Deploying Printers Through Group Policy
Hello,
we are going to deploy printers through GPOs but i have a questions regarding the deployment .
Please check the Screen Shot
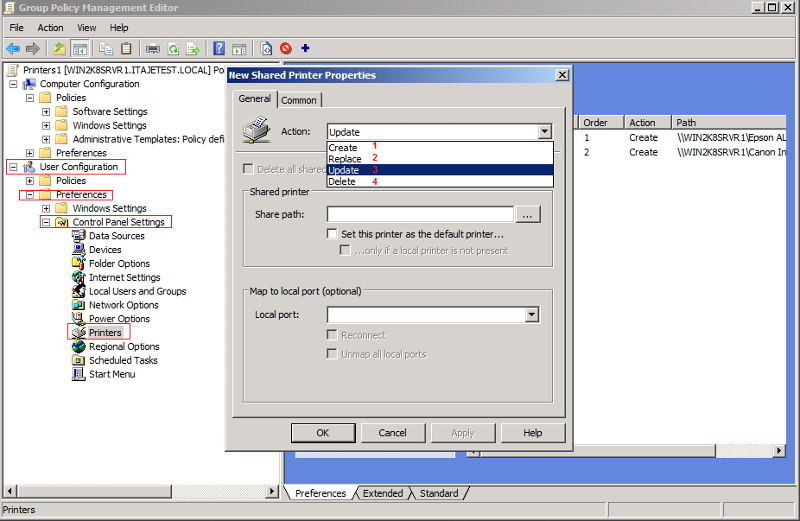
What the Difference between
1- Create
2- Replace
3- Update
In our deployment we are going to use Update but if the user change the Default Printers after log off and log in or restart does it will come back again as group policy or no ?
Regards
we are going to deploy printers through GPOs but i have a questions regarding the deployment .
Please check the Screen Shot

What the Difference between
1- Create
2- Replace
3- Update
In our deployment we are going to use Update but if the user change the Default Printers after log off and log in or restart does it will come back again as group policy or no ?
Regards
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Otherwise use Print Managment Console to deploy the printers. The difference being that with Print Management Console you will need to deploy PushPrinterconnections.exe