Create route to alternate gateway in ASA 5510
My apologies, I am fairly green when it comes to Cisco.
I have a setup in which I have a Cisco box as my default gateway (with local address 192.168.99.1, let's say) and another router which I intend to use as a VPN appliance at 192.168.99.2. The VPN network is 172.16.0.0 so I need to add a static route to the Cisco which routes traffic to/from 172.16.0.0 to the gateway 192.168.99.2. I added a default route which seems to work, however, the ASA seems to get hung up on an implicit rule (according to the Packet Tracer)
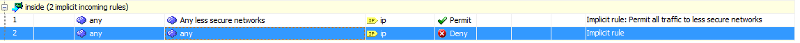
If I try and manually add rules to allow traffic in both directions on the inside interface, it automatically overwrites the first implicit rule. How do I add the rules I need?
I have a setup in which I have a Cisco box as my default gateway (with local address 192.168.99.1, let's say) and another router which I intend to use as a VPN appliance at 192.168.99.2. The VPN network is 172.16.0.0 so I need to add a static route to the Cisco which routes traffic to/from 172.16.0.0 to the gateway 192.168.99.2. I added a default route which seems to work, however, the ASA seems to get hung up on an implicit rule (according to the Packet Tracer)

If I try and manually add rules to allow traffic in both directions on the inside interface, it automatically overwrites the first implicit rule. How do I add the rules I need?
Please post a sanitized config for both cisco devices.
Based on the picture you need to re-sequence the ACL.
Example:
Router(config)# ip access-list resequence inside 100 10
should re-sequence starting at 100 and incrementing by 10.
Then you can insert up to 9 lines after the permit line and keep the deny any any as the last line.
Example:
Router(config)# ip access-list resequence inside 100 10
should re-sequence starting at 100 and incrementing by 10.
Then you can insert up to 9 lines after the permit line and keep the deny any any as the last line.
ASKER
Only the primary gateway (192.168.66.1) is a Cisco.
I can get communication to work if I manually add a static route to systems on the internal network so they know to use the alternate gateway when communicating with the 172.16.0.0 network, so I am fairly sure the issue is with the default gateway.
Cryptochecksum: ??????????????????????????
: Saved
: Written by enable_15 at 13:42:49.775 UTC Wed Aug 20 2014
!
ASA Version 8.2(5)
!
hostname STA-5510
domain-name myorg.ca.org
enable password ???????????????? encrypted
passwd ???????????????? encrypted
names
!
interface Ethernet0/0
description TPAC Primary ISP
nameif outside
security-level 0
ip address 64.???.???2.150 255.255.255.240
!
interface Ethernet0/1
description OLD XO Backup ISP
nameif backup
security-level 1
ip address 64.???.???.70 255.255.255.240
!
interface Ethernet0/2
description Inside
nameif inside
security-level 100
ip address 192.168.99.1 255.255.255.0
!
interface Ethernet0/3
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
nameif management
security-level 100
no ip address
management-only
!
regex Pandora "\.pandora\.com"
ftp mode passive
dns domain-lookup outside
dns domain-lookup backup
dns domain-lookup inside
dns server-group DefaultDNS
domain-name myorg.ca.org
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq https
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq www
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq 9675
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq 9676
access-list outside_access_in extended permit tcp any host 64.???.???2.148 eq https
access-list outside_access_in extended permit tcp any host 64.???.???2.148 eq www
access-list outside_access_in extended permit tcp any host 64.???.???2.148 eq smtp
access-list backup_access_in extended permit icmp any any
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq https
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq www
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq 9675
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq 9676
access-list backup_access_in extended permit tcp any host 64.???.???.72 eq https
access-list backup_access_in extended permit tcp any host 64.???.???.72 eq www
access-list backup_access_in extended permit tcp any host 64.???.???.72 eq smtp
access-list backup_access_in extended permit ip any 172.16.0.0 255.255.255.0
access-list backup_access_in extended permit ip 172.16.0.0 255.255.255.0 any
access-list backup_access_in extended permit ip 192.168.99.0 255.255.255.0 172.16.0.0 255.255.255.0
access-list nonat extended permit ip 192.168.99.0 255.255.255.0 192.168.2??.0 255.255.255.0
access-list nonat extended permit ip 192.168.2??.0 255.255.255.0 192.168.99.0 255.255.255.0
access-list nonat extended permit ip 192.168.99.0 255.255.255.0 10.???.???.0 255.255.255.0
access-list nonat extended permit ip 192.168.99.0 255.255.255.0 172.16.0.0 255.255.255.0
access-list nonat extended permit ip 172.16.0.0 255.255.255.0 192.168.99.0 255.255.255.0
access-list orgsplit standard permit 192.168.99.0 255.255.255.0
access-list vpn_sta_2_ih extended permit ip 192.168.99.0 255.255.255.0 10.???.???.0 255.255.255.0
access-list stasslsplit standard permit 192.168.99.0 255.255.255.0
access-list stasslsplit standard permit 10.???.???.0 255.255.255.0
pager lines 24
logging enable
logging timestamp
logging buffer-size 819200
logging console informational
logging monitor informational
logging buffered informational
logging trap informational
logging history informational
logging asdm informational
logging device-id ipaddress outside
flow-export destination inside 192.168.99.75 2002
mtu outside 1500
mtu backup 1500
mtu inside 1500
mtu management 1500
ip local pool orgpool 192.168.2??.1-192.168.2??.
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-649-103.bin
no asdm history enable
arp timeout 14400
global (outside) 1 64.???.???2.151
global (backup) 1 64.???.???.71
nat (inside) 0 access-list nonat
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,backup) 64.???.???.72 192.168.99.54 netmask 255.255.255.255
static (inside,outside) 64.???.???2.148 192.168.99.54 netmask 255.255.255.255
access-group outside_access_in in interface outside
access-group backup_access_in in interface backup
route outside 0.0.0.0 0.0.0.0 64.???.???2.145 1
route backup 0.0.0.0 0.0.0.0 64.???.???.65 254
route inside 172.16.0.0 255.255.255.0 192.168.99.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
ldap attribute-map ORGMAP
map-name STA IETF-Radius-Class
map-value STA CN=VPN,DC=myorg,DC=ca,DC=o
dynamic-access-policy-reco
action terminate
dynamic-access-policy-reco
aaa-server ldapgroup protocol ldap
aaa-server ldapgroup (inside) host 192.168.99.8
ldap-base-dn dc=myorg, dc=ca, dc=org
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password ?????????????????
ldap-login-dn cn=VPNAdmin, dc=myorg, dc=ca, dc=org
server-type microsoft
ldap-attribute-map ORGMAP
http server enable
http 192.168.99.0 255.255.255.0 inside
snmp-server host inside 192.168.99.8 community myorgorg
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sla monitor 127
type echo protocol ipIcmpEcho 8.8.8.8 interface outside
num-packets 3
frequency 10
sla monitor schedule 127 life forever start-time now
service resetoutside
crypto ipsec transform-set orgsplit-set esp-3des esp-sha-hmac
crypto ipsec transform-set orgsplit-set-bk esp-3des esp-sha-hmac
crypto ipsec transform-set org_vpn_set_primary esp-3des esp-sha-hmac
crypto ipsec transform-set org_vpn_set_backup esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map outside_dyn_map 88 set transform-set orgsplit-set
crypto dynamic-map backup_dyn_map 99 set transform-set orgsplit-set-bk
crypto map outside_map 10 match address vpn_sta_2_ih
crypto map outside_map 10 set peer 98.1??.1??.55 99.1??.2??.93
crypto map outside_map 10 set transform-set org_vpn_set_primary
crypto map outside_map 11 match address vpn_sta_2_ih
crypto map outside_map 11 set peer 98.1??.1??.55 99.1??.2??.93
crypto map outside_map 11 set transform-set org_vpn_set_backup
crypto map outside_map 88 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto map outside_map interface backup
crypto map backup_map 9 ipsec-isakmp dynamic backup_dyn_map
crypto ca trustpoint localtrust
enrollment self
fqdn stavpn.myorg.ca.org
subject-name CN=myorg.ca.org
keypair stavpnkey
crl configure
crypto ca certificate chain localtrust
certificate ??????????????????????????
quit
crypto isakmp enable outside
crypto isakmp enable backup
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
track 1 rtr 128 reachability
telnet 192.168.99.0 255.255.255.0 inside
telnet timeout 15
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point localtrust outside
webvpn
port 444
enable outside
enable backup
svc image disk0:/anyconnect-win-2.5.
svc enable
tunnel-group-list enable
group-policy noaccess_pri internal
group-policy noaccess_pri attributes
vpn-simultaneous-logins 0
group-policy noaccess_bk internal
group-policy noaccess_bk attributes
vpn-simultaneous-logins 0
group-policy orgsplitpolicy_pri internal
group-policy orgsplitpolicy_pri attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-tunnel-protocol IPSec l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value orgsplit
default-domain value myorg.ca.org
group-policy orgsslpolicy_pri internal
group-policy orgsslpolicy_pri attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol IPSec l2tp-ipsec webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value stasslsplit
default-domain value myorg.ca.org
group-policy orgsplitpolicy_bk internal
group-policy orgsplitpolicy_bk attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-tunnel-protocol IPSec l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value orgsplit
default-domain value myorg.ca.org
group-policy orgsslpolicy_bk internal
group-policy orgsslpolicy_bk attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol IPSec l2tp-ipsec webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value stasslsplit
default-domain value myorg.ca.org
username test password ????????????? encrypted privilege 15
username vpnuser password ??????????? encrypted
username vpnuser attributes
service-type remote-access
username neadmin password ????????????? encrypted
tunnel-group orgsplitgroup_pri type remote-access
tunnel-group orgsplitgroup_pri general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsplitpolicy_pri
tunnel-group orgsplitgroup_pri ipsec-attributes
pre-shared-key ???????????????????
tunnel-group orgsplitgroup_bk type remote-access
tunnel-group orgsplitgroup_bk general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsplitpolicy_bk
tunnel-group orgsplitgroup_bk ipsec-attributes
pre-shared-key ?????????????????
tunnel-group 98.1??.1??.55 type ipsec-l2l
tunnel-group 98.1??.1??.55 ipsec-attributes
pre-shared-key ????????????????
isakmp keepalive threshold 20 retry 3
tunnel-group stasslgroup_pri type remote-access
tunnel-group stasslgroup_pri general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsslpolicy_pri
tunnel-group stasslgroup_bk type remote-access
tunnel-group stasslgroup_bk general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsslpolicy_bk
!
class-map type regex match-any PandoraBlock
match regex Pandora
class-map inspection_default
match default-inspection-traffic
class-map type inspect http match-all AppHeaderClass
match request header regex Pandora regex Pandora
class-map flow_export_class
match any
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map type inspect http http_inspection_policy
parameters
protocol-violation action drop-connection
match request method connect
drop-connection log
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
policy-map flow_export_policy
class flow_export_class
flow-export event-type all destination 192.168.99.75
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:???????????
: end
I can get communication to work if I manually add a static route to systems on the internal network so they know to use the alternate gateway when communicating with the 172.16.0.0 network, so I am fairly sure the issue is with the default gateway.
Cryptochecksum: ??????????????????????????
: Saved
: Written by enable_15 at 13:42:49.775 UTC Wed Aug 20 2014
!
ASA Version 8.2(5)
!
hostname STA-5510
domain-name myorg.ca.org
enable password ???????????????? encrypted
passwd ???????????????? encrypted
names
!
interface Ethernet0/0
description TPAC Primary ISP
nameif outside
security-level 0
ip address 64.???.???2.150 255.255.255.240
!
interface Ethernet0/1
description OLD XO Backup ISP
nameif backup
security-level 1
ip address 64.???.???.70 255.255.255.240
!
interface Ethernet0/2
description Inside
nameif inside
security-level 100
ip address 192.168.99.1 255.255.255.0
!
interface Ethernet0/3
no nameif
no security-level
no ip address
!
interface Management0/0
shutdown
nameif management
security-level 100
no ip address
management-only
!
regex Pandora "\.pandora\.com"
ftp mode passive
dns domain-lookup outside
dns domain-lookup backup
dns domain-lookup inside
dns server-group DefaultDNS
domain-name myorg.ca.org
access-list outside_access_in extended permit icmp any any
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq https
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq www
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq 9675
access-list outside_access_in extended permit tcp any host 64.???.???2.150 eq 9676
access-list outside_access_in extended permit tcp any host 64.???.???2.148 eq https
access-list outside_access_in extended permit tcp any host 64.???.???2.148 eq www
access-list outside_access_in extended permit tcp any host 64.???.???2.148 eq smtp
access-list backup_access_in extended permit icmp any any
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq https
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq www
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq 9675
access-list backup_access_in extended permit tcp any host 64.???.???.70 eq 9676
access-list backup_access_in extended permit tcp any host 64.???.???.72 eq https
access-list backup_access_in extended permit tcp any host 64.???.???.72 eq www
access-list backup_access_in extended permit tcp any host 64.???.???.72 eq smtp
access-list backup_access_in extended permit ip any 172.16.0.0 255.255.255.0
access-list backup_access_in extended permit ip 172.16.0.0 255.255.255.0 any
access-list backup_access_in extended permit ip 192.168.99.0 255.255.255.0 172.16.0.0 255.255.255.0
access-list nonat extended permit ip 192.168.99.0 255.255.255.0 192.168.2??.0 255.255.255.0
access-list nonat extended permit ip 192.168.2??.0 255.255.255.0 192.168.99.0 255.255.255.0
access-list nonat extended permit ip 192.168.99.0 255.255.255.0 10.???.???.0 255.255.255.0
access-list nonat extended permit ip 192.168.99.0 255.255.255.0 172.16.0.0 255.255.255.0
access-list nonat extended permit ip 172.16.0.0 255.255.255.0 192.168.99.0 255.255.255.0
access-list orgsplit standard permit 192.168.99.0 255.255.255.0
access-list vpn_sta_2_ih extended permit ip 192.168.99.0 255.255.255.0 10.???.???.0 255.255.255.0
access-list stasslsplit standard permit 192.168.99.0 255.255.255.0
access-list stasslsplit standard permit 10.???.???.0 255.255.255.0
pager lines 24
logging enable
logging timestamp
logging buffer-size 819200
logging console informational
logging monitor informational
logging buffered informational
logging trap informational
logging history informational
logging asdm informational
logging device-id ipaddress outside
flow-export destination inside 192.168.99.75 2002
mtu outside 1500
mtu backup 1500
mtu inside 1500
mtu management 1500
ip local pool orgpool 192.168.2??.1-192.168.2??.
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-649-103.bin
no asdm history enable
arp timeout 14400
global (outside) 1 64.???.???2.151
global (backup) 1 64.???.???.71
nat (inside) 0 access-list nonat
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,backup) 64.???.???.72 192.168.99.54 netmask 255.255.255.255
static (inside,outside) 64.???.???2.148 192.168.99.54 netmask 255.255.255.255
access-group outside_access_in in interface outside
access-group backup_access_in in interface backup
route outside 0.0.0.0 0.0.0.0 64.???.???2.145 1
route backup 0.0.0.0 0.0.0.0 64.???.???.65 254
route inside 172.16.0.0 255.255.255.0 192.168.99.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
ldap attribute-map ORGMAP
map-name STA IETF-Radius-Class
map-value STA CN=VPN,DC=myorg,DC=ca,DC=o
dynamic-access-policy-reco
action terminate
dynamic-access-policy-reco
aaa-server ldapgroup protocol ldap
aaa-server ldapgroup (inside) host 192.168.99.8
ldap-base-dn dc=myorg, dc=ca, dc=org
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password ?????????????????
ldap-login-dn cn=VPNAdmin, dc=myorg, dc=ca, dc=org
server-type microsoft
ldap-attribute-map ORGMAP
http server enable
http 192.168.99.0 255.255.255.0 inside
snmp-server host inside 192.168.99.8 community myorgorg
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
sla monitor 127
type echo protocol ipIcmpEcho 8.8.8.8 interface outside
num-packets 3
frequency 10
sla monitor schedule 127 life forever start-time now
service resetoutside
crypto ipsec transform-set orgsplit-set esp-3des esp-sha-hmac
crypto ipsec transform-set orgsplit-set-bk esp-3des esp-sha-hmac
crypto ipsec transform-set org_vpn_set_primary esp-3des esp-sha-hmac
crypto ipsec transform-set org_vpn_set_backup esp-3des esp-sha-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map outside_dyn_map 88 set transform-set orgsplit-set
crypto dynamic-map backup_dyn_map 99 set transform-set orgsplit-set-bk
crypto map outside_map 10 match address vpn_sta_2_ih
crypto map outside_map 10 set peer 98.1??.1??.55 99.1??.2??.93
crypto map outside_map 10 set transform-set org_vpn_set_primary
crypto map outside_map 11 match address vpn_sta_2_ih
crypto map outside_map 11 set peer 98.1??.1??.55 99.1??.2??.93
crypto map outside_map 11 set transform-set org_vpn_set_backup
crypto map outside_map 88 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto map outside_map interface backup
crypto map backup_map 9 ipsec-isakmp dynamic backup_dyn_map
crypto ca trustpoint localtrust
enrollment self
fqdn stavpn.myorg.ca.org
subject-name CN=myorg.ca.org
keypair stavpnkey
crl configure
crypto ca certificate chain localtrust
certificate ??????????????????????????
quit
crypto isakmp enable outside
crypto isakmp enable backup
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
!
track 1 rtr 128 reachability
telnet 192.168.99.0 255.255.255.0 inside
telnet timeout 15
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics host
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl trust-point localtrust outside
webvpn
port 444
enable outside
enable backup
svc image disk0:/anyconnect-win-2.5.
svc enable
tunnel-group-list enable
group-policy noaccess_pri internal
group-policy noaccess_pri attributes
vpn-simultaneous-logins 0
group-policy noaccess_bk internal
group-policy noaccess_bk attributes
vpn-simultaneous-logins 0
group-policy orgsplitpolicy_pri internal
group-policy orgsplitpolicy_pri attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-tunnel-protocol IPSec l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value orgsplit
default-domain value myorg.ca.org
group-policy orgsslpolicy_pri internal
group-policy orgsslpolicy_pri attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol IPSec l2tp-ipsec webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value stasslsplit
default-domain value myorg.ca.org
group-policy orgsplitpolicy_bk internal
group-policy orgsplitpolicy_bk attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-tunnel-protocol IPSec l2tp-ipsec
split-tunnel-policy tunnelspecified
split-tunnel-network-list value orgsplit
default-domain value myorg.ca.org
group-policy orgsslpolicy_bk internal
group-policy orgsslpolicy_bk attributes
dns-server value 192.168.99.6 192.168.99.8
vpn-idle-timeout none
vpn-session-timeout none
vpn-tunnel-protocol IPSec l2tp-ipsec webvpn
split-tunnel-policy tunnelspecified
split-tunnel-network-list value stasslsplit
default-domain value myorg.ca.org
username test password ????????????? encrypted privilege 15
username vpnuser password ??????????? encrypted
username vpnuser attributes
service-type remote-access
username neadmin password ????????????? encrypted
tunnel-group orgsplitgroup_pri type remote-access
tunnel-group orgsplitgroup_pri general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsplitpolicy_pri
tunnel-group orgsplitgroup_pri ipsec-attributes
pre-shared-key ???????????????????
tunnel-group orgsplitgroup_bk type remote-access
tunnel-group orgsplitgroup_bk general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsplitpolicy_bk
tunnel-group orgsplitgroup_bk ipsec-attributes
pre-shared-key ?????????????????
tunnel-group 98.1??.1??.55 type ipsec-l2l
tunnel-group 98.1??.1??.55 ipsec-attributes
pre-shared-key ????????????????
isakmp keepalive threshold 20 retry 3
tunnel-group stasslgroup_pri type remote-access
tunnel-group stasslgroup_pri general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsslpolicy_pri
tunnel-group stasslgroup_bk type remote-access
tunnel-group stasslgroup_bk general-attributes
address-pool orgpool
authentication-server-grou
default-group-policy orgsslpolicy_bk
!
class-map type regex match-any PandoraBlock
match regex Pandora
class-map inspection_default
match default-inspection-traffic
class-map type inspect http match-all AppHeaderClass
match request header regex Pandora regex Pandora
class-map flow_export_class
match any
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map type inspect http http_inspection_policy
parameters
protocol-violation action drop-connection
match request method connect
drop-connection log
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect ip-options
policy-map flow_export_policy
class flow_export_class
flow-export event-type all destination 192.168.99.75
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:???????????
: end
ASKER
pony10us,
So just log into the CLI and execute that command?
So just log into the CLI and execute that command?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ha! I did not know that. Now I can edit the rest of the config. Thanks!