Marketing_Insists
asked on
cacls to icacls/powershell
I can restrict access to a file like so with cacls:
How can I duplicate this result with icacls or powershell?
echo Y|cacls "C:\Program Files\SomeProgram\SomeFile.exe" /p administrators:F
cacls "C:\Program Files\SomeProgram\SomeFile.exe" /e /g "corp\domain admins":F
cacls "C:\Program Files\SomeProgram\SomeFile.exe" /e /g "corp\dotnetdev":FHow can I duplicate this result with icacls or powershell?
For icacls, syntax is pretty much the same as cacls.
icacls folderORfile /grant:r Administrators:F
icacls folderORfile /grant "corp\Domain Admins":F
icacls folderORfile /grant "corp\dotnetdev":FASKER
@Sunburn
I almost have it, but I can't delete the permissions in the middle part of the script,
I almost have it, but I can't delete the permissions in the middle part of the script,
$file = "C:\Program Files\SomeProgram\SomeFile.exe"
# Below Deletes inheritance, hurray!
$acl = get-acl $file
$isProtected = $true
$preserveInheritance = $false
$acl.SetAccessRuleProtection($isProtected, $preserveInheritance)
Set-Acl -Path $file -AclObject $acl
#can't delete permissions, booo!
$acl = get-acl $file
$account = new-object system.security.principal.ntaccount("*")
$acl.purgeaccessrules($account)
set-acl -aclobject $acl -path $file
# below would be releveant if the above worked
$array = @("administrators","corp\domain admins","corp\dotnetdev")
foreach ($element in $array) {
$permission = $element,"FullControl","Allow"
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule $permission
$acl.SetAccessRule($accessRule)
$acl | Set-Acl $file
}ASKER
@footech
That grants permissions, but I can't figure out how to delete the remaining permissions. the /remove seems to require explicit user\group specifications, so the below wouldn't work either.
That grants permissions, but I can't figure out how to delete the remaining permissions. the /remove seems to require explicit user\group specifications, so the below wouldn't work either.
icacls "C:\Program Files\SomeProgram\SomeFile.exe" /remove:g
icacls "C:\Program Files\SomeProgram\SomeFile.exe" /remove:g *ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks! this did it
With PowerShell you can try something like this..
$file = "C:\Program Files\SomeProgram\SomeFile.exe"
$acl = get-acl $file
$acl.Access | % {
$acl.purgeaccessrules($_.IdentityReference)
Set-Acl -AclObject $acl -path $file -ErrorAction SilentlyContinue
}
$array = @("administrators","corp\domain admins","corp\dotnetdev")
foreach ($element in $array) {
$permission = $element,"FullControl","Allow"
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule $permission
$acl.SetAccessRule($accessRule)
$acl | Set-Acl $file
}
$isProtected = $true
$preserveInheritance = $false
$acl.SetAccessRuleProtection($isProtected, $preserveInheritance)
Set-Acl -Path $file -AclObject $acl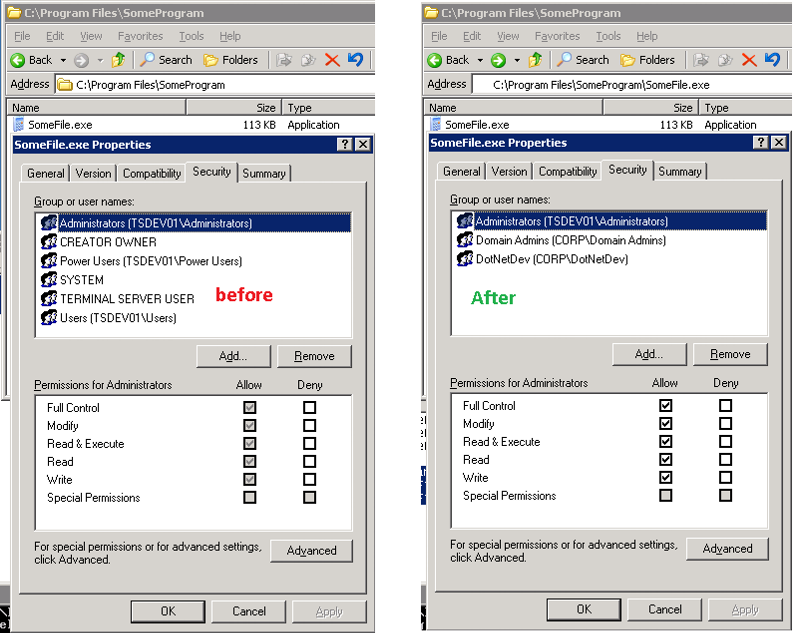
References :
http://chrisfederico.wordpress.com/2008/02/01/setting-acl-on-a-file-or-directory-in-powershell/
http://technet.microsoft.com/en-us/library/ff730951.aspx