Cisco ASA Question
I wanted to ask you the following:
How can you permit traffic to specific host on another interface if you have configured deny all traffic from one interface to another meaning between two network /24 .
What is the exmpet rule? Is it necessary to setup between two Site to site vp's?
Does anyone share with me ebbok on Cisco ASA preferable ASDM
Thank you
My ASA is 5512x
How can you permit traffic to specific host on another interface if you have configured deny all traffic from one interface to another meaning between two network /24 .
What is the exmpet rule? Is it necessary to setup between two Site to site vp's?
Does anyone share with me ebbok on Cisco ASA preferable ASDM
Thank you
My ASA is 5512x
ASKER
I have done it I believe and it doenst work.,....
How can I enable traffic from an another internface to outside does it need NAt rule or Access rule
thank you
How can I enable traffic from an another internface to outside does it need NAt rule or Access rule
thank you
ASKER
I have ASA 9.0 ASDM 7
It actually needs both
1. NAT rule - purpose of this is that from an inside interface (having internal private IP) it needs to be NATed (hidden) to an external public IP which is routable within the internet. In this case the outside interface has the public IP address and internal traffic going to the internet gets NATed to the outside interface IP.
2. ACL rule - this is needed for the firewall to identify which traffic is allowed/denied INCOMING (usually) to the interface where it is applied to.
3. default route - if you have not done so, you'll need to specify a default route pointing to your internet router
those are the three basic things you need.
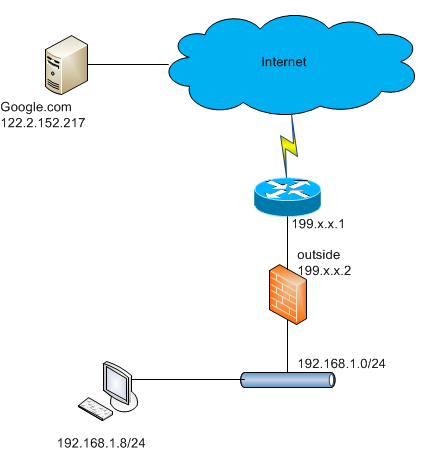
now consider the following example below:
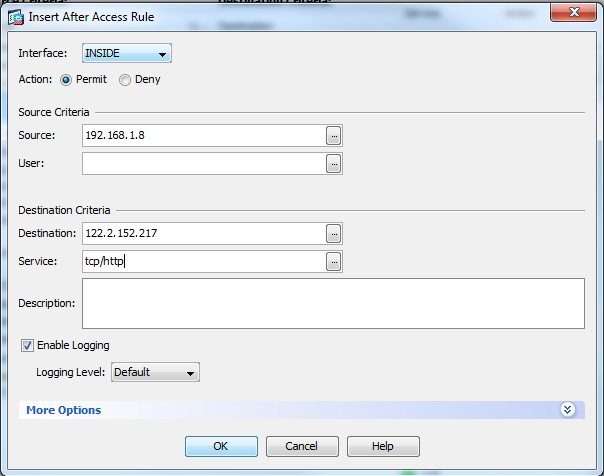
 add permissive ACL
add permissive ACL
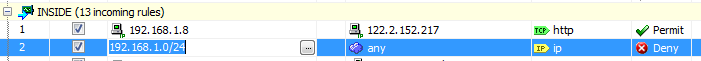 the permit rule is on top of the deny rule
the permit rule is on top of the deny rule
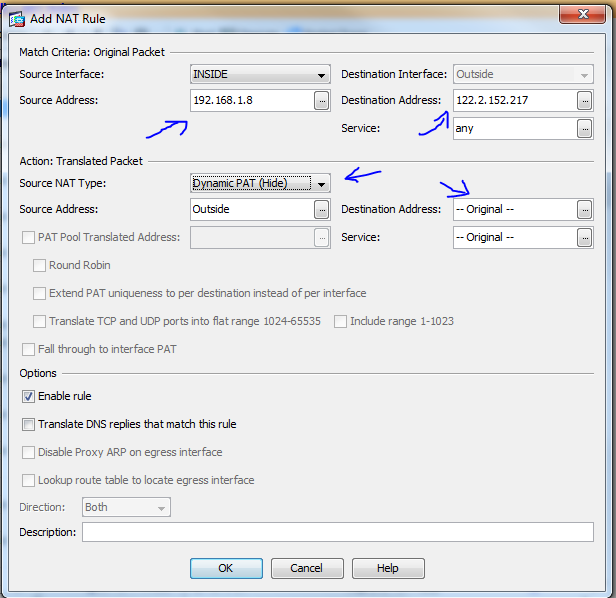
add NAT
let me know if this clarifies things more.
hope this helps!
1. NAT rule - purpose of this is that from an inside interface (having internal private IP) it needs to be NATed (hidden) to an external public IP which is routable within the internet. In this case the outside interface has the public IP address and internal traffic going to the internet gets NATed to the outside interface IP.
2. ACL rule - this is needed for the firewall to identify which traffic is allowed/denied INCOMING (usually) to the interface where it is applied to.
3. default route - if you have not done so, you'll need to specify a default route pointing to your internet router
those are the three basic things you need.
now consider the following example below:
add NAT
for source 192.168.1.8, destination 122.2.152.217
NAT the source IP to the outside interface IP, while keeping the destination the same(122.2.152.217)
let me know if this clarifies things more.
hope this helps!
ASKER
Thank very helpfull information...Will do and let u know....what shall I do to permit Traffic from one interface to another? Shall I need both?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
as example you can use the following ASA ASDM configuration guide from cisco
http://www.cisco.com/en/US/docs/security/asa/asa91/asdm71/firewall/asdm_71_firewall.pdf
you can search for other version configuration guides by searching for "ASA ASDM configuration Guide"
by default there is an implicit deny on end of each interface access rule, but in case you placed a deny statement, you can place a rule on top of that deny statement to allow a specific IP before denying anything else.
shown in the figure, you can add ACL after and highlighted ACL, or you can move the created ACL up and down via the arrow keys pointed here. just make sure your permit statement is ahead of the deny statement