Mango-Man
asked on
Juniper SSG20 Firewall Blocking SSL
Hi all,
I have a Plesk web server behind a Juniper firewall. The firewall is configured as per these instructions:
http://kb.juniper.net/InfoCenter/index?page=content&id=KB4216
Now while most of the services are working fine (http, smtp, pop) some are not such as SSL (port 443), the plesk webadmin (port 8443)
Does anyone know if there is something special that needs to be configured on the VIP or policy to allow SSL related traffic through?
Thanks
Bob
I have a Plesk web server behind a Juniper firewall. The firewall is configured as per these instructions:
http://kb.juniper.net/InfoCenter/index?page=content&id=KB4216
Now while most of the services are working fine (http, smtp, pop) some are not such as SSL (port 443), the plesk webadmin (port 8443)
Does anyone know if there is something special that needs to be configured on the VIP or policy to allow SSL related traffic through?
Thanks
Bob
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Sry but looks like attachment didnt make it; can you repost.
Thank you.
Thank you.
ASKER
dpk_wal,
Can you advise where in the GUI I would find the option to export the configuration? I can't see anything appropriate under management or reports.
Thanks!
Bob
Can you advise where in the GUI I would find the option to export the configuration? I can't see anything appropriate under management or reports.
Thanks!
Bob
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Thanks Qlemo! :)
ASKER
Thanks both for your help!
Apologies for the confusion on the questions, to answer correctly:
Q1) Yes the VIP uses a different IP to the one defined on its interface (see images below)
Q2) The VIP is on the same subnet as the interface IP (/24) (see images below)
As requested, here is the sanitized config export:
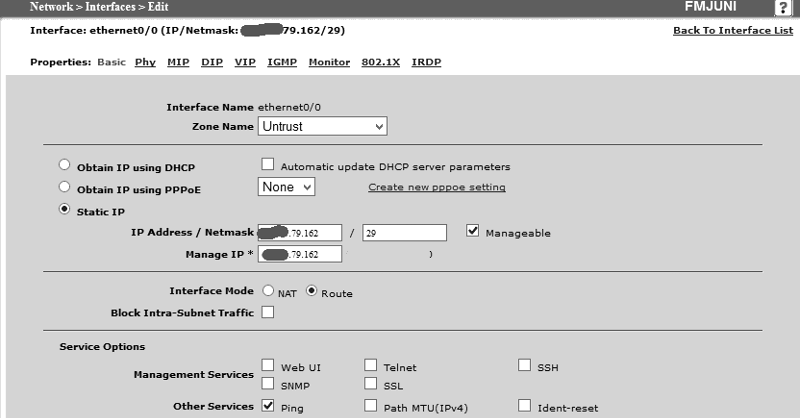
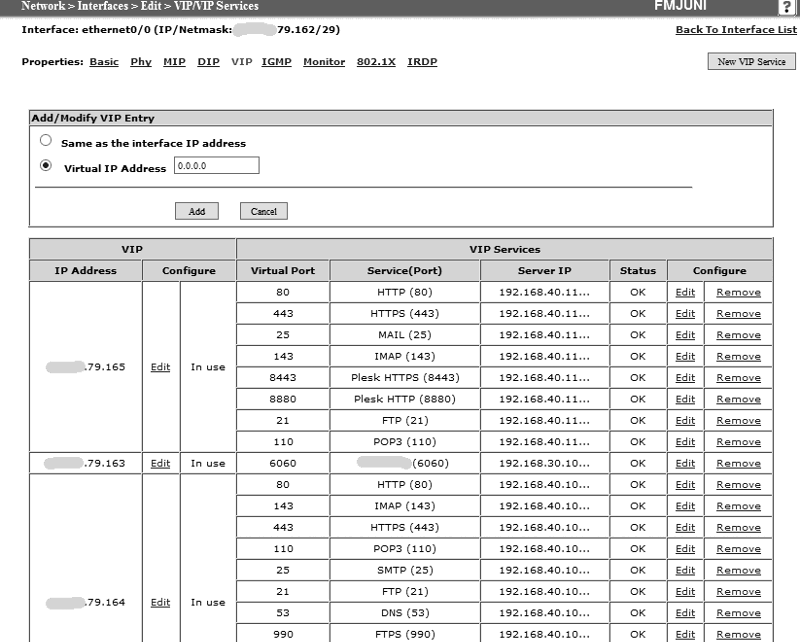
Apologies for the confusion on the questions, to answer correctly:
Q1) Yes the VIP uses a different IP to the one defined on its interface (see images below)
Q2) The VIP is on the same subnet as the interface IP (/24) (see images below)
As requested, here is the sanitized config export:
unset key protection enable
set clock timezone 0
set vrouter trust-vr sharable
set vrouter "untrust-vr"
exit
set vrouter "trust-vr"
unset auto-route-export
exit
set service "Spandex" protocol tcp src-port 6060-6061 dst-port 6060-6061
set service "Spandex" + tcp src-port 32004-32004 dst-port 32004-32004
set service "Spandex" + tcp src-port 32007-32007 dst-port 32007-32007
set service "FTP-DATA" protocol tcp src-port 20-20 dst-port 20-20
set service "SMTPS" protocol tcp src-port 465-465 dst-port 465-465
set service "FTPS" protocol tcp src-port 990-990 dst-port 990-990
set service "IMAPS" protocol tcp src-port 993-993 dst-port 993-993
set service "POP3S" protocol tcp src-port 995-995 dst-port 995-995
set service "Plesk HTTPS" protocol tcp src-port 8443-8443 dst-port 8443-8443
set service "Plesk HTTP" protocol tcp src-port 8880-8880 dst-port 8880-8880
set service "Web Service Requests" protocol tcp src-port 6061-6061 dst-port 6061-6061
set alg appleichat enable
unset alg appleichat re-assembly enable
set alg sctp enable
set auth-server "Local" id 0
set auth-server "Local" server-name "Local"
set auth default auth server "Local"
set auth radius accounting port 1646
set admin name "expert-sexchange"
set admin password "nDZlSpoodleDoodleDingoDongdfdfn"
set admin http redirect
set admin auth web timeout 10
set admin auth dial-in timeout 3
set admin auth server "Local"
set admin format dos
set zone "Trust" vrouter "trust-vr"
set zone "Untrust" vrouter "trust-vr"
set zone "DMZ" vrouter "trust-vr"
set zone "VLAN" vrouter "trust-vr"
set zone id 100 "OurSpandexServer / Spandex"
set zone id 101 "OurWebServer / Plesk"
set zone "Untrust-Tun" vrouter "trust-vr"
set zone "Trust" tcp-rst
set zone "Untrust" block
unset zone "Untrust" tcp-rst
set zone "MGT" block
unset zone "V1-Trust" tcp-rst
unset zone "V1-Untrust" tcp-rst
set zone "DMZ" tcp-rst
unset zone "V1-DMZ" tcp-rst
unset zone "VLAN" tcp-rst
set zone "OurSpandexServer / Spandex" tcp-rst
set zone "OurWebServer / Plesk" tcp-rst
set zone "Untrust" screen tear-drop
set zone "Untrust" screen syn-flood
set zone "Untrust" screen ping-death
set zone "Untrust" screen ip-filter-src
set zone "Untrust" screen land
set zone "V1-Untrust" screen tear-drop
set zone "V1-Untrust" screen syn-flood
set zone "V1-Untrust" screen ping-death
set zone "V1-Untrust" screen ip-filter-src
set zone "V1-Untrust" screen land
set interface adsl1/0 phy operating-mode auto
set interface "ethernet0/0" zone "Untrust"
set interface "ethernet0/1" zone "DMZ"
set interface "ethernet0/3" zone "OurSpandexServer / Spandex"
set interface "ethernet0/4" zone "OurWebServer / Plesk"
set interface "wireless0/0" zone "Trust"
set interface "bgroup0" zone "Trust"
set interface "adsl1/0" pvc 8 35 mux llc protocol bridged qos ubr zone "Untrust"
set interface bgroup0 port ethernet0/2
unset interface vlan1 ip
set interface ethernet0/0 ip 12.345.79.162/29
set interface ethernet0/0 route
set interface ethernet0/1 ip 192.168.10.1/24
set interface ethernet0/1 nat
set interface ethernet0/3 ip 192.168.30.1/24
set interface ethernet0/3 route
set interface ethernet0/4 ip 192.168.40.1/24
set interface ethernet0/4 route
set interface wireless0/0 ip 192.168.5.1/24
set interface wireless0/0 nat
set interface bgroup0 ip 192.168.20.1/24
set interface bgroup0 nat
set interface ethernet0/0 gateway 12.345.79.161
unset interface vlan1 bypass-others-ipsec
unset interface vlan1 bypass-non-ip
set interface ethernet0/0 ip manageable
set interface ethernet0/1 ip manageable
set interface ethernet0/3 ip manageable
set interface ethernet0/4 ip manageable
set interface wireless0/0 ip manageable
set interface bgroup0 ip manageable
set interface ethernet0/0 manage ping
set interface ethernet0/3 manage ping
set interface ethernet0/3 manage ssh
set interface ethernet0/3 manage telnet
set interface ethernet0/3 manage snmp
set interface ethernet0/3 manage ssl
set interface ethernet0/3 manage web
set interface ethernet0/4 manage ping
set interface ethernet0/4 manage ssh
set interface ethernet0/4 manage telnet
set interface ethernet0/4 manage snmp
set interface ethernet0/4 manage ssl
set interface ethernet0/4 manage web
set interface bgroup0 manage mtrace
set interface ethernet0/0 vip 12.345.79.165 80 "HTTP" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 443 "HTTPS" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 25 "MAIL" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 143 "IMAP" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 8443 "Plesk HTTPS" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 8880 "Plesk HTTP" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 21 "FTP" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.165 + 110 "POP3" 192.168.40.11
set interface ethernet0/0 vip 12.345.79.163 6060 "Spandex" 192.168.30.10
set interface ethernet0/0 vip 12.345.79.164 80 "HTTP" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 143 "IMAP" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 443 "HTTPS" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 110 "POP3" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 25 "SMTP" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 21 "FTP" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 53 "DNS" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 990 "FTPS" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 993 "IMAPS" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 995 "POP3S" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 8443 "Plesk HTTPS" 192.168.40.10
set interface ethernet0/0 vip 12.345.79.164 + 8880 "Plesk HTTP" 192.168.40.10
set interface wireless0/0 dhcp server service
set interface wireless0/0 dhcp server auto
set interface wireless0/0 dhcp server option dns1 64.54.126.22
set interface wireless0/0 dhcp server option dns2 64.54.116.4
set interface wireless0/0 dhcp server ip 192.168.5.55 to 192.168.5.85
unset interface wireless0/0 dhcp server config next-server-ip
set interface "serial0/0" modem settings "USR" init "AT&F"
set interface "serial0/0" modem settings "USR" active
set interface "serial0/0" modem speed 115200
set interface "serial0/0" modem retry 3
set interface "serial0/0" modem interval 10
set interface "serial0/0" modem idle-time 10
set interface wireless0 wlan 0
set flow tcp-mss
unset flow tcp-syn-check
unset flow tcp-syn-bit-check
set flow reverse-route clear-text prefer
set flow reverse-route tunnel always
set hostname FMJUNI
set pki authority default scep mode "auto"
set pki x509 default cert-path partial
set dns host dns1 64.54.126.22 src-interface ethernet0/0
set dns host dns2 64.54.116.4 src-interface ethernet0/0
set dns host dns3 208.67.222.222 src-interface ethernet0/0
set address "Trust" "192.168.20.10/24" 192.168.20.10 255.255.255.0
set address "OurSpandexServer / Spandex" "192.168.30.10/24" 192.168.30.10 255.255.255.0
set address "OurSpandexServer / Spandex" "192.168.30.10/32" 192.168.30.10 255.255.255.255
set address "OurWebServer / Plesk" "192.168.30.10/32" 192.168.30.10 255.255.255.255
set address "OurWebServer / Plesk" "192.168.40.10/24" 192.168.40.10 255.255.255.0
set crypto-policy
exit
set ike respond-bad-spi 1
set ike ikev2 ike-sa-soft-lifetime 60
unset ike ikeid-enumeration
unset ike dos-protection
unset ipsec access-session enable
set ipsec access-session maximum 5000
set ipsec access-session upper-threshold 0
set ipsec access-session lower-threshold 0
set ipsec access-session dead-p2-sa-timeout 0
unset ipsec access-session log-error
unset ipsec access-session info-exch-connected
unset ipsec access-session use-error-log
set vrouter "untrust-vr"
exit
set vrouter "trust-vr"
exit
set url protocol websense
exit
set policy id 3 from "OurWebServer / Plesk" to "Untrust" "Any" "Any" "ANY" nat src permit log
set policy id 3
exit
set policy id 2 from "OurSpandexServer / Spandex" to "Untrust" "Any" "Any" "ANY" nat src permit log
set policy id 2
exit
set policy id 1 from "Trust" to "Untrust" "Any" "Any" "ANY" permit
set policy id 1
exit
set policy id 9 name "Bob`s Alternative OurWebServer Rule" from "Untrust" to "Trust" "Any" "VIP(12.345.79.165)" "DNS" permit
set policy id 9
set service "FTP"
set service "HTTP"
set service "HTTPS"
set service "IMAPS"
set service "Plesk HTTP"
set service "Plesk HTTPS"
set service "POP3S"
set service "SMTP"
set service "SMTPS"
set service "TFTP"
exit
set policy id 10 name "Spandex Inbound via VIP" from "Untrust" to "Trust" "Any" "VIP(12.345.79.163)" "HTTP" permit
set policy id 10
set service "HTTPS"
set service "Spandex"
exit
set policy id 13 name "OurWebServer Webserver via VIP" from "Untrust" to "Trust" "Any" "VIP(12.345.79.164)" "DNS" permit
set policy id 13
set service "FTP"
set service "HTTP"
set service "HTTPS"
set service "IMAPS"
set service "MAIL"
set service "PING"
set service "Plesk HTTP"
set service "Plesk HTTPS"
set service "POP3"
set service "POP3S"
set service "SMTP"
set service "SMTPS"
exit
set nsmgmt bulkcli reboot-timeout 60
set ssh version v2
set config lock timeout 5
unset license-key auto-update
set telnet client enable
set wlan 0 channel auto
set wlan 1 channel auto
set ssid name POTATO
set ssid POTATO authentication wpa2-psk passphrase 4BHCt5bENBiNGoBangOILoveBongosnCeF1+iKyIYHBuNI= encryption aes
set ssid POTATO interface wireless0
set snmp port listen 161
set snmp port trap 162
set vrouter "untrust-vr"
exit
set vrouter "trust-vr"
unset add-default-route
exit
set vrouter "untrust-vr"
exit
set vrouter "trust-vr"
exit
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Qlemo,
Thanks again for your help!
First step, if you do not know better, is to enable traffic logging (on session begin) in the corresponding policies (9 and 13 here). Then try to use the failing services, and watch whether the attempts are logged.
I've enabled logging for all three policies (on session begin checked) and nothing is being logged at all (I'm going to Reports > System Log > Event). I went in to Configuration > Report Settings > Log Settings and ticked *everything* but still no luck.
I would have chosen MIPs here. You are mapping one public IP to exact one private IP.
Understood - they were actually originally MIPs but I was following advice given elsewhere and the walkthrough for publishing a web server on the Juniper website said either. If either works, I'd prefer to use VIPs as it means I can split services between different internal servers later on (with the same public IP which means clients don't have to change any settings!)
On another note, you do not need to apply restrictions in the VIP policies, unless you want to block services configured in the VIP table temporarily. The VIP table definition itself is the restriction, and suffices.
Ok so if I understand correctly, I keep the policy allowing 'ANY to VIP' but don't select any services? As there doesn't seem to be an *any* or *all* option, will this not simply completely block traffic or doesn't not selecting a service tell the system to allow any? Screenshot:

Thanks again for your help!
First step, if you do not know better, is to enable traffic logging (on session begin) in the corresponding policies (9 and 13 here). Then try to use the failing services, and watch whether the attempts are logged.
I've enabled logging for all three policies (on session begin checked) and nothing is being logged at all (I'm going to Reports > System Log > Event). I went in to Configuration > Report Settings > Log Settings and ticked *everything* but still no luck.
I would have chosen MIPs here. You are mapping one public IP to exact one private IP.
Understood - they were actually originally MIPs but I was following advice given elsewhere and the walkthrough for publishing a web server on the Juniper website said either. If either works, I'd prefer to use VIPs as it means I can split services between different internal servers later on (with the same public IP which means clients don't have to change any settings!)
On another note, you do not need to apply restrictions in the VIP policies, unless you want to block services configured in the VIP table temporarily. The VIP table definition itself is the restriction, and suffices.
Ok so if I understand correctly, I keep the policy allowing 'ANY to VIP' but don't select any services? As there doesn't seem to be an *any* or *all* option, will this not simply completely block traffic or doesn't not selecting a service tell the system to allow any? Screenshot:
ASKER
Again, if you're interested - I'd be happy to arrange remote access and pay you via PayPal to simply fix this for us.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi Qlemo,
Whoops! I didn't realize it was against the rules!
So I changed the services list to ANY (I was blind but now I see) on the policy for one of the interfaces and hey presto, port 8443 immediately started working and I could view the GUI in a browser! I tried telnetting to and yep connection made.
I removed those entries from the defined VIP services and I was unable to access them so I'm all good - everything is blocked except the services explicitly defined in the VIP definition!
One thing is still baffling me - I would break it out to a seperate question but I suspect you'll answer it in two seconds: the list of 'services' available in the VIP definition page doesn't seem to be the same list as the one available in policies (or if it is, it's only registering the first port of one of my entries). Is it the same list or are services defined for VIPs configured somewhere else (not Policy Elements > Services > Custom)
Many thanks for all your help with this!
Bob
Whoops! I didn't realize it was against the rules!
So I changed the services list to ANY (I was blind but now I see) on the policy for one of the interfaces and hey presto, port 8443 immediately started working and I could view the GUI in a browser! I tried telnetting to and yep connection made.
I removed those entries from the defined VIP services and I was unable to access them so I'm all good - everything is blocked except the services explicitly defined in the VIP definition!
One thing is still baffling me - I would break it out to a seperate question but I suspect you'll answer it in two seconds: the list of 'services' available in the VIP definition page doesn't seem to be the same list as the one available in policies (or if it is, it's only registering the first port of one of my entries). Is it the same list or are services defined for VIPs configured somewhere else (not Policy Elements > Services > Custom)
Many thanks for all your help with this!
Bob
ASKER
Apologies - disregard the last query - it *is* the same list but when applying these services to VIPs, the firewall only seems to take notice of the first port if that service has multiple ports defined.
I have therefore changed the services to only have one port per entry.
Thanks again!
I have therefore changed the services to only have one port per entry.
Thanks again!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hey Qlemo,
That's what I assumed but until I split the services, one of my custom ports just wasn't working - as soon as I split it, it started working.
I'm so happy its working that I'm not going to worry too much about the why!
Thanks again for all your help!
Bob
That's what I assumed but until I split the services, one of my custom ports just wasn't working - as soon as I split it, it started working.
I'm so happy its working that I'm not going to worry too much about the why!
Thanks again for all your help!
Bob
ASKER
Qlemo should get paid by Juniper! He spent a lot of time guiding me through my problem without getting frustrated with my lack of knowledge - wonderful.
I forgot to mention you need a special setting, only available in the CLI (telnet, SSH or serial), to allow for multi-port VIP services ... Thought that is the default meanwhile with current firmware releases.
set vip multi-port
save
reset
ASKER
Note: One thing to clarify - many of the ports *are* for this VIP/private IP mapping are working perfectly so it's not a general configuration issue,
1. Is the VIP using the same IP as interface IP.
No - the VIP is a public IP, the trusted interface is a private IP (192.168.40.10)
2. Is VIP IP in different subnet that interface IP subnet.
Yes (see above answer) and above note
3. Are you using HTTPS to manage SSG; if yes, then changing management port would do the trick
The Juniper unit is on a separate port and given that port 80 is working fine on my other IPs (so the WebGUI isn't likely to be inteferring with 443 either), I don't think that's the problem.
Does anyone want to do some remote consulting on this? It's a simple setup on blanks servers at the moment so I can provide TeamViewer access. All I need is:
All required services accessible (a short list include https, https on 8443, etc).
A brief explanation of what was done.
A backup of the router configuration.
Thanks
Bob