Help with Exchange 2007 SSL Certificate:
I'm having a hard time trying to install the new SSL certificate we purchased from CertificatesForExchange.co
I generated a new CSR and submitted it to CertificatesForExchange.co
After the domain verification process, I downloaded the zip file which contained 2 files.
One is a CRT and the other is a P7B file. I placed them both in C:\SSL_Certs.
I renamed the CRT file 2014_SSL.crt.
I imported the P7B file into the "Intermediate Certification Authorities" store without issue.
I then ran the following command: Import-ExchangeCertificate
I got the following:
When I run Enable-ExchangeCertificate
I get the following error:
Get-ExchangeCertificate | fl
2 certificates show up. A self-signed certificate and the SSL certificate we purchased from CertificatesForExchange last year which expires 7/26/14.
I thought when I imported the new certificate named 2014_SSL.crt it would show up in this list.
Can anyone help me with this?
I generated a new CSR and submitted it to CertificatesForExchange.co
After the domain verification process, I downloaded the zip file which contained 2 files.
One is a CRT and the other is a P7B file. I placed them both in C:\SSL_Certs.
I renamed the CRT file 2014_SSL.crt.
I imported the P7B file into the "Intermediate Certification Authorities" store without issue.
I then ran the following command: Import-ExchangeCertificate
I got the following:
Thumbprint Services Subject
---------- -------- -------
D2BC4203CB132E3CA9AD86F35E32D901ADFBCF8E ..... CN=webmail.domainABC....When I run Enable-ExchangeCertificate
I get the following error:
Enable-ExchangeCertificate -D2BC4203CB132E3CA9AD86F35E32D901ADFBCF8E -Services "SMTP, IMAP, IIS"
Enable-ExchangeCertificate : A parameter cannot be found that matches parameter name 'D2BC4203CB132E3CA9AD86F35E32D901ADFBCF8E'.
At line:1 char:69
+ Enable-ExchangeCertificate -D2BC4203CB132E3CA9AD86F35E32D901ADFBCF8E <<<< -S
ervices "SMTP, IMAP, IIS"Get-ExchangeCertificate | fl
2 certificates show up. A self-signed certificate and the SSL certificate we purchased from CertificatesForExchange last year which expires 7/26/14.
I thought when I imported the new certificate named 2014_SSL.crt it would show up in this list.
Can anyone help me with this?
ASKER
lmao I didn't spell Thumbprint properly??? Sigh.
I generated the CSR request using Exchange Management Shell by typing:
I generated the CSR request using Exchange Management Shell by typing:
New-ExchangeCertificate -generaterequest -keysize 2048 -subjectname "c=US, l=Wayne, s=NJ,
o=Company ABC, cn=webmail.DomainABC.com" -domainname autodiscover.DomainABC.com, ServerA,
ServerA.DomainABC.local, ServerA.DomainABC.com -PrivateKeyExportable $true -path
c:\2014_Exchange_SSL.txtASKER
Oh...I didn't add thumbprint at all. You didn't spell thumbprint right lol. Sorry about that.
lol yup I see my typo :)
Once you correct the command it should work.
Also you can process the request through the command:
Import-ExchangeCertificate
Then:
Enable-ExchangeCertificate
I think thumbprint is correct this time.
Once you correct the command it should work.
Also you can process the request through the command:
Import-ExchangeCertificate
Then:
Enable-ExchangeCertificate
I think thumbprint is correct this time.
ASKER
OK I think I finally got somewhere but before I go any further I wanted your input.
When I run the command PROPERLY (thank you for pointing out the missing "Thumbprint") I get the warning below.
Is the old certificate that is going to expire in a few days the one that's taking precedence?
When I run the command PROPERLY (thank you for pointing out the missing "Thumbprint") I get the warning below.
Is the old certificate that is going to expire in a few days the one that's taking precedence?
Enable-ExchangeCertificate -Thumbprint 84F342232907060A61C9A3D112DB0A09329C2429
-Services "SMTP, IMAP, IIS"
WARNING: This certificate will not be used for external TLS connections with an FQDN of
'ServerA.DomainABC.local' because the CA-signed certificate with thumbprint 'A7ACB1C7B81F946BF985454D2956E34082DBFDBE' takes precedence. The following connectors
match that FQDN: Default ServerA.
Confirm Overwrite existing default SMTP certificate,
'A7ACB1C7B81F946BF985454D2956E34082DBFDBE' (expires 7/26/2014 11:01:43 AM),
with certificate '84F342232907060A61C9A3D112DB0A09329C2429' (expires 7/26/2015
11:01:43 AM)?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help
(default is "Y"):
If you use a self signed certificate for SMTP do not overwrite.
That being said, the smtp certificate is set to expire on 07/26 so I think if you are going to continue to use a self-signed certificate for this then you will need to generate a new one.
If you plan on using the third party certificate that you just got, then go ahead and overwrite.
That being said, the smtp certificate is set to expire on 07/26 so I think if you are going to continue to use a self-signed certificate for this then you will need to generate a new one.
If you plan on using the third party certificate that you just got, then go ahead and overwrite.
ASKER
The self-signed certificate doesn't expire for a few years.
I went ahead and clicked overwrite.
The thing is, when I type Get-ExchangeCertificate | fl the new certificate has a status of INVALID.
The certificate that is going to expire in a few days has a status of VALID.
Am I supposed to remove the current certificate or restart the services or anything like that?
I went ahead and clicked overwrite.
The thing is, when I type Get-ExchangeCertificate | fl the new certificate has a status of INVALID.
The certificate that is going to expire in a few days has a status of VALID.
Am I supposed to remove the current certificate or restart the services or anything like that?
Can you verify the certificate chain is properly installed:
go to the certificate in mmc
mmc.exe - add remove snapins - certificates - computer account - local computer
Expand personal and double click on the new certificate in the right pane.
Confirm that this says you have a private key for this certificate
Click on certification path - go to the certificate at the top of the path - double click on the certificate at the top and save to file - once done go back to the mmc and go to "Trusted Root Certification Authorities" and right click and import - navigate to the certificate you just shared and complete the wizard.
go to the certificate in mmc
mmc.exe - add remove snapins - certificates - computer account - local computer
Expand personal and double click on the new certificate in the right pane.
Confirm that this says you have a private key for this certificate
Click on certification path - go to the certificate at the top of the path - double click on the certificate at the top and save to file - once done go back to the mmc and go to "Trusted Root Certification Authorities" and right click and import - navigate to the certificate you just shared and complete the wizard.
ASKER
I went ahead and did what you said but it didn't change anything.
When you mentioned saving the top most file in the path to file, are you referring to the details tab of that certificate where you can click copy to file? Because that's what I did and it allowed me to export the certificate.
When you mentioned saving the top most file in the path to file, are you referring to the details tab of that certificate where you can click copy to file? Because that's what I did and it allowed me to export the certificate.
Did you open the certificate and confirm that this says you have a private key for this certificate
ASKER
Yes. It says I have a private key for this certificate.
Did you install the second file as per the instructions?
There are two files in the zip file - one is your certificate, one is the intermediate certificate bundle. The second one MUST be installed on to your server.
Click start, run, then type MMC.
Choose certificates as the add in and then computer.
Go to intermediate certificates and choose tasks, import. Select the intermediate bundle.
Once done, close MMC (no need to save it).
As for overwriting the SMTP certificate, I wouldn't normally do that.
Therefore what I would do is run
new-exchangecertificate
no further commands. You will get a prompt to replace the default SMTP certificate. Say yes and then remove the other self signed certificates.
Simon.
There are two files in the zip file - one is your certificate, one is the intermediate certificate bundle. The second one MUST be installed on to your server.
Click start, run, then type MMC.
Choose certificates as the add in and then computer.
Go to intermediate certificates and choose tasks, import. Select the intermediate bundle.
Once done, close MMC (no need to save it).
As for overwriting the SMTP certificate, I wouldn't normally do that.
Therefore what I would do is run
new-exchangecertificate
no further commands. You will get a prompt to replace the default SMTP certificate. Say yes and then remove the other self signed certificates.
Simon.
ASKER
Yes, I've installed the 2nd certificate each time I've attempted to do this so it's definitely in there.
I followed the instructions to the letter. The issue is that the instructions on each and every site don't mention what to do if you are RENEWING the certificate or REPLACING the certificate. They just tell you the steps as if you were getting a signed certificate for the first time.
If I type in only New-ExchangeCertificate I get the following message:
This is leading me to believe that the newest signed certificate has already been successfully installed.
The one that expires on 7/26/2015 is the one I renewed recently.
But this same certificate has a "status" of "invalid".
Is it possible it's going to wait until the 26th which is when the current signed certificate expires?
I followed the instructions to the letter. The issue is that the instructions on each and every site don't mention what to do if you are RENEWING the certificate or REPLACING the certificate. They just tell you the steps as if you were getting a signed certificate for the first time.
If I type in only New-ExchangeCertificate I get the following message:
[PS] C:\Documents and Settings\Administrator.DOMAINABC\Desktop>new-exchangecert
ficate
WARNING: This certificate will not be used for external TLS connections with an
FQDN of 'ServerA.DomainABC.local' because the CA-signed certificate with
thumbprint 'A7ACB1C7B81F946BF985454D2956E34082DBFDBE' takes precedence. The
following connectors match that FQDN: Default ServerA.
Confirm
Overwrite existing default SMTP certificate,
'84F342232907060A61C9A3D112DB0A09329C2429' (expires 7/26/2015 11:01:43 AM),
with certificate '26151F12BC80BA8AD60D86127F0EC207A8DCAAD8' (expires 7/24/2019
2:20:50 PM)?
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help
(default is "Y"):This is leading me to believe that the newest signed certificate has already been successfully installed.
The one that expires on 7/26/2015 is the one I renewed recently.
But this same certificate has a "status" of "invalid".
Is it possible it's going to wait until the 26th which is when the current signed certificate expires?
There is no difference between a new certificate and a renewal. The process is identical.
Exchange doesn't actually change the certificate until you enable the services.
The reason I said to change back to a self signed SSL certificate for SMTP (therefore using new-exchangecertificate) is due to Exchange needing an SSL certificate that matches the FQDN of the server itself. As you cannot put internal names on public SSL certificates, the best option is to have the default SMTP certificate as a self signed and use the trusted one for everything else.
You could have a bad certificate. Within the SSL management tool you can rekey the SSL certificate.
Simon.
Exchange doesn't actually change the certificate until you enable the services.
The reason I said to change back to a self signed SSL certificate for SMTP (therefore using new-exchangecertificate) is due to Exchange needing an SSL certificate that matches the FQDN of the server itself. As you cannot put internal names on public SSL certificates, the best option is to have the default SMTP certificate as a self signed and use the trusted one for everything else.
You could have a bad certificate. Within the SSL management tool you can rekey the SSL certificate.
Simon.
ASKER
The 2 SSL certs (the one expiring soon and the new one that expires next year) both have the following subject alternative names plus a few others:
ServerA.DomainABC.local
ServerA
The self-signed certificate has the same 2 listed above.
Does this mean we don't necessarily need to enable the self-signed certificate for SMTP because the SSL certificates cover those 2 names?
ServerA.DomainABC.local
ServerA
The self-signed certificate has the same 2 listed above.
Does this mean we don't necessarily need to enable the self-signed certificate for SMTP because the SSL certificates cover those 2 names?
You don't need to at the moment.
However trusted SSL certificates dated after November 2015 cannot have internal names on them.
That means for most sites they will need to have two SSL certificates in place - a trusted one for web services and a self signed one for SMTP.
Simon.
However trusted SSL certificates dated after November 2015 cannot have internal names on them.
That means for most sites they will need to have two SSL certificates in place - a trusted one for web services and a self signed one for SMTP.
Simon.
ASKER
This is what shows up when I run the get cert command.
Questions:
- Why is the middle one (outlined in yellow) still showing as invalid?
- I didn't remove the expired certificate. How come it's not on the list?
- The bottom one is self signed and doesn't even have any services associated with it. Does it need to be there?
- The top one is OK I think but you're saying after Nov 2015 I'll need another self-signed cert for webmail? Isn't that the purpose of the SSL cert?
- Email on our mobile phones are still working. Should we expect this to stop working soon?
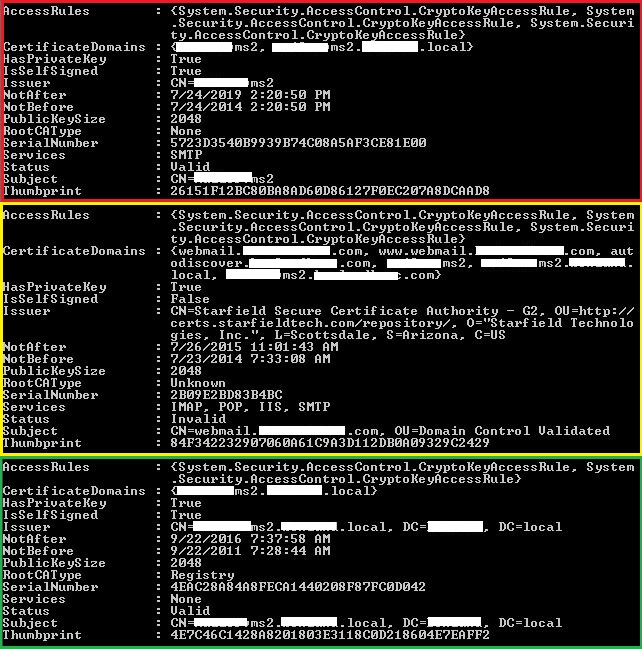
Questions:
- Why is the middle one (outlined in yellow) still showing as invalid?
- I didn't remove the expired certificate. How come it's not on the list?
- The bottom one is self signed and doesn't even have any services associated with it. Does it need to be there?
- The top one is OK I think but you're saying after Nov 2015 I'll need another self-signed cert for webmail? Isn't that the purpose of the SSL cert?
- Email on our mobile phones are still working. Should we expect this to stop working soon?
The top certificate is fine, and will remain fine until 2015. However you could look at removing everything and creating new certificates - you need the two as outlined.
There is something with your trusted certificate.
The RootCAType should say ThirdParty.
That means it cannot identify the certificate correctly.
Therefore you either have
- a corrupt SSL certificate
- missing intermediate certificate
- missing root certificates
The first one can be resolved by getting the certificate rekeyed. Create a new request in Exchange and use that to do the rekey.
The second one you should have done as part of the original installation. You got the intermediate certificates as part of the bundle.
The third one is more serious and I doubt if that is the cause unless someone has been mucking about with the server certificates.
With the SSL provider's site there should be a validation tool. That will test to ensure that you have installed everything correctly.
Simon.
There is something with your trusted certificate.
The RootCAType should say ThirdParty.
That means it cannot identify the certificate correctly.
Therefore you either have
- a corrupt SSL certificate
- missing intermediate certificate
- missing root certificates
The first one can be resolved by getting the certificate rekeyed. Create a new request in Exchange and use that to do the rekey.
The second one you should have done as part of the original installation. You got the intermediate certificates as part of the bundle.
The third one is more serious and I doubt if that is the cause unless someone has been mucking about with the server certificates.
With the SSL provider's site there should be a validation tool. That will test to ensure that you have installed everything correctly.
Simon.
ASKER
Was that an independent checking tool, or the one from the SSL provider?
For whatever reason the server cannot tell the certificate is valid. Do you have a proxy or anything else that could be blocking the server from connecting to the hosts on the internet used for validation/revocation checks?
Simon.
For whatever reason the server cannot tell the certificate is valid. Do you have a proxy or anything else that could be blocking the server from connecting to the hosts on the internet used for validation/revocation checks?
Simon.
ASKER
There is no proxy involved that I know of.
Digicert.com is where I ran the validation.
I purchased the certificate from certificatesforexchange.co
I don't see a validation tool on their page.
If you see one, please send me a link to it.
Digicert.com is where I ran the validation.
I purchased the certificate from certificatesforexchange.co
I don't see a validation tool on their page.
If you see one, please send me a link to it.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Everything seems to be working so I'd rather not mess around with it any longer.
If an issue arises, I'll have to handle it at that time.
If not, next year when we renew the cert I'll try and make sure things go a bit smoother.
Thanks for the help.
If an issue arises, I'll have to handle it at that time.
If not, next year when we renew the cert I'll try and make sure things go a bit smoother.
Thanks for the help.
Was it done through IIS ?
If so simply ensure you complete the request process in IIS.
Alternatively you can go to an elevated command prompt and run:
certreq -accept C:\SSL_Certs\2014_SSL.crt
Once the above is run it should indicate if the certificate is installed or if it failed.
As for exchange:
your command syntax is wrong, you nee the "Thumbprint" flag
Enable-ExchangeCertificate