certificate choice for machine based authentication
Hi,
can any one tell me how to make a certificate the preferred choice for machine based authentication?
I have laptops with 3 or 4 client certs and I need to insure which one is chosen for authentication to the wireless network.
I have read about "weight" but I cant see how to set this up or check it?
Cheers
can any one tell me how to make a certificate the preferred choice for machine based authentication?
I have laptops with 3 or 4 client certs and I need to insure which one is chosen for authentication to the wireless network.
I have read about "weight" but I cant see how to set this up or check it?
Cheers
ASKER
umm no i mean computer certs :)
Before my time, but ig you go on our CA, it has about 6 computer certs templates that are all set to autoenroll. So a PC gets turned on and it gets them all.
Most of them are the same apart from the SAN name, but this is where the issue is, I need the principle name to be complete and this is not the case for all of them :(
yes its bad practice and should not be so, but sadly it is legacy and not something I can change over night.
Before my time, but ig you go on our CA, it has about 6 computer certs templates that are all set to autoenroll. So a PC gets turned on and it gets them all.
Most of them are the same apart from the SAN name, but this is where the issue is, I need the principle name to be complete and this is not the case for all of them :(
yes its bad practice and should not be so, but sadly it is legacy and not something I can change over night.
If the certificates are autoenrolled with GPO and the autoenrollment is set on default domain policy, you can revoke certificates - then they're removed from computers
And then remove all "bad" certificate templates from CA - create a new working template (or use computer ) and set properties for autoenrollment. In sercurity for certificate template, only let a specific group be able to auto enroll, and then add just some test computers to that group, and test certs ... when all are good - add more computers to group - enroll and connect :)
And then remove all "bad" certificate templates from CA - create a new working template (or use computer ) and set properties for autoenrollment. In sercurity for certificate template, only let a specific group be able to auto enroll, and then add just some test computers to that group, and test certs ... when all are good - add more computers to group - enroll and connect :)
ASKER
Yer that would be how to do it, but the issue is going through the hundreds of templates that people have created over the years and working out what is needed and what is not.
Unfortunately our set up is never as simple as "one size fits all", we don't control the users devices as much as we would like,Some so while the process is simple we have to be careful to not upset people. Some applications we have require specific machine certs to be installed that are not linked to the Domain CA and used to authenticate against a specifics workstation or server that is not on the domain. And a few are even used for licencing purposes.
Now i am sure that 99.9% could be resolved, but working in a science institute I know that you have to take each PC individual when you make changes like this. I think this is why Windows 8 allows you to have mutiply Computer certs and manage them more easly.
Unfortunately our set up is never as simple as "one size fits all", we don't control the users devices as much as we would like,Some so while the process is simple we have to be careful to not upset people. Some applications we have require specific machine certs to be installed that are not linked to the Domain CA and used to authenticate against a specifics workstation or server that is not on the domain. And a few are even used for licencing purposes.
Now i am sure that 99.9% could be resolved, but working in a science institute I know that you have to take each PC individual when you make changes like this. I think this is why Windows 8 allows you to have mutiply Computer certs and manage them more easly.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Hmmm, you're thinking too far ahead, Jakob :-)
ASKER
craigbeck, oh is did not realise you could do that, I will have to look in to how to do this on CISCO ISE radius.
I basically want to use the cert that has
"principle name contains @company.ac.uk"
Sounds promicing
I basically want to use the cert that has
"principle name contains @company.ac.uk"
Sounds promicing
@craigbeck ---- well, that's was all I had to offer :-)
Ah good luck with that in ISE... ;-)
You can do it but you might need to create a new Certificate Authentication Profile and a new ID store sequence, then add that sequence to the authentication rule.
I'm not saying these screenshots are exactly what you'll need but they'll help point you in the right direction...
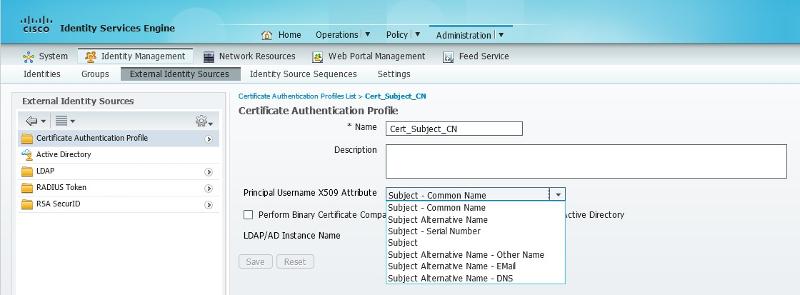
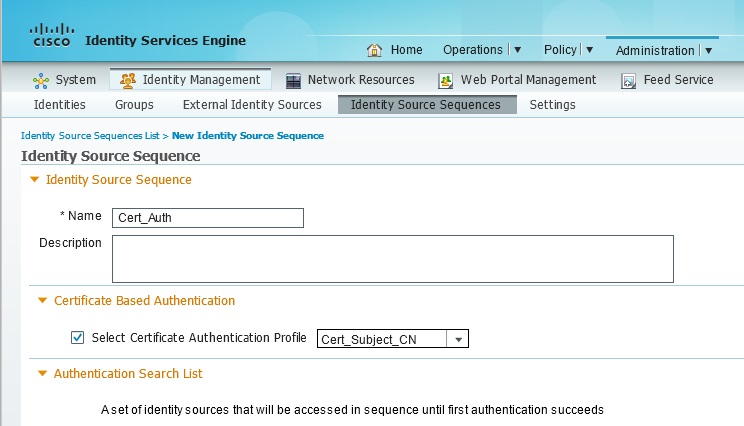
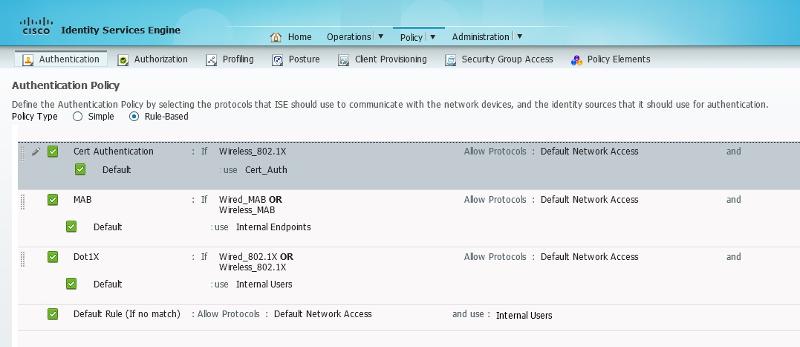
You can do it but you might need to create a new Certificate Authentication Profile and a new ID store sequence, then add that sequence to the authentication rule.
I'm not saying these screenshots are exactly what you'll need but they'll help point you in the right direction...



ASKER
You seem to know ISE, so may be you can answer this.
My authentication profile says,
If method is TLS use cert store other wise use AD.
So my machine set up to use certificate authenticates fine.
But my authorization profile tries to match an AD group but returns that machine failed AD authentication? Even though if I set it to use peep/ms-chap it works fine.
My authentication profile says,
If method is TLS use cert store other wise use AD.
So my machine set up to use certificate authenticates fine.
But my authorization profile tries to match an AD group but returns that machine failed AD authentication? Even though if I set it to use peep/ms-chap it works fine.
The authorisation profile just sets access based on what the ISE sees in the RADIUS packet, so once authentication is passed you should be able to see what you need to configure based on the authentication result.
To simplify, use a permit all authorisation rule first, then authenticate and check the log in ISE. hen pick out certain attributes to create your authorisation rule and set required permissions on that rule.
To simplify, use a permit all authorisation rule first, then authenticate and check the log in ISE. hen pick out certain attributes to create your authorisation rule and set required permissions on that rule.
You can't have more than one computer certificate from a specific CA per machine, so as long as you set the authentication method to use Computer Authentication it will always use the machine certificate.