sunhux
asked on
Measures against hacking of websites
Lately, an anonymous group has appeared in youtube
to hack websites, possibly by altering the pages on
the websites:
http://www.youtube.com/watch?v=AJCU14M7PBU
I'll need to brainstorm for a list of preventive measures to
pre-empt the above attacks.
a) run vulnerability scan (Nessus) ?
b) apply latest MS security patches ?
Anything else?
to hack websites, possibly by altering the pages on
the websites:
http://www.youtube.com/watch?v=AJCU14M7PBU
I'll need to brainstorm for a list of preventive measures to
pre-empt the above attacks.
a) run vulnerability scan (Nessus) ?
b) apply latest MS security patches ?
Anything else?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
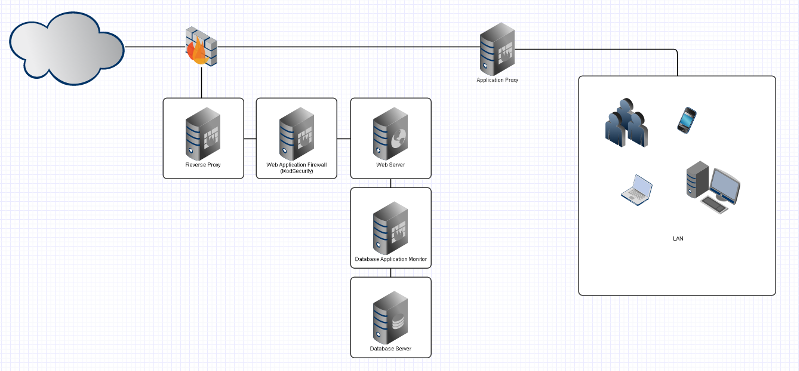
Here's a sample diagram depicting my recommended approach.