Bruteforcing with Burp Suite: how to set up the Payload
Greeting Everyone,
I am in the process of verifying a Vulnerability on one of my companies’ websites and needs a bit of help with it ( see screen shot below). I used burp suite to crawl the website, used the Scanner, and sent the results to the intruder function to verify the brute force Vulnerability ….. I changed the attack type to “cluster bomb” and went to “clear” the presets (highlighted in Orange) .. But I am not for sure how to reset for the “wrap_username=$Admin$”, “wrap_password=$anypasswor
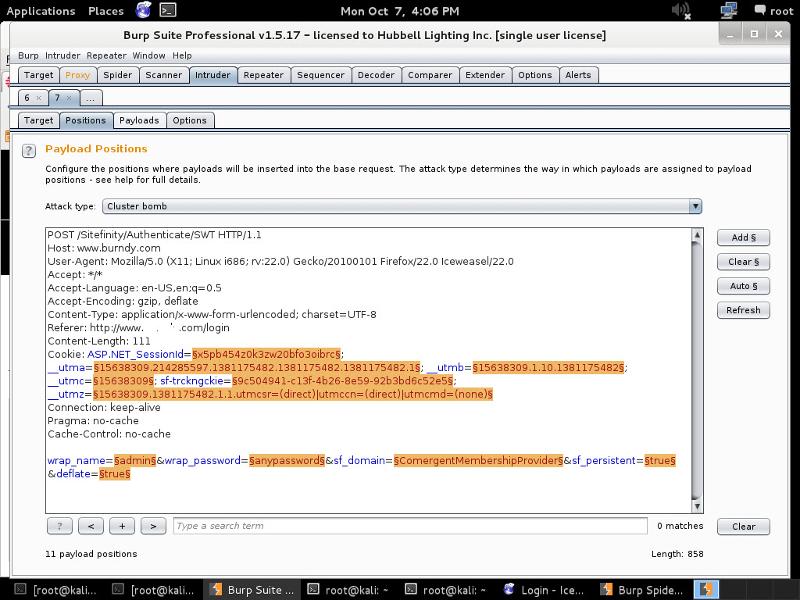
I am in the process of verifying a Vulnerability on one of my companies’ websites and needs a bit of help with it ( see screen shot below). I used burp suite to crawl the website, used the Scanner, and sent the results to the intruder function to verify the brute force Vulnerability ….. I changed the attack type to “cluster bomb” and went to “clear” the presets (highlighted in Orange) .. But I am not for sure how to reset for the “wrap_username=$Admin$”, “wrap_password=$anypasswor

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER