lebz29
asked on
AddTrust External CA Root warning
I recently deployed a wireless solution and want to to use 802.1x. Everything is working between the wifi controller and the RADIUS server. When my Window 7 clients connects to the wifi I am prompted with a warning.
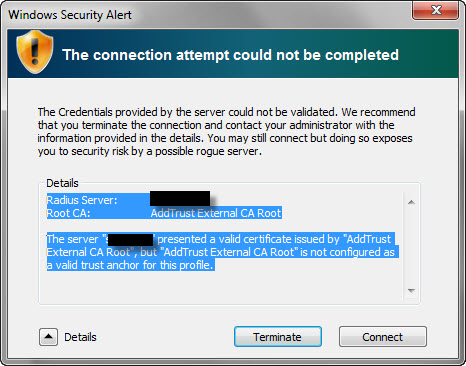
The credentials provided by the server could not be validated. We recommend you terminate...
Radius Server: xxx
Root CA: AddTrust External CA Root
The server "xxx" presented a valid certificate issued by "AddTrust External CA Root", but "AddTrust External CA Root" is not configured as a valid trust anchor for this profile.
If I select connect everything works fine and I can authenticate and connect to the corporate WIFI. Please see attached as well.
Thank you
The credentials provided by the server could not be validated. We recommend you terminate...
Radius Server: xxx
Root CA: AddTrust External CA Root
The server "xxx" presented a valid certificate issued by "AddTrust External CA Root", but "AddTrust External CA Root" is not configured as a valid trust anchor for this profile.
If I select connect everything works fine and I can authenticate and connect to the corporate WIFI. Please see attached as well.

Thank you
The cert issuer appears to not be trusted by your computer:
See below
http://support.microsoft.com/kb/2518158
You need to add that cert to your local store:
Export the certificate of the CA that issued the certificate to the authentication server to a file "AddTrust External CA Root.cer".
Copy the file to the workgroup machine and then run the following command from an elevated Command Prompt:
certutil -enterprise -addstore NTAuth "AddTrust External CA Root.cer"
See below
http://support.microsoft.com/kb/2518158
You need to add that cert to your local store:
Export the certificate of the CA that issued the certificate to the authentication server to a file "AddTrust External CA Root.cer".
Copy the file to the workgroup machine and then run the following command from an elevated Command Prompt:
certutil -enterprise -addstore NTAuth "AddTrust External CA Root.cer"
ASKER
The cert was issue by Comdo for a internal server.
They sent 3 files
1) servername.crt
2) COMODOHigh-AssuranceSecure
3) AddTrustExternalCARoot.crt
For the authentication I am using EAP (PEAP)
They sent 3 files
1) servername.crt
2) COMODOHigh-AssuranceSecure
3) AddTrustExternalCARoot.crt
For the authentication I am using EAP (PEAP)
certutil -enterprise -addstore NTAuth AddTrustExternalCARoot.crt
if you continue to have issues you may also have to add the COMODOxx cert to your intermediate cert store.
certutil -addstore -f CA pathto:\COMODOHigh-Assuran
certutil -addstore -f ROOT AddTrustExternalCARoot.crt
if you continue to have issues you may also have to add the COMODOxx cert to your intermediate cert store.
certutil -addstore -f CA pathto:\COMODOHigh-Assuran
certutil -addstore -f ROOT AddTrustExternalCARoot.crt
ASKER
Thank you. I tried the above on my local computer and I am still getting the popup. Maybe Comodo was a bad choice for a SSL cert?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Bingo! Ran the following on my DC
certutil -dspublish -f COMODOHigh-AssuranceSecure
Thank you all
certutil -dspublish -f COMODOHigh-AssuranceSecure
Thank you all
Open the wireless network. Or, click the "Add" button to create a new network, then open it.
The Wireless Network Properties window appears. Click the Security tab.
Under "Choose a network authentication method", select "Microsoft: Smart Card or other certificate". I assume this is already selected.
Click the "Settings" button.
The "Smart Card or other Certificate Properties" window appears.
Here is the answer. Under the "Trusted Root Certification Authorities" list, you have to manually select the Root CA of your company. By default, these are all blank. That is why the warning message appears the first time if you do not select your company's Root CA. If you connect despite the warning, then your company's Root CA is now selected, and you no longer get the warning on subsequent connections. So, to avoid the warning, just select this box when you set up the network, before you connect for the first time.
If you do not see your company's Root CA here, that is likely due to the fact that by default, double clicking your certificate to install it probably puts it under the "Intermediate Certification Authorities" tab. You need to select the "Trusted Root Certification Authorities" tab instead. You can see where certificates go under: Internet Explorer > Internet Options > Content > Certificates