Winfix1
asked on
Juniper Netscreen SSG20 VPN Config
Hi
I have a working VPN config between a remote Checkpoint site (that I dont manage) and our Juniper Netscreen.
VPN is policy based with traffic at the remote site only being allowed to initiate a connection for an application they run to a server at our end. All works fine.
I now need to allow a print server queue located at my site to send print jobs to a printer at the remote site. The application that is run creates a print request to the database at my end sends the print to to the print queue. I am told by the admin at the remote site that I need to add the printer IP to my encryption domain and give it the relevant access ie port 9100 outgoing through the tunnel.
How do I add the printer IP to my encryption domain?
Once added do I add a trust to untrust policy for the port number?
Thanks
I have a working VPN config between a remote Checkpoint site (that I dont manage) and our Juniper Netscreen.
VPN is policy based with traffic at the remote site only being allowed to initiate a connection for an application they run to a server at our end. All works fine.
I now need to allow a print server queue located at my site to send print jobs to a printer at the remote site. The application that is run creates a print request to the database at my end sends the print to to the print queue. I am told by the admin at the remote site that I need to add the printer IP to my encryption domain and give it the relevant access ie port 9100 outgoing through the tunnel.
How do I add the printer IP to my encryption domain?
Once added do I add a trust to untrust policy for the port number?
Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
if you edit the incoming policy for the VPN. there is a check mark at the bottom for "Modify matching bidirectional VPN policy " Enabling this will create the matching policy VPN for traffic going the opposite way.
ASKER
Thanks OK. But what do I need to modify so that my server sends/routes traffic for the printer ip 10.132.145.10 down the vpn tunnel? Currently it tries to just send out to the internet.
The destination IP of the matching VPN policy should be 10.132.145.0/24, this will make sure all traffic destined for that subnet goes via the VPN and not out to the internet.
ASKER
Hi
Thanks. Ticking "Modify matching bidirectional VPN policy", does not stick. It reverts back to unticked?
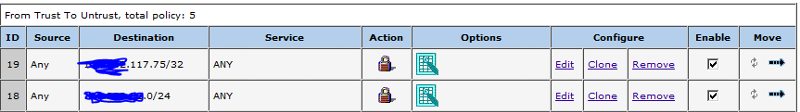
Here is the policy

The source address is 80.x.x.x through a MIP. But traffic I generate needs to go down the tunnel to 10.132.145.10, this is where the printer will try to send to.
How would I set 10.132.145.10 to go down the tunnel?
Thanks
Thanks. Ticking "Modify matching bidirectional VPN policy", does not stick. It reverts back to unticked?
Here is the policy

The source address is 80.x.x.x through a MIP. But traffic I generate needs to go down the tunnel to 10.132.145.10, this is where the printer will try to send to.
How would I set 10.132.145.10 to go down the tunnel?
Thanks
I see your problem, this is not a VPN. It is actually a mapped IP. Basically your internal server is reachable from the internet via the public IP MIP(81.*.*.229)
In this configuration you will not be able to actually print to the printer in the other network.
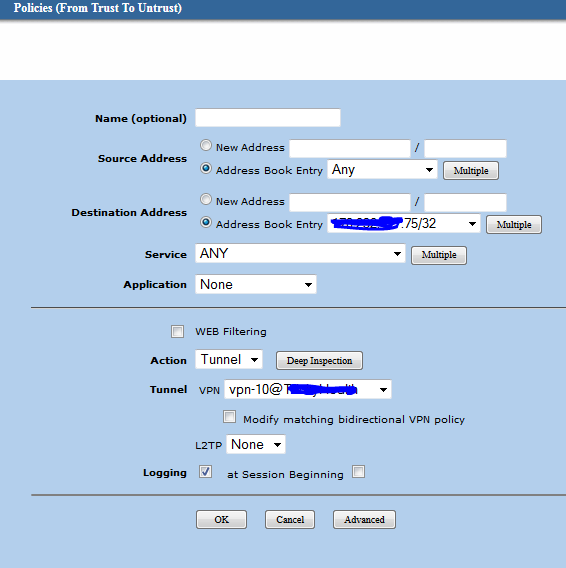
In a policy based VPN, This is what you would have:
The source IP would be your LAN.
The destination IP would be the remote LAN.
The action would be = tunnel.
The tunnel VPN = The autokey IKE setup under the VPN menu.
And lastly you could then check the box for matching bidirectional vpn.
Below is a screen shot of a policy based VPN. Mine is one way only so the bidirection is unchecked
In this configuration you will not be able to actually print to the printer in the other network.
In a policy based VPN, This is what you would have:
The source IP would be your LAN.
The destination IP would be the remote LAN.
The action would be = tunnel.
The tunnel VPN = The autokey IKE setup under the VPN menu.
And lastly you could then check the box for matching bidirectional vpn.
Below is a screen shot of a policy based VPN. Mine is one way only so the bidirection is unchecked
ASKER
Thanks
ASKER
OK at present I just have an Incoming policy for the VPN. There is no outgoing policy as outgoing traffic to the VPN was not required before.
How do I create an relevant outgoing policy to point the traffic to the VPN for the remote printer IP traffic?