Symantec is detecting W32.Slugin.A!inf virus in SBS 2011
I am getting the virus alert after every few days.... the server SBS 2011 is new & all the updates & service packs are current & updated.
Having Symantec Endpoint protection 11.x
Please find the log files & screenshots.
Please guide me on how to get rid of the infection.
virus.csv
symantec.JPG
symantec2.JPG
Having Symantec Endpoint protection 11.x
Please find the log files & screenshots.
Please guide me on how to get rid of the infection.
virus.csv
symantec.JPG
symantec2.JPG
ASKER
Thanks for your support.
I did what you have guided.
Please find the screenshot. I haven't applied the fix yet, as I guess its a false alarm by the NPE.
Need your suggestion.
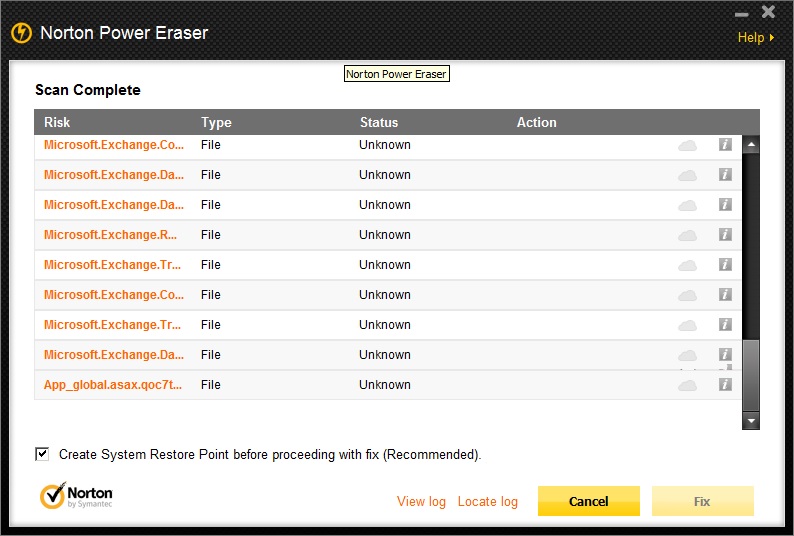 Info20130630190309.xml
Info20130630190309.xml
I did what you have guided.
Please find the screenshot. I haven't applied the fix yet, as I guess its a false alarm by the NPE.
Need your suggestion.
 Info20130630190309.xml
Info20130630190309.xml
ASKER
I have deleted the user profile & created fresh one, but again got more than 250 notifications of this virus.
Also tried Dr. Web antivirus tool to remove infection.
Also tried Dr. Web antivirus tool to remove infection.
ASKER
I have created another user with Network Administrator role, still getting virus detection. Have already full scanned using Symantec endpoint protection 10.x & Dr. web tool.
Still getting alerts ... all the files are detected in temp directory with file name as DWH****.tmp
Still getting alerts ... all the files are detected in temp directory with file name as DWH****.tmp
Probably good to verify existence of the symptoms of files created by this malware to see if removal does really helps...
http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=Virus%3aWin32%2fSlugin.A!dll
http://www.microsoft.com/security/portal/threat/encyclopedia/entry.aspx?Name=Virus%3aWin32%2fSlugin.A!dll
I would use Kaspersky Rescue Disk.
ASKER
Kaspersky Rescue requirements lis do not have server OS as supported OS.
Can I install it on SBS 2011 safely?
Can I install it on SBS 2011 safely?
You don't need to install it. Download the ISO, create your bootable ISO with it and boot the server from the CD.
Sorry, there's a typo.
Create your bootable CD (not ISO).
Create your bootable CD (not ISO).
ASKER
@takecoffee I tried AVG tool too.
@strivoli First I would take full block level back before I would consider running the tool from bootable CD. Secondly that task requires shutting down my server. :(
@strivoli First I would take full block level back before I would consider running the tool from bootable CD. Secondly that task requires shutting down my server. :(
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
A complete fresh backup of the server? Sure!
Shutting down the server? Yes. But it might be (sometimes) the only way to get a virus-free server.
Shutting down the server? Yes. But it might be (sometimes) the only way to get a virus-free server.
I must agree with clean slate of health since it is critical server backend. Eventually you may not be able to have clean it with its remanence and doing already spread across the server repository and I do suggest a wide spread scanning to all server and file share this infected server is connected and try to contain the spread.
there is mentioned of manual removal but it is not effective as what if you come back and this is totally different variant since the last one is old named as shared by experts. go for clean slate
there is mentioned of manual removal but it is not effective as what if you come back and this is totally different variant since the last one is old named as shared by experts. go for clean slate
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Some even has AV running as vm appliance while server instance running under the blade hypervisor... wondering if there is any reporting of this infection and scan all portable storage used in this server as well to find more cahoots
ASKER
I have noticed one strange thing.... I never get any virus notification if I keep my self logout on the server but get notifications/detections whenever I keep my self login to the server locally (locked position)
I am managing the server remotely through logmein ... that is the reason I couldn't try fixing using boot media.
I am managing the server remotely through logmein ... that is the reason I couldn't try fixing using boot media.
There are malware that evade Remote desktop and one example is shylock
http://www.darkreading.com/endpoint/financial-malware-detects-remote-desktop/240142738?nomobile=1
http://www.darkreading.com/endpoint/financial-malware-detects-remote-desktop/240142738?nomobile=1
ASKER
How to get rid & protect from them.
I suggest clean install if viable as If it infected mbr you need to preboot into external cd to do clean up and I am not in full trust to the system though..
ASKER
installing & configuring all the services & all the connected clients is a nightmare.
Don't want to go with it.
Don't want to go with it.
Did you try RogueKiller?
ASKER
The server is facing another issue... backup is not running .... have to fix it first before I could do any virus fixes.
I've requested that this question be deleted for the following reason:
Not enough information to confirm an answer.
Not enough information to confirm an answer.
ASKER
I am managing the server remotely. As the step requires my physical visit to the server location... I would do it at my next visit. I would update the thread thereafter. Please do not delete this thread.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Try the Microsoft Safety Scanner to remove Babonock: http://www.microsoft.com/security/portal/threat/encyclopedia/Entry.aspx?Name=TrojanSpy%3AWin32%2FBabonock.A#tab=1
ASKER
ASKER
As it was an infection at server level, I was very apprehensive on running a new tool on the server.
I got same infection on a desktop recently, I did all the testing on that.
Found roguekiller as best. Virustotal.com gave me confirmation & details about the infection.
I guess mallwarebytes.org is loosing its charm. I used to use it most of the time but from some time its failing to detect repeatedly.
I got same infection on a desktop recently, I did all the testing on that.
Found roguekiller as best. Virustotal.com gave me confirmation & details about the infection.
I guess mallwarebytes.org is loosing its charm. I used to use it most of the time but from some time its failing to detect repeatedly.
ASKER
Sorry to say, the virus is still there. :(
The issue seemed resolved but it did not.
The issue seemed resolved but it did not.
ASKER
These dialog boxes i am getting repeatedly.
Scan type: Auto-Protect Scan
Event: Risk Found!
Security risk detected: W32.Slugin.A!inf
File: C:\Users\itmanager\AppData
Location: C:\Users\itmanager\AppData
Computer: IBMDC
User: itmanager
Action taken: Pending Side Effects Analysis : Access denied
Date found: 23 October 2013 13:31:22
Scan type: Auto-Protect Scan
Event: Risk Found!
Security risk detected: W32.Slugin.A!inf
File: C:\Users\itmanager\AppData
Location: C:\Users\itmanager\AppData
Computer: IBMDC
User: itmanager
Action taken: Pending Side Effects Analysis : Access denied
Date found: 23 October 2013 13:31:22
Try the newer versions of both RogueKiller and the safety scanner.
ASKER
http://home.mcafee.com/virusinfo/virusprofile.aspx?key=1556281#none
As per above link; do you think MBR is infected?
Detection as per kaspersky: Trojan.Win32.Rozena.hod
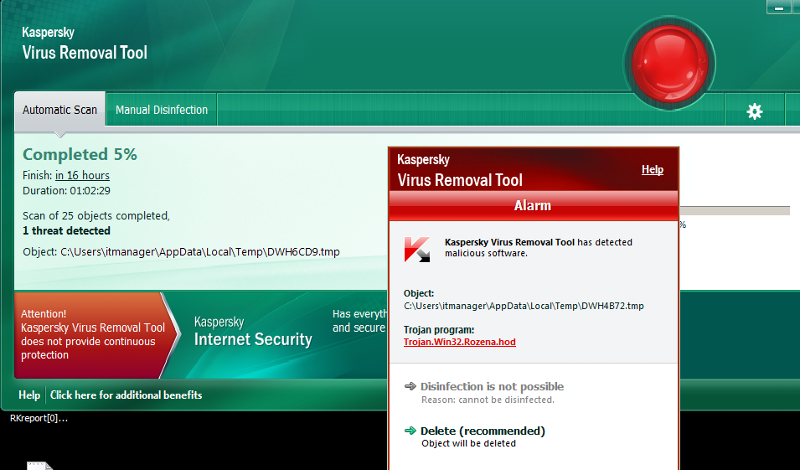
As per above link; do you think MBR is infected?
Detection as per kaspersky: Trojan.Win32.Rozena.hod

That detection is for a PE Trojan which means there are EXE and/or DLL files which are infected.
Your best course would be to run MS Windows Defender Offline ( http://windows.microsoft.com/en-US/windows/what-is-windows-defender-offline ) or AVG's Rescue CD ( http://www.avg.com/us-en/avg-rescue-cd ); but, both will want you to burn a CD which you must boot to in order to run the scans.
Pay CLOSE attention to what files are detected as you may need to restore them from another source to finally fix th eproblem.
Your best course would be to run MS Windows Defender Offline ( http://windows.microsoft.com/en-US/windows/what-is-windows-defender-offline ) or AVG's Rescue CD ( http://www.avg.com/us-en/avg-rescue-cd ); but, both will want you to burn a CD which you must boot to in order to run the scans.
Pay CLOSE attention to what files are detected as you may need to restore them from another source to finally fix th eproblem.
http://security.symantec.com/nbrt/npe.aspx?lcid=1033
http://www.symantec.com/security_response/writeup.jsp?docid=2008-102513-4113-99&tabid=3