omar07
asked on
Router and syslog server
Hello,
Please find attached diagram, I have Cisco router and ASA firewall, I need to send syslog messages from the router to the syslog server, which is directly attached to the firewall via switch. Now, I can ping from the syslog server to the router, but I can't ping from the router to the syslog server. How can I enable traffic to flow from the router to the syslog server.
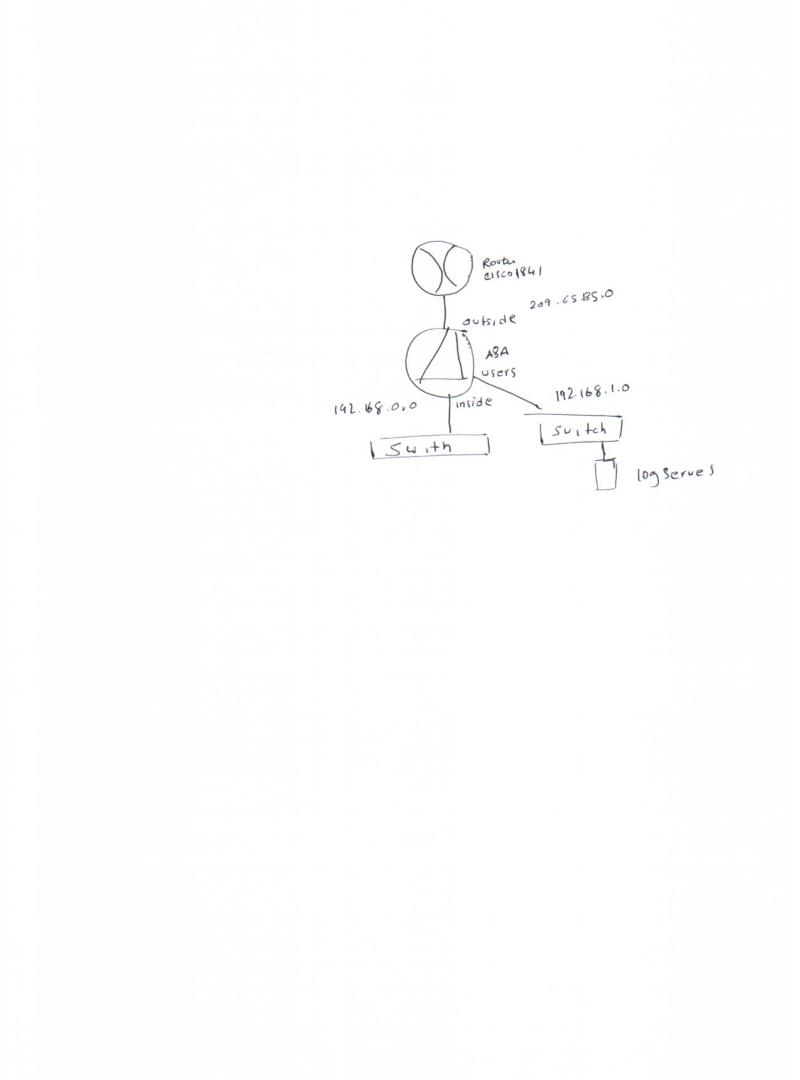
Please find attached diagram, I have Cisco router and ASA firewall, I need to send syslog messages from the router to the syslog server, which is directly attached to the firewall via switch. Now, I can ping from the syslog server to the router, but I can't ping from the router to the syslog server. How can I enable traffic to flow from the router to the syslog server.

Post you config pls
ASKER
I tried this config;
access-list syslog-messages extended permit ip host 209.165.135.1 any (router attached to outside int)
access-group syslog-messages in int outside
static (users,outside) 192.168.1.0 192.168.1.0 netmask 255.255.255.0
and it still not working.
access-list syslog-messages extended permit ip host 209.165.135.1 any (router attached to outside int)
access-group syslog-messages in int outside
static (users,outside) 192.168.1.0 192.168.1.0 netmask 255.255.255.0
and it still not working.
You need to create a static NAT for your log server with a dedicated Outside IP address
static (users,outside) 192.168.1.0 192.168.1.0 netmask 255.255.255.0 - this is not correct
static (users,outside) outside_ip_address log_server_ip netmask 255.255.255.255 - this is how it should be
static (users,outside) 192.168.1.0 192.168.1.0 netmask 255.255.255.0 - this is not correct
static (users,outside) outside_ip_address log_server_ip netmask 255.255.255.255 - this is how it should be
ASKER
I tried the following config in the ASA.
access-list syslog-messages extended permit ip host 209.165.135.1 any (the ip of the router)
access-group syslog-messages in int outside
static (users,outside) 290.165.135.1 192.168.220.1 netmask 255.255.255.255
still not working, I can't even ping from the router to the syslog sever
access-list syslog-messages extended permit ip host 209.165.135.1 any (the ip of the router)
access-group syslog-messages in int outside
static (users,outside) 290.165.135.1 192.168.220.1 netmask 255.255.255.255
still not working, I can't even ping from the router to the syslog sever
For this to work you need:
1. An inbound NAT / PAT rule from interface outside to users. For example:
static (users,outside) udp 1.2.3.1 514 192.168.220.1 514 netmask 255.255.255.255
Or:
static (users,outside) 1.2.3.1 192.168.220.1 netmask 255.255.255.255
Where 1.2.3.1 is an IP you can present on your firewall (or the interface IP). Alternatively, you can present this on the interface IP as follows:
static (users,outside) udp interface 514 192.168.220.1 514 netmask 255.255.255.255
2. An access rule applying to inbound traffic on the outside interface:
access-list acl_outside_in permit udp host 2.3.4.2 host 1.2.3.1 eq 514
access-group acl_outside_in in interface outside
Where 2.3.4.2 is the router IP and 1.2.3.1 is the address you're using in the NAT rule to present syslog on the outside interface. Obviously you can make the ACL name whatever you please.
Logging should show you hits on the rule if it's actually getting that far.
Chris
1. An inbound NAT / PAT rule from interface outside to users. For example:
static (users,outside) udp 1.2.3.1 514 192.168.220.1 514 netmask 255.255.255.255
Or:
static (users,outside) 1.2.3.1 192.168.220.1 netmask 255.255.255.255
Where 1.2.3.1 is an IP you can present on your firewall (or the interface IP). Alternatively, you can present this on the interface IP as follows:
static (users,outside) udp interface 514 192.168.220.1 514 netmask 255.255.255.255
2. An access rule applying to inbound traffic on the outside interface:
access-list acl_outside_in permit udp host 2.3.4.2 host 1.2.3.1 eq 514
access-group acl_outside_in in interface outside
Where 2.3.4.2 is the router IP and 1.2.3.1 is the address you're using in the NAT rule to present syslog on the outside interface. Obviously you can make the ACL name whatever you please.
Logging should show you hits on the rule if it's actually getting that far.
Chris
ASKER
Hello,
I tried the following:
static (users,outside) interface syslog_server netmask 255.255.255.255
access-list acl_outside_in extended permit ip host router_ip host syslog_server
access-list acl_outside_in extended permit ip any any
access-group acl_outside_in in interface outside
I still can't ping from the router to the syslog server.
I'd like to note, that I'm configuring global outside and insdie nat for internet connection.
Thanks
I tried the following:
static (users,outside) interface syslog_server netmask 255.255.255.255
access-list acl_outside_in extended permit ip host router_ip host syslog_server
access-list acl_outside_in extended permit ip any any
access-group acl_outside_in in interface outside
I still can't ping from the router to the syslog server.
I'd like to note, that I'm configuring global outside and insdie nat for internet connection.
Thanks
This rule won't work if "syslog_server" is the private IP:
access-list acl_outside_in extended permit ip host router_ip host syslog_server
Cisco firewalls process access lists first, then perform NAT.
However, this one should be catching:
access-list acl_outside_in extended permit ip any any
So, are you getting any hits on that rule (show access-list acl_outside_in)? Have you got any log entries to do with the inbound traffic (show log)?
I forget if it applies, but we may as well consider it. What security levels have you applied to each of the interfaces this is to traverse?
Chris
access-list acl_outside_in extended permit ip host router_ip host syslog_server
Cisco firewalls process access lists first, then perform NAT.
However, this one should be catching:
access-list acl_outside_in extended permit ip any any
So, are you getting any hits on that rule (show access-list acl_outside_in)? Have you got any log entries to do with the inbound traffic (show log)?
I forget if it applies, but we may as well consider it. What security levels have you applied to each of the interfaces this is to traverse?
Chris
ASKER
Hello,
The syslog server is private ip address, and the outside interface of the firewall is 0 and the users is 90. I configured the following in the firewall:
static (users,outside) interface syslog-server netmask 255.255.255.255
access-list acl_outside_in extended permit ip any any
access-group acl_outside_in in interface outside
and I did not get any hit count on the access-list rule, when I ping to the syslog-server, however I can ping the outside interface of the firewall.
The syslog server is private ip address, and the outside interface of the firewall is 0 and the users is 90. I configured the following in the firewall:
static (users,outside) interface syslog-server netmask 255.255.255.255
access-list acl_outside_in extended permit ip any any
access-group acl_outside_in in interface outside
and I did not get any hit count on the access-list rule, when I ping to the syslog-server, however I can ping the outside interface of the firewall.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hello,
Now, I'm able to get hits on the access list rule, but first I had to add route in the router to the log server, something like ip route syslog-server firewall-interface 1, after that I started to get hit counts on the access-list :access-list acl_outside_in extended permit udp host router-ip host syslog-server eq syslog log
Now, I'm able to get hits on the access list rule, but first I had to add route in the router to the log server, something like ip route syslog-server firewall-interface 1, after that I started to get hit counts on the access-list :access-list acl_outside_in extended permit udp host router-ip host syslog-server eq syslog log
Excellent, that is good news. It looks like you're not using the NAT rule in that case, but that's fine. You might consider killing the inbound NAT rule if you're routing in like that.
Chris
Chris
ASKER
I'm still getting this error, or shall I post new question since I alreay closed this case.
Feb 03 2013 14:10:43: %ASA-5-305013: Asymmetric NAT rules matched for forward an
d reverse flows; Connection for udp src outside:router-ip/64661 dst users:log-server/514
denied due to NAT reverse path failure
Feb 03 2013 14:10:43: %ASA-5-305013: Asymmetric NAT rules matched for forward an
d reverse flows; Connection for udp src outside:router-ip/64661 dst users:log-server/514
denied due to NAT reverse path failure
If you've set up routing from the router to 192.168.1.220 you can kill off the inbound NAT rule as you're not using it. That should get rid of the error message above as well.
Chris
Chris
Another option is to create a sub interface on the router, another interface on the firewall, and use that to pass traffic. The first options are usually easier.