cisco 2901 k will not nat internet traffic not passing traffic in or out
I have a 2901k9 router that has the attached config.
My issue is that is now does connect the vpn or indeed allow internet +web traffic into the local network..
stumped.
Thanks
Matthew
r1config.txt
My issue is that is now does connect the vpn or indeed allow internet +web traffic into the local network..
stumped.
Thanks
Matthew
r1config.txt
ASKER
thanks for your response, just amended config with your suggestion still not working
Delete your last NAT and ACL commands but keep your existing interface NAT config
Copy and paste the following into a global configuration prompt:
access-list 101 deny ip 192.168.10.0 0.0.1.255 10.98.136.0 0.0.1.255
access-list 101 permit ip 192.168.10.0 0.0.1.255 any
access-list 101 permit ip 192.168.250.0 0.0.0.255 any
ip nat inside source list 101 int gi0/1 overload
Copy and paste the following into a global configuration prompt:
access-list 101 deny ip 192.168.10.0 0.0.1.255 10.98.136.0 0.0.1.255
access-list 101 permit ip 192.168.10.0 0.0.1.255 any
access-list 101 permit ip 192.168.250.0 0.0.0.255 any
ip nat inside source list 101 int gi0/1 overload
TCP_179: How is your config functionally any different from the one I posted?
ASKER
Sorry, which config is preferred way ?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you donjohnston but i need the vpn there as it used for hosted desktops.
the only config i need is for all users behind network 192.168.10.0/23 to nat out to internet.
these users should be able to connect to hosted desktops
the nat inbound is only for 3 ports.... RDP 3389 , TCP port 6200 and tcp port 554
which is the default route you suggest to delete ? the one ending gigabitethernet0/1 ?
Thank you for your time
the only config i need is for all users behind network 192.168.10.0/23 to nat out to internet.
these users should be able to connect to hosted desktops
the nat inbound is only for 3 ports.... RDP 3389 , TCP port 6200 and tcp port 554
which is the default route you suggest to delete ? the one ending gigabitethernet0/1 ?
Thank you for your time
Yes, delete the route that uses the interface.
When troubleshooting, sometimes it helps to remove extraneous info from the config.
When troubleshooting, sometimes it helps to remove extraneous info from the config.
ASKER
that worked!!!!! Thank you
My solution would have worked and the extended ACL was meant to exempt NAT when the destination was that of another subnet over the VPN, donjohnson.
There was absolutely no reason to remove the VPN configuration.
There was absolutely no reason to remove the VPN configuration.
Now when Maphew adds his VPN configuration back it will again not work...
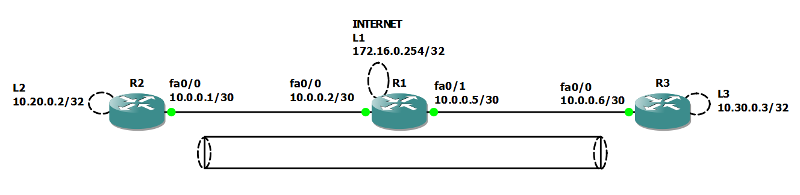
Here is R2's configuration; only the important output is posted here... below you will notice that pings to the internet and fa0/0 of R3 are successful, however due to the lack of a nat exemption, a ping to the subnet over the tunnel is not successful...
crypto isakmp policy 10
encr aes 256
authentication pre-share
crypto isakmp key cisco123 address 10.0.0.6
!
!
crypto ipsec transform-set aesset esp-aes 256 esp-sha-hmac
!
crypto map aesmap 10 ipsec-isakmp
set peer 10.0.0.6
set transform-set aesset
match address ACL_VPN
interface Loopback2
ip address 10.20.0.2 255.255.255.255
ip nat inside
ip virtual-reassembly
!
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map aesmap
ip access-list standard NAT_ACL
permit 10.20.0.2 0.0.0.0
!
ip access-list extended ACL_VPN
permit ip host 10.20.0.2 host 10.30.0.3
R2#ping
Protocol [ip]:
Target IP address: 10.0.0.6
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.6, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/46/64 ms
R2#
R2#
R2#
R2#ping
Protocol [ip]:
Target IP address: 172.16.0.254
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.254, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/32/44 ms
R2#
R2#
R2#
R2#ping
Protocol [ip]:
Target IP address: 10.30.0.3
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.30.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
.....
Success rate is 0 percent (0/5)
crypto isakmp policy 10
encr aes 256
authentication pre-share
crypto isakmp key cisco123 address 10.0.0.6
!
!
crypto ipsec transform-set aesset esp-aes 256 esp-sha-hmac
!
crypto map aesmap 10 ipsec-isakmp
set peer 10.0.0.6
set transform-set aesset
match address ACL_VPN
interface Loopback2
ip address 10.20.0.2 255.255.255.255
ip nat inside
ip virtual-reassembly
!
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.252
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map aesmap
ip access-list standard NAT_ACL
permit 10.20.0.2 0.0.0.0
!
ip access-list extended ACL_VPN
permit ip host 10.20.0.2 host 10.30.0.3
R2#ping
Protocol [ip]:
Target IP address: 10.0.0.6
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.0.0.6, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 32/46/64 ms
R2#
R2#
R2#
R2#ping
Protocol [ip]:
Target IP address: 172.16.0.254
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.0.254, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/32/44 ms
R2#
R2#
R2#
R2#ping
Protocol [ip]:
Target IP address: 10.30.0.3
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.30.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
.....
Success rate is 0 percent (0/5)
Now, here's where we use an Extended ACL and add a NAT exemption to prevent the IPsec tunnel traffic from being translated to the outside ip address:
R2(config)#do show ip access-list
Standard IP access list NAT_ACL
10 permit 10.20.0.2 (4 matches)
Extended IP access list ACL_VPN
10 permit ip host 10.20.0.2 host 10.30.0.3 (28 matches)
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#no ip access-list standard NAT_ACL
R2(config)#
R2(config)#
R2(config)#ip access-list extended NAT_ACL
R2(config-ext-nacl)#deny ip 10.20.0.2 0.0.0.0 10.30.0.3 0.0.0.0
R2(config-ext-nacl)#permit
R2(config-ext-nacl)#end
R2#
R2#
R2#pi
*Mar 1 00:32:39.383: %SYS-5-CONFIG_I: Configured from console by console
R2#ping
Protocol [ip]:
Target IP address: 10.30.0.3
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.30.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 44/63/88 ms
R2#
R2(config)#do show ip access-list
Standard IP access list NAT_ACL
10 permit 10.20.0.2 (4 matches)
Extended IP access list ACL_VPN
10 permit ip host 10.20.0.2 host 10.30.0.3 (28 matches)
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#
R2(config)#no ip access-list standard NAT_ACL
R2(config)#
R2(config)#
R2(config)#ip access-list extended NAT_ACL
R2(config-ext-nacl)#deny ip 10.20.0.2 0.0.0.0 10.30.0.3 0.0.0.0
R2(config-ext-nacl)#permit
R2(config-ext-nacl)#end
R2#
R2#
R2#pi
*Mar 1 00:32:39.383: %SYS-5-CONFIG_I: Configured from console by console
R2#ping
Protocol [ip]:
Target IP address: 10.30.0.3
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.20.0.2
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.30.0.3, timeout is 2 seconds:
Packet sent with a source address of 10.20.0.2
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 44/63/88 ms
R2#
Mathew, I hope you follow my advice Sir... I will also upload my lab files for you to examine at your convenience. Have a good weekend, and please feel free to contact me any time you have any issues. SEE ATTACHED FOR LAB AND CONFIGS
NOTE: Due to not being able to upload .cfg and .net files, I changed any of these file types to .txt. If you wish to run the lab in GNS3, please thange topology.txt to topology.net, and change all files in the configs folder to .cfg, thank you.
VPN-NAT.zip
NOTE: Due to not being able to upload .cfg and .net files, I changed any of these file types to .txt. If you wish to run the lab in GNS3, please thange topology.txt to topology.net, and change all files in the configs folder to .cfg, thank you.
VPN-NAT.zip
ASKER
Thank you TCP_179 for the detailed support you were correct on the re adding of vpn.
Ca you explain again why this issue reappeared ?
I am using CCP to create the VPN ut it detects my previous NAT rules ..
Thank you again
CCP-vpn.png
Ca you explain again why this issue reappeared ?
I am using CCP to create the VPN ut it detects my previous NAT rules ..
Thank you again
CCP-vpn.png
Sure, the NAT rules that you were told to use translated your private LANs whether they went over the VPN or not; no matter the destination. That is why when I presented the solution to you I used an extended ACL to deny the "Interesting" traffic, or simply your VPN subnet from being translated when going over the VPN tunnel, and then permitted the same subnet, including your other LAN subnet to be translated when going to any destination.
ip nat inside source list 1 int g0/1 overload
access-list 1 permit 192.168.10.0 0.0.1.255
access-list 1 permit 192.168.250.0 0.0.0.255