Cannot ping ASA 5505 INSIDE INTERFACE across VPN.
Hello,
I cannot ping one of our remote offices ASA 5505's across the site-to-site VPN tunnel. I've compared the configs of our offices and they do not look any different, so I do not know what I'm missing.
Site 1 cannot ping the inside interface of site 2, however site 2 can ping the inside interface of site 1.
ICMP traffic is being allowed through the firewall and ICMP is enabled in the global policy settings to be inspected.
Quick note, I can ping site 2's inside interface from a system within site 2, I just can't do it across the VPN.
I'm working via ASDM, so any help fixing this via ASDM would be greatly appreciated.
I cannot ping one of our remote offices ASA 5505's across the site-to-site VPN tunnel. I've compared the configs of our offices and they do not look any different, so I do not know what I'm missing.
Site 1 cannot ping the inside interface of site 2, however site 2 can ping the inside interface of site 1.
ICMP traffic is being allowed through the firewall and ICMP is enabled in the global policy settings to be inspected.
Quick note, I can ping site 2's inside interface from a system within site 2, I just can't do it across the VPN.
I'm working via ASDM, so any help fixing this via ASDM would be greatly appreciated.
ASKER
I'm getting 'Request timed out."
Okay, that means that the ping is probably getting from Site 1 to Site 2 but Site 2 is unable or refusing to send a response.
I would start by looking at the ACL's on Site 2 for an implicit deny.
I would start by looking at the ACL's on Site 2 for an implicit deny.
ASKER
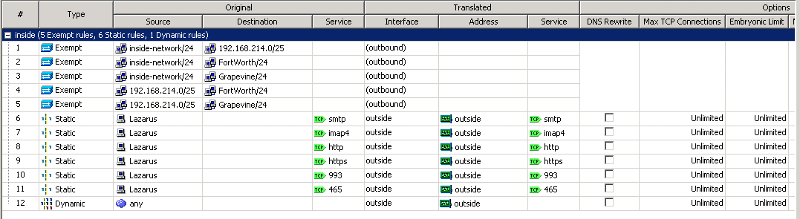
I've attached a screenshot of my ACL. There are no implicit deny's for ICMP traffic.
ACL.png
ACL.png
Which firmware version are you using?
Also can you post your NAT statements?
-BB
Also can you post your NAT statements?
-BB
ASKER
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
We do not have a service agreement with Cisco, so I do not have the ability to download firmware from their site. Is there another way to procure it?
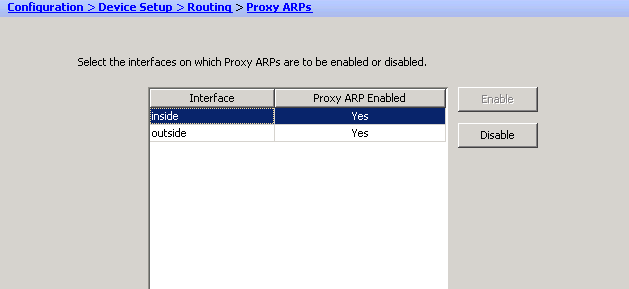
No legal ways that I know of. The goal is basically to turn proxy arp off on your tunnel NAT configuration.
MO
MO
ASKER
Ahh, and I suppose there's no way to do it in my current firmware?
I don't believe so. Sorry about that. Support contract on a 5505 for 8x5 NBD is pretty reasonable. I believe it's only $100. Maybe $150 for the upgraded 24x7, 4 hour hardware replacement warranty. Either one will give you access to Cisco.com so you can download the latest system and asdm software.
MO
MO
I believe the above costs are for the 50 User licensed 5505. If this is a 10 User licensed 5505 it's even cheaper for SMARTnet.
MO
MO
ASKER
Would advise against that. Those are proxy arp settings on physical interfaces which you most likely need intact. We're talking about turning the proxy arp off specially on the tunnel NAT.
MO
MO
Here's a good read on how proxy arp works on an ASA: http://www.packetu.com/2011/11/07/the-asas-arp-behavior/
I would advise against turning it off globally on an interface. Since the issue is with how proxy-arp works across a VPN tunnel then you only need the ability to turn off proxy-arp on the NAT (or no NAT, technically) associated with the VPN tunnel.
MO
I would advise against turning it off globally on an interface. Since the issue is with how proxy-arp works across a VPN tunnel then you only need the ability to turn off proxy-arp on the NAT (or no NAT, technically) associated with the VPN tunnel.
MO
ASKER
Thanks for the info MO, I'll read up on it. I'm still trying to figure out how to purchase a service contract. Cisco's site redirects me to resellers, but the reseller sites aren't listing cisco service contracts so I'm emailing sales to get some answers.
Get one through CDW. That's probably the easiest.
MO
MO
mgortega:
I see what you are getting at now. Makes sense. Here is another good article: http://www.fir3net.com/Cisco-ASA/cisco-asa-proxy-arp-gotcha.html
I see what you are getting at now. Makes sense. Here is another good article: http://www.fir3net.com/Cisco-ASA/cisco-asa-proxy-arp-gotcha.html
Unreachable would mean the issue is probably at Site 1 (the originator of the failing ping)
Time Out would mean the issue is probably at Site 2 (the responder of the failing ping)