MrMay
asked on
encryption mixup
Hello,
I'm trying to understand how encryption works.
This is my understanding. Symmetric key is the usage of the same key on both computers (sending computer and receiving computer). Pretty much a private key between the two, right?
Asymmetric key is the usage of two keys, public and private on each computer, right?
Now, I read two different articles online and each one has the data different.
When a sending computer encrypts a msg, it first encrypts the msg with its private key and then it encrypts it with a public key. or is it the other way... the sending computer encrypts the msg with the public key and then with the private key... ?????
I'm trying to understand how encryption works.
This is my understanding. Symmetric key is the usage of the same key on both computers (sending computer and receiving computer). Pretty much a private key between the two, right?
Asymmetric key is the usage of two keys, public and private on each computer, right?
Now, I read two different articles online and each one has the data different.
When a sending computer encrypts a msg, it first encrypts the msg with its private key and then it encrypts it with a public key. or is it the other way... the sending computer encrypts the msg with the public key and then with the private key... ?????
It depends who you want to be able to read the message.
ASKER
ozo... you answer does not answer my question.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ok, let's say that I encrypt a msg using my private key and I send the corresponding public key to Bob. How do I know that Bob will get that public key and not someone else (man in the middle attacker) pretending to be Bob?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
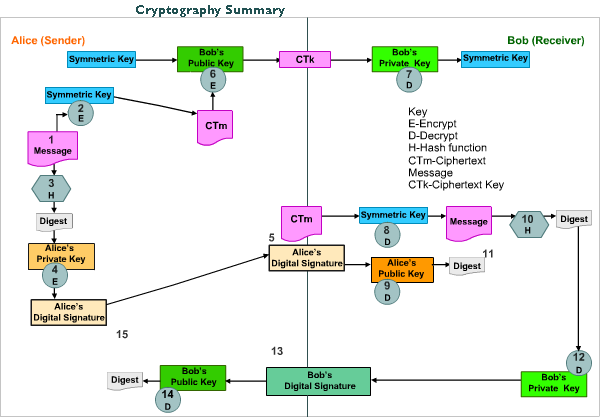
Here is a look at how message integrity controls and digital signatures fit into the overall process of transmitting information to ensure confidentiality, integrity, non-repudiation, and assurance of delivery. Now they actually have confidentiality, integrity, proof of origin, and proof of receipt.