llesane
asked on
Bitlocker TPM Lockout
Iam having issues with initializing the TPM. when I try and manually create the password it give me an error message saying initializing the tpm security hardware access is denied the tpm defending against dictionary attacks and it is in a timeout period. HOw do I get out of the time out period? There is no other option except for initialize TPM.
Thanks,
Thanks,
ASKER
That didnt work. I cleared then activated becasue it defaults to deactivate. it does not allow me to initialize it still give me that error msg.
Check this article and see if it helps: http://technet.microsoft.c
ASKER
Thanks, but that doesnt not help. I only have the initialize TPM option. The other options are greyed out.
Okay need more information then, What is the PC vendor Make/Model and what Operating System?
ASKER
With this message, I get the error cannot take ownership.
ASKER
Dell latitude E6420 Windows 7 64 bit which is on a domain
Are you getting this error? 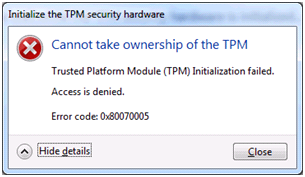
If so see this TechNet blog post http://blogs.technet.com/b

If so see this TechNet blog post http://blogs.technet.com/b
ASKER
From the forum, pls see
You may also want to check out Dell CCTK in their main site
Best Practices for Remote Enabling of Trusted Platform Modules (TPM) on Dell Business Client Systems
http://media.community.dell.com/en/dtc/attach/tpm_best_practices%20-%20web%20post.zip
TPM for Dell Business Clients Using Self Contained Executable
http://media.community.dell.com/en/dtc/attach/enabling_tpm_with_cctk_sce.pdf
MBAM has been able to take ownership consistently after these steps. These have have worked so far for 6400, 4300, 6410 and 6320 models in our environment.
1. If the TPM is on, turn it off in the BIOS. (uncheck the TPM security box) Power off.
2. Enable the TPM and power off.
3. Check the BIOS and confirm TPM Security is checked and disabled is ticked.
You may also want to check out Dell CCTK in their main site
Best Practices for Remote Enabling of Trusted Platform Modules (TPM) on Dell Business Client Systems
http://media.community.dell.com/en/dtc/attach/tpm_best_practices%20-%20web%20post.zip
TPM for Dell Business Clients Using Self Contained Executable
http://media.community.dell.com/en/dtc/attach/enabling_tpm_with_cctk_sce.pdf
ASKER
Just to confirm once I do this; I will then activate the TPM and continue with initializing the TPM in the OS?
ASKER
Just an FYI this still doesn't work for me. After activating the TPM again in the BIOS. Trying it without activating now.
Likely, the TPM is locked out due to too many incorrect attempts at entering the owner authorization or other authorization values. The TPM will lock out for the entire time-out period and additional attempts at resetting the lock will fail. You need to have the TPM owner password so that you can reset the lockout. Pls see
http://trekker.net/archives/how-do-i-fix-the-tpm-is-defending-against-dictionary-attacks-and-is-in-a-time-out-period/
More details from MSDN (Reset the TPM Lockout)
http://technet.microsoft.com/en-us/library/dd851452.aspx
Btw, you may want to catch the CCTK in attached pdf (also in the prev post link)
http://trekker.net/archives/how-do-i-fix-the-tpm-is-defending-against-dictionary-attacks-and-is-in-a-time-out-period/
More details from MSDN (Reset the TPM Lockout)
http://technet.microsoft.com/en-us/library/dd851452.aspx
Btw, you may want to catch the CCTK in attached pdf (also in the prev post link)
PREREQUISITESTPM-Best-Practices.pdf
1. TPM must be present.
2. Trusted Platform Module (TPM) must not be currently owned
3. TPM must be in deactivated state
4. BIOS Administrator Password has to be set
Dell Client Configuration Toolkit (CCTK) is a command-line-driven utility that can be used to configure BIOS settings on OptiPlexTM, LatitudeTM, and Dell PrecisionTM systems. Using CCTK you can configure the BIOS administrator password and the TPM enumeration and TPM activation states in a Pre-OS and Post-OS environment. For step by step instructions, see the APPENDIX.
APPENDIX
CCTK command line step by step:
Setup BIOS password: cctk --setuppwd=<New-password>
TPM enable: cctk --tpm=on --valsetuppwd=<BIOS password>
TPM activate: cctk --tpmactivation=activate --valsetuppwd=<BIOS password>
TPM check: cctk --tpm --tpmactivation
ASKER
Thank you for that information but like I explained previously there is not an option to clear TPM in the action panel in windows. It only allows me to initialize the TPM. But when I try it gives me the above error. How can I unlock the TPM from the lock out period? How long does the lock out period last? Could I decrypt and the encrypt the drive again? Would it be best to reimage the drive? Maybe I'll try the CCTK option you provided. Suggestions?
It is more of reset ("Reset TPM Lockout") than to clear ("Clear TPM") tpm from the TPM Management (tpm.msc) snap-in. So if it is really not seeing either one, I do suggest "Initialize TPM" steps to be reviewed.
http://technet.microsoft.com/en-us/library/cc753140.aspx
In all, the TPM should be in can be in one of the following states and we need it to be the last state to proceed to use bitlocker or in specific for the tpm actions. The owner password is to be set
-Unowned and turned off
-Unowned and turned on
-Owned but turned off
-Owned and turned on
For the TPM ownership status, this info is stored in below registry values. You may want to check out just to confirm state.
DWORD: OSManagedAuthLevel in HKEY_LOCAL_MACHINE\SOFTWAR
e.g. 0-None, 2-Delegated, 4-Full
As for the lockout info, that varies from the manufacturer but the industry standards specify that the user is allowed at least one attempt to reset the TPM lockout by using the owner authorization value, even when the TPM is locked out. If the wrong value is used when attempting to reset the TPM lockout, on subsequent attempts to enter the owner authorization value, the TPM may respond as if the correct value is incorrect or respond that the TPM is locked out.
But there is actually Windows GPO defaults value to control the lockout parameters
-summary @ http://technet.microsoft.com/en-us/library/dn466535.aspx
-details of gpo @ http://technet.microsoft.com/en-us/library/jj679889.aspx
e.g. Standard User Lockout Duration = default value of 480 minutes (8 hours) is used
( If the number of TPM commands with an authorization failure within the lockout duration equals a threshold, a standard user is prevented from sending commands that require authorization to the TPM.)
e.g. Standard User Individual Lockout Threshold = default value of 4 is used
( If the number of authorization failures for the user within the duration that is set for the Standard User Lockout Duration policy setting equals this value, the standard user is prevented from sending commands that require authorization to the Trusted Platform Module (TPM).)
e.g. Standard User Total Lockout Threshold = default value of 9 is used
(If the total number of authorization failures for all standard users within the duration that is set for the Standard User Lockout Duration policy equals this value, all standard users are prevented from sending commands that require authorization to the Trusted Platform Module (TPM).)
The CCTK is good but it go back to ownership and initialised state which the PDF also link back to Microsoft websites e.g.
http://technet.microsoft.com/en-us/library/cc749022(WS.10).aspx
http://technet.microsoft.com/en-us/library/cc753140.aspx
In all, the TPM should be in can be in one of the following states and we need it to be the last state to proceed to use bitlocker or in specific for the tpm actions. The owner password is to be set
-Unowned and turned off
-Unowned and turned on
-Owned but turned off
-Owned and turned on
For the TPM ownership status, this info is stored in below registry values. You may want to check out just to confirm state.
DWORD: OSManagedAuthLevel in HKEY_LOCAL_MACHINE\SOFTWAR
e.g. 0-None, 2-Delegated, 4-Full
As for the lockout info, that varies from the manufacturer but the industry standards specify that the user is allowed at least one attempt to reset the TPM lockout by using the owner authorization value, even when the TPM is locked out. If the wrong value is used when attempting to reset the TPM lockout, on subsequent attempts to enter the owner authorization value, the TPM may respond as if the correct value is incorrect or respond that the TPM is locked out.
But there is actually Windows GPO defaults value to control the lockout parameters
-summary @ http://technet.microsoft.com/en-us/library/dn466535.aspx
-details of gpo @ http://technet.microsoft.com/en-us/library/jj679889.aspx
e.g. Standard User Lockout Duration = default value of 480 minutes (8 hours) is used
( If the number of TPM commands with an authorization failure within the lockout duration equals a threshold, a standard user is prevented from sending commands that require authorization to the TPM.)
e.g. Standard User Individual Lockout Threshold = default value of 4 is used
( If the number of authorization failures for the user within the duration that is set for the Standard User Lockout Duration policy setting equals this value, the standard user is prevented from sending commands that require authorization to the Trusted Platform Module (TPM).)
e.g. Standard User Total Lockout Threshold = default value of 9 is used
(If the total number of authorization failures for all standard users within the duration that is set for the Standard User Lockout Duration policy equals this value, all standard users are prevented from sending commands that require authorization to the Trusted Platform Module (TPM).)
The CCTK is good but it go back to ownership and initialised state which the PDF also link back to Microsoft websites e.g.
http://technet.microsoft.com/en-us/library/cc749022(WS.10).aspx
Also Microsoft Technet also shared so it is advised to check back with the manufacturer of Your TPM and request support from manufacturer.
e.g. Most manufacturers use the PIN authentication failure count to exponentially increase lockout time to the PIN interface. However, each manufacturer has different policies regarding when and how the failure counter is decreased or reset.
There is Bitlocker's Manage-bde.exe which serve more like CLI
http://technet.microsoft.com/en-us/library/dd875513(v=ws.10).aspx
e.g. -autounlock - Syntax
manage-bde -autounlock {-enable | -disable | -ClearAllKeys} Volume [-ComputerName Name]
http://technet.microsoft.com/en-us/library/dd894351(WS.10).aspx
e.g. Most manufacturers use the PIN authentication failure count to exponentially increase lockout time to the PIN interface. However, each manufacturer has different policies regarding when and how the failure counter is decreased or reset.
There is Bitlocker's Manage-bde.exe which serve more like CLI
http://technet.microsoft.com/en-us/library/dd875513(v=ws.10).aspx
e.g. -autounlock - Syntax
manage-bde -autounlock {-enable | -disable | -ClearAllKeys} Volume [-ComputerName Name]
http://technet.microsoft.com/en-us/library/dd894351(WS.10).aspx
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
thanks for sharing
ASKER
None of the solutions got me to the point I needed.
If you don't want to use TPM then in the BIOS TPM settings turn off TPM