Techrunner
asked on
Outbound Traffic with Multiple ISP WAN connections
Hello Experts,
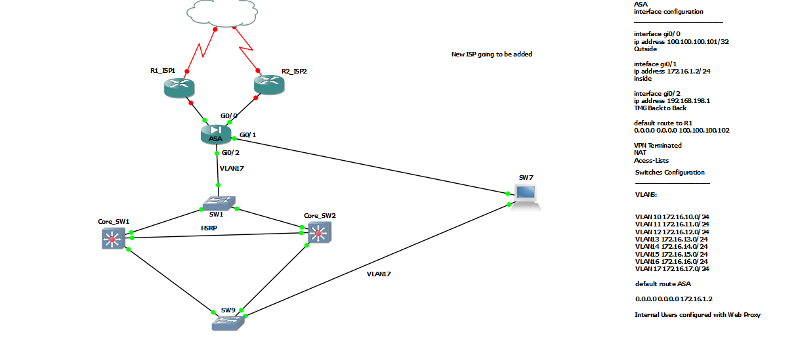
Please have a look at my diagram I've mentioned all required information
- We are using Microsoft TMG Firewall as a web proxy for our internal clients. Its has 2 NIC External connected to ASA and Internal connected to Switch.
- We are going to add a new ISP, now I want that proxy should route all the internet traffic to New R2_ISP2 as primary, if ISP2 fails he should automatically route to R1
- I want to keep R1 now for VPN Traffic and Inbound Services a nd as backup if R1_ISP2 fails for outbound internet traffic
Please help me to achieve and where R2_ISP2 should be connected in the diagram to achieve the above rule.
Please let me know if my question is not clear.
Thanks in advance
Topology2.jpeg.jpeg.jpeg
Please have a look at my diagram I've mentioned all required information
- We are using Microsoft TMG Firewall as a web proxy for our internal clients. Its has 2 NIC External connected to ASA and Internal connected to Switch.
- We are going to add a new ISP, now I want that proxy should route all the internet traffic to New R2_ISP2 as primary, if ISP2 fails he should automatically route to R1
- I want to keep R1 now for VPN Traffic and Inbound Services a nd as backup if R1_ISP2 fails for outbound internet traffic
Please help me to achieve and where R2_ISP2 should be connected in the diagram to achieve the above rule.
Please let me know if my question is not clear.
Thanks in advance
Topology2.jpeg.jpeg.jpeg
I agree with vyarad. BGP is the right way to go about this. I'd consider one of the following:
1. Put another router in between the ASA and your ISP's router. Have connect both ISPs to that router and have BGP do the routing.
2. If you have control over it, you could possibly connect one of the routers to the other, and then use BGP with both of them, to best determine the appropriate route.
1. Put another router in between the ASA and your ISP's router. Have connect both ISPs to that router and have BGP do the routing.
2. If you have control over it, you could possibly connect one of the routers to the other, and then use BGP with both of them, to best determine the appropriate route.
ASKER
Thank You Guys for your response.
But I want only my web proxy server to go to R2_ISP2.
Our users are using Microsoft TMG as there proxy. Currently the external NIC of proxy server is connected to ASA and ASA is performing the NAT and has default route to R1_ISP1 router.
Now I want to bring R2_ISP2 in the scenario so it can use this line as primary and R2_ISP1 as secondary.
But I want only my web proxy server to go to R2_ISP2.
Our users are using Microsoft TMG as there proxy. Currently the external NIC of proxy server is connected to ASA and ASA is performing the NAT and has default route to R1_ISP1 router.
Now I want to bring R2_ISP2 in the scenario so it can use this line as primary and R2_ISP1 as secondary.
The problem isn't switching you over to R2_ISP2. The problem is setting up R2_ISP1 as a secondary. Not only that, but you want to keep R2_ISP1 up and running for a different service in the meantime. You need to have some way of making that switchover happen. What mechanism do you want to use?
We're both thinking that the appropriate one to use is a dynamic routing protocol; specifically, BGP. But the ASA doesn't speak BGP, so it's not going to know which router to use, directly. So you're going to need the ASA to send packets to one of the routers, and let that router make the decision. If its BGP table says that the correct route is the other route, it'll forward it along.
You could also do it without BGP, sort of. You could, again, select one of the routers to be the primary (or you could do something like HSRP and use a "shared" IP address), and give the primary router a static route to the other one for the 0.0.0.0 route. Assuming you'd be using R2_ISP2 as the primary, you'd weight that route to make it less attractive than its directly-attached route. Now, if the directly-attached connection (ISP) goes down, packets will be redirected to R2_ISP1, which also has a 0.0.0.0 route through its own direct-connection. That would work, except that you pretty much wouldn't be able to use it for those specific applications. It would just be a backup connection. See the picture here.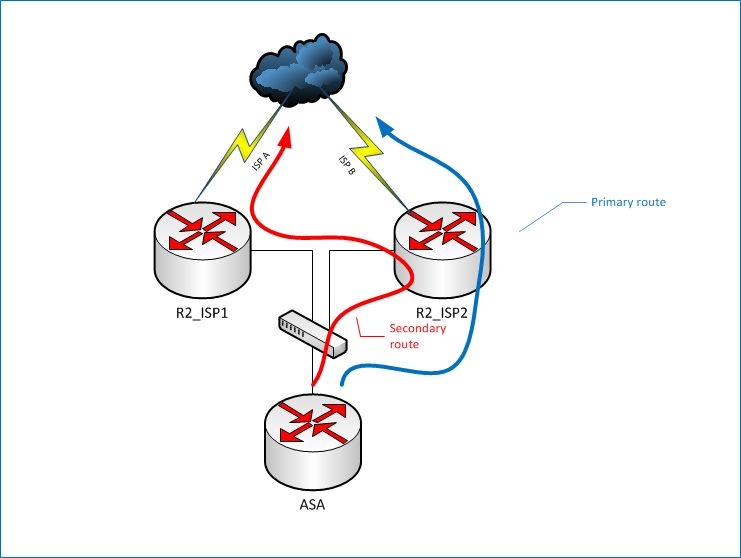 Those are the only two ways I can think of.
Those are the only two ways I can think of.
We're both thinking that the appropriate one to use is a dynamic routing protocol; specifically, BGP. But the ASA doesn't speak BGP, so it's not going to know which router to use, directly. So you're going to need the ASA to send packets to one of the routers, and let that router make the decision. If its BGP table says that the correct route is the other route, it'll forward it along.
You could also do it without BGP, sort of. You could, again, select one of the routers to be the primary (or you could do something like HSRP and use a "shared" IP address), and give the primary router a static route to the other one for the 0.0.0.0 route. Assuming you'd be using R2_ISP2 as the primary, you'd weight that route to make it less attractive than its directly-attached route. Now, if the directly-attached connection (ISP) goes down, packets will be redirected to R2_ISP1, which also has a 0.0.0.0 route through its own direct-connection. That would work, except that you pretty much wouldn't be able to use it for those specific applications. It would just be a backup connection. See the picture here.
 Those are the only two ways I can think of.
Those are the only two ways I can think of.
ASKER
Hi,
Thanks.
Please can you provide me an example or confiugration similar to my scenarion so I can start workaround.
Thanks
Thanks.
Please can you provide me an example or confiugration similar to my scenarion so I can start workaround.
Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
BGP is the vision of networking specialist. If TMG can do load-balancing and redundant connection itself this is a good solution without doubt.
ASKER
Actually I have experienced a lot of issues with many customers regarding TMG ISP-R.
So I want to keep TMG only as web proxy.
I am only looking for a way to let TMG forward any traffic to R2-ISP2, if this line fails route to R1_ISP1.
How I can achieve this using cisco routing based protocol or static routing.
If this is possible, where should I place R2 in the scenario.
I have never worked with BGP.
Thanks
So I want to keep TMG only as web proxy.
I am only looking for a way to let TMG forward any traffic to R2-ISP2, if this line fails route to R1_ISP1.
How I can achieve this using cisco routing based protocol or static routing.
If this is possible, where should I place R2 in the scenario.
I have never worked with BGP.
Thanks
I think all you're going to do via a standard BGP configuration is route out of the most efficient path to the destination if you're using two different ISPs. To fully support what you want using BGP you'd need your own PI IPv4 address space and ASN. I'd say it's overkill for this solution.
If you go with BGP, you need to use the same ISP at least if you want to offer inbound services in order to ensure that DNS changes aren't required. To achieve this, the ISP needs to be able to use the same ASN on each link so that the IP addresses you've been assigned from the ISP's PA space can be routed down the second link. That's highly unlikely unless you go with two circuits which terminate at the same PoP and use the same circuit type.
Have a look at this - it's an interesting article which explains how you'd need to do it...
https://supportforums.cisco.com/docs/DOC-13015
If you go with BGP, you need to use the same ISP at least if you want to offer inbound services in order to ensure that DNS changes aren't required. To achieve this, the ISP needs to be able to use the same ASN on each link so that the IP addresses you've been assigned from the ISP's PA space can be routed down the second link. That's highly unlikely unless you go with two circuits which terminate at the same PoP and use the same circuit type.
Have a look at this - it's an interesting article which explains how you'd need to do it...
https://supportforums.cisco.com/docs/DOC-13015
All presented solutions have a chance to live. You need try a couple of them and choose affordable.
ASKER
thanks.
I guess I am failing to ask the question properly.
Just to review my scenario and what I am looking for.
- I have Cisco ASA with 3 interfaces
Gi0/0 - Outside to R1_ISP1 Router
Gi0/1 - Inside to Internal Network
Gi0/2 - TMG Back to Back - Connected External interface of TMG
- ASA has now default route to R1 router
- I have Mulitlayer Layer switch inside network with different vlans. Switch has default route to ASA.
- I have TMG with 2 interfaces ( Internal and External). External NIC connected directly connected to ASA as mentioned above.
- Our users using Web Proxy to go internet ( http and https).
Now we purchased additional internet line dedicated only for Internal Web traffic. And keep previous ISP for VPN and Publishing Internal resources.
My concern
How can I let my proxy server route traffic to R2_ISP2, if this fails he should route web traffic to R1
I guess I am failing to ask the question properly.
Just to review my scenario and what I am looking for.
- I have Cisco ASA with 3 interfaces
Gi0/0 - Outside to R1_ISP1 Router
Gi0/1 - Inside to Internal Network
Gi0/2 - TMG Back to Back - Connected External interface of TMG
- ASA has now default route to R1 router
- I have Mulitlayer Layer switch inside network with different vlans. Switch has default route to ASA.
- I have TMG with 2 interfaces ( Internal and External). External NIC connected directly connected to ASA as mentioned above.
- Our users using Web Proxy to go internet ( http and https).
Now we purchased additional internet line dedicated only for Internal Web traffic. And keep previous ISP for VPN and Publishing Internal resources.
My concern
How can I let my proxy server route traffic to R2_ISP2, if this fails he should route web traffic to R1
ASKER
ASKER
I prefer to keep only 1 router and terminate both ISP at the same router.
Yes. You can do this as I described. The link in my first message
ASKER
Hi,
I don't have enough interface on my router so I cannot connect additional router.
i need to do on the same router, please can help on this.
ISP1 is a leased line
ISP2 is a DIA ( Fiber).
Thanks
I don't have enough interface on my router so I cannot connect additional router.
i need to do on the same router, please can help on this.
ISP1 is a leased line
ISP2 is a DIA ( Fiber).
Thanks
You can do ISP failover easily from the ASA using the IP SLA feature. However, it will mean you can only use one line at a time.
Here, you want to use one line for one thing and the other line for something else - simultaneously.
We can't do this as the ASA doesn't do policy-based routing.
So, if you look at the link I posted previously it shows how to achieve what you want to do. The requirement is still fulfilled in that both ISP links terminate into one router, but it means you need a router in addition to the ASA you have.
Just to add to this though, if you want to use the TMG as a proxy only you should change its role to a single-legged TMG server and disconnect the external interface.
Here, you want to use one line for one thing and the other line for something else - simultaneously.
We can't do this as the ASA doesn't do policy-based routing.
So, if you look at the link I posted previously it shows how to achieve what you want to do. The requirement is still fulfilled in that both ISP links terminate into one router, but it means you need a router in addition to the ASA you have.
Just to add to this though, if you want to use the TMG as a proxy only you should change its role to a single-legged TMG server and disconnect the external interface.
With regard to each solution being valid and to choose an affordable one, I think that as the author is using a TMG it would be safe to assume that cost is an issue here?
The ongoing cost of a BGP solution isn't cheap, and therefore probably isn't affordable, especially if the only acceptable full solution is to run your own ASN and PI addressing.
Just my opinion though...
The ongoing cost of a BGP solution isn't cheap, and therefore probably isn't affordable, especially if the only acceptable full solution is to run your own ASN and PI addressing.
Just my opinion though...
ASKER
Thanks craigbeck. You are right.
Just to clarify,
- why I would need additional router. I have already 1 router connected outside interface of ASA.
- Why would would need to remove external NIC of TMG. In my opinion I dont want want to keep Single Legged TMG.
Just to clarify,
- why I would need additional router. I have already 1 router connected outside interface of ASA.
- Why would would need to remove external NIC of TMG. In my opinion I dont want want to keep Single Legged TMG.
Well if you're only using the TMG as a proxy there's absolutely no point in keeping it as a firewall - you have the ASA for that.
What is the router which is connected to ISP1/ASA (make/model)?
What is the router which is connected to ISP1/ASA (make/model)?
ASKER
Hi,
That Router is currently our edge router and its has leased line terminated to it. Model is 1841 IP services License.
ISP Modem >> Router >> ASA
That Router is currently our edge router and its has leased line terminated to it. Model is 1841 IP services License.
ISP Modem >> Router >> ASA
Ok so it only has 2 interfaces. You'd need a switch that supports VLANs so you can use a subinterface from the router to the ASA and the secondary link via one physical interface.
ASKER
Hi,
Router has already 4port ethernet switch.
Please can you also help with configuration
Also if i need 2 use 2 different routers what the config will be ?
Thanks for your support
Router has already 4port ethernet switch.
Please can you also help with configuration
Also if i need 2 use 2 different routers what the config will be ?
Thanks for your support
Ok so you have a 4ESW in the 1841?
If so, that makes it easier.
We can use Fa0 and Fa1 as the internet links, and the 4ESW as the link to the ASA.
If you can post the 1841 config (remove passwords and public IP addresses) we can see how we can adjust the config to suit.
If so, that makes it easier.
We can use Fa0 and Fa1 as the internet links, and the 4ESW as the link to the ASA.
If you can post the 1841 config (remove passwords and public IP addresses) we can see how we can adjust the config to suit.
ASKER
Sir,
Is is just possible to use 2 different router I guess that would saved me from single point of router failure.
For ASA, we are going to have another one for Active/standby failover.
Thanks
Is is just possible to use 2 different router I guess that would saved me from single point of router failure.
For ASA, we are going to have another one for Active/standby failover.
Thanks
No you won't be able to do it with two different routers if you still want to use the ASA. The problem is that the ASA doesn't do PBR, so it has to send everything to one gateway at a time - it can't use two different gateways as a proper router can.
It sounds like you're going to need a WAN switch anyway if you are going active/standby with the ASA, so doing it with the 1841 and the ESW is the way to go.
It sounds like you're going to need a WAN switch anyway if you are going active/standby with the ASA, so doing it with the 1841 and the ESW is the way to go.
ASKER
Hi,
here is my current router config. Please let me know if you need to know anything from the config.
here is my current router config. Please let me know if you need to know anything from the config.
hostname R1_ISP1
!
boot-start-marker
boot-end-marker
!
no logging buffered
enable secret XXXXXXXXXXXXXXXXXXXXXXXXXXXx
!
ip name-server 4.2.2.2
ip name-server 8.8.8.8
!
username admin privilege XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXxx
!
!
track 1 interface Tunnel0 line-protocol
!
track 2 interface Tunnel1 line-protocol
!
no crypto isakmp ccm
!
!
!
!
interface Tunnel0
description Connection to ISP DIA
ip unnumbered FastEthernet0/0
ip tcp adjust-mss 1400
keepalive 10 3
tunnel source 192.168.X.X
tunnel destination 192.168.X,X
!
interface Tunnel1
description Connection to ISP Wireless Backup
ip unnumbered FastEthernet0/1
ip tcp adjust-mss 1452
keepalive 10 3
tunnel source 192.168.X.X
tunnel destination 192.168.X.X
!
interface FastEthernet0/0
description *Connection to ISP-DIA
ip address 192.168.X.X 255.255.255.252
!
interface FastEthernet0/1
description *Connection to ISP- Wavelan
ip address 192.168.X.X 255.255.255.252
!
interface FastEthernet0/0/0
load-interval 30
duplex full
speed 100
!
interface FastEthernet0/0/1
duplex full
speed 100
!
interface FastEthernet0/0/2
!
interface FastEthernet0/0/3
!
interface Vlan1
description $ES_LAN$
ip address 100.100.100.101 255.255.255.240
!
ip classless
ip route 0.0.0.0 0.0.0.0 192.168.X.X track 1
ip route 0.0.0.0 0.0.0.0 192.168.X.X 100 track 2
line con 0
password XXXXXXXXXXXXXXXXXXxx
login
line aux 0
line vty 0 4
password XXXXXXXXXXXXXXXXXXXXXxxx
login
!
end
Ok so you have two ISPs there already??
Are you adding a third ISP link?
Are you adding a third ISP link?
ASKER
No Actually its same ISP.
Our ISP has given us free Wireless Point to Point as backup if the cable leased line goes down.
I am going to add different ISP, just for the internet web traffic for internal proxy server.
Our ISP has given us free Wireless Point to Point as backup if the cable leased line goes down.
I am going to add different ISP, just for the internet web traffic for internal proxy server.
Ok that makes the config a bit different then. Not much, but I wish your diagram showed that!
So your ISP is using private addressing between you and them? How do you publish inbound services? Does the ISP provide one or more public IP addresses for you?
So your ISP is using private addressing between you and them? How do you publish inbound services? Does the ISP provide one or more public IP addresses for you?
ASKER
Sorry for not reflecting that on diagram.
Just to mention one thing, the IP address I used under vlan 1 interface is a publi IP and here I mentioned fictitious IP
interface Vlan1
description $ES_LAN$
ip address 100.100.100.101 255.255.255.240
yes the rest ISP using private IP addressing.
They have given a pool of Public Addresses.
Router has 2 port and 4 port ethernet switch
Route 2 ports are connected to ISP modem
and one of the ports from switch is connected to ASA.
sh ip int brief on router
Interface IP-Address OK? Method Status Prot
ocol
FastEthernet0/0 192.168.x.x YES NVRAM up up
FastEthernet0/1 192.168.x.x YES NVRAM up up
FastEthernet0/0/0 unassigned YES unset up up
FastEthernet0/0/1 unassigned YES unset down down
FastEthernet0/0/2 unassigned YES unset up down
FastEthernet0/0/3 unassigned YES unset down down
Vlan1 100.100.100.101 YES NVRAM up up
Dialer0 unassigned YES NVRAM up up
Tunnel0 192.168.X,X YES TFTP up up
Tunnel1 192.168.X.XYES TFTP up up
ASA interface
int gi0/0
nameif Outside
ip address 100.100.100.102
route outside 0.0.0.0 0.0.0.0 100.100.100.101
Just to mention one thing, the IP address I used under vlan 1 interface is a publi IP and here I mentioned fictitious IP
interface Vlan1
description $ES_LAN$
ip address 100.100.100.101 255.255.255.240
yes the rest ISP using private IP addressing.
They have given a pool of Public Addresses.
Router has 2 port and 4 port ethernet switch
Route 2 ports are connected to ISP modem
and one of the ports from switch is connected to ASA.
sh ip int brief on router
Interface IP-Address OK? Method Status Prot
ocol
FastEthernet0/0 192.168.x.x YES NVRAM up up
FastEthernet0/1 192.168.x.x YES NVRAM up up
FastEthernet0/0/0 unassigned YES unset up up
FastEthernet0/0/1 unassigned YES unset down down
FastEthernet0/0/2 unassigned YES unset up down
FastEthernet0/0/3 unassigned YES unset down down
Vlan1 100.100.100.101 YES NVRAM up up
Dialer0 unassigned YES NVRAM up up
Tunnel0 192.168.X,X YES TFTP up up
Tunnel1 192.168.X.XYES TFTP up up
ASA interface
int gi0/0
nameif Outside
ip address 100.100.100.102
route outside 0.0.0.0 0.0.0.0 100.100.100.101
Ok so is there really public addressing on the outside interface of the ASA?
ASKER
Yes.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi,
Frankly I would keep the same running scneario instead of using TMG ISP-R.
No way to to by using different route for ISP :(
Can you help with the config I am ready to face the challenges.
Thanks
Frankly I would keep the same running scneario instead of using TMG ISP-R.
No way to to by using different route for ISP :(
Can you help with the config I am ready to face the challenges.
Thanks
ASKER
I can also manage any downtime.
Running ISP-R would still keep the same router scenario, it would just route internet traffic out of the TMG directly, rather than via the ASA/router.
Of course, if you really want to I can try to help, but it could cause issues with what you already have going on in terms of inbound services as we'd need to run NAT at the routers and move your public IP addressing away from the ASA.
Of course, if you really want to I can try to help, but it could cause issues with what you already have going on in terms of inbound services as we'd need to run NAT at the routers and move your public IP addressing away from the ASA.
ASKER
Sir,
I would highly appreciate your help
Can post sample config so I can just emulate on emulator like GNS3.
Thanks.
I would highly appreciate your help
Can post sample config so I can just emulate on emulator like GNS3.
Thanks.
As a basic outline, something like this would work...
vlan 2
!
int fa0/0/3
description Link to ISP2
switchport mode access
switchport access vlan 2
no shutdown
!
int vlan 2
ip address a.b.c.d 255.255.x.y
!
int vlan 1
ip policy route-map Web_Traffic_Map
!
ip access-list extended Web_Traffic
permit tcp host <ASA_WAN_IP> any eq http
permit tcp host <ASA_WAN_IP> any eq https
!
route-map Web_Traffic_Map permit 10
match ip address Web_Traffic
set ip next-hop <ISP2 Gateway>
!ASKER
Sir,
If I make TMG as Single Legged, can we make this scenario easier.
Thanks
If I make TMG as Single Legged, can we make this scenario easier.
Thanks
No because you're not using the TMG as a firewall anyway.
As I said it would be simpler to leave the router setup as it is and use ISP-R on the TMG. You'd need to add a third NIC to the TMG though.
The main problem here is the Tunnel interfaces on the router. They're there for a reason (probably to allow certain types of traffic over your ISP's link) so I'd not want to break that.
You may be able to remove the public IP addressing completely from the ASA and use routing instead of NAT, but you'd still need to NAT at the router and that's a complete unknown as you've not provided your ASA config.
As I said it would be simpler to leave the router setup as it is and use ISP-R on the TMG. You'd need to add a third NIC to the TMG though.
The main problem here is the Tunnel interfaces on the router. They're there for a reason (probably to allow certain types of traffic over your ISP's link) so I'd not want to break that.
You may be able to remove the public IP addressing completely from the ASA and use routing instead of NAT, but you'd still need to NAT at the router and that's a complete unknown as you've not provided your ASA config.
ASKER
I got have some idea.
I dont if this will work
I have 4 interfaces on ASA.
Outside
Inside
DMZ
TMG ( for back to back)
- If I can tell the Core Switch to route the internal IP of TMG to next-hop that could be another sub-interface of ASA inside interface.
- Connect the ISP2 on ASA ( but the problem I dont have another interface on ASA)
- Adjust NAT and ACL of TMG server to public IP address of ISP2.
How about that ?
I dont if this will work
I have 4 interfaces on ASA.
Outside
Inside
DMZ
TMG ( for back to back)
- If I can tell the Core Switch to route the internal IP of TMG to next-hop that could be another sub-interface of ASA inside interface.
- Connect the ISP2 on ASA ( but the problem I dont have another interface on ASA)
- Adjust NAT and ACL of TMG server to public IP address of ISP2.
How about that ?
ASKER
How about if we used different Routers for ISP 1 and ISP2 ?
That won't work.
You can't connect the 2nd ISP link to the ASA directly as it won't do policy-based routing.
You can't tell the core to route the internal leg of the TMG to the next-hop as that will just bypass your proxy.
You can't adjust NAT as the 2nd ISPs IP addresses can't be added to the ASA on the same interface as ISP1.
You can't connect the 2nd ISP link to the ASA directly as it won't do policy-based routing.
You can't tell the core to route the internal leg of the TMG to the next-hop as that will just bypass your proxy.
You can't adjust NAT as the 2nd ISPs IP addresses can't be added to the ASA on the same interface as ISP1.
If you use different routers for ISP1 and ISP2 it won't work - again, the ASA doesn't do PBR so it can't decide by itself which router to send the traffic to. This is what the router has to do, hence connecting both ISP links to the router and not just to the ASA.
ASKER
Thanks.
Just a though ,what if we put a router behind ASA
Just a though ,what if we put a router behind ASA
ASKER
Oops !! I already have L3 switch behind ASA.
No it has to be on the WAN side of the ASA. If you were to use an internal router that would be the TMG :-)
ASKER
I came across reading the PBR will be supported on ASA with 9.x version.
That's true... to a point. It's not true PBR though.
This is an interesting read... (the last section), but I don't think it would work as you can only install one route in the routing table for default traffic.
You could try it in GNS if you have an ASA image.
This is an interesting read... (the last section), but I don't think it would work as you can only install one route in the routing table for default traffic.
You could try it in GNS if you have an ASA image.
ASKER
Hi,
Which one you are talking about ?
Which one you are talking about ?
One of the more interesting things that some desire to achieve with policy based routing in IOS is routing by traffic type. For example, traffic to port 80 and 443 might go to isp2. All other traffic could go to isp1. This can be accomplished in the ASA by using a configuration similar to the following.
//delete the previous destination translation
ASA(config)#no static (isp2,inside) 128.0.0.0 128.0.0.0 netmask 128.0.0.0
//create destination translations that include tcp/udp ports
static (isp2,inside) tcp 0.0.0.0 80 0.0.0.0 80 netmask 0.0.0.0
static (isp2,inside) tcp 0.0.0.0 443 0.0.0.0 443 netmask 0.0.0.0
Unlike IOS based routers, the ASA does not support policy based routing. While this certainly creates limitations, there are options that will allow an administrator to achieve some of the same goals. Prior to implementing destination translation or destination translation exemptions, it is very important to understand the proxy arp behavior on the ASA. When a destination translation or exemption exists, outbound packets use the entry to determine the egress interface. Once the egress interface is chosen, the ASA does a route lookup specific to the chosen interface. By understanding these interactions, an administrator can use destination translation exemptions to steer packets to the desired interface. This can alleviate some of the limitations found in the ASA.
ASKER
Hi,
Just to add something.
If I add L3 Switch Switch between ASA and Router and let switch do PBR ? How about that
Just to add something.
If I add L3 Switch Switch between ASA and Router and let switch do PBR ? How about that
ASKER
Great Article
http://www.packetu.com/2011/11/28/egress-interface-selection-on-the-cisco-asa/
I can do this only the thing is that it will give be failback option.
But I have another problem I don't free Interface on ASA. Is there any way to overcome this.
Thanks
http://www.packetu.com/2011/11/28/egress-interface-selection-on-the-cisco-asa/
I can do this only the thing is that it will give be failback option.
But I have another problem I don't free Interface on ASA. Is there any way to overcome this.
Thanks
The L3 switch method wouldn't work - you'd still have the same issue with having to move the public IP addresses up to the L3 switch and the problem with that is that the L3 switch won't do NAT.
ASKER
Hi,
Just a thought.
- Connect the Router to L3 Core Switch.
- Route the TMG internal IP to Router.
Just a thought.
- Connect the Router to L3 Core Switch.
- Route the TMG internal IP to Router.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi craigbeck,
Happy New Year
Sorry for the delay.
I didn't got your point " Reconfigure the TMG as a proxy only, and use policy routing at the external router."
Thanks
Happy New Year
Sorry for the delay.
I didn't got your point " Reconfigure the TMG as a proxy only, and use policy routing at the external router."
Thanks
Hi Samir,
Happy new year to you too :-)
What I mean is, use the TMG toolbox to configure the TMG as a single-legged proxy. This would mean the TMG would be just as a normal server on the network. It would use the ASA as its default gateway. When HTTP(S) traffic passes through the ASA toward the external router which has both ISP connections it would use policy-based routing to send HTTP(S) traffic to ISP2.
Happy new year to you too :-)
What I mean is, use the TMG toolbox to configure the TMG as a single-legged proxy. This would mean the TMG would be just as a normal server on the network. It would use the ASA as its default gateway. When HTTP(S) traffic passes through the ASA toward the external router which has both ISP connections it would use policy-based routing to send HTTP(S) traffic to ISP2.
ASKER
Hi,
Thanks.
I was thinking something similar.
- Connect ISP2 to ASA
- Make the TMG as single leg.
- Point the TMG gateway to ASA.
- NAT the TMG IP to ISP2 interface
- Add route on ASA
- route outside 0.0.0.0 0.0.0.0 ISP2 metric 2
How about that ?
Thanks.
I was thinking something similar.
- Connect ISP2 to ASA
- Make the TMG as single leg.
- Point the TMG gateway to ASA.
- NAT the TMG IP to ISP2 interface
- Add route on ASA
- route outside 0.0.0.0 0.0.0.0 ISP2 metric 2
How about that ?
ASKER
I guess I will go with TMG ISP-R feature.
3 Interfaces
1 ASA Back to Back
2 ISP2 Router
3 internal.
Please can you provide me step by step guide to configure it.
Thanks
3 Interfaces
1 ASA Back to Back
2 ISP2 Router
3 internal.
Please can you provide me step by step guide to configure it.
Thanks
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi,
I have open a new ticket just to clarify some issues with DNS. Please can you have a look.
I will close this ticket for now.
https://www.experts-exchange.com/questions/28330829/TMG-2010-ISP-Redudancy.html?anchorAnswerId=39757220#a39757220
Thanks
I have open a new ticket just to clarify some issues with DNS. Please can you have a look.
I will close this ticket for now.
https://www.experts-exchange.com/questions/28330829/TMG-2010-ISP-Redudancy.html?anchorAnswerId=39757220#a39757220
Thanks
ASKER
Thanks craigbeck. for your great help and support I greatly appreciate that.
Thanks once again.
Thanks once again.
Also you can configure dynamic routing with your ISPs if they agree and make one prior to another, configure NAT for Proxy for each destination.
And at last third option is to configure static default routes to ISPs with object tracking. Here is a link http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_configuration_example09186a00806e880b.shtml#cli