How to password encrypt a hard drive.
I have a backup 3.5" 1tb hard drive. I need to know a way of encrypting the contents of this drive and require a password to access it. It does NOT have to be any sort of high level government super encryption. Just a format that would be EXTREMELY difficult for your average hacker / thief to crack. Any suggestions from an Expert that has had PERSONAL EXPERIENCE with a particular program? Must be easy to use and cost no more than $60. Free would be nice.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
THANK YOU SO MUCH!!! I feel that I have received a mini education on passwords and truly appreciate each response! I had NO idea how complicated this subject is and how vulnerable people are. I appreciate ALL you EXPERTS! I apologize for the long response time. Health problems.
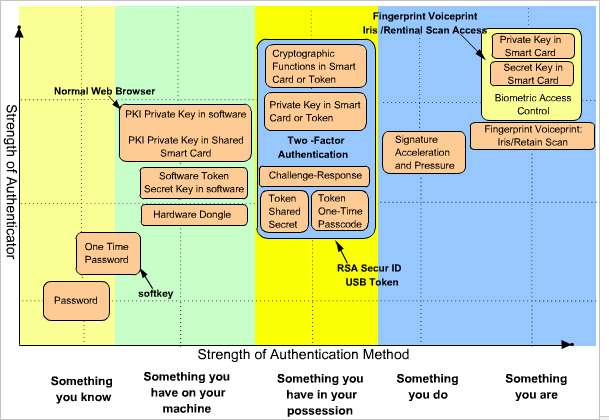
Precisely why two-factor authentication is so highly recommended.
My YubiKey is to the far right.
Another suggestion is to reference a file or passphase (a complete sentence or paragraph of your choosing) and perform a SHA-256 hash against it (could combine with a salt for added measure.) You'd then use the SHA-256 hash as your actual password.