Help analyzing Wireshark data
I am having some network issues and it was suggested that I run Wireshark. It is running and flashing all over the place. Can someone help me analyze what it's doing? I'm quite lost.
you have to filter the wireshark data to look for the specific protocol your investigating
ASKER
I selected my ethernet port and clicked Start. Is that what you mean?
Laura Chappell has a free 4-part Wireshark 101 tutorial series on her site at
https://www.lcuportal2.com/index.php?option=com_content&view=category&layout=blog&id=49&Itemid=75
Download the FLV files or watch them online there.
Note they're in reverse order in the file listing... I renamed them when downloading so they appear in the correct order when listed alphabetically.
e.g.
https://www.lcuportal2.com/index.php?option=com_content&view=category&layout=blog&id=49&Itemid=75
Download the FLV files or watch them online there.
Note they're in reverse order in the file listing... I renamed them when downloading so they appear in the correct order when listed alphabetically.
e.g.

ASKER
I watched the videos and I still don't understand where to start. On youtube most of the vids are for hacking passwords, which I have no interest in. I wan't to find out why one computer in the office loses the connection to another computer in the office.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
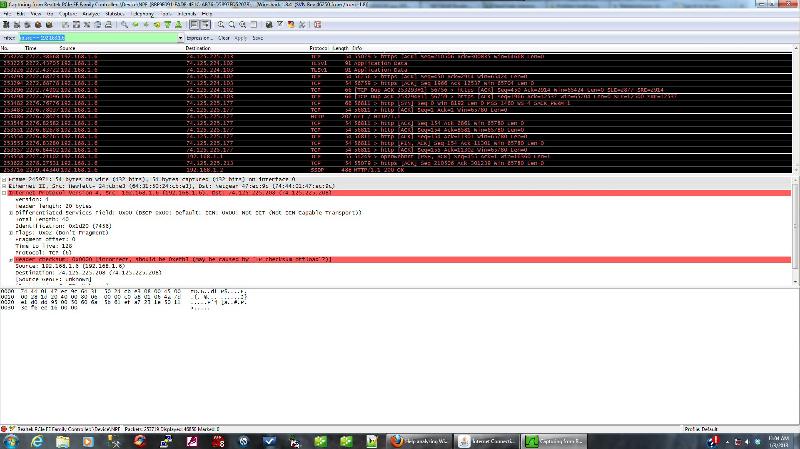
You know you only set the display filter, right? You are filtering what you see, not what is captured - which is ok if you wanted to do exactly that.
Don't care about that red stuff. You can see that the checksum is incorrect, which is quite common if the NIC drivers perform the calculation of checksums (called "offload").
If we subtract that, the capture does not show anything unusual.
Don't care about that red stuff. You can see that the checksum is incorrect, which is quite common if the NIC drivers perform the calculation of checksums (called "offload").
If we subtract that, the capture does not show anything unusual.
ASKER
Yes, the lady in the video said to do display filters so that you can look deeper if you wish and the data will be there.
ASKER
There is definitely something going on because every now and then, like 5 times a day, I'll go to google.com and it says server not found. So then I do a refresh and it's all good. What should I look for in the feed for something like that?
Good question. That could be
(a) DNS not resolving fast enough, so the DNS reply comes in after the browser gave up already
(b) A routing issue, so the HTTP request could not go out, or the reply not come back
(c) A timing issue, so the answer was received much too late
(d) IPv6 addresses might get preferred over IPv4, though you do not have any IPv6 route into the Internet. This will only apply if you have IPv6 bound to your NIC driver, which is the default with Vista and later.
I would start with a filter for DNS traffic (udp port 53) in addition to traffic to google.com (173.194.70.x/24). Note that DNS queries for google.com will return in 1 IPv6 and 6 IPv4 addresses usually.
(a) DNS not resolving fast enough, so the DNS reply comes in after the browser gave up already
(b) A routing issue, so the HTTP request could not go out, or the reply not come back
(c) A timing issue, so the answer was received much too late
(d) IPv6 addresses might get preferred over IPv4, though you do not have any IPv6 route into the Internet. This will only apply if you have IPv6 bound to your NIC driver, which is the default with Vista and later.
I would start with a filter for DNS traffic (udp port 53) in addition to traffic to google.com (173.194.70.x/24). Note that DNS queries for google.com will return in 1 IPv6 and 6 IPv4 addresses usually.
ASKER
So I was capturing everything and it failed for amazon.com. I immediately stopped the capture so I was hoping to see something at the end of the logs. I set up a display filter of ip.proto == 17 but I'm not sure that is correct.
Can you help me write a display filter that might help to find what just happened?
Can you help me write a display filter that might help to find what just happened?
First filter should be for DNS - to see if the address has been resolved. If it has, next filter is for the resolved IP address (from and to). Have a look into the display filter samples configured with WireShark for the syntax.