cameljoe121
asked on
Cisco ASA5505 How to Block IP from internet access not internal resources VIA ASDM 6.4
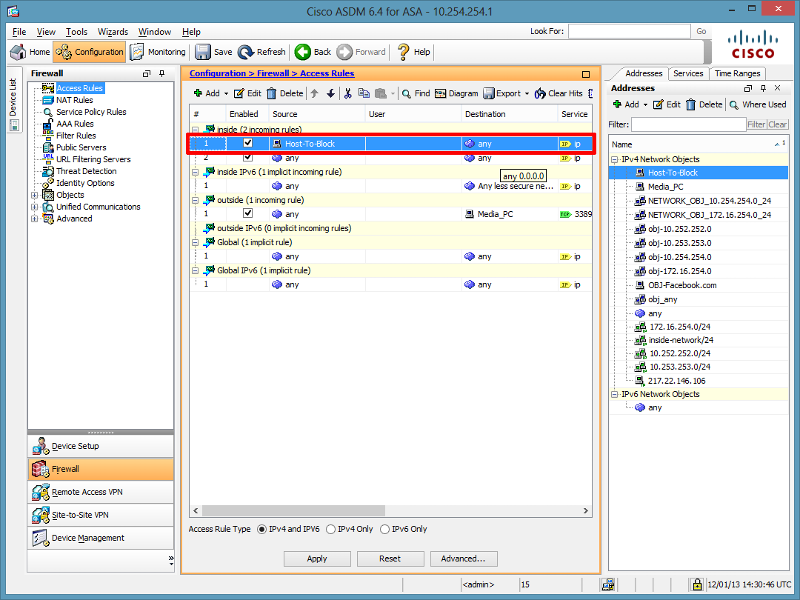
I have a ASA5505 I need to know how to block certain IP address from reaching the internet but, still allowing them to access internal resources file server print etc.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Here You go, I've written it up for you.
Cisco ASA 5500 - Deny a Single IP Address External Access
Pete
Cisco ASA 5500 - Deny a Single IP Address External Access
Pete
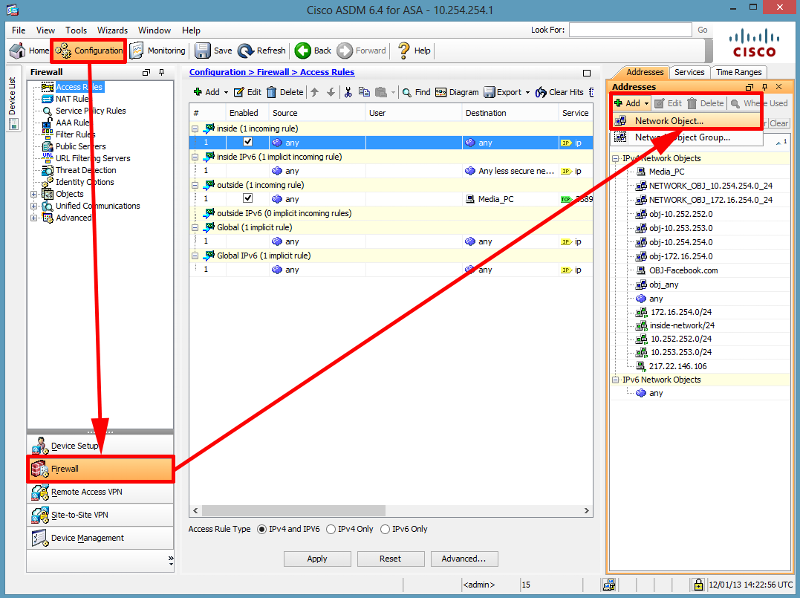
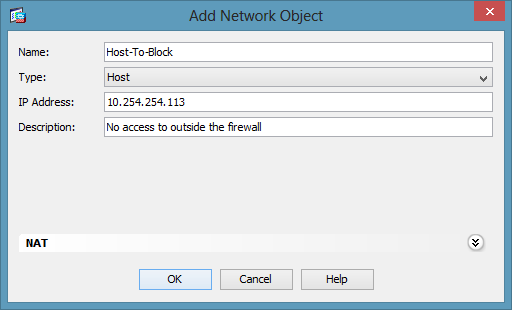
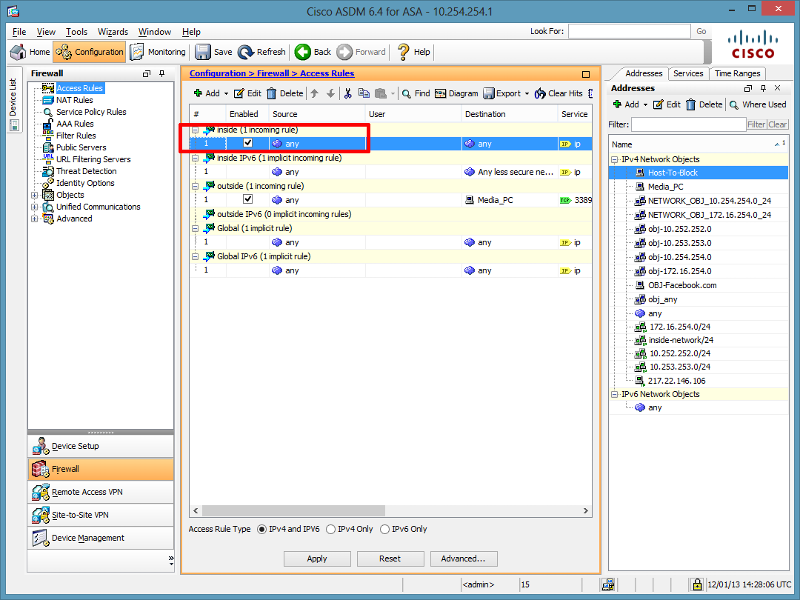
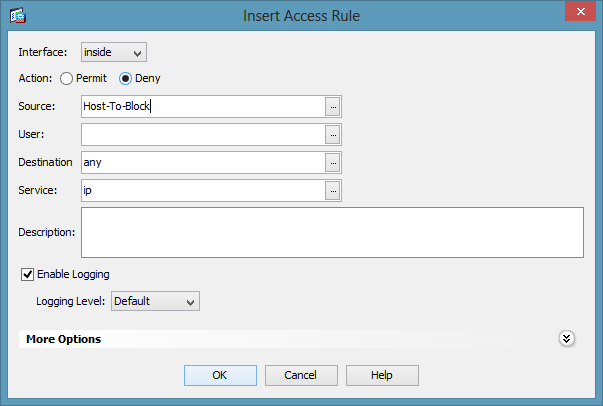
Open in new window
If you have multiple subnets on your internal network and the ASA is your default gateway you might need a couple permit lines in front of the deny line. Let's say 10.10.10.10 is on 255.255.0.0 subnet and you also have 10.20.0.0/16 and 10.30.0.0/16 networks they need to reach.
Open in new window