Cisco SG500 Intervlan routing ACL
Hi,
I have a stack of SG500 switches that are in layer 3 mode.
There are 3 VLANS
100 = Data 192.168.1.0
200 = Phone 192.168.200.0
500 = Management 192.168.220.0
Each VLAN has an ip address and clients have their gateways set as the switches interface address. Intervlan is working and clients can ping across VLANS and access the internet.
I now want to apply some restrictions. For example I want to be able to apply rules such as:-
1) Any client on 100 or 200 can not access each other or Management
2) Management can access anything on ANY VLAN.
3) Clients on 100 can access host 192.168.200.100 on vlan 200 on port 443 only.
I have tried setting up an example ACL and ACE such as per attached screenshot and apply the ACL to all ports on the switch:-
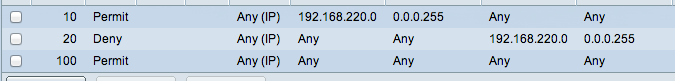
When I do this the management can't ping anything. It seems that the 'deny' is blocking the replies etc.
Is this possible, if you how? Thanks in advance.
I have a stack of SG500 switches that are in layer 3 mode.
There are 3 VLANS
100 = Data 192.168.1.0
200 = Phone 192.168.200.0
500 = Management 192.168.220.0
Each VLAN has an ip address and clients have their gateways set as the switches interface address. Intervlan is working and clients can ping across VLANS and access the internet.
I now want to apply some restrictions. For example I want to be able to apply rules such as:-
1) Any client on 100 or 200 can not access each other or Management
2) Management can access anything on ANY VLAN.
3) Clients on 100 can access host 192.168.200.100 on vlan 200 on port 443 only.
I have tried setting up an example ACL and ACE such as per attached screenshot and apply the ACL to all ports on the switch:-

When I do this the management can't ping anything. It seems that the 'deny' is blocking the replies etc.
Is this possible, if you how? Thanks in advance.
ASKER
@cyonconcisco
Ok, if thats the case then whats the point of the switch access-lists? Other forum posts seem to suggest this is possible.
Ok, if thats the case then whats the point of the switch access-lists? Other forum posts seem to suggest this is possible.
Give this a try:
VLAN 100
access-list 100 permit icmp any any echo-reply
access-list 100 permit tcp any host 192,.168.200.100 eq 443(https)
access-list 100 deny ip any 192.168.200.0 0.0.0.255
access-list 100 deny ip any 196.168.220.0 0.0.0.255
access-list 100 permit ip any any
interface vlan100
ip access-group 100 in
VLAN 200
access-list 200 permit icmp any any echo-reply
access-list 200 permit ip host 192.168.200.100 192.168.100.0 0.0.0.255
access-list 200 deny ip any 192.168.100.0 0.0.0.255
access-list 200 deny ip any 196.168.220.0 0.0.0.255
access-list 200 permit ip any any
interface vlan200
ip access-group 200 in
VLAN 100
access-list 100 permit icmp any any echo-reply
access-list 100 permit tcp any host 192,.168.200.100 eq 443(https)
access-list 100 deny ip any 192.168.200.0 0.0.0.255
access-list 100 deny ip any 196.168.220.0 0.0.0.255
access-list 100 permit ip any any
interface vlan100
ip access-group 100 in
VLAN 200
access-list 200 permit icmp any any echo-reply
access-list 200 permit ip host 192.168.200.100 192.168.100.0 0.0.0.255
access-list 200 deny ip any 192.168.100.0 0.0.0.255
access-list 200 deny ip any 196.168.220.0 0.0.0.255
access-list 200 permit ip any any
interface vlan200
ip access-group 200 in
ASKER
@Soulja
Sorry but your commands are for IOS, this is a small business switch (SG500) and the commands are very different.
Sorry but your commands are for IOS, this is a small business switch (SG500) and the commands are very different.
The point of ACL is to filter one-way traffic for static protocols and ports.
If you need bi-directional communication you need to open the return traffic on the ACL.
If its just ping you want from management then echo-reply is enought.
If you need telnet, ssh, snmp, syslog, then you need the corresponding ports opened.
But then the statement:
VLAN 100 and 200 should not reach MANAGEMENT VLAN is not completedly true,
It should be
VLAN 100 and 200 should not reach MANAGEMENT VLAN except for Ping, Telnet, SSH, etc.
Regards
If you need bi-directional communication you need to open the return traffic on the ACL.
If its just ping you want from management then echo-reply is enought.
If you need telnet, ssh, snmp, syslog, then you need the corresponding ports opened.
But then the statement:
VLAN 100 and 200 should not reach MANAGEMENT VLAN is not completedly true,
It should be
VLAN 100 and 200 should not reach MANAGEMENT VLAN except for Ping, Telnet, SSH, etc.
Regards
@AW5000
Yes, I am aware of that. You should still be able to make your ACL based on what I provided in the gui. Of course it won't be the exact commands but the order and source/dest information should be the same. Also the direction I applied it on your vlan interfaces.
Yes, I am aware of that. You should still be able to make your ACL based on what I provided in the gui. Of course it won't be the exact commands but the order and source/dest information should be the same. Also the direction I applied it on your vlan interfaces.
ASKER
@cyonconcisco
That seems very impractical. Also surely that would allow 100 and 200 to be telnet and ssh in to the management vlan.
Ok, I think I need to work out an alternative.
That seems very impractical. Also surely that would allow 100 and 200 to be telnet and ssh in to the management vlan.
Ok, I think I need to work out an alternative.
Create your GUI acl layed out how I did the CLI ACL's above. This should meet all of your requirement.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Cyon is correct. After looking at my acl's. It doesn't account for return traffic back to the management vlan, so yes you would need some type of stateful inspection.
@Cyon
Based on your ACL shouldn't the direction be input on the VLAN interfaces? Also, echo reply allows ping replies back to management, not ping requests, so the two vlan will not be able to ping management, just reply to pings from management.
@Cyon
Based on your ACL shouldn't the direction be input on the VLAN interfaces? Also, echo reply allows ping replies back to management, not ping requests, so the two vlan will not be able to ping management, just reply to pings from management.
@Soulja
Yes youre correct, thats not "echo-reply" but "echo" for the output traffic.
The ACLS can be inbound but you should invert the source/destination on the statements.
Yes youre correct, thats not "echo-reply" but "echo" for the output traffic.
The ACLS can be inbound but you should invert the source/destination on the statements.
but because its for traffic goint to the management VLAN , it should expect "echo-reply" ans the packets comming from VLAN 100 and 200.
Asumming the ping was originated on Management Vlan
Asumming the ping was originated on Management Vlan
@Cyon,
Based on your ACL it should be inbound.
Inbound means sourcing from the vlan to the vlan interface.
Outbound means destined for the vlan from the vlan interface.
Based on your ACL it should be inbound.
Inbound means sourcing from the vlan to the vlan interface.
Outbound means destined for the vlan from the vlan interface.
VLAN 100 and 200 should not reach MANAGEMENT VLAN,
But Management VLAN should reach VLAN 100 and 200?
If this is what you want you need a Firewall or something that does inspection for the traffic you want to pass from management to vlan 100 and 200.
Or you can try reflexive ACL , although I think they are not supported on the SG500.
Regards