BBrayton
asked on
How to stop port scanning hackers
I have a server that had 28000 failed login attempts. when i clikt on the failed login attempt it shows a username and a ip address outside the network and a port. How can I stop this from happening.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
router linksys rvo42
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
we use port forwarding and only allow certain ports
what port?
In the RV042
Check to make sure you have the firewall enabled also check all settings are correct for your network
port forwarding just allows you to route traffic that does not block access
Check to make sure you have the firewall enabled also check all settings are correct for your network
port forwarding just allows you to route traffic that does not block access
ASKER
25, 80, 443, 1723, 3389, 987
25, 80, 443, 1723, 3389, 987
Are these the ports you are forwarding or the ports that the attacks are coming from?
ASKER
forwarding
is the firewall running on the RV042?
What ports are you seeing the attacks on?
ASKER
under firewall settings firewall is enabled, so is SPI, Denial of service, Wan reqests, and Multicast Passthrough, and HTTPS. remote management is disabled
ASKER
port 2700
ASKER
2689 too
it changes
it changes
ASKER
they are scanning for open ports
You need to setup an access rule in your rv042 to block port 2700
ASKER
but the port allways changes
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
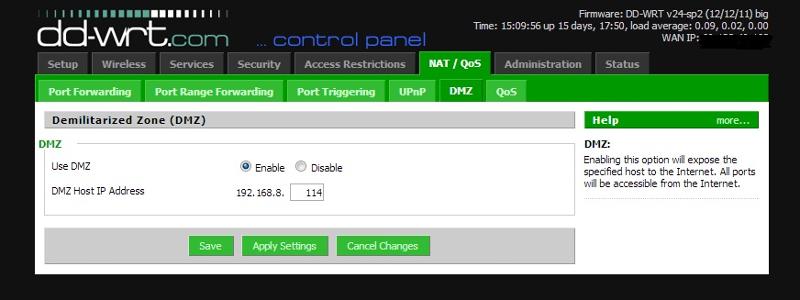
if DMZ is off on the router doesnt that mean that the ports that are forwarded and the only ports that pass through
DMZ is active for a specified IP address / host. All ports are forwarded on that IP address, but other hosts are only accessible via the specified forwarded ports.
ASKER
isn't DMZ for all inbound traffic.
For the specified hosts yea.. Enabling it wont open all ports on your whole network.
was you getting event id 529 in the security log?
You need to Restrict (on firewall) the allowed source ip to your one
You need to Restrict (on firewall) the allowed source ip to your one
ASKER
yes 529
What are your access rules in the rv042? Please post screen shot
ASKER
Lan allow all traffic
wan1 deny all traffic
wan2 deny all traffic
wan1 deny all traffic
wan2 deny all traffic
That looks good
back to head scratching mode
back to head scratching mode
What is the offending IP address?
ASKER
48.182.109.26
114.70.63.85
67.55.113.168
207.237.187.100
these are only a few the IP keeps changing as well
114.70.63.85
67.55.113.168
207.237.187.100
these are only a few the IP keeps changing as well
Try setting up this on the rv042
Define a DENY rule:
Source: Internal LAN
Destination: Internet
Protocol: DNS (UDP, TCP Prot:53)
This will stop outside attempts against DNS
Define a DENY rule:
Source: Internal LAN
Destination: Internet
Protocol: DNS (UDP, TCP Prot:53)
This will stop outside attempts against DNS
Send an email to the organizations.. Also keep an eye on your firewall / logs because these are all random organizations most likely a hacker has a backdoor on their servers or switches and may be targeting you from these remote addresses (based on the number of attempts).
By alerting the real owners hopefully they will take care of this on their end. I understand these are only a few of the IP's but its a start. Again, keep a close eye on your log..
net48admin@prudential.com
search-apnic-not-arin@apni
abuse@webair.com
For all abuse issues, please contact abuse@rcn.com
By alerting the real owners hopefully they will take care of this on their end. I understand these are only a few of the IP's but its a start. Again, keep a close eye on your log..
net48admin@prudential.com
search-apnic-not-arin@apni
abuse@webair.com
For all abuse issues, please contact abuse@rcn.com
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I've requested that this question be deleted for the following reason:
n
n
You had a lot of helpful information and you are deleting the question without follow up and your reason is "n".
Hardly seems far to those that invested their time.
Hardly seems far to those that invested their time.
Do you run a firewall on your server or on the router?
If router what type you have?