VPN device Behind Router/Firewall
I have a vendor who is dropping a VPN device in our facility for a site to site VPN that is needed to interface with a software we have on site with a software they host for us. I attached a network diagram so you can see what my network looks like. I do have a public IP Address to give them for the outside interface of their VPN device, but I"m not sure where to plug the outside interface of the VPN Device in at. The VPN device is located in the lower left corner of the diagram and must be in the location shown on the diagram as it's behind a locked door and this is a requirement. Will it work, if I just plug the outside and inside interface of the VPN device into the switch as shown. I concerned I'll have issues since it sits behind my router and ASA.
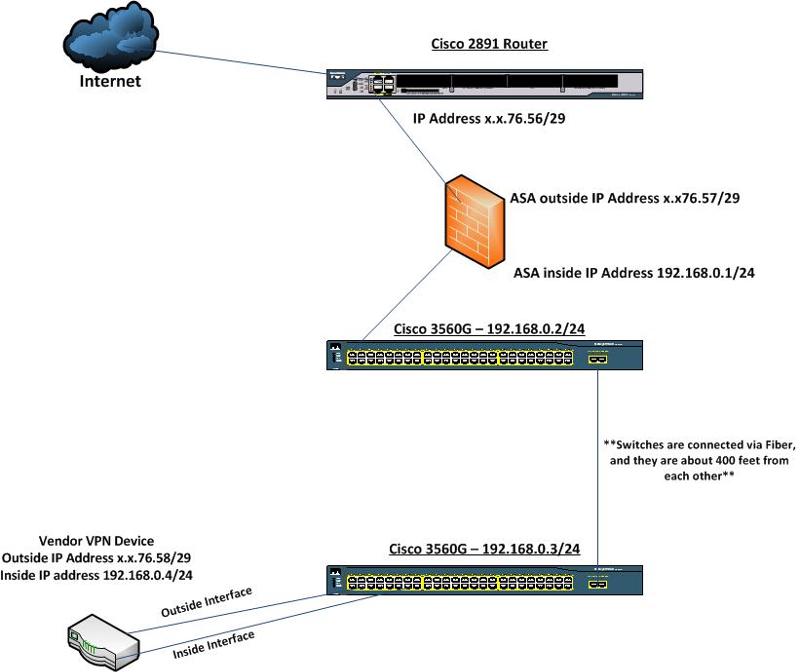

You may need to create a DMZ on your firewall and then use a Vlan to route the external interface through to your VPN device? Can you patch the external interface through to the firewall and set it as above and then port forward the public IP address?
As Integrity has mentioned it would be best to create a DMZ interface which hangs off the ASA. But you can also do this by creating a new VLAN just for this VPN traffic and connect the VPN device to this VLAN.
The problem with this is that the ASA would need an IP in the same subnet as the outside interface of the VPN device to act as a default gateway, so this might stop up here if you dont have enough IPs in that range.
The way I would suggest doing it is to allocate a new private IP to the device outside interface, lets say 172.16.1.2 for example. Create a new VLAN and allow this VLAN over the trunks toward the ASA. Create a new subinterface on the ASA and place it in the newly created VLAN and give it an IP of 172.16.1.1. The internal inside interface can remain as is.
Now make sure that your ISP is routing the x.x.76.58/29 network toward the outside interface of your ASA. Create a NAT statement that translates the public IP to 172.16.1.2.
That should get connection to the outside. Next you will need to make sure that the traffic that is to encrypted is correctly configured on the VPN device, but that would be a different discussion.
The problem with this is that the ASA would need an IP in the same subnet as the outside interface of the VPN device to act as a default gateway, so this might stop up here if you dont have enough IPs in that range.
The way I would suggest doing it is to allocate a new private IP to the device outside interface, lets say 172.16.1.2 for example. Create a new VLAN and allow this VLAN over the trunks toward the ASA. Create a new subinterface on the ASA and place it in the newly created VLAN and give it an IP of 172.16.1.1. The internal inside interface can remain as is.
Now make sure that your ISP is routing the x.x.76.58/29 network toward the outside interface of your ASA. Create a NAT statement that translates the public IP to 172.16.1.2.
That should get connection to the outside. Next you will need to make sure that the traffic that is to encrypted is correctly configured on the VPN device, but that would be a different discussion.
ASKER
My ASA's outside interface is in the same public ip block as the vendors outside interface on their VPN device. MAG03, let me make sure I understand your first option. Your saying I could create another VLAN on both switches and assign the VLAN an IP Address in the same range as the outside interface of my ASA and the vendors VPN device outside interface. I do have two extra IP addresses in this IP block so that is an option if I am understanding you correctly. I will be adding a couple new switches in the next couple months, but they shouldn't require a VLAN in this IP range right. There won't be anything with a public address plugged into them. Only the two switches shown above will. This should work right?
In this case you can not use the first example of setting another external IP on the ASA which is in the same subnet as the outside interface.
The only option in this case is to NAT the external IP to an internal IP on the VPN device, as i mentioned in the second example.
The only time a switch needs a VLAN configured on it is if traffic in that VLAN needs to traverse that switch (sort of transit through the switch) or there are devices on that switch that need to communicate with other devices in that VLAN. Otherwise they do not require the VLAN to be configured on them.
The only option in this case is to NAT the external IP to an internal IP on the VPN device, as i mentioned in the second example.
The only time a switch needs a VLAN configured on it is if traffic in that VLAN needs to traverse that switch (sort of transit through the switch) or there are devices on that switch that need to communicate with other devices in that VLAN. Otherwise they do not require the VLAN to be configured on them.
ASKER
lets say i create a public VLAN on the two switches using my public IP range. Could I then connect the interface on the router that goes to the ASA into that VLAN in the first switch. i would connect the outside interface of the ASA into that VLAN as well. Then finally I will connect the outside interface of the vendors VPN device into this VLAN on the second switch. This way all devices that have a public IP address are connected to the "public" VLAN. I think this would work. I would normally NAT the internal to a public IP like you mentioned, but the vendor already Put the IP Address on their outside interface.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks.