marrj
asked on
DNS Host Record Disappearing Windows Server
I have a Windows 2008 R2 server that I want to manually create an A record in DNS for. I also do not want it to try to register its own name. So, as I would have done in Server 2003, I disabled its ability to register a name in the TCP/IPv4 properties of the NIC. Then, I went to my DNS and created a record. All seems right with the world. However, after a few hours, the manually created A record disappears. I have the same problem with a Server 2012 machine. This method has worked perfectly for me in the past with older OSs like 2003 and 2000. Has Microsoft disabled the ability to do this?
ASKER
My zones are set to receive both secure and nonsecure updates.
Scavenging is not enabled.
Yes, the servers all have static IPs.
Yes, my zones are AD-integrated.
Replication seems to be working fine. No errors are present in the logs.
I just tested the same procedure from a Windows Server 2003 machine and it works as planned. So, it seems to be something unique to the later operating systems.
Scavenging is not enabled.
Yes, the servers all have static IPs.
Yes, my zones are AD-integrated.
Replication seems to be working fine. No errors are present in the logs.
I just tested the same procedure from a Windows Server 2003 machine and it works as planned. So, it seems to be something unique to the later operating systems.
Some process must be acting to specifically remove those records. I have plenty of 2008 R2 DCs running DNS, and I've never had a problem like you describe. Any records that I create stick around.
I was trying to think of a way that another machine or DHCP might delete the record, but I'm not coming up with anything that sounds right. You might try adjusting the security on the record, but with allowing non-secure updates, I'm not positive if this would help. At this point I would enable the DNS auditing to see if it gives you some useful information. Last thing I would check is with ADSIEdit - check to see if there is a duplicate or conflicting zone. This link gives some more detail.
http://msmvps.com/blogs/acefekay/archive/2009/09/02/using-adsi-edit-to-resolve-conflicting-or-duplicate-ad-integrated-dns-zones.aspx
Other than that I'm afraid I'm out of ideas.
I was trying to think of a way that another machine or DHCP might delete the record, but I'm not coming up with anything that sounds right. You might try adjusting the security on the record, but with allowing non-secure updates, I'm not positive if this would help. At this point I would enable the DNS auditing to see if it gives you some useful information. Last thing I would check is with ADSIEdit - check to see if there is a duplicate or conflicting zone. This link gives some more detail.
http://msmvps.com/blogs/acefekay/archive/2009/09/02/using-adsi-edit-to-resolve-conflicting-or-duplicate-ad-integrated-dns-zones.aspx
Other than that I'm afraid I'm out of ideas.
ASKER
I took your advice and enabled auditing. After sorting through the security logs on my 16 domain controllers, I found one that logs four 5136 events every time the record in question is deleted.
Here are the four events I see when a record disappears. The DNS server that these events appear on is running Windows Server 2012. The machine whose record keeps getting deleted is running Windows Server 2012 R2. This particular DC that keeps deleting the records happens to host my PDC emulator role. All other fsmo roles are on other DCs. I have also attached a screenshot of the advanced properties of this particular DC, so you can see that scavenging is disabled. Scavenging for the zone is disabled as well.
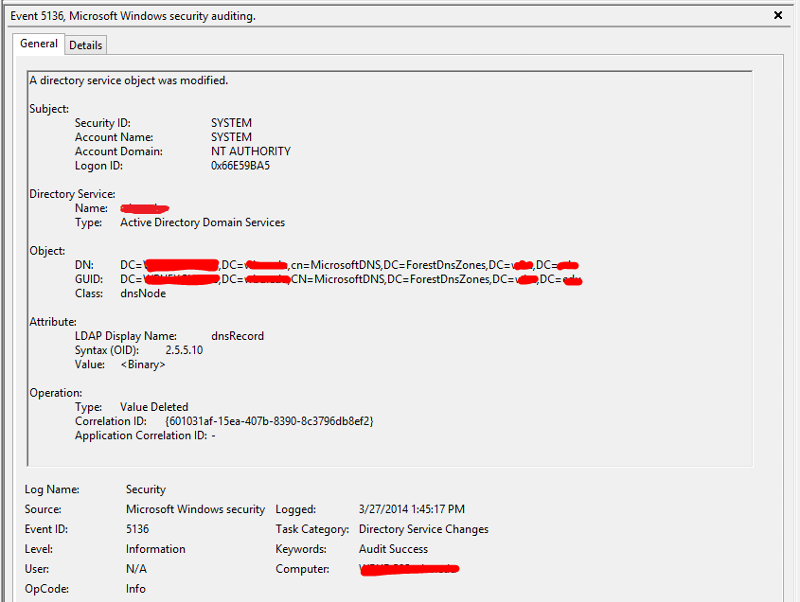
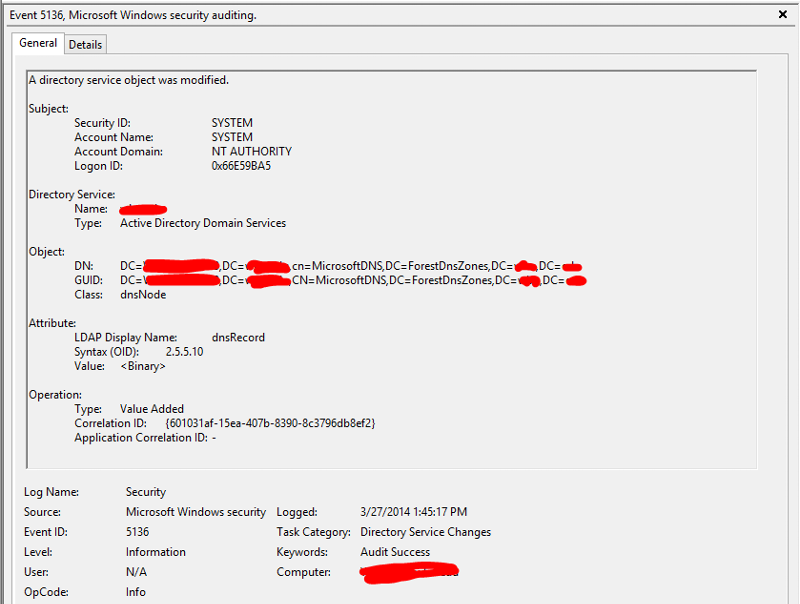
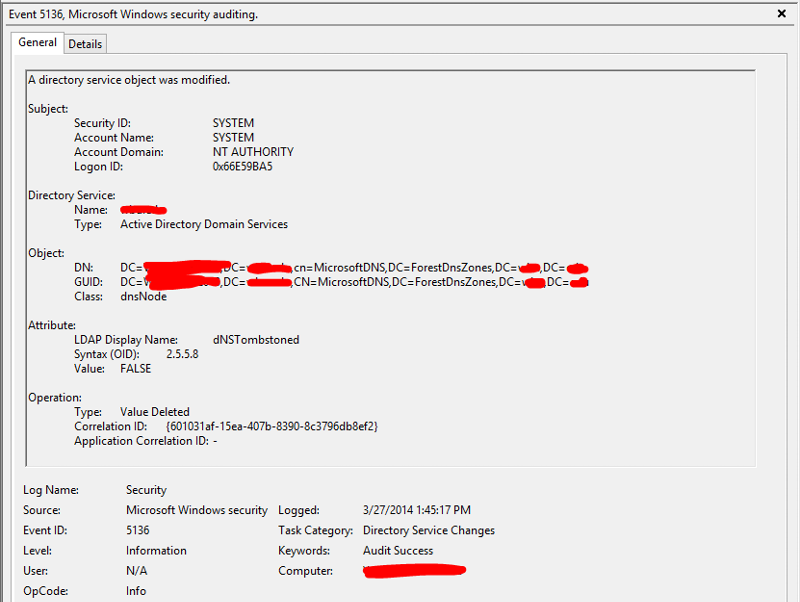
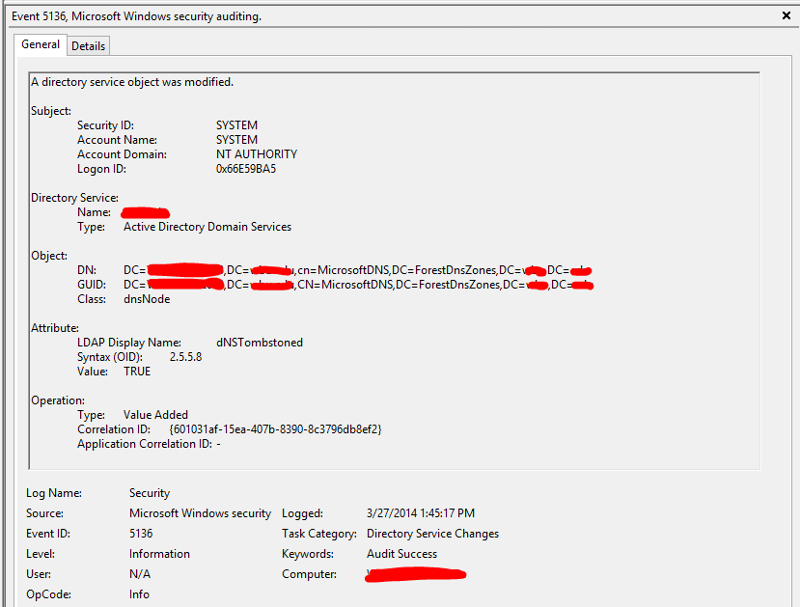
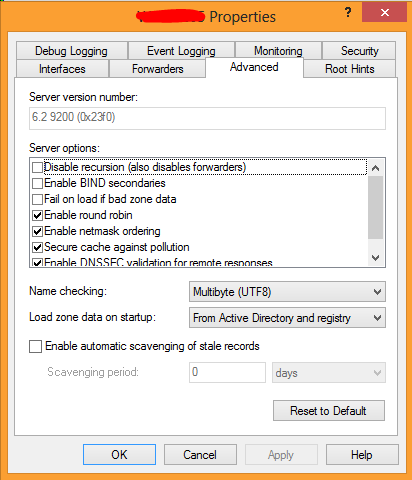
Here are the four events I see when a record disappears. The DNS server that these events appear on is running Windows Server 2012. The machine whose record keeps getting deleted is running Windows Server 2012 R2. This particular DC that keeps deleting the records happens to host my PDC emulator role. All other fsmo roles are on other DCs. I have also attached a screenshot of the advanced properties of this particular DC, so you can see that scavenging is disabled. Scavenging for the zone is disabled as well.
ASKER
I also attempted to locate duplicate zones via ADSI edit. I'm having a little trouble finding my zones. I've attached a screenshot of what my tree looks like. My "Microsoft DNS" container seems to be located under the "System" container, rather than on the root like most of the articles that I've read refer to. Also, when I do open the "Microsoft DNS" container, only some of my zones appear. I have 3 forward lookup zones and about 30 reverse lookup zones in my AD-integrated DNS. Only 5 reverse zones appear in the container. To my knowledge, my DNS has been functioning perfectly fine for many years until this recent issue of static A records disappearing.
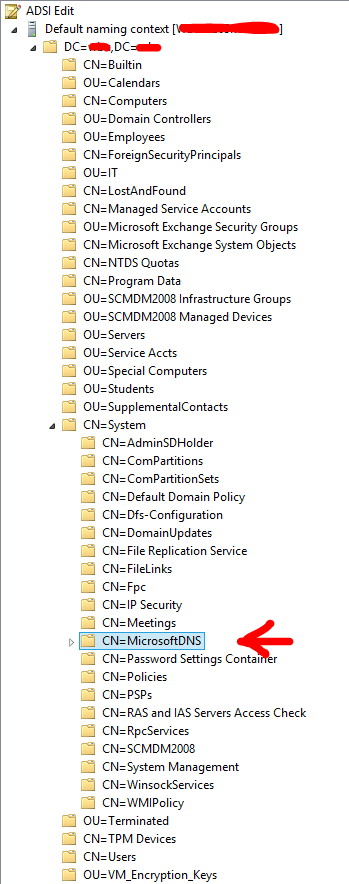
ASKER
I've attached a screenshot of one of my AD-integrated zones that I can't seem to find in AD, just to prove that the settings are correct.
Also, I found this article about the location of AD-integrated zones. I am now curious as to whether the location of zones in my AD is a remnant of the 2000 days. My domain would have started life in those days and has been upgraded through the years. I am now at a 2008 functional level forest-wide. http://technet.microsoft.com/en-us/library/cc978010.aspx
Any thoughts?
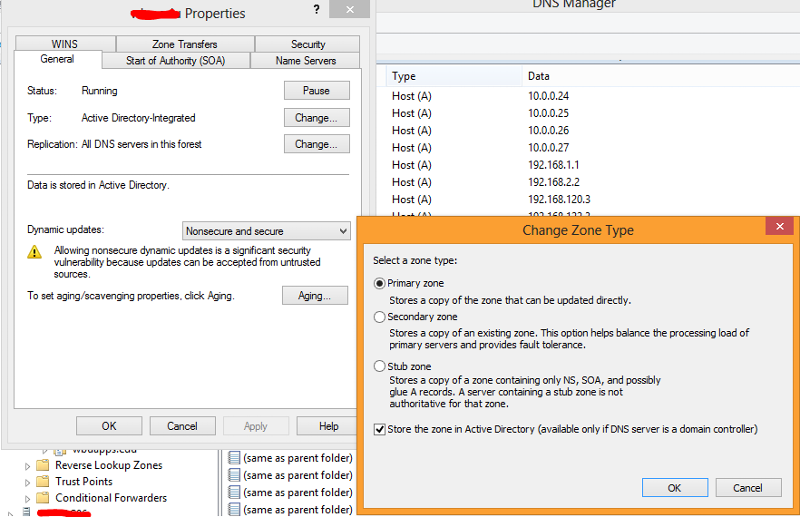
Also, I found this article about the location of AD-integrated zones. I am now curious as to whether the location of zones in my AD is a remnant of the 2000 days. My domain would have started life in those days and has been upgraded through the years. I am now at a 2008 functional level forest-wide. http://technet.microsoft.com/en-us/library/cc978010.aspx
Any thoughts?
ASKER
Also, in my ADSI edit too, I don't have the "Domain" naming context to connect to. The only options I have are "Configuration", "Schema", "Default Naming Context", and "RootDSE".
Depending on what the replication is set to for each zone, the location where it is stored will be different. The naming contexts "dc=domain,dc=com", "dc=domaindnszones,dc=doma
Prior to Server 2003 zones were only stored in the default naming context. With 2003 and later the default when setting up a new domain was for it to be in DomainDnsZones, and the _msdcs zone to be in ForestDnsZones. However, upgrading a domain from 2000 wouldn't automatically change where a zone was stored, so that's likely what you're seeing. My recommendation would be to have every zone (except _msdcs) stored the DomainDnsZones application partition (naming context) unless you're aware of the need to place it elsewhere.
I'll see if there's anything more I can suggest based on the events you posted.
Prior to Server 2003 zones were only stored in the default naming context. With 2003 and later the default when setting up a new domain was for it to be in DomainDnsZones, and the _msdcs zone to be in ForestDnsZones. However, upgrading a domain from 2000 wouldn't automatically change where a zone was stored, so that's likely what you're seeing. My recommendation would be to have every zone (except _msdcs) stored the DomainDnsZones application partition (naming context) unless you're aware of the need to place it elsewhere.
I'll see if there's anything more I can suggest based on the events you posted.
The naming context "dc=domain,dc=com" is also referred to as the default or domain naming context.
ASKER
http://social.technet.microsoft.com/forums/windowsserver/en-US/4ba67b5e-18e1-4351-8e06-97a8a59ac1d7/static-dns-records-disappearing
I found this article that describes something similar to what I'm seeing. There are a few differences though. I only have the issue under the following circumstances.
1. The record in question is a static A record, with no scavenging enabled.
2. The host that I am creating the A record for is joined to the domain and would automatically register a hostname identical to that which I create if I let it.
3. The host I am creating the record for has a static IP that the record will resolve to.
4. The host I am creating the record for is running a Windows Server 2008 R2 OS or newer.
Just to recap, I have disabled the box on the properties of the NIC that "automatically register" the DNS name. I simply want to manually create a single A record for the host because the NIC has multiple IPs. I want certain traffic to be directed to a particular IP, rather than creating a round-robin across 3-4 different IPs. In Windows 2003 and prior, it works flawlessly.
I found this article that describes something similar to what I'm seeing. There are a few differences though. I only have the issue under the following circumstances.
1. The record in question is a static A record, with no scavenging enabled.
2. The host that I am creating the A record for is joined to the domain and would automatically register a hostname identical to that which I create if I let it.
3. The host I am creating the record for has a static IP that the record will resolve to.
4. The host I am creating the record for is running a Windows Server 2008 R2 OS or newer.
Just to recap, I have disabled the box on the properties of the NIC that "automatically register" the DNS name. I simply want to manually create a single A record for the host because the NIC has multiple IPs. I want certain traffic to be directed to a particular IP, rather than creating a round-robin across 3-4 different IPs. In Windows 2003 and prior, it works flawlessly.
You might check out this link
http://blogs.technet.com/b/networking/archive/2011/08/17/tracking-dns-record-deletion.aspx
It describes a number of scenarios in which a record can be deleted. Updating a record with a TTL = 0 isn't one I'd heard of before.
Is a DHCP server running on the same machine (the DC)?
I also find myself wondering if allowing non-secure dynamic updates could be contributing to this issue, as is does make it easier for a record to be changed by a different machine. Is this record in the same range as a DHCP scope?
http://blogs.technet.com/b/networking/archive/2011/08/17/tracking-dns-record-deletion.aspx
It describes a number of scenarios in which a record can be deleted. Updating a record with a TTL = 0 isn't one I'd heard of before.
Is a DHCP server running on the same machine (the DC)?
I also find myself wondering if allowing non-secure dynamic updates could be contributing to this issue, as is does make it easier for a record to be changed by a different machine. Is this record in the same range as a DHCP scope?
ASKER
The DC that shows the deleted record events is a DHCP server for many of my subnets. However, the subnet that the server I'm trying to create a record for is not one of them. I have another DHCP server that serves that subnet. The reason being that I have WDS on that second server and having DHCP colocated just makes life easier.
The IPs on the server I'm trying to create a record for are outside of my DHCP scope for that subnet.
If I pursue the option of converting my forward lookup zone to allow secure updates only, what repercussions am I looking at? I'd hate to compromise the integrity of my zone. Everything I have is in that zone.
I really appreciate you sticking with me on this one.
I have verified one more theory that I've had:
1. If I create an A record by any other name than the hostname of the server, it sticks and is never deleted.
I will now experiment with the TTL of the record and get back with you.
The IPs on the server I'm trying to create a record for are outside of my DHCP scope for that subnet.
If I pursue the option of converting my forward lookup zone to allow secure updates only, what repercussions am I looking at? I'd hate to compromise the integrity of my zone. Everything I have is in that zone.
I really appreciate you sticking with me on this one.
I have verified one more theory that I've had:
1. If I create an A record by any other name than the hostname of the server, it sticks and is never deleted.
I will now experiment with the TTL of the record and get back with you.
ASKER
Looking at the article you sent me, I think the last scenario described in the table most closely resembles my particular issue. Since SYSTEM is performing the delete, and since the log entries actually reference the tombstoning process, I think I am looking at some kind of internal AD delete.
At this point, I'm ok with writing it off as being "by design". I just can't figure out what the difference in operating systems has to do with this. I'm guessing Microsoft somehow changed the behavior of client-enabled DNS changes in Server 2008.
At this point, I'm ok with writing it off as being "by design". I just can't figure out what the difference in operating systems has to do with this. I'm guessing Microsoft somehow changed the behavior of client-enabled DNS changes in Server 2008.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I think I'm just going to redesign the host and let it automatically register a name.
Sorry we weren't able to find an exact cause for this.
Cheers!
Cheers!
Are your zones set up to allow secure updates only?
I assume the server is set up with a static IP, correct?
Are you using AD integrated zones? Have you verified that replication is working properly and that there are no errors in event logs?
You might try enabling auditing for DNS.
http://blogs.technet.com/b/askpfeplat/archive/2013/10/12/who-moved-the-dns-cheese-auditing-for-ad-integrated-dns-zone-and-record-deletions.aspx
It seems very unlikely given the short duration, but have you checked your scavenging settings?