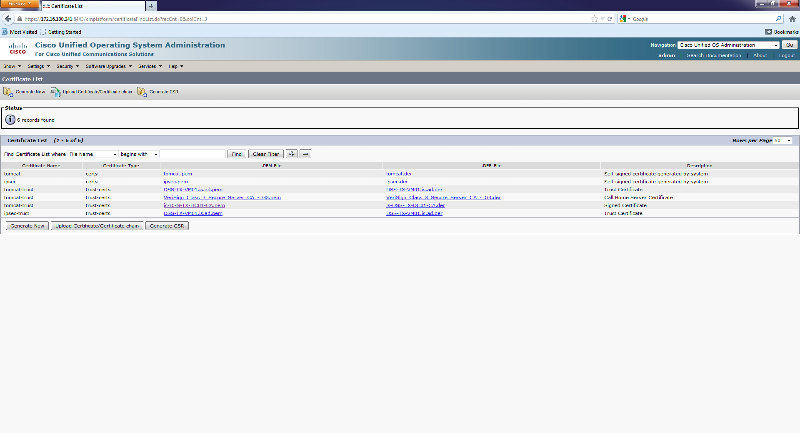
https://supportforums.cisco.com/docs/DOC-22014
However, I cannot get the certificate for Connection-trust to work it did for tomcat-trust as you can see here.
Here are the screenshots:


ASKER
This is what I got from Cisco Tech email:
As per our phone conversation, we need to check with AD team/system administrator for any such parameter on the AD 2008 R2 (disable the SSL/TTS certificate authentication) end which is preventing simple authentication from Unity Connection side. From the looks of it seems AD is configured to perform SASL authentication with the GSSAPI which is why UC is unable to connect.
Or, we will need to install LDAP trusted certificated on UC:
Step 1 From UC OS Administration page, navigate to Security > Certificate Management.
The Certificate List window displays.
Step 2 Click Upload Certificate. The Upload Certificate Trust List dialog box opens.
Step 3 Select directory-trust from the Certificate Name list.
Step 4 Enter the file to upload in the Upload File field.
Step 5 To upload the file, click the Upload File button.
Step 6 Log into Cisco Unified Serviceability page.
Step 7 Navigate to Tools > Control Center - Feature Services.
Step 8 Restart the service Cisco Dirsync.
Step 9 Log in to the Cisco Unified Communications Operating System CLI as an administrator.
Step 10 To restart the Tomcat service, enter the command: utils service restart Cisco Tomcat.
Step 11 After the services have been restarted, you can add the directory agreement for SSL.
Best regards,
As per our phone conversation, we need to check with AD team/system administrator for any such parameter on the AD 2008 R2 (disable the SSL/TTS certificate authentication) end which is preventing simple authentication from Unity Connection side. From the looks of it seems AD is configured to perform SASL authentication with the GSSAPI which is why UC is unable to connect.
Or, we will need to install LDAP trusted certificated on UC:
Step 1 From UC OS Administration page, navigate to Security > Certificate Management.
The Certificate List window displays.
Step 2 Click Upload Certificate. The Upload Certificate Trust List dialog box opens.
Step 3 Select directory-trust from the Certificate Name list.
Step 4 Enter the file to upload in the Upload File field.
Step 5 To upload the file, click the Upload File button.
Step 6 Log into Cisco Unified Serviceability page.
Step 7 Navigate to Tools > Control Center - Feature Services.
Step 8 Restart the service Cisco Dirsync.
Step 9 Log in to the Cisco Unified Communications Operating System CLI as an administrator.
Step 10 To restart the Tomcat service, enter the command: utils service restart Cisco Tomcat.
Step 11 After the services have been restarted, you can add the directory agreement for SSL.
Best regards,
The first capture that is the one that makes you think AD is requesting secure communications, where did you collect it from?
ASKER
The captures are between the server and the unity box using wireshark.
here is some output:
LDAPMessage bindResponse(1) strongAuthRequired (00002028: LdapErr: DSID-0C0901FC, comment: The server requires binds to turn on integrity checking if SSL\TLS are not already active on the connection, data 0, v1db1)
607 6.654684000 172.16.100.10 172.16.100.241 TCP 74 ldap > 47210 [SYN, ACK] Seq=0 Ack=1 Win=8192 Len=0 MSS=1460 WS=256 SACK_PERM=1 TSval=64775753 TSecr=3548594
656 6.658694000 172.16.100.10 172.16.100.241 TCP 66 ldap > 47210 [ACK] Seq=191 Ack=82 Win=66560 Len=0 TSval=64775753 TSecr=3548597
here is some output:
LDAPMessage bindResponse(1) strongAuthRequired (00002028: LdapErr: DSID-0C0901FC, comment: The server requires binds to turn on integrity checking if SSL\TLS are not already active on the connection, data 0, v1db1)
607 6.654684000 172.16.100.10 172.16.100.241 TCP 74 ldap > 47210 [SYN, ACK] Seq=0 Ack=1 Win=8192 Len=0 MSS=1460 WS=256 SACK_PERM=1 TSval=64775753 TSecr=3548594
656 6.658694000 172.16.100.10 172.16.100.241 TCP 66 ldap > 47210 [ACK] Seq=191 Ack=82 Win=66560 Len=0 TSval=64775753 TSecr=3548597
Mate, I know that. Not what I am asking though. Where are you running Wireshark? In the Active Directory server? In a PC with spanning switchports? There are different ways to sniff packets, I would like to know where did you collect those captures from.
Could you please upload a sample sniffer trace to cloudshark.org?
Could you please upload a sample sniffer trace to cloudshark.org?
ASKER
Sorry! The Active Directory server I am running wireshark. Sure, will upload right now the sample sniffer.
ASKER
I am feeling a little "ifi" about this cloudshark upload....
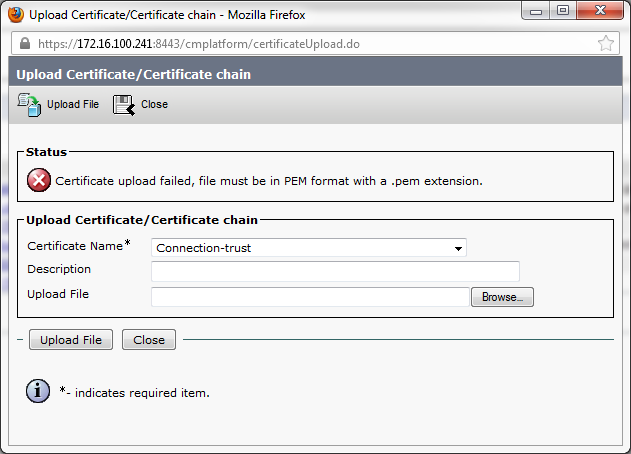
The file Connection-trust you tried to upload, does it have the .pem extension?
ASKER
No, is (.cer) I don't know how to create a certificate with extension. Will Google that now I guess.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you for your help!!!!