superjohnbarnes
asked on
Server 2012 iSCSI target removal
At the moment I have a windows server 2012 running Hyper-V. On it I have a 600 GB iSCSI target which is connected to another iSCSI target on a replication (DR) server.
I need to decommision the replication server and move to another server but I am concerned about removing the iSCSI targets on the live server.
Is it simply a case of removing the target and then adding another one to the new server or will removing the target in some way disrupt the data?
Thanks,
I need to decommision the replication server and move to another server but I am concerned about removing the iSCSI targets on the live server.
Is it simply a case of removing the target and then adding another one to the new server or will removing the target in some way disrupt the data?
Thanks,
You either are misusing terminology or you have done something that is *very* bad. There is a difference between an initiator and a target, and for windows these almost always be a one to one ratio. Based on your description, that isn't the case, so you are already in a situation where data corruption can occur. But in general, if you keep to a 1:1 connection between initiator and target, you can disconnect and reconnect to a new server without issue. Of course if you disconnect while an application is writing data, the application could fail or data may be inconsistent, but that is a separate issue. You'd usually stop SQL, exchange, etch before disconnecting a target to avoid that issue.
ASKER
Hi Cliff,
You have me worried now! Although this setup has been running well for over a year with replication of 3 virtual servers to a DR server the possibility of having the virtual disks incorrectly setup has me a little concerned.
Can you explain the 1 to 1 ratio? Should I be using a target on the main server and just initiator on the DR server with no target or virtual disks? I need to be able to failover to the DR server.
Thanks,
Peter
You have me worried now! Although this setup has been running well for over a year with replication of 3 virtual servers to a DR server the possibility of having the virtual disks incorrectly setup has me a little concerned.
Can you explain the 1 to 1 ratio? Should I be using a target on the main server and just initiator on the DR server with no target or virtual disks? I need to be able to failover to the DR server.
Thanks,
Peter
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi Cliff,
Looking further into this it does indeed look like I have setup correctly with the 1 to 1 relationship. But the question still remains (happy to open another) as to which I remove. This might be a stupid question but I would just like to make sure. Do i remove the iSCSi virtual disk or the iSCSI target. I am 90% sure that i will be the target. Please see the attached.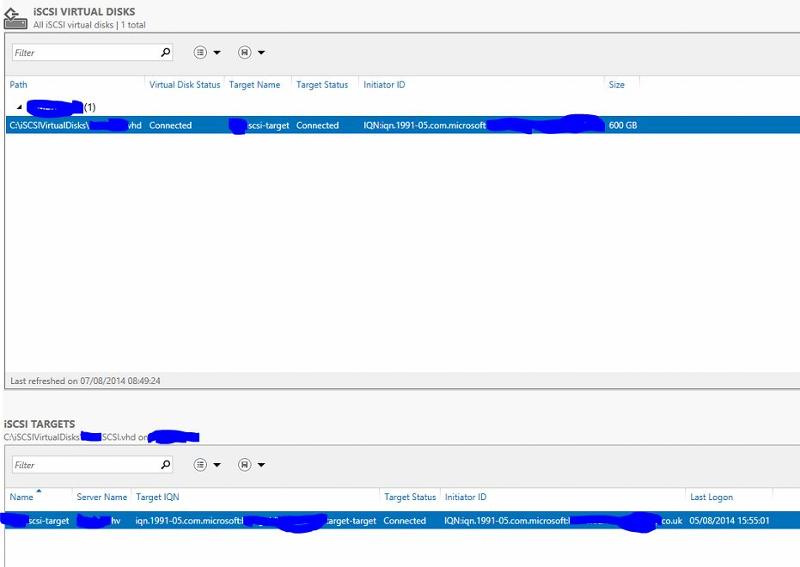
Looking further into this it does indeed look like I have setup correctly with the 1 to 1 relationship. But the question still remains (happy to open another) as to which I remove. This might be a stupid question but I would just like to make sure. Do i remove the iSCSi virtual disk or the iSCSI target. I am 90% sure that i will be the target. Please see the attached.
Since your target still shows as connected, I would not remove if. I'd disconnect from the initiator end of the connection first. Then you can retire the target at your leisure.
ASKER
Excellent. Worked a treat. Thanks again.