HP Procurve 5406zl Default Gateway / Default Routing
Hi All,
I need some help finishing the config of my core switch.
I have HP 2920s that uplink to it.
My firewall is 10.1.100.10
I've setup a VLAN 100 for it with an ip address of 10.1.100.1
I've tried adding a Default Gateway to the 5406 and although I can ping external addresses from the 5406, servers on VLAN10 cannot.
I have untagged port E1 which the firewall patches into.
Also what do I need to do on the 2920s are regards default gateways?
I need some help finishing the config of my core switch.
I have HP 2920s that uplink to it.
My firewall is 10.1.100.10
I've setup a VLAN 100 for it with an ip address of 10.1.100.1
I've tried adding a Default Gateway to the 5406 and although I can ping external addresses from the 5406, servers on VLAN10 cannot.
I have untagged port E1 which the firewall patches into.
Also what do I need to do on the 2920s are regards default gateways?
hostname "5406-Core"
module 1 type j9538a
module 2 type j9538a
module 3 type j9546a
module 4 type j9546a
module 5 type j9550a
ip routing
interface A1
name "Uplink to Admin1"
exit
interface A2
name "Uplink to Admin2"
exit
interface A3
name "Uplink to Admin3"
exit
interface B7
name "Uplink to Admin4"
exit
interface B8
name "Uplink to Admin5"
exit
interface E1
name "Uplink to Firewall"
exit
snmp-server community "public" unrestricted
vlan 1
name "DEFAULT_VLAN"
no untagged A1-A3,B7-B8,E1-E13
untagged A4-A8,B1-B6,C1-C8,D1-D8,E14-E24
ip address dhcp-bootp
exit
vlan 10
name "Servers"
untagged E2-E13
ip address 10.1.10.1 255.255.255.0
exit
vlan 15
name "iSCSI_A"
ip address 10.1.15.1 255.255.255.0
exit
vlan 16
name "iSCSI_B"
ip address 10.1.16.1 255.255.255.0
exit
vlan 17
name "vMotion"
ip address 10.1.17.1 255.255.255.0
exit
vlan 18
name "vHA"
ip address 10.1.18.1 255.255.255.0
exit
vlan 20
name "Workstations"
tagged A1-A3,B7-B8
ip address 10.1.20.1 255.255.255.0
ip helper-address 10.1.10.10
ip helper-address 10.1.10.11
exit
vlan 30
name "Printers"
tagged A1-A3,B7-B8
ip address 10.1.30.1 255.255.255.0
ip helper-address 10.1.10.10
ip helper-address 10.1.10.11
exit
vlan 40
name "Private_WiFi"
tagged A1-A3,B7-B8
ip address 10.1.40.1 255.255.255.0
ip helper-address 10.1.10.10
ip helper-address 10.1.10.11
exit
vlan 41
name "Warehouse_WiFi"
tagged A1-A3,B7-B8
ip address 10.1.41.1 255.255.255.0
ip helper-address 10.1.10.10
ip helper-address 10.1.10.11
exit
vlan 42
name "Public_WiFi"
tagged A1-A3,B7-B8
ip address 10.1.42.1 255.255.255.0
ip helper-address 10.1.10.10
ip helper-address 10.1.10.11
exit
vlan 99
name "Switch_Management"
tagged A1-A3,B7-B8
ip address 10.1.99.1 255.255.255.0
exit
vlan 100
name "Firewall_In"
untagged E1
ip address 10.1.100.1 255.255.255.0
exit
spanning-tree
spanning-tree priority 0 force-version rstp-operation
no tftp server
no autorun
no dhcp config-file-update
no dhcp image-file-update
password manager
---
hostname "Admin1"
module 1 type j9726a
dhcp-snooping
dhcp-snooping authorized-server 10.1.10.10
dhcp-snooping authorized-server 10.1.10.11
dhcp-snooping vlan 20 30 40-42
telnet-server listen data
web-management listen data
ip default-gateway 10.1.99.1
ip ssh listen data
interface A1
dhcp-snooping trust
exit
snmp-server community "public" unrestricted
snmp-server listen data
snmp-server contact "Me" location "Admin Office"
oobm
disable
ip address dhcp-bootp
exit
vlan 1
name "DEFAULT_VLAN"
no untagged 1-24
untagged A1-A2,B1-B2
no ip address
exit
vlan 20
name "Workstations"
untagged 1-20
tagged A1
no ip address
exit
vlan 30
name "Printers"
untagged 21-24
tagged A1
no ip address
exit
vlan 40
name "Private_WiFi"
tagged A1
no ip address
exit
vlan 41
name "Warehouse_WiFi"
tagged A1
no ip address
exit
vlan 42
name "Public_WiFi"
tagged A1
no ip address
exit
vlan 99
name "Switch_Management"
tagged A1
ip address 10.1.99.10 255.255.255.0
exit
spanning-tree
spanning-tree 1 admin-edge-port
spanning-tree 1 bpdu-protection
spanning-tree 2 admin-edge-port
spanning-tree 2 bpdu-protection
spanning-tree 3 admin-edge-port
spanning-tree 3 bpdu-protection
spanning-tree 4 admin-edge-port
spanning-tree 4 bpdu-protection
spanning-tree 5 admin-edge-port
spanning-tree 5 bpdu-protection
spanning-tree 6 admin-edge-port
spanning-tree 6 bpdu-protection
spanning-tree 7 admin-edge-port
spanning-tree 7 bpdu-protection
spanning-tree 8 admin-edge-port
spanning-tree 8 bpdu-protection
spanning-tree 9 admin-edge-port
spanning-tree 9 bpdu-protection
spanning-tree 10 admin-edge-port
spanning-tree 10 bpdu-protection
spanning-tree 11 admin-edge-port
spanning-tree 11 bpdu-protection
spanning-tree 12 admin-edge-port
spanning-tree 12 bpdu-protection
spanning-tree 13 admin-edge-port
spanning-tree 13 bpdu-protection
spanning-tree 14 admin-edge-port
spanning-tree 14 bpdu-protection
spanning-tree 15 admin-edge-port
spanning-tree 15 bpdu-protection
spanning-tree 16 admin-edge-port
spanning-tree 16 bpdu-protection
spanning-tree 17 admin-edge-port
spanning-tree 17 bpdu-protection
spanning-tree 18 admin-edge-port
spanning-tree 18 bpdu-protection
spanning-tree 19 admin-edge-port
spanning-tree 19 bpdu-protection
spanning-tree 20 admin-edge-port
spanning-tree 20 bpdu-protection
spanning-tree 21 admin-edge-port
spanning-tree 21 bpdu-protection
spanning-tree 22 admin-edge-port
spanning-tree 22 bpdu-protection
spanning-tree 23 admin-edge-port
spanning-tree 23 bpdu-protection
spanning-tree 24 admin-edge-port
spanning-tree 24 bpdu-protection
spanning-tree instance ist A1 path-cost 2000
spanning-tree force-version rstp-operation
tftp server listen data
password managerASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
No. Your 2920 isn't doing any routing.
ASKER
So just ip route 0.0.0.0 0.0.0.0 10.1.100.10 on the "core" 5406
Yep.
ASKER
So I've added "ip route 0.0.0.0 0.0.0.0 10.1.100.10" to the 5406.
The 5406 can ping google on 8.8.8.8, but servers on VLAN10 cannot ping 8.8.8.8
Servers on VLAN10 can ping 10.1.100.1, but not 10.1.100.10 - the firewall.
The 5406 can ping google on 8.8.8.8, but servers on VLAN10 cannot ping 8.8.8.8
Servers on VLAN10 can ping 10.1.100.1, but not 10.1.100.10 - the firewall.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
As far as I can see, yes. That looks right.
ASKER
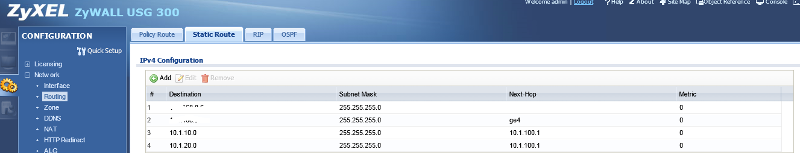
So destination is VLAN subnet identifier, next hop is firewall VLAN gateway.
Should I put the following in the VLANS.
ip igmp
ip rip 10.1.10.1
vlan 10
name "Servers"
untagged E2-E13
ip address 10.1.10.1 255.255.255.0
ip igmp
ip rip 10.1.10.1
Should I put the following in the VLANS.
ip igmp
ip rip 10.1.10.1
vlan 10
name "Servers"
untagged E2-E13
ip address 10.1.10.1 255.255.255.0
ip igmp
ip rip 10.1.10.1
You can either create static routes on the firewall or run a routing protocol on the 5400 and firewall.
Either way works fine.
Either way works fine.
ASKER
If I create static routes on the firewall do I still need ip igmp and ip rip on the vlans?
No. And you don't need IGMP to run RIP.
ASKER