DukewillNukem
asked on
EMET best practice
i just started to configure the EMET settngs in GPO,however-i dont know how those settings will affect the software behaviour and how users will be affected.
can somebody give some ideas how to start and what setting does what?
i.e. what happens when ASLR is set to "application opt-in" or when
deep hooks,anti detours,banned functions,exploit action is set to enabled?
can somebody give some ideas how to start and what setting does what?
i.e. what happens when ASLR is set to "application opt-in" or when
deep hooks,anti detours,banned functions,exploit action is set to enabled?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
EMET is also aware of some compatibility issues on it's own, and set's a conservative setting for some items.
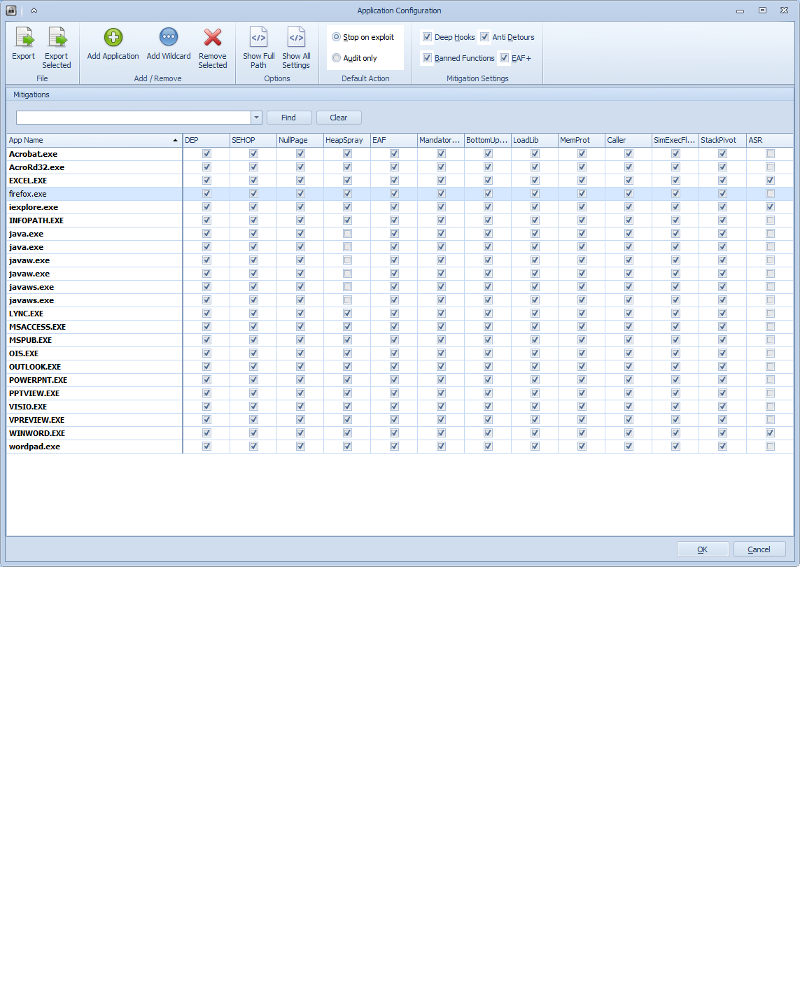 Those are some of the defaults EMET uses for different programs, there are others, but that is the basic idea. I would start with the defaults, then read the PDF that accompanies EMET for more details inside each mitigation. OPT-IN is best to start with, you can see also how M$ has chosen other more advanced defaults too, like the forbidding of flash and active-x in office documents:
Those are some of the defaults EMET uses for different programs, there are others, but that is the basic idea. I would start with the defaults, then read the PDF that accompanies EMET for more details inside each mitigation. OPT-IN is best to start with, you can see also how M$ has chosen other more advanced defaults too, like the forbidding of flash and active-x in office documents:
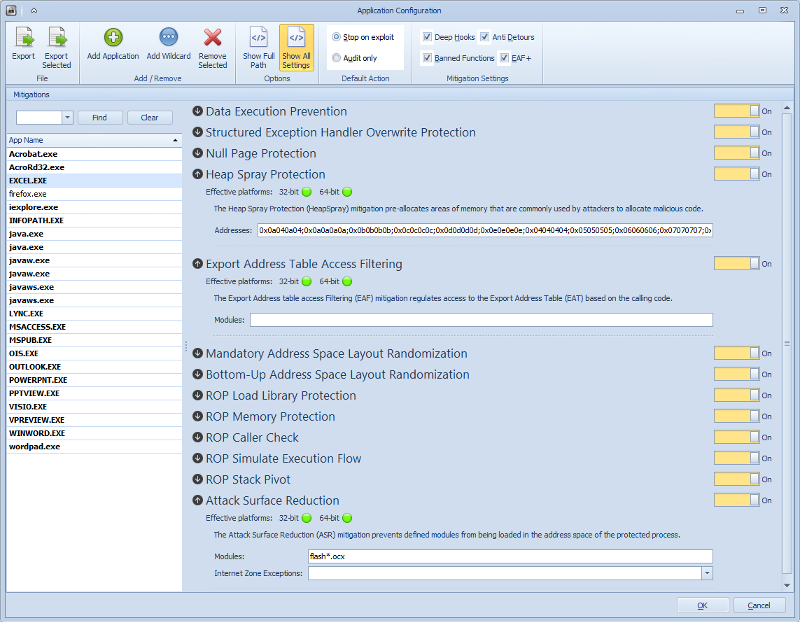 -rich
-rich
 Those are some of the defaults EMET uses for different programs, there are others, but that is the basic idea. I would start with the defaults, then read the PDF that accompanies EMET for more details inside each mitigation. OPT-IN is best to start with, you can see also how M$ has chosen other more advanced defaults too, like the forbidding of flash and active-x in office documents:
Those are some of the defaults EMET uses for different programs, there are others, but that is the basic idea. I would start with the defaults, then read the PDF that accompanies EMET for more details inside each mitigation. OPT-IN is best to start with, you can see also how M$ has chosen other more advanced defaults too, like the forbidding of flash and active-x in office documents: -rich
-rich
ASKER
ok,thx. i got that far already, now ill have to start with more 3rd party tools-and even tougher-with seldcoded apps.
is there a list that M$ has published whats supported?
is there a list that M$ has published whats supported?
There are too many applications to list. EMET supports most things. Enable the application and test it. You may have to adjust the settings. SEHOP, DEP and EAF are the most common to adjust.
If the application is not internet facing or use very much, there is no need to include it in EMET.
If the application is not internet facing or use very much, there is no need to include it in EMET.
ASKER
what are the typical internet facing applications?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
ok,thank you. we do have a lot of "selfcoded" application,which im not sure about how they will behave once imported in EMET.
i assume, you would start with the recommended settings first?
i assume, you would start with the recommended settings first?
It's more trial and error, but you don't have to expect problems, EMET is made so that it hopefully won't interfere. The techniques in EMET happen around the executable, not to it. You can enable 2 protections without emet, the DEP and ASLR can be set by using the program peflags, and they add two tags inside the exe (emet does not do this), and the OS will read them and apply DEP and ASLR. That is a more obtrusive way to enable some of the protections, but it will follow the exe to every OS. The others would have to be compiled into your EXE's logic and execution trees. EMET allows you to get that advanced functionality without having to recode. EMET also allows you to opt-out, and if you have issues after enabling it, you have to start to opt-out of certain protections.
-rich
-rich
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
@DukewillNukem - Good luck with EMET. It is new and it is good. I have every confidence it will improve. EMET 5 is in Tech Preview. I have tried it and I am waiting until the production version comes out.